Computer Science > QUESTIONS & ANSWERS > 2022 CCSP Study - Udemy 600 Questions and Answers. (All)
2022 CCSP Study - Udemy 600 Questions and Answers.
Document Content and Description Below
2022 CCSP Study - Udemy 600 Questions Within LDAP, which of the following acts as the primary key for an object? A. CN B. AN C. HN D. Distinguished Name (DN) Artificial intelligence that i... ncorporates emotional intelligence, social intelligence, and cognitive learning and responses is known as: A. Humanized B. Human-like C. Analytical D. Human-inspired A small business was unhappy with its cloud provider's services. For this reason, the business decided to remove all data and applications from its cloud provider's environment and move to a new cloud provider. It was able to do so without any major impact on its production and operations. What term BEST describes the ability to do this? A. Multitenancy B. Rapid elasticity C. Reversibility D. On-demand self-service There are four main cloud deployment models: public cloud, private cloud, community cloud, and which of the following? A. Mixed cloud B. Metropolitan cloud C. Hybrid cloud D. Expanded cloud Through the Common Criteria standard, what does an EAL2 score tell us about the organization's security practices and results? A. It has been structurally tested B. It has been functionally tested C. It has been methodically tested and checked D. It has a formally verified design and has been tested An engineer needs to ensure that data has been completely removed from cloud servers after a data migration. Which data sanitation technique can be used in a cloud environment successfully? A. Incineration B. Degaussing C. Destruction D. Overwriting "Finite State Model" is one of the 11 sections that are defined in which standard? A. PCI DSS B. NIST SP 800-53 C. FIPS 140-2 D. ISO/IEC 27001 A merchant takes credit cards through a point of sale system. Which compliance standard must the merchant adhere to? A. ISO/IEC 27017 B. Common criteria C. FIPS 140-2 D. PCI DSS Which of the following regulatory requirements applies to a retail clothing store that accepts credit cards? A. FISMA B. HIPAA C. PCI DSS D. NFPA Interoperability can BEST be described as: A. The ease with which resources can be rapidly expanded as needed by a cloud customer. B. The ability for two customers to share the same pool of resources while being isolated from each other. C. The ease with which components of an application or service can be moved or reused. D. The ability of customers to make changed to their cloud infrastructure with minimal input from the cloud provider. Company A and Company B have both purchased cloud services from a cloud service provider. Company A and Company B are both sharing access to a pool of resources owned by the cloud service provider. Which of the following BEST describes Company A and Company B? A. Audit B. Partner C. Tenant D. Broker Your organization must be able to rapidly scale resources up or down, as required, to meet future needs and from a variety of cloud geographical regions. Which cloud characteristic is required in this scenario? A. Scalability B. Resource Pooling C. Elasticity D. High Availability Cloud service providers will have clear requirements for items such as uptime, customer service response time, and availability. Where would these requirements MOST LIKELY be outlined for the client? A. RPO B. RTO C. SLA D. NIST In a shared responsibility continuum, who takes a larger security role in an IaaS model and a smaller role in a SaaS model? A. Cloud Service Broker (CSB) B. Cloud Service Provider (CSP) C. Cloud Service Partner D. Cloud Service Customer (CSC) After terminating an employee, the former employee went on to leak an organization's sensitive intellectual property to a competitor. Which type of threat is being described here? A. Denial of Service (DoS) B. Advanced Persistent Threat (APT) C. Malicious Insider D. Account Hijacking An engineer just purchased a software suite for his organization. The software is hosted by a cloud provider and that cloud provider maintains and manages the application itself, as well the entire infrastructure and platform. The software is accessed over the Internet and is not installed locally on any employee's machine. What type of cloud service is being described here? A. CaaS B. SaaS C. IaaS D. PaaS What role do Amazon Web Services, Microsoft Azure, and Google Cloud play in cloud computing? A. Cloud Service Partner B. Cloud Service Provider C. Cloud Service Broker D. Cloud Service Customer An organization is running VMware Workstation. What type of hypervisor is this? A. Software-based B. IaaS C. PaaS D. Bare-metal An organization had a large amount of private data stolen by a hacker and then leaked online. This is an example of which type of threat? A. Advanced persistent threat B. Malicious insider C. Data breach D. Account hijacking Which of the following areas is always entirely the CSP's responsibility, regardless of the cloud service model used? A. Virtualization B. Networking C. Databases D. Storage Which of the following organizations publishes security standards applicable to any systems used by the federal government and its contractors? A. ISO B. ISACA C. SOC D. NIST Which of the following is an example of data sanitation? A. An engineer installed new locks on the server rack so that attackers cannot gain unauthorized physical access B. After replacing a hard drive, a user smashed the old hard drive with a hammer so that data couldn't be recovered from it C. An engineer applies encryption to a user's hard drive so that it's protected if it's ever stolen D. A user resets their password every 30 days in order to help prevent breaches Company A and Company B both purchase cloud services from the same cloud provider. The cloud provider has Company A and Company B sharing the same environment but ensures that both Company A's and Company B's data is isolated from each other and not visible to the other. What can this type of scenario be described as? A. Hybrid cloud B. On-demand self-service C. Private tenant D. Multitenancy Which of the following would benefit the MOST from a private cloud deployment? A. A small business that needs to keep costs low B. A medium-sized business that requires some data to be kept confidential, but also has a lot of non-private data stored C. A healthcare organization that needs to keep all of its patients' data secure, no matter the cost D. A student building a lab for testing purposes An organization purchases their accounting program through the cloud. The accounting program is hosted entirely by the cloud provider, on cloud hosted servers. The cloud customer is not responsible for maintaining any of items needed in order to access the accounting program, they are simply able to access the program from anywhere that they have an Internet connection. What type of cloud service is being described here? A. SaaS B. DaaS C. PaaS D. IaaS An engineer is moving an application from one cloud provider to another cloud provider. Which of the following gives him the ability to do this? A. Rapid elasticity B. Multitenancy C. Cloud application portability D. Cloud data portability The FIPS 140-2 standard defines four levels of security. Of the four levels, which provides the HIGHEST level of security and tamper protection? A. Level 1 B. Level 2 C. Level 3 D Level 4 Which of the following is NOT one of the main cloud service categories? A. Internet service capability B. Software service capability C. Platform service capability D. Infrastructure service capability In terms of cloud services, at what point are there concerns regarding data protection and privacy present? A. All options are correct B. During a contract C. During the erasure or destruction of data D. At the end of a contract Which of the following statements regarding moving from a data center model to a cloud model is TRUE? A. A traditional data center is much more secure than a cloud environment. B. A traditional data center will have higher costs on the operational side and lower costs in regard to hardware. C. The pricing for cloud computing may be less predictable than that of a traditional data center. D. Using a cloud environment or a traditional data center will incur the exact same costs. Alice is responsible for preparing systems for the cloud, as well as administering and monitoring services. When requested, Alice provides audit data. She is also responsible for managing inventory and assets. Which title BEST fits Alice's responsibilities? A. Cloud service broker B. Cloud service business manager C. Cloud service operations manager D. Cloud service