Computer Networking > EXAM > (answered 2022/2023) Palo Alto PCNSE NGFW Questions Exam (All)
(answered 2022/2023) Palo Alto PCNSE NGFW Questions Exam
Document Content and Description Below
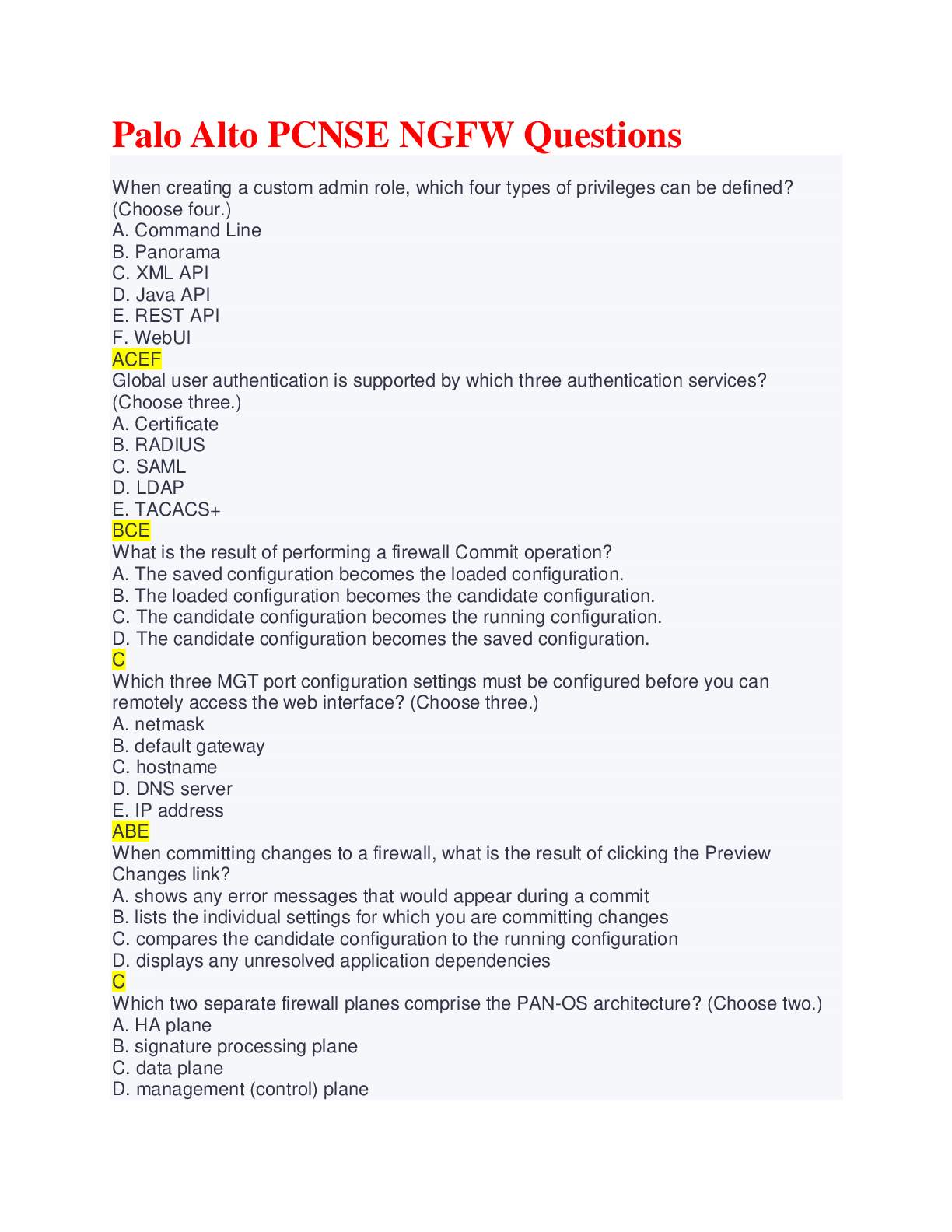
Palo Alto PCNSE NGFW Questions & Answers Latest fall 2022/2023. When creating a custom admin role, which four types of privileges can be defined? (Choose four.) A. Command Line B. Panorama C. XM... L API D. Java API E. REST API F. WebUI Global user authentication is supported by which three authentication services? (Choose three.) A. Certificate B. RADIUS C. SAML D. LDAP E. TACACS+ What is the result of performing a firewall Commit operation? A. The saved configuration becomes the loaded configuration. B. The loaded configuration becomes the candidate configuration. C. The candidate configuration becomes the running configuration. D. The candidate configuration becomes the saved configuration. "correct answer" - C Which three MGT port configuration settings must be configured before you can remotely access the web interface? (Choose three.) A. netmask B. default gateway C. hostname D. DNS server E. IP address When committing changes to a firewall, what is the result of clicking the Preview Changes link? A. shows any error messages that would appear during a commit B. lists the individual settings for which you are committing changes C. compares the candidate configuration to the running configuration D. displays any unresolved application dependencies Which two separate firewall planes comprise the PAN-OS architecture? (Choose two.) A. HA plane B. signature processing plane C. data plane D. management (control) plane E. routing plane Which two statements are true regarding the candidate configuration? (Choose two.) A. It controls the current operation of the firewall. B. It always contains the factory default configuration. C. It contains possible changes to the current configuration. D. It can be reverted to the current configuration. Which object cannot be segmented using virtual systems on a firewall? A. network security zone B. data plane interface C. administrative access D. MGT interface The Palo Alto Networks Cybersecurity Portfolio focuses on which three principle technologies? (Choose three.) A. securing the cloud B. securing operations response C. securing third-party application access D. securing the enterprise E. securing the internet of things What are the two attributes of the dedicated out-of-band network management port in Palo Alto Networks firewalls? (Choose two.) A. supports only SSH connections B. labeled MGT by default C. requires a static, non-DHCP network configuration D. cannot be configured as a standard traffic port True or false? To register a hardware firewall, you will need the firewall's serial number. A. true B. false n the web interface, what is signified when a text box is highlighted in red? A. The value in the text box is required. B. The value in the text box is controlled by Panorama. C. The value in the text box is optional. D. The value in the text box is an error. True or false? Service routes can be used to configure an in-band port to access external services. A. true B. false True or false? The running configuration consists of configuration changes in progress but not active on the firewall. A. true B. false True or false? Server Profiles define connections that the firewall can make to external servers. A. true B. false True or false? Certificate-based authentication replaces all other forms of either local or external authentication. A. true B. false Which two activities are part of the cyberattack lifecycle reconnaissance stage? (Choose two.) A. port scans B. social engineering C. RAT installation D. establish C2 At which packet flow stage does the firewall detect and block pre-session reconnaissance and DoS attacks? A. application identification B. content inspection C. ingress D. slowpath True or false? A Layer 3 interface can be configured as dual stack with both IPv4 and IPv6 addresses. A. true B. false Which protection method can be used to mitigate