developer Which of the following would benefit the MOST from using a hybrid cloud? A. A group of organizations looking to create a shared service for all their customers to use B. A small business that doesn't have much sensitive data and is just looking to move email to the cloud C. An organization that only requires that certain items are kept very secure, but can't afford a full private cloud D. A healthcare company that needs to ensure that all of their data is kept extremely secure and private, no matter the expense When an application is accessed via a network and is NOT installed locally onto a user's computer, this application is known as which of the following? A. Tenant B. Cloud application C. Measured service D. IaaS In which of the following cloud deployment models is the cloud provider responsible for the operating systems and hosting environment, while the customer is responsible for deploying their applications within the provided platform infrastructure? A. CaaS B. SaaS C. PaaS D. IaaS Traditional encryption methods may become obsolete as the cloud's computing power and innovative technology improve optimization issues. What kind of advanced technology is potentially capable of defeating today's encryption methods? A. Machine learning B. Artificial intelligence C. Quantum computing D. Blockchain In which of the following cloud categories does the cloud customer have full access to and control over the operating systems, storage, and applications without having access to the physical infrastructure? A. PaaS B. SaaS C. IaaS D. MaaS A software development company is looking to purchase a cloud service. They need the ability to develop and maintain their applications in the cloud without needing to manage and maintain the servers and network equipment that keeps the applications running. Which of the following cloud service types BEST fits the needs of the software development company? A. DaaS B. PaaS C. SaaS D. IaaS To ensure compliance with regulatory requirements, an organization must conduct an annual assessment of its negotiated service agreements with its present cloud provider. This year, the organization may decide to change their CSP due to cost concerns. What should the organization consider as it evaluates the service agreement? A. Reversibility B. Resiliency C. Auditability D. Interoperability Cloud security is a challenge. What aspect of cloud computing creates new complexities to security in the cloud? A. Encryption B. Measured service C. Broad network access D. Multi-tenancy A software developer is looking for a way to avoid installing and running application software directly within the operating system. As an alternative, it is suggested they should begin storing applications and any associated library files in the cloud. Which cloud service is being discussed? A. Virtualization B. Containerization C. Quantum computing D. Blockchain A law firm is moving their data to the cloud. For legal reasons, they need to ensure that their data is kept completely private, and that the data is owned entirely by themselves and nobody else. Which cloud deployment model would be the BEST fit for this law firm? A. Private cloud B. Community cloud C. Public cloud D. Hybrid cloud Through sustained cooperation with a cloud service provider, the third-party file hosting and sharing platform extends its reach to service areas where it lacks infrastructure. What functional cloud computing role does the third-party file hosting and sharing platform play in this scenario? A. Cloud Service Partner B. Cloud Service Broker C. Cloud Service Provider (CSP) D. Cloud Service Customer (CSC) Which of the following is widely considered to be the "gold standard" in regard to the security of information systems and their data? A. FIPS 140-2 B. ISO/IEC 27001 C. NIST SP 800-53 D. PCI DSS Which of the following is true in terms of maintenance and versioning in the cloud? A. Updates and patches are scheduled with the customer in the SaaS or PaaS model. B. The CSC is responsible for the maintenance and versioning of the hardware, network, and storage, as well as the virtualization software, in an IaaS solution. C. The Cloud Service Customer (CSC) is responsible for the maintenance and versioning of the apps they acquire and develop in a PaaS solution. The Cloud Service Provider (CSP) is responsible for the platform, tools, and underlying infrastructure. D. The CSC is responsible for the maintenance and versioning of all components in a SaaS product. Which cloud computing role delivers value by aggregating services from many vendors, integrating them with an organization's current infrastructure, and customizing services that a CSP cannot provide? A. Cloud Service Broker B. Cloud Service Partner C. Cloud Service Provider (CSP) D. Cloud Service Customer (CSC) Which of the following would be a benefit of using a public cloud deployment rather than a private, hybrid, or community cloud deployment? A. Inexpensive B. Control over systems C. Security D. Full ownership of data Which cloud service provider role oversees business plans and customer relationships with cloud customers? A. Inter-cloud provider B. Cloud service business manager C. Cloud service manager D. Cloud service deployment manager A cloud engineer needs to rapidly deploy an application package throughout a large cloud environment. Which of the following could this engineer use to accomplish this easily? A. Machine learning B. Containers C. Key management D. MDM An organization has spent quite a significant amount of their budget on vendor-specific investments and now the cost for them to move to a new cloud provider would be far too high to be feasible. What is the term used to describe this type of scenario? A. Provider exit B. Data sanitation C. Customer lock-in D. Vendor lock-in What is an essential layer around a virtual machine, subnet, or cloud resource as part of a layered defense strategy? A. Contextual-based security B. Network security group C. Cloud gateway D. Ingress and egress monitoring Which of the following is a benefit of using a private cloud over a hybrid, community, or public cloud deployment? A. Easier setup B. Most scalable C. Security D. Less expensive The requirement that providers must restrict physical access to cardholder data falls under which regulatory standard? A. PCI DSS B. FIPS 140-2 C. NIST SP 800-53 D. SOC 1 A cloud administrator would like to reduce the risk of vendor lock-in. What cloud shared consideration should the administrator be looking for? A. Interoperability B. Versioning C. Availability D. Reversibility Through Common Criteria, what does an EAL4 score tell us about an organization's security practices and results? A. It has been structurally tested B. It has been functionally tested C. It has been semi-formally designed and tested D. It has been methodically designed, tested, and reviewed When data is stored on a device, but not being used by an application or actively traversing the network, it is called: A. Data in transit B. Data at rest C. Structured data D. Unstructured data Data can be encrypted and then the encryption keys can be destroyed as a method of data sanitation. This process is known as: A. Overwriting B. Cryptographic erasing C. Encrypted overwriting D. Incineration Adam would like to find information regarding the minimal requirements that his organization's cloud provider must meet for contractual satisfaction. Where could Adam find this information? A. SLA B. ISO C. API D. EAL Your organization has suffered a fire in its office building, and it is your responsibility to maintain operations during the incident. Which document should you consult before moving forward? A. DRP B. IRP C. AUP D. BCP Which of the following blockchain types requires a permission to join but can be open and utilized by a group of different organizations working together? A. Consortium B. Neighborhood C. Community D. Public Which of these cloud-related factors has the biggest influence on vendor lock-in? A. Reversibility B. Portability C. Interoperability D. Resiliency The terms public, private, hybrid, and community are types of: A. On-demand self-service B. Cloud service category C. Cloud tenant D. Cloud deployment model A small enterprise would like to move their environment from one cloud provider to another. However, the cloud provider implemented techniques which have made it very difficult to move their systems to a new provider. What is this an example of? A. Vendor lock-in B. Data elasticity C. Cloud proprietary D. Provider control In a SaaS environment, if either SQL injection or cross-site scripting vulnerabilities exist within any SaaS implementation, every customer's data becomes at risk. Of the following, what is the BEST method for preventing this type of security risk? A. The provider should sign a contract stating that they are liable for any breaches. B. The provider should ensure that anti-virus software is up to date within their environment. C. The provider should have different data stores for each customer and keep all customers as segregated as possible. D. The provider should ensure that there is a patch schedule in place and that it is adhered to. Your organization currently hosts its cloud environment in the organization's data center. The organization utilizes a provider for their backup solution in accordance with their business continuity plan. Which configuration BEST describes their deployment? A. Cloud service backup, third-party backup B. Private cloud, cloud service backup C. Private cloud, private backup D. Cloud service backup, private backup Which of the following regulatory requirements applies to those in the health care industry? A. FISMA B. FRCP C. PCI DSS D. HIPAA Which of the following statements regarding type 2 hypervisors is TRUE? A. Due to being software-based, it's less likely that an attacker will be able to inject malicious code into the hypervisor. B. Due to being hardware-based, it's less likely that an attacker will be able to inject malicious code into the hypervisor. C. Due to being software-based, they are more vulnerable to flaws and exploits than type 1 hypervisors. D. Due to being hardware-based, they are more vulnerable to flaws and exploits than type 1 hypervisors. A cloud service is: A. Specifically a piece of software that is hosted in the cloud B. Any capability which is offered by a cloud provider C. Specifically an application which is offered by a cloud provider D. The process of building infrastructure in the cloud An engineer is concerned about the security of mobile devices in the organization which have been given access to corporate resources. What can this engineer implement to manage and maintain the devices? A. AI B. IoT C. BYOD D. MDM Which type of AI is purely cognitive-based? A. Humanized B. Analytical C. Enhanced D. Human-inspired Which of the following terms BEST describes the role of someone who connects existing systems and services to the cloud? A. Cloud service operations manager B. Cloud service auditor C. Cloud service integrator D. Cloud service business manager An organization is using VMware ESXI. Which of the following is this an example of? A. Type 4 hypervisor B. Type 3 hypervisor C. Type 1 hypervisor D. Type 2 hypervisor A cloud provider has assembled all of the cloud resources together and made them available for allocation to cloud customers. Which term BEST describes this process? A. Data portability B. Reversibility C. Application portability D. Resource pooling An engineer needs to provision a new cloud service. He is able to do so without ever interacting with the cloud provider. What is this known as? A. On-demand self service B. Reversibility C. Hybrid cloud D. Resource pooling A cloud provider has several of its cloud customers sharing access to its pool of resources. What term is used to describe the customers? A. Partner B. Auditor C. Hybrid D. Tenant Your company has invested in a PaaS (platform as a service) development platform. What would the organization's new role be? A. Cloud Service Customer (CSC) B. Cloud Service Partner C. Cloud Service Provider (CSP) D. Cloud Service Broker The FIPS 140-2 standard is divided into 11 sections that define security requirements. Which of the following is NOT one of these sections? A. Self-tests B. Physical security C. Security budget D. Operational environment Which of the following statements about type 1 hypervisors is TRUE? A. Due to it being software-based, it's less vulnerable to an attack from someone injecting malicious code than a type 2 hypervisor. B. Due to it being tied to the physical hardware of the machine, it's more vulnerable to an attack from someone using software exploits than a type 2 hypervisor. C. Due to being tied to the physical hardware of the machine, it would be harder for an attacker to inject malicious code to gain access than it would be on a type 2 hypervisor. D. Due to it being software-based, it's more vulnerable to an attack from someone using software exploits than a type 2 hypervisor. What term is used to describe an individual or organization that serves as an intermediary between cloud customers and a cloud service provider? A. Cloud service auditor B. Cloud service user C. Cloud service partner D. Cloud service broker What term BEST describes the scenario of multiple cloud customers sharing the same resources within the same environment, while also isolating them from each other for security purposes? A. Multitenancy B. On-demand self service C. Shared tenancy D. Hybrid cloud A college student is looking to set up her own cloud server so that she can install a few programs and create a lab. She needs a cloud option that is cost-effective and will allow her to only pay for what she needs. She doesn't have the funds to purchase and maintain her own hardware. Which cloud model would suit this student's needs the BEST? A. Private cloud B. Public cloud C. Community cloud D. Hybrid cloud James is able to connect to his home's thermostat using the Internet on his phone and adjust the temperature remotely. This is an example of which type of technology? A. AI B. Machine learning C. IoT D. Blockchain Cloud security is a difficult task, made all the more difficult by laws and regulations imposing restrictions on cross-border data transfers. The actual hardware in the cloud can be located anywhere, so it is critical to understand where your data resides. Which of the following statements is true in regards to responsibility of data? A. The cloud service customer retains ultimate responsibility for the data's security, regardless of whether cloud or non-cloud services are employed. B. The cloud service provider (CSP) retains ultimate responsibility for the data's security, regardless of whether cloud or non-cloud services are employed. C. Both the cloud service provider (CSP) and the cloud service customer (CSC) retain responsibility for the data's security, regardless of whether cloud or non-cloud services are employed. D. The cloud administrator retains ultimate responsibility for the data's security, regardless of whether cloud or non-cloud services are employed. The CSP will not permit your business to conduct an independent examination of cloud service controls, and has indicated that this role must be performed by an independent third party and the results provided to your organization. What type of cloud challenge is this? A. Resiliency B. Auditability C. Regulatory D. Governance The six-step cloud secure data life cycle starts with the creation of data and ends with: A. The destruction of data B. The sharing of data C. The use of data D. The archival of data A network engineer wants to move all of his organization's physical hardware to the cloud. This includes routers, switches, firewalls, and servers. He is looking for a service that will allow him to manage the operating systems of the servers and all of the applications that will be installed on the servers, but he no longer wants to have to manage any physical hardware. Which type of cloud provider would BEST fit this network engineer's needs? A. MaaS B. PaaS C. IaaS D. SaaS Of the following, which feature of cloud computing allows data to move between multiple cloud providers seamlessly? A. Interoperability B. Portability C. Auditability D. Resiliency Which of the following operates by consuming a large amount of data and analyzing that data for patterns? A. Artificial intelligence B. Internet of Things C. Block chain D. Machine learning Of the following, which is the MOST common and likely scenario to cause a vendor lock-in? A. Many proprietary requirements from the cloud provider B. Overly expensive hardware C. Undocumented software D. Poorly written SLAs The terms, "evaluation assurance level" (EAL), "protection profile" (PP), and "security assurance requirements" (SARs) are related to which of the following standards? A. PCI DSS B. Common Criteria C. NIST SP 800-53 D. FIPS 140-2 Which of the following is an example of the Internet of Things (IoT)? A. A computing device that can perform actions that it has not been programmed to do B. A computer with the capability to analyze data in a human-like manner C. An engineer using cryptography to link a list of records together D. A smart refrigerator that can send a grocery list to the