single-session DoS attacks? A. DoS Protection policy B. packet buffer protection C. Zone Protection Profile D. DoS Protection Profile True or false? DoS Protection policy is applied to session traffic before a Zone Protection Profile. A. true B. false Which type of protection is provided by both a Zone Protection Profile and a DoS Protection Profile? A. packet-based and protocol-based B. session limits C. reconnaissance D. flood Which firewall configuration component is used to block access to known-bad IP addresses? A. NAT policy B. IP Security Profile C. Security policy D. Vulnerability Protection Profile In which three locations can you configure the firewall to use an EDL? (Choose three.) A. DoS Protection Profile B. URL Filtering Profile C. Antivirus Profile D. Anti-Spyware Profile E. Security policy In which firewall configuration component can you use an EDL of type Domain List? A. Antivirus Profile B. Security policy C. Anti-Spyware Profile D. URL Filtering Profile True or false? A best practice is to enable the "sinkhole" action in an Anti-Spyware Profile. A. true B. false True or false? When migration is done from the firewall of another vendor to a Palo Alto Networks firewall, a best practice is to always migrate the existing Security policy. A. true B. false True or false? If App-ID cannot identify the traffic, Content-ID cannot inspect the traffic for malware. A. true B. false Which item is the name of an object that dynamically identifies and associates applications based on application attributes that you define: Category, Subcategory, Technology, Risk, and Characteristic? A. application B. application profile C. application filter D. application group Before App-ID would identify traffic as facebook-base, it would first identify the traffic as which application? A. web-browsing B. ssl C. unknown-udp D. unknown-tcp When are brand-new application signatures released by Palo Alto Networks? A. once per month B. as soon as possible C. with each PAN-OS software update D. once per week What triggers Security policy rule match in the Policy Optimizer's No App Specified window? A. "any" in the Application column B. "Allow" in the Action column C. "unknown" in the Application column D. "application-default" in the Service column True or false? Content-ID inspection is possible for a custom application only if you define a Parent App for the custom application and the Parent App is a non-custom App-ID application. A. true B. false True or false? You must define a custom signature for a custom application that is identified by an Application Override rule. A. true B. false True or false? Content-ID inspection is possible for custom application traffic that is identified by an Application Override rule, but only if the custom application's Parent App is based on a non-custom application. A. true B. false Which file type can a firewall send to WildFire when the firewall does not have a WildFire subscription? A. JAR B. APK C. PDF D. EXE Which WildFire verdict might indicate obtrusive behavior but not a security threat? A. Phishing B. Grayware C. Benign D. Malware "correct answer" True or false? When a malicious file or link is detected in an email, WildFire can update antivirus signatures in the PAN-DB database. A. true B. false Which two types of activities does SSL/TLS decryption by the firewall help to block? (Choose two.) A. protocol-based attacks B. sensitive data exfiltration C. malware introduction D. denial-of-service attacks True or false? If OCSP and CRL are configured on a firewall, CRL is consulted first. A. true B. false "correct answer" True or false? The firewall still can check for expired or untrusted certificates even if the SSL traffic is not being decrypted. A. true B. false True or false? The SSL forward untrust certificate should not be trusted by the client but should still be a CA certificate. A. true B. false Which two items are encrypted using the firewall master key? (Choose two.) A. local user passwords B. public key C. private key D. digital certificates True or false? The Antivirus, Anti-Spyware, and