owner via a push notification to their mobile phone Which of the following terms can be used to describe the process of overwriting erased data with arbitrary data and zero values as a method of data sanitation? A. Zeroing B. Cryptographic erasing C. Data hijacking D. Degaussing Which of the following is a security concern within an IaaS environment? A. Web application security B. Multitenancy C. System isolation D. Cross-site scripting Which of the following statements about the IaaS cloud service category is FALSE? A. IaaS customers can have metered usage, meaning they only pay for the resources they are using. B. IaaS can provide HA (high availability) functionality. C. IaaS is often less expensive than owning and maintaining physical hardware. D. IaaS does not provide much scalability. An attacker has managed to gain access to one of the file servers within an organization using a social engineering technique. Now that he has access to the file server, he has planted a backdoor so that he can return regularly and collect data without the organization knowing. He has had this access for several months and has stayed under the radar so that the organization can't detect him. What type of threat is being described here? A. Advanced persistent threat B. Malicious insider C. Account hijacking D. Denial of service In the cloud, what are the major cloud performance concerns? A. Virtualization B. Encryption and security C. Availability and bandwidth D. Identity and access Your organization has paid for cloud services, but when users seek to access them, the cloud services are unresponsive. The SLA requirements do not cover these repeated failures. What obstacles does the organization face? A. Interoperability B. Availability C. Portability D. Reversibility When data is used in an application where it is viewable to users, customers, etc., it is known as which stage of the cloud secure data life cycle? A. Archive B. Use C. Store D. Share Which organization officially defines cloud computing as "a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computer resources that can be rapidly provisioned and released with minimal management effort or service provider interaction"? A. ITIL B. NIST C. ISO D. TOGAF When data is being used by an application, it is referred to as: A. Data at rest B. Data in transit C. Unstructured data D. Structured data The mechanism that directs and controls the provisioning and use of cloud services both internally and externally is referred to as A. SLA B. Privacy C. Interoperability D. Governance An organization is alerted that a regulatory agency is initiating an investigation against it and the organization must suspend all relevant data destruction activities until the investigation has been fully resolved. What process is being described? A. Legal hold B. Non-repudiation C. Attribution D. Chain of custody Structured and unstructured storage pertain to which of the three cloud service models? A. PaaS B. DaaS C. IaaS D. SaaS Data that is easily searchable and organized within a database is known as: A. Structured data B. Uncorrelated data C. Unstructured data D. Correlated data Volume and object are storage types used in which cloud service model? A. PaaS B. DaaS C. IaaS D. SaaS Which cloud storage type operates as a web service call or as an API? A. Volume B. Object C. Unstructured D. Structured What is used to consolidate large amounts of structured data, often from desperate sources inside or outside the organization, with the goal of supporting business intelligence and analysis efforts? A. Data mart B. Data mining C. Data warehouse D. Data lake Cryptographic erasure is an example of: A. Data storage B. Data dispersion C. Data archival D. Data sanitation Brock is interested in implementing a SIEM. Which of the following is a function that Brock can expect from the SIEM? A. Backup data B. Block malware C. Reporting D. Encrypt data Masking, obfuscations, and anonymization are all techniques used in which of the following? A. Data mirroring B. Hashing C. Encryption D. Data de-identification What two organizational activities are reliant on identifying and mapping the location of data within an organization? A. Supply chain management and communications B. Antivirus and DLP C. Problem management and continuous improvement D. Asset Inventory and risk assessment Metadata is BEST described as: A. Data about data B. Location data C. Personally identifiable data D. Sensitive data In regard to data privacy, the security of the actual data is the responsibility of the cloud customer in which of the following cloud service models? A. All cloud service models B. SaaS only C. PaaS only D. IaaS only Data discovery can be described as which of the following? A. The practice of safeguarding encryption keys B. The method of using masking, obfuscation, or anonymization to protect sensitive data C. A set of controls and practices put in place to ensure that data is only accessible to those authorized to access it D. A business intelligence operation and user-driven process to look for patterns or specific attributes within data File level and storage level encryption methods are used to protect data in which state? A. Data in transit B. Data in motion C. Data at rest D. Data in use Data loss prevention (DLP) is made up of three common stages. Which of the following is the FIRST stage of DLP implementation? A. Enforcement B. Monitoring C. Discovery and classification D. Data de-identification There are two main types of storage in SaaS environments. Which SaaS storage type is the classic form of storing data within databases that the application uses and maintains? A. Content and file storage B. Object storage C. Information storage and management D. Volume storage Which of the following places controls on how protected health information must be handled in the United States? A. HIPAA B. PCI C. GDPR D. SOX An engineer is looking for a way to protect data in the share phase of the cloud data lifecycle. Which technology can be utilized to accomplish this? A. DAST B. BYOD C. TPM D. DLP During which phase of the cloud data lifecycle is data removed from being active or "hot" within the system to long term storage? A. Use phase B. Share phase C. Archive phase D. Destroy phase What is a cloud storage architecture that organizes data into fields based on the properties of individual data elements? A. File-based B. Object-based C. Database D. Raw-data Which of the following BEST describes the "create" phase of the cloud data lifecycle? A. Only when data first enters a system B. Only when data is newly created or newly imported into a system C. Only when data is modified into a new form D. Any time data is considered new What are the functions of substitution, shuffling, value variance, nullification, and encryption on data used for? A. DLP B. Obfuscation C. Discovery D. Tokenization The most common and well understood threat to storage is: A. Unauthorized access to data B. Accidental deletion of data C. Improper credential management D. Malware that modifies data The role of governance in regard to data stored in a cloud environment is the sole responsibility of who? A. Cloud provider B. Cloud auditor C. Cloud customer D. Cloud broker Data rights management (DRM) is a practice that is encapsulated within which concept? A. Supply chain management B. Interoperability and portability C. Information rights management D. Mobile security Michael needs to perform data destruction within a public cloud model. What method is Michael able to use? A. Incineration B. Degaussing C. Overwriting D. Shredding Your organization uses an IaaS cloud model and they need to select a storage mechanism that allows metadata tags. What would be the BEST option for your organization? A. Volume storage B. Block storage C. Object storage D. Blob storage Which phase of the cloud data lifecycle is the first phase in which security controls are implemented to protect data at rest? A. Use B. Create C. Store D. Destroy IRM is typically provisioned by the data owner. In what access model is the owner responsible for specifying metadata like classification rating and user role? A. Mandatory Access Control B. Rule-based Access Control C. Role-based Access Control D. Discretionary Access Control Data archiving and retention as it relates to official judicial or law enforcement requests is known as: A. Legal hold B. Regulatory hold C. Court archiving D. Law retention Your organization is considering using a data rights management solution that provides replication restrictions. Which of the following is the MOST accurate description of this functionality? A. Permissions can be modified after a document has been shared. B. Data is secure no matter where it is stored. C. Dates and time-limitations can be applied. D. The illicit or unauthorized copying of data is prohibited. Maxwell is developing a DLP strategy. Which of the following is NOT a component of DLP that Maxwell has to be concerned with? A. Discovery and classification B. Enforcement C. Evidence and custody D. Monitoring In regard to data sanitization, which type of cloud service model requires special considerations as the data is often more interconnected throughout the platform? A. SaaS B. IaaS C. DaaS D. PaaS Which of the following did the European Union (EU) officially implement in 2018? A. GDPR B. PCI DSS C. APEC D. HIPAA Any text, or binary data, that does not conform to a specific type of defined data structure or defined format can simply be classified as: A. Classified data B. Discovered data C. Structured data D. Unstructured data A breach occurred at a doctor's office in which information about a patient's medical history and treatment were stolen. What type of data has been stolen in this scenario? A. PCI B. PII C. PCD D. PHI Of the following, which is NOT one of the three data states? A. Data in use B. Data at rest C. Data in motion D. Data in encryption You're revising your organization's data destruction policy to guarantee that your cloud deployment is adequately protected. Which stage of the cloud data lifecycle will be impacted by this policy? A. All phases of the cloud data lifecycle. B. Store C. Destroy D. Create As you are drafting your organization's cloud data destruction policy, which of the following is NOT a consideration that may affect the policy? A. Retention requirements B. Compliance and governance C. Data discovery D. Business processes When is the MOST optimal time to determine if data is classified as secure? A. Use phase B. Create phase C. Store phase D. Archive phase Tokenization can BEST be described as: A. The practice of safeguarding encryption keys B. A set of controls and practices put in place to ensure that data is only accessible to individuals who are authorized to access it C. The practice of utilizing a random or opaque value in data to replace what would otherwise be sensitive data D. A method which involves transforming a string of characters into a fixed-length value or key that represents the original string Certain data will require more advanced security controls in addition to traditional security controls. This may include extra access controls lists placed on the data or having additional permission requirements to access the data. This extension of normal data protection is known as which of the following? A. Data rights management B. Threat and vulnerability management C. Identify access management D. Infrastructure and access management An engineer has been tasked with ensuring that only authorized systems and users have access to sensitive information. This is done using a set of controls to protect the data. What name is given to the set of controls that ensures data is only accessible by authorized users and systems? A. DLP B. API C. SLA D. SDN Emilia is a cloud security engineer. She needs to verify the integrity and completeness of data stored within a cloud environment. Which of the following technologies can help Emilia to ensure the integrity of data in a cloud environment? A. Mapping B. Obfuscation C. Hashing D. Metadata Having a proper mapping strategy will enable an organization to do which of the following? A. Easily group together data of similar types B. Know when data is modified within an application C. Classify data based on whether it is structured or unstructured D. Know all of the locations where data is present within its application DLP solutions that are implemented on the network perimeter, to capture traffic as it leaves the network, are used to protect data in which state? A. Data in storage B. Data in transit C. Data at rest D. Data in use During a cyber investigation, it is critical that any time evidence changes hands, it is documented. What is this process known as? A. Chain of custody B. Evidence correlation C. Non repudiation D. Evidence retention In traditional data centers, physical separation and segregation are used to secure data. However, these concepts are not possible in or applicable to cloud environments. With concepts like multitenancy and resource pooling at the forefront of cloud technologies, which of the following is used to keep data private? A. Antivirus B. Object storage C. Encryption D. BYOD The process of removing all identifiable characteristics from data is known as: A. Anonymization B. Obfuscation C. Hashing D. Masking Of the following, which is the MOST important to consider when setting minimum encryption levels and retention timelines? A. Storage requirements B. Security team size C. Regulatory requirements D. Budget What is used to consolidate large amounts of unstructured data, often from disparate sources inside or outside the organization, with the goal of supporting business intelligence and analysis efforts? A. Data mart B. Data mining C. Data warehouse D. Data lake The software as a service (SaaS) hosting model uses which of the following types of storage methods? A. Content and file storage B. Structured C. Object D. Volume Of the following, which is NOT a typical attribute of IRM implementations? A. Auditing B. Protection C. Policy control D. Deletion Regarding data privacy, different roles and responsibilities exist between the cloud customer and cloud provider. In a Platform as a Service environment, where does the responsibility fall for platform security? A. A third party is solely responsible B. Responsibility is shared between the cloud customer and the cloud provider C. The cloud provider is solely responsible D. The cloud customer is solely responsible Your organization is transitioning from one cloud service provider to another and is apprehensive that data will remain retrievable even after it has been requested to be destroyed. Which data disposal method is the BEST for ensuring data recovery is impossible? A. Crypto-shredding B. Mapping C. Clearing D. Anonymization What term is used to describe the business intelligence and user-driven process in which data is analyzed and represented visually in order to look for specific attributes and patterns within that data? A. Data discovery B. Data deduplication C. Data de-identification D. Data classification Client care representatives in your firm are now permitted to access and see customer accounts. For added protection, you'd like to build a feature that obscures a portion of the data when a customer support representative reviews a customer's account. What type of data protection is your firm attempting to implement? A. Masking B. Key management C. Hashing D. Tokenization Which of the following is NOT a feature that is provided by a typical SIEM solution? A. Alerting B. Reporting C. Web content filtering D. Correlation Which storage medium is commonly utilized for processing? A. Long-term B. Raw-disk C. RAID D. Ephermeral An organization utilized data event logging recommendations by OWASP in their cloud auditing plan. Which of the following is NOT a recommendation? A. Network traffic logs B. Differing classification schemes C. Time synchronization D. Identity attribution IRM can be used as a means for: A. Data classification and data deletion B. Data control and data modification C. Data modification and data deletion D. Data classification and control A cloud provider has its customer's data distributed throughout numerous data centers worldwide for the purpose of disaster recovery. What is the name of this process? A. Data sanitization B. Cloud distribution C. Community cloud D. Data dispersion Data dispersal in cloud settings can have a mixed effect on an organization's security. What are the disadvantages of data dispersion? A. Availability of data B. Reconstruction of data C. Erasure coding of data D. Relocation of data An engineer needs to find out when a document was originally created. What could this engineer look at to find this information? A. Sanitized data B. Metadata C. Data maps D. Data tags Which storage type uses a virtual hard drive that is attached to the virtual host? A. Volume B. Structured C. Unstructured D. Object Of the following, which is an example of a direct identifier within PII? A. Birth date B. Zip code C. Gender D. National identification number Of the following, which is NOT one of the three ways to implement key storage in a cloud environment? A. Having the keys stored on a dedicated host server in the same network but