Vulnerability Protection profiles use signatures received in content updates to detect malware in allowed traffic. A. true B. false Sinkhole events are recorded in which log? A. URL Filtering B. Data Filtering C. Threat D. WildFire Submissions In a Data Filtering profile, which three types of numbers are included in the predefined patterns? (Choose three.) A. driver's license B. passport C. bank routing D. Social Security E. credit card True or false? Data Filtering profile packet captures are prohibited unless you configure a data protection password. A. true B. false Which three configuration tasks for Device-ID are performed at the firewall? (Choose three.) A. Activate the Cortex Data Lake instance. B. Enable Device-ID per zone. C. Configure a Log Forwarding Profile. D. Enable EALs. E. Activate the IoT Security app. Which two Palo Alto Networks subscriptions services are required for IoT security? (Choose two.) A. Cortex Data Lake B. Cortex XDR C. Device Security D. IoT Security Which three log files can you add columns to view the metadata for source and destination devices? (Choose three.) A. Traffic B. GlobalProtect C. URL Filtering D. User-ID E. Decryption A policy rule recommendation first must be activated in the IoT Security app before it can be imported into the firewall. A. true B. false You should activate your Cortex Data Lake subscription before you activate your IoT subscription. A. true B. false All firewall platforms running PAN-OS 10.0 support enforcement of IoT Security policy. A. true B. false Which user mapping method is recommended for a high-security environment? A. GlobalProtect B. Client Probing C. Server Monitoring D. Session Monitoring Which authentication method is not a local authentication method? A. local user database authentication B. local authentication without a database C. local certificate authority D. local domain authentication Which four secondary authentication vendors are supported by the firewall? (Choose four.) A. Vasco Identikey B. Duo v2 C. Okta Adaptive D. PingID E. RSA SecurID Access Which two statements are true regarding User-ID and firewall configuration? (Choose two.) A. The User-ID agent must be installed on the domain controller. B. Communications between the firewall and the User-ID agent are sent over an encrypted SSL connection. C. The firewall needs to have information for every User-ID agent to which it will connect. D. NetBIOS is the only client probing method supported by the User-ID agent. Which three items are valid choices when the Source User field is configured in a Security policy rule? (Choose three.) A. unknown B. none C. known-user D. all E. any True or false? You must deploy the Windows-based User-ID agent to collect IP address-to-username mappings from a Windows AD domain controller. A. true B. false Which statement is true regarding User-ID and Security policy rules? A. The Source IP and Source User fields cannot be used in the same policy. B. Users can be used in policy rules only if they are known by the firewall. C. The Source User field can match only users, not groups. D. If the user associated with an IP address cannot be determined, all traffic from that address will be dropped. Which two port numbers would be used when an LDAP Server Profile is configured? (Choose two.) A. 49 B. 1812 C. 636 D. 389 Firewall evaluation of the configuration of which object is optional during the external authentication process? A. Authentication Profile B. authentication enforcement object C. Authentication Sequence D. Authentication policy When you are configuring domain credential filtering, the User-ID agent should be installed on which type of Active Directory server? A. Global Catalog Server B. PDC Emulator C. read-only domain controller D. Member Server Which two firewall objects can be configured to forward firewall logs to external destinations? (Choose two.) A. security zone B. network interface C. Security policy rule D. Application Override rule Which two actions affect all of the widgets in the Application Command Center? (Choose two.) A. setting a local filter B. setting a global filter C. selecting a time range D. setting a global search Which two firewall features display information using widgets? (Choose two.) A. Dashboard B. ACC C. botnet report D. Traffic log You can customize the list of logs that are aggregated into the Unified log. A. true B. false Which three statements about the automated correlation engine are correct? (Choose three.) A. It uses correlation objects as input. B. It is available only in Panorama. C. It detects possible infected hosts. D. It outputs correlation events. E. It requires Cortex Data Lake. SNMP GET requests to a firewall return operational statistics, and SNMP SET requests update the firewall configuration. A. true B. false Which three statements about the predefined reports are correct? (Choose three.) A. They are generated daily by default. B. They are emailed daily to users. C. They are customizable. D. There are more than 40 predefined reports. E. They are grouped in five categories. Which step of the cyberattack lifecycle is used by an attacker to carefully plan their attacks? A. reconnaissance B. weaponization C. delivery D. exploitation Which typical application use can be a gray area on whether the application should be enabled or blocked? A. sanctioned B. tolerated C. unsanctioned What is the application database that Palo Alto Networks uses along with App-ID to identify applications? A. appid.com B. applipedia.com C. cyberpedia.com D. SaaS-apps.com Which tool provides a simple workflow to migrate your legacy or port-based Security policy rulebase to an App-ID-based rulebase? A. Policy Optimizer B. Expedition C. Best Practice Assessment D. IronSkillet Which tool enables you to migrate existing rules from a legacy firewall to a Palo Alto Networks Next-Generation Firewall? A. Policy Optimizer B. Expedition C. Best Practice Assessment D. IronSkillet Which phase of the migration process would you use to add application-based rules above the corresponding port-based rules? A. Phase 1 B. Phase 2 C. Phase 3 D. Phase 4 Which VM-Series firewall does NOT currently support Device-ID? A. VM-50 B. VM-100 C. VM-300 D. VM-500 True or false? The IoT Security app approach starts by identifying and classifying the devices in your network. A. True B. False Which Level of Device Classification classifies the device based on the vendor and model? A. First Level B. Second Level C. Third Level D. Fourth Level Which policy configuration can an administrator enable to allow Cisco VoIP devices to access only the required applications? A. Control the attack surface B. Decrypt based on device C. Track a device across the network D. Allow access based on device identity Which Level of Device Classification identifies the industry in which the device operates? A. First Level B. Second Level C. Third Level D. Fourth Level Organizations that have not enabled User-ID for visibility create Security policies based on which of the following? A. port B. protocol C. IP address D. MAC address True or false? User-ID enables security teams to define policy rules on firewalls to safely enable applications and control access based on users or groups of users. A. True B. False At which step of the User-ID roadmap would you employ a IP-to-user mapping strategy? A. Understand your environment B. Identify IP-user mapping strategies for visibility C. Implement user visibility D. Implement identity-based policies What could a SOC analyst use to trigger selective actions on the firewall that will be enforced immediately? A. Zero Trust B. identity-based policies C. dynamic user groups D. multi-factor authentication What is the maximum number of agents that you can add for data redistribution? A. 10 B. 50 C. 100 D. 250 What percentage of malware campaigns are expected to use some type of encryption? A. 60 percent B. 70 percent C. 85 percent D. 95 percent True or false? Data Loss and Compliance checks stop the loss of sensitive data such as personally identifiable information (PII) and intellectual property (IP). A. True B. False Which of the following identifies and prevents corporate computer