which is separate from the where the encryption service is housed B. Having the keys stored and accessed within the same virtual machine as the encryption service or engine C. Having an external and independent service or system host the key storage D. Creating a physical copy of the encryption keys and storing them in a physical safe The BEST time to classify data is in which phase of the data lifecycle? A. Archive B. Create C. Use D. Store A cloud engineer is interested in grouping data elements of similar types together. This would allow her to quickly locate similar data in the future and compare it. Which technology could the cloud engineer use to accomplish this task? A. Hashing B. Metadata C. Labeling D. Encryption An engineer is working with data that is in the store phase of the cloud data lifecycle. Now that the data is in the store phase, what must the engineer immediately employ on top of security controls? A. Data classification B. Backup methods C. Sharing permissions D. Data destruction methods You're revising your organization's data retention policy to guarantee that your cloud deployment is adequately protected. Which stage of the cloud data lifecycle will be impacted by this policy? A. Use B. Archive C. Store D. Destroy Tracking file modifications is imperative when it comes to data security strategies. What can be used to ensure the integrity of data? A. Tokenization B. Obfuscation C. Hashing D. DLP In a cloud environment, security of the physical equipment becomes the sole responsibility of which of the following? A. Cloud broker B. Cloud customer C. Cloud auditor D. Cloud provider Of the following, which term describes the "slices" of the main storage infrastructure which are then allocated virtual machines in volume storage? A. RAM B. RAID C. CPU D. LUNs A person's birth date is an example of what type of PII? A. Direct identifier B. Nondescript identifier C. Descript identifier D. Indirect identifier Data loss prevention (DLP) is BEST described as: A. A set of controls and practices put in place to ensure that data is only accessible to those authorized to access it B. The practice of safeguarding encryption keys C. The practice of utilizing a random or opaque value to replace what would otherwise be sensitive data D. The method of using masking, obfuscation, or anonymization to protect sensitive data The purpose of labeling data is to accomplish which of the following? A. Know all of the locations within an organization where data could be stored B. Group data elements together and provide information about those elements C. Classify data based on where it's located within the organization D. Protect data that can be considered sensitive or classified Due to the volume of log data generated by systems, it poses a challenge for organizations when performing log reviews. What can an organization implement to help solve this issue? A. DLP B. SIEM C. IDS/IPS D. Next-generation firewall The data technique by which data dispersion encrypts data along with parity bits is referred to as: A. Hashing B. Erasure coding C. RAID D. Data encoding What form of storage is used when content is saved in object storage and then dispersed to multiple geographical hosts to increase internet consumption speed? A. SAN B. SDS C. CDN D. SDN Data loss prevention (DLP) is comprised of three major components including discovery and classification, enforcement, and which of the following? A. Data de-identification B. Data leakage C. Encryption D. Monitoring Data that can't be easily used in a formatted database is known as: A. Correlated data B. Structured data C. Unstructured data D. Uncorrelated data A data leak is MOST LIKELY to occur during which phase of the cloud data lifecycle? A. Destroy B. Archive C. Store D. Use Your organization is considering using a data rights management solution that provides persistent protection. Which of the following is the MOST accurate description of this functionality? A. Permissions can be modified after a document has been shared. B. Data is secure no matter where it is stored. C. The illicit or unauthorized copying of data is prohibited. D. Dates and time-limitations can be applied. Jada is currently vetting the tokenization process of her organization's cloud provider. What is one risk that Jada should ensure is limited during the tokenization process? A. SLA modifications B. File type changes C. Price changes D. Vendor lock-in Which emerging technology, that is still in the early phases of development, would allow for the manipulation of encrypted data without the need to unencrypt it? A. Labeling B. Tokenization C. Homomorphic encryption D. Data de-identification Hashing can be used to do which of the following? A. Quickly ensure the integrity of data which is spread throughout multiple storage locations B. Group multiple data objects of the same type together so that they can be easily found later C. Encrypt data so that it can only be viewed by authorized individuals D. Determine the origin and location of a data object In the cloud, data is frequently stored in order to be recovered later, if necessary. Which section of a data retention policy would outline the steps involved in this process? A. Archiving and retrieval procedures B. Retention Periods C. Data classification D. Retention formats An engineer has implemented data loss prevention solutions that are installed on each of the systems which house and store data. This includes any servers, workstations, and mobile devices which hold data. These DLP solutions are used to protect data in which state? A. Data in motion B. Data in use C. Data in transit D. Data at rest A social security number is which type of PII? A. Nondescript identifier B. Descript identifier C. Direct identifier D. Indirect identifier A security incident occurred within an organization that affected numerous servers and network devices. A security engineer was able to use the SIEM to see all of the logs pertaining to that event, even though they occurred on different devices, by using the IP address of the source. Which function of a SIEM is being described in this scenario? A. Correlation B. Compliance C. Aggregation D. Reporting Select the correct order of the cloud data lifecycle. A. Create, store, use, share, archive, destroy B. Create, share, use, store, archive, destroy C. Create, use, archive, store, share, destroy D. Create, use, store, share, archive, destroy Jonathan is responsible for creating a cloud data archiving strategy. Which of the following must Jonathan take into consideration when creating the strategy? A. Amount B. Size C. Format D. Classification An organization implemented a data rights management program. The cloud security specialist has been tasked with the responsibility of ensuring an in-depth report on the usage and access history that can be generated for all files. Which of the following BEST represents this functionality? A. Continuous auditing B. Persistant protection C. Rights revocation D. Replication restrictions Which of the following is NOT considered PHI? A. Medical history B. Demographic information C. Lab results D. Passport number During which phase of the cloud data lifecycle would data undergo overwriting? A. Use B. Archive C. Destroy D. Store In an IaaS environment, who allocates and maintains storage? A. Cloud broker B. Cloud customer C. Cloud auditor D. Cloud provider How many layers of encryption are typically used on database storage systems? A. One layer B. Two layers C. Three layers D. Four layers The MOST common form of structured data is found within: A. Relational databases B. File servers C. Emails D. Pictures Which of the following can data masking NOT be used for? A. Remote access B. Least privilege C. Authentication D. Sandbox environment [Show More]
Last updated: 1 year ago
Preview 1 out of 36 pages

Reviews( 0 )
Recommended For You
*NURSING> QUESTIONS & ANSWERS > Brownie Recipe 2 Week 3- Week 7. Plus Quiz 1-6, ATI Adv. Med-surg FINAL EXAM, 600 Questions and Answers. (All)

Brownie Recipe 2 Week 3- Week 7. Plus Quiz 1-6, ATI Adv. Med-surg FINAL EXAM, 600 Questions and Answers.
SAMPLES: WEEK 3 1. Consequence of too much O2 → dry & cracking oral mucosa 2. PE s/sx → petechiae, pleural rub, tachycardia (not bradycardia, hypertension) 3. 1 day post surgery (thoracotom...
By Kirsch , Uploaded: Mar 17, 2022
$10
*NURSING> QUESTIONS & ANSWERS > NCSBN TEST BANK for the NCLEX-RN & NCLEX-PN. Contains More than 2000 Q&A Plus Review and Rationale in 517 PAGES. (All)
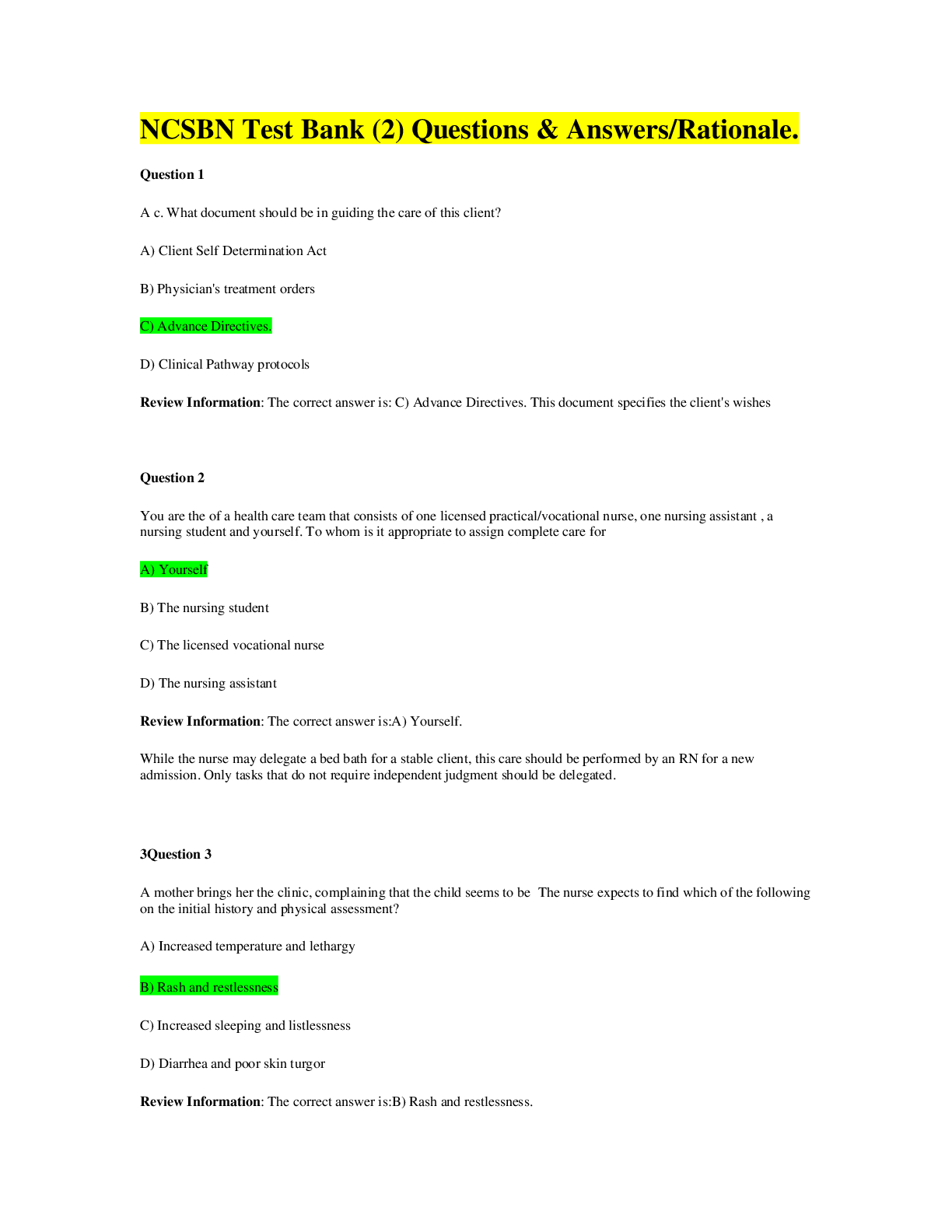
NCSBN TEST BANK for the NCLEX-RN & NCLEX-PN. Contains More than 2000 Q&A Plus Review and Rationale in 517 PAGES.