and internet usage policy violations? A. Threat B. Inside Behavior C. Phishing and Credential Attacks D. Data Loss and Compliance Check Which time frame within the decryption rollout is considered the most critical and is the time when you eliminate most problems and move to your user base? A. days 0-30 B. days 30-90 C. days 90-180 D. days 180-240 Which protocol offers improved security, performance, and privacy benefits over the previous versions? A. TLS 1.2 B. TLS 1.3 C. SSL 3.0 D. PCT 1.0 The Cloud Identity Engine allows you to write Security policy based on which two things? A. users and groups B. users and privileges C. domain and access D. priority and level The Cloud Identity Engine provides Palo Alto Networks apps and services with which type of access to your directory information for user visibility and policy enforcement? A. write B. edit-only C. administrative D. read-only To authenticate users, what do Google, Azure and Okta need configured in the Cloud Identity Engine? A. a SAML 2.0-based identity provider (IdP) B. an on-prem Active Directory C. Security policies D. user-to-IP mappings When you configure to activate Cloud Identity Engine, what required information do you need to provide? (Choose three.) A. Company account B. Name C. Description D. Region E. Zone To collect attributes from your Active Directory and synchronize them with the Cloud Identity Engine, which three versions of TLS encryption is supported? (Choose three.) A. TLS 1.0 B. TLS 1.1 C. TLS 1.2 D. TLS 1.3 E. TLS 1.4 True or false? You do not need to install or configure a Cloud Identity agent to collect attributes from a cloud-based directory. A. True B. False To set up the Cloud Identity Engine, which two required tasks will you need to perform? (Choose two.) A. Log in to the Cloud Identity Engine app on the hub to generate a certificate to authenticate the agent and the Cloud Identity Engine. B. Associate the Cloud Identity Engine with Palo Alto Networks apps to select which apps can use your directory information. C. Restart PAN-OS to force a reboot. D. Register your cloud-identity security service with the technical assistance center (TAC). The Cloud Identity Engine allows you to write security policy based on which two of the following? (Choose two.) A. IP addresses B. users C. groups D. IP/port pairs The components of the Cloud Identity Engine deployment vary based on which two of the following factors? (Choose two.) A. whether the Cloud Identity Engine is accessing an on-premises directory (Active Directory) B. whether the Cloud Identity Engine is accessing a cloud-based directory (Azure Active Directory) C. whether the number of IdPs exceeds 100 D. whether the number of user groups exceeds 10,000 Which two actions do you need to perform to use the Cloud Identity Engine with an on-premises Active Directory? (Choose two.) A. Install the Cloud Identity agent on a Windows server (the agent host) and configure it to connect to your Active Directory and the Cloud Identity Engine. B. Access the Cloud Identity Engine app on the hub so you can manage your Cloud Identity Engine instances and Cloud Identity agents. C. Map your user IP addresses to user groups. D. Set your system clock to the GMT time zone. Which three of the following are challenges enterprises face in verifying users and enforcing identity-based security? (Choose three.) A. Fragmentation of identities, and difficulty in ensuring consistent application of identity-based security controls, has created a significant barrier to adopting Zero Trust. B. Setting up on-prem IdPs provides the necessary network security capabilities to achieve Zero Trust. C. Integration of APIs for end-user authentication through authentication policies. D. Configuring, maintaining, and synchronizing network security with multiple IdPs can be time-consuming and resource-intensive. E. Adding administrative users and configuring network access lists. Which two of the following statements about the Cloud Identity Engine are true? (Choose two.) A. It simplifies Zero Trust with easy-to-deploy user identity and access across all locations. B. It is a cloud-native identity synchronization and authentication service—providing a single secure user identity across Palo Alto Networks on-prem and cloud product lines. C. It authenticates and authorizes all users and computers in a Windows domain type network. D. It is a secure identity cloud that links all your apps, logins, and devices into a unified digital fabric. Palo Alto Networks was the first next-generation firewall vendor to enable identity-based security by A. referencing users' IP addresses. B. leveraging user-based policies. C. blocking abnormal user behavior. D. using group information to grant individual permissions. True or false? Identity providers (IdPs) are typically cloud-hosted services and often operate with single sign-on (SSO) providers to authenticate users. A. true B. false True or false? Authentication policy enables you to authenticate end users before they can access services and applications. A. true B. false The Cloud Identity Engine empowers organizations to move toward Zero Trust by enabling them to do which two of the following? (Choose two.) A. Consistently authenticate and authorize their users when in central locations. B. Accurately enforce security decisions for all their users at all times, with assured synchronization of all identity-related data in the cloud. C. Accelerate their transition to cloud-based identity, knowing that their network security infrastructure never needs to be updated. D. Save time in deployment and management of identity-based controls on their network security infrastructure. Sharing of on-prem Active Directory (AD) groups to other branches via the Cloud offers which two benefits? (Choose two.) A. Enables customers to download groups and users from their on-prem AD to other branches via cloud. B. Removes the complexity of managing multiple connections to AD. C. Allows for setup and configuration to be done in hours. D. Allows other vendors write access into AD via the Cloud Identity Engine. What are three benefits that customers receive with the Cloud Identity Engine? (Choose three.) A. Enable identity across the infrastructure. Configure once and CIE pulls incremental directory information automatically on consistent intervals. No additional changes required for additional IdPs (authentication). B. Guarantee compliance to all legal and regulatory requirements, thus reducing the auditing strain incurred on other departments within the organization. C. It is maintenance-free - No need to make changes on your infrastructure as identity providers make changes. All changes by identity providers, e.g., any updates by identity providers or changes in authentication protocols of directories do not require additional configuration on each firewall, management, endpoints. D. Easily identify and verify all IP addresses across the infrastructure and achieve Zero Trust. E. With minimal effort, enable and secure identity irrespective of whether they are using on-prem, cloud hybrid, or multicloud identity sources (IdPs). Which three of the following are Zero Touch approaches? (Choose three.) A. Microsoft Azure B. Google BeyondCorp C. Gartner CARTA D. Amazon Web Services E. Forrester Zero Trust Which of the following were authentication challenges faced by customers before the Cloud Identity Engine solution? A. Ping, Okta, AuthO, and SAML were not supported in most environments. B. There was significantly less configuration to firewalls, management, and endpoints. C. Every identity provider had to be added to all firewalls, management, and endpoints. D. Any changes by identity providers needed to be configured on the firewalls. Which type of interface is a subinterface? A. logical Layer 3 B. logical Layer 2 C. tap D. VWire What is the maximum character length for gateway and tunnel names? A. 31 B. 52 C. 63 D. 100 What are three benefits of Aggregate Ethernet? (Choose three.) A. redundancy B. increased bandwidth C. reduced packet loss D. load balancing E. mixing of interface types "correct answer" - ABD Which ID is the subinterface number analagous