NCSBN TEST BANK -for the NCLEX-RN & NCLEX-PN. Updated 2022/2023. Contains More than 2000 Q&A Plus Review and Rationale in 517 PAGES. (All Testable Questions for NCLEX-RN & NCLEX-PN)
By Expert1 , Uploaded: Jul 28, 2020
$20
Business> QUESTIONS & ANSWERS > CLM 031 EXAM (All)

CLM 031 EXAM
CLM 031 = 100% Question 1: 5b Select the statement that is correct concerning performance work statement (PWS) requirements: - All answers are correct. - PWS should describe requirements necessary...
By Book Worm, Certified , Uploaded: Nov 03, 2022
$5
*NURSING> QUESTIONS & ANSWERS > PHIL 347 Week 6 Checkpoint Quiz. Score 100/100 (All)
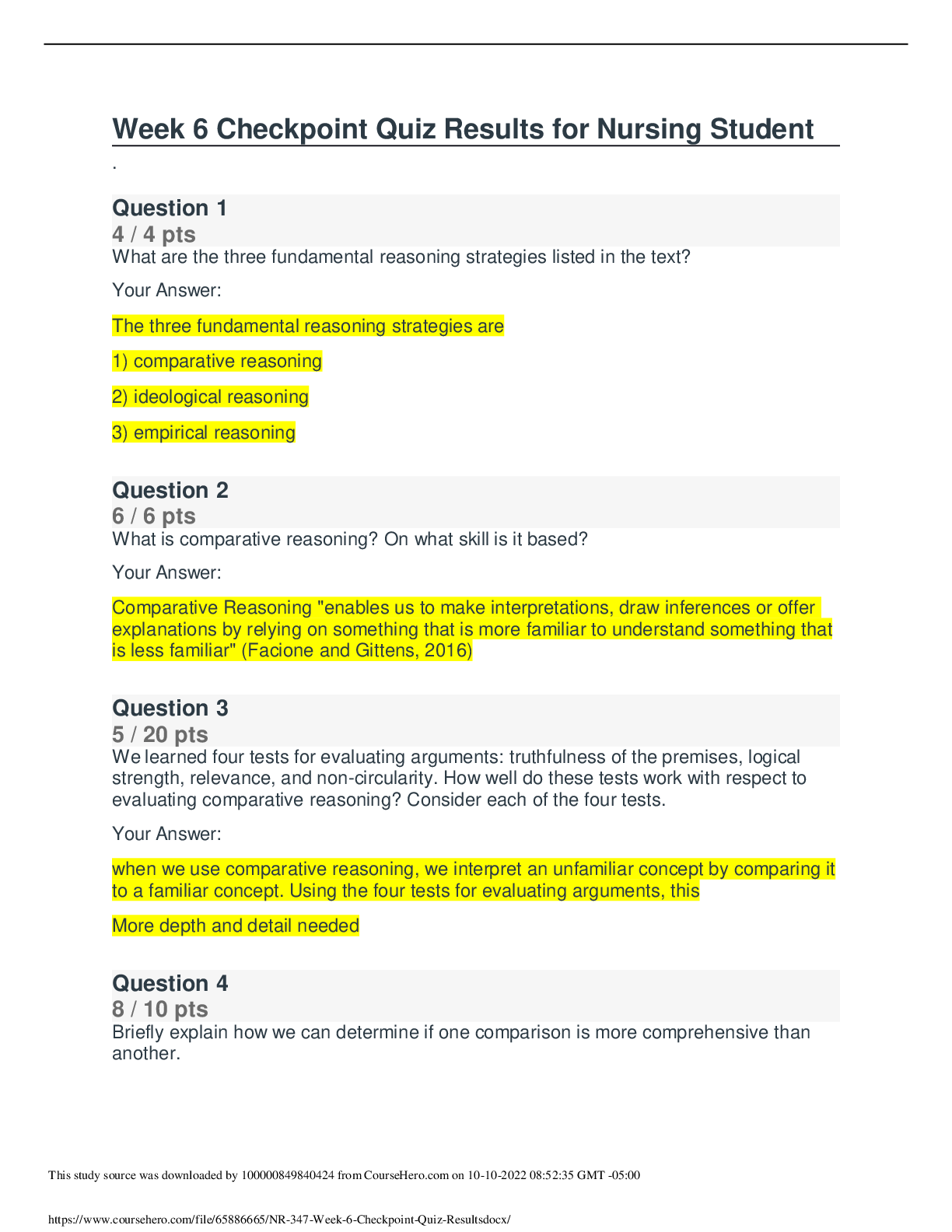
PHIL 347 Week 6 Checkpoint Quiz. Score 100/100
Question: What are the three fundamental reasoning strategies listed in the text? Question: What is comparative reasoning? On what skill is it based? Question: We learned four tests for evaluating...
By Amanda Rosales , Uploaded: Mar 24, 2021
$7
Business> QUESTIONS & ANSWERS > BUSINESS 1007 (All)
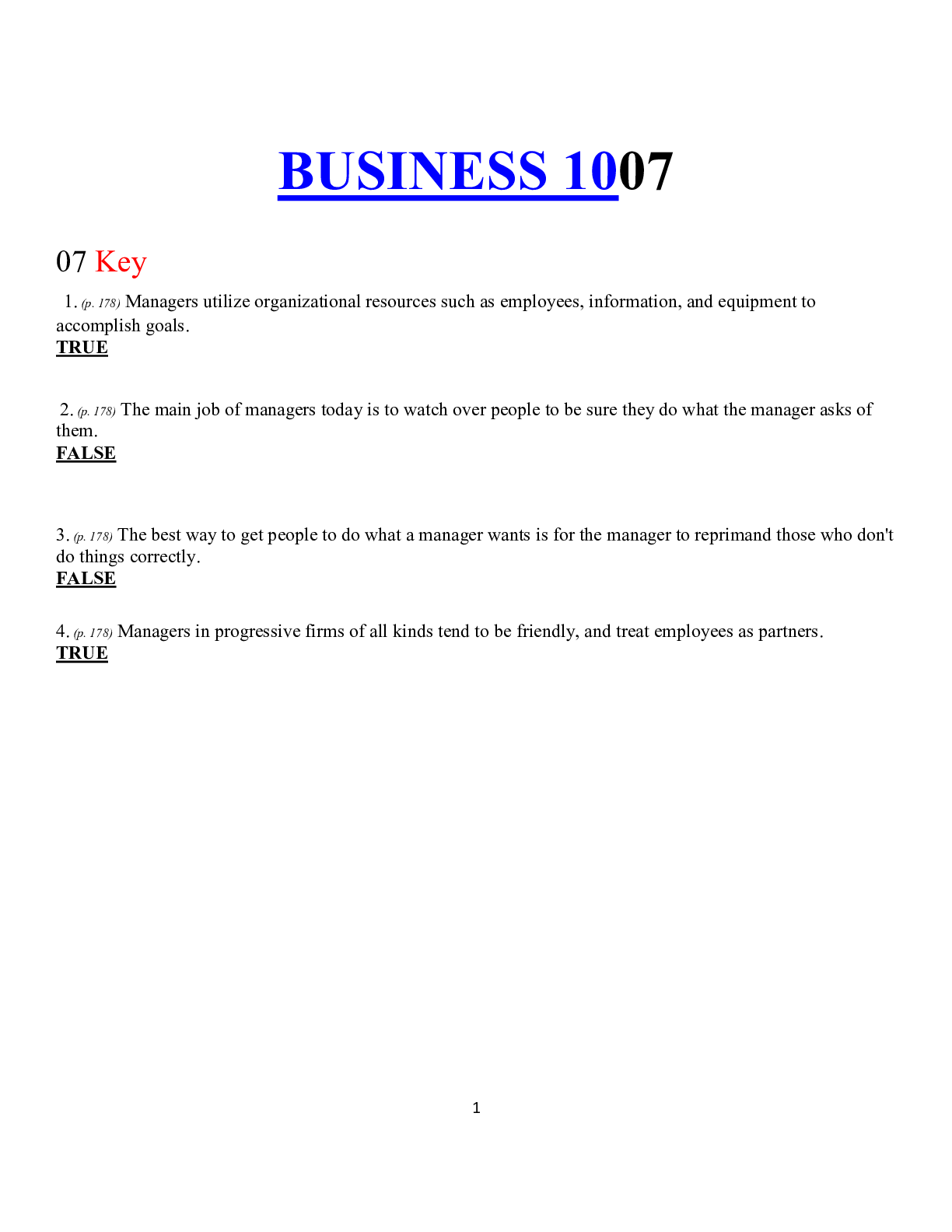
BUSINESS 1007
BUSINESS 1007 07 Key 1. (p. 178) Managers utilize organizational resources such as employees, information, and equipment to accomplish goals. 2. (p. 178) The main job of managers today is to w...
By Kirsch , Uploaded: Oct 19, 2019
$6
Anthropology> QUESTIONS & ANSWERS > KOR 352 FA19 101 week 8 Quiz. Already Graded A (All)

KOR 352 FA19 101 week 8 Quiz. Already Graded A
KOR 352 FA19 101: Week 8 Quiz Question 1 (0.25 points) Which of the following is not true of Kim and Finch’s observations during their field research in South Korea from 1997 to 2000? Question 1 o...
By Kirsch , Uploaded: Oct 17, 2019
$9
E-Commerce> QUESTIONS & ANSWERS > ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score (All)
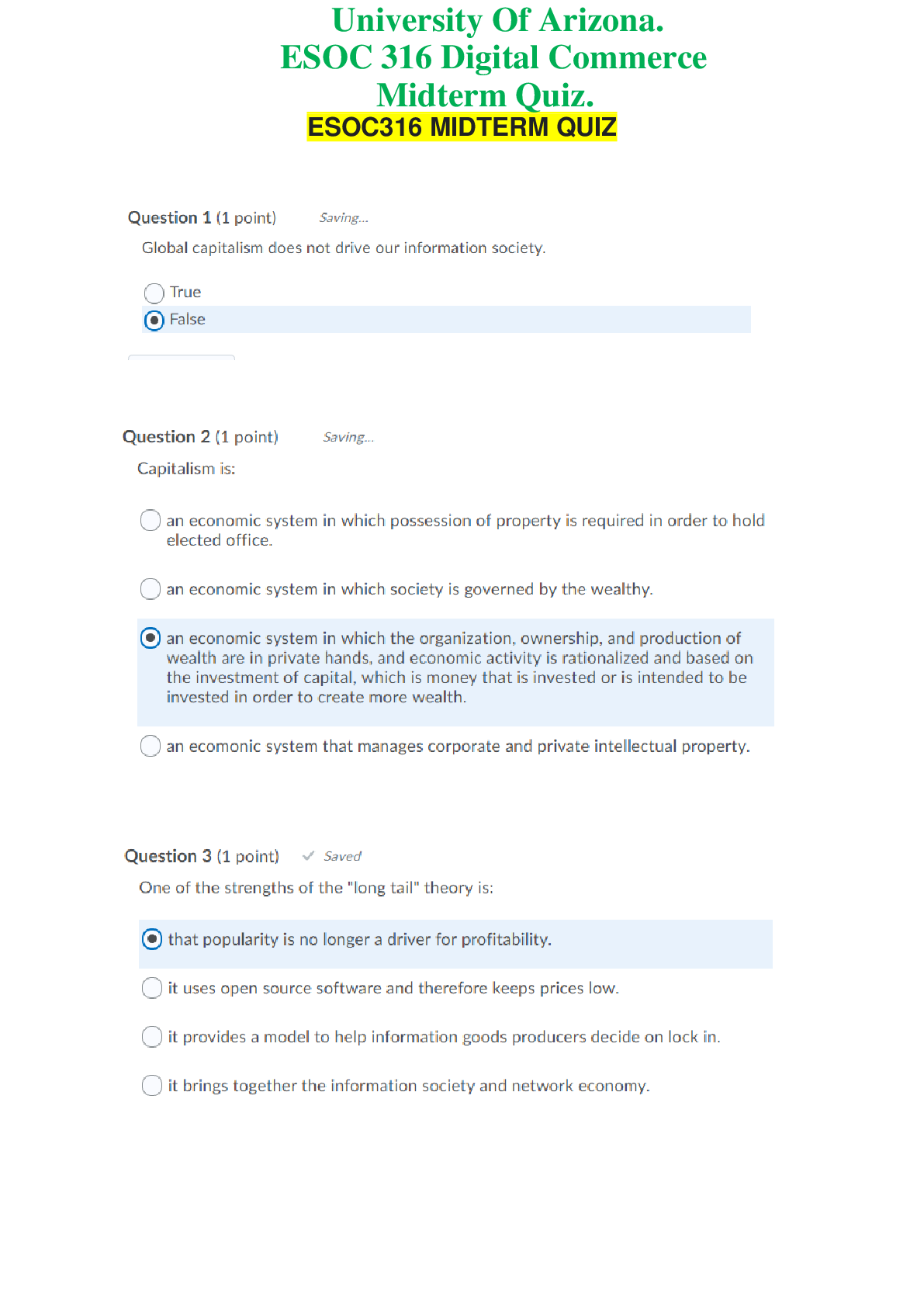
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score ESOC316 MIDTERM QUIZQuestion 6 (1 point) Saved Information has several properties that make information goods...
By Kirsch , Uploaded: Oct 15, 2019
$9.5
Marketing> QUESTIONS & ANSWERS > Marketing Management Chapter 2 to Chapter 10 Q&A (All)

Marketing Management Chapter 2 to Chapter 10 Q&A
Chapter 2 to Chapter 10 Chapter 2: Developing Marketing Strategies and Plans GENERAL CONCEPT QUESTIONS Multiple Choice 66 Chapter 1: Marketing: Managing Profitable Customer Relationships...
By Kirsch , Uploaded: Oct 14, 2019
$10
Marketing> QUESTIONS & ANSWERS > MKT 530 Customer Relationship Management. 155 Questions and Answers (All)

MKT 530 Customer Relationship Management. 155 Questions and Answers
MKT 530 All Questions and Answers MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) As the manager of an organization that is att...
By Kirsch , Uploaded: Oct 14, 2019
$10
Art> QUESTIONS & ANSWERS > MAS 337 Exam 1. Graded A (All)

MAS 337 Exam 1. Graded A
MAS 337 Exam 1 Match the son with its corresponding region. 1.Oaxaca 2.Veracruz 3.Michoacan 4.Jalisco 5.Hidalgo 1. Son istemeno 2. Son Jarocho 3. Son Abajeno 4. Son Jalisciense 5. Son Huast...
By Kirsch , Uploaded: Oct 14, 2019
$6
Document information
Connected school, study & course
About the document
Uploaded On
Jul 24, 2022
Number of pages
36
Written in
Additional information
This document has been written for:
Uploaded
Jul 24, 2022
Downloads
0
Views
58