to? A. Ethernet ID B. SD-WAN Interface ID C. Ethernet Aggregate ID D. VLAN ID Which IPsec protocol provides both data integrity and encryption? A. Authentication Header B. Internet Key Exchange C. Diffie-Hellman Exchange D. Encapsulation Security Payload In IKE Phase 1, which three mode settings are available? (Choose three.) A. auto B. main C. passive D. network E. aggressive True or false: IKE Phase 1 is concerned with authenticating the endpoints; IKE Phase 2 is concerned with data traffic that crosses the tunnel. A. True B. False Which profile specifies protocols and algorithms for identification, authentication, and encryption for Phase 1 negotiations? A. IKE Crypto B. IPsec Crypto C. IKE Gateway D. IPsec Tunnel Which profile specifies protocols and algorithms for identification, authentication, and encryption for Phase 2? A. IKE Crypto B. IPsec Crypto C. IKE Gateway D. IPsec Tunnel Which IPsec protocol provides data integrity but not encryption? A. Authentication Header B. Internet Key Exchange C. Diffie-Hellman Exchange D. Encapsulation Security Payload What is used on each side of a tunnel to identify the traffic that will be sent across the tunnel? A. peer list B. proxy ID C. tunnel ID D. tunnel interface Which IPsec protocol negotiates the password algorithm? A. Authentication Header B. Internet Key Exchange C. Diffie-Hellman Exchange D. Encapsulation Security Payload "correct answer" Each tunnel interface can support a maximum of how many IPsec tunnels? A. 1 B. 5 C. 10 D. 20 True or false: The Palo Alto Networks firewall sets up a route-based VPN for which the firewall makes a routing decision based on the destination IP address. A. True B. False True or false? When you create a static route for the VPN, no next hop IP address is required. A. true B. false Which two options are true regarding a VPN tunnel interface? (Choose two.) A. The tunnel interface always requires an IP address. B. The interface name "tunnel" can be renamed to anything you want, up to 20 characters in length. C. A tunnel interface is a logical Layer 3 interface. D. The tunnel interface must be added to a Layer 3 security zone. "correct answer" - CD From which device should you begin to troubleshoot IPsec VPN connection issues? A. initiator B. responder C. network sniffer D. router What is the authentication component of the Cloud Identity Engine? A. OKTA B. SAML C. Azure D. Active Directory The Network Packet Broker is supported on which two Palo Alto Networks firewalls? (Choose two.) A. PA-800 B. VM-100 C. VM-300 D. PA-5200 Traditional App-ID only delivers new applications once per ___________? A. day B. week C. month D. year Which protocol is used by the OpenConfig plugin for operational services? A. gPAN B. gNMI C. gNOI D. gRCP Which categorization takes precedence if there is a verdict mismatch in Advanced URL Filtering? A. first match B. last match C. most severe D. least severe Which ML-Powered NGFW is optimized to meet the requirements for distributed enterprise branch offices? A. PA-220 B. PA-400 C. PA-3200 D. PA-5450 What is the maximum number of data processor cards that can be installed in the PA-5450 firewall? A. 2 B. 3 C. 5 D. 6 How are Security policies defined in the Cloud Identity Engine? A. based on IP addresses B. based on mail addresses C. based on MAC addresses D. based on users and groups What is required to enable Network Packet Broker? A. SSL Forward Proxy decryption B. WildFire subscription C. proxy disabled D. forward encryption enabled Which subscription is required to enable the App-ID Cloud Engine? A. Global Protect gateway B. WildFire C. SaaS Security Inline D. Threat Prevention Which protocol is used by the OpenConfig plugin for configuration management? A. gCON B. gNOI C. gNMI D. gPAN Advanced URL Filtering uses which existing configuration setting? A. URL filtering B. Malicious DB C. WildFire D. URL-ID Which three new PA-Series platforms are designed for the branch office? (Choose three.) A. PA-440 B. PA-4550 C. PA-460 D. PA-450 E. PA-5450 What is the name of a tool that creates highly available and customizable attacks? A. Cobalt Attack B. Cobalt Strike C. Cobalt Threats D. Cobalt C2 Toolkit Which two protections for DNS Record Attacks were added in Nebula? (Choose two.) A. Domain Squatting B. Wildcard DNS C. Dangling DNS D. CNAME Cloaking What do phishing sites often rely on before phishing content is served? A. Web crawlers B. URL databases C. user interaction D. evasive techniques What are two challenges that administrators commonly run into during the upgrade process? A. too many steps B. not enough time C. too many active users D. not enough administrators When were dependency checks performed in previous versions of PAN-OS? A. before installation B. after installation C. during installation D. beginning of installation Which two protocols does Advanced Threat Prevention use to prevent unknown C2 traffic? (Choose two.) A. known tcp B. SSL C. HTTP D. known udp Which method is available to perform a BPA? A. Expedition Tool B. Customer Support Portal C. Create Support Ticket D. NGFW What are three available options in the AAC by default to enable administrators to perform deep traffic and network analysis? (Choose three.) A. Networks B. Threat C. Restricted D. Tunnel E. IPsec VPN True or False: Extra consideration should be given when determining whether to enable logging. A. True B. False True or False: The Best Practice Assessment Tool output sometimes will suggest actions that are irrelevant or may prove to have detrimental consequences. A. True B. False At which location do you access the online BPA tool? A. Palo Alto Networks homepage B. Customer Support Portal C. LIVEcommunity D. Tech Support What are two available methods in which to perform a BPA? (Choose two.) A. Next-Generation Firewall B. online via a web interface portal C. create support ticket D. Expedition tool Which option is a valid URL filtering action? A. allow B. deny C. stop D. forward Which option is a valid Vulnerability action? A. alert B. deny C. return D. inform Security Profiles and Content-ID offer protection from which three threat categories? (Choose three.) A. Payload B. Sinkhole C. IP-based D. DNS-based E. URL Palo Alto Networks recommends the default-paloalto-dns signature action be set to: A. alert B. block C. sinkhole D. allow Which two options can be applied to a Security policy? (Choose two.) A. Zone Protection Profile B. DoS Protection Profile C. Security Profile Group D. Antivirus Profile Which is not a valid URL filtering action? A. deny B. allow C. continue D. override Which feature does not require a valid threat subscription license? A. Anti-Spyware B. Vulnerability Protection C. DoS Protection Profile D. Antivirus True or false? Palo Alto Networks recommends the software to be upgraded to the latest release. A. True B. False Which option helps the firewall admin to track all rule changes? A. Tag B. Description C. Audit Comment D. Rule Name "correct answer" Which two statements are true about tags? (Choose two.) A. Can be used only on Security policies. B. Can be used to filter the ruleset. C. A single tag cannot be used on multiple policies. D. Tag enforcement for the rules can be made mandatory Palo Alto Networks suggests keeping your PAN-OS version within how many minor versions of the major lines? A. one B. two C. three D. four "correct answer" What are two benefits of tagging? (Choose two.) A. filtering views B. grouping rules C. filtering actions D. report grouping "correct answer" Logs can be forwarded to which three external storage locations? (Choose three.) A. Panorama B. syslog C. email server D. SFTP server E. cloud server "correct answer" Dynamic Address Group and dynamic user group creation involves which three common steps? (Choose three.) A. creation of a tag B. assignment of a tag in the Log Forwarding Profile C. use of the User-ID feature D. application on Security policies E. assignment of a Security Profile "correct answer" True or False? The predefined log format cannot be changed for both syslog and email server forwarding. A. true B. false "correct answer" [Show More]
Last updated: 1 year ago
Preview 1 out of 25 pages
Reviews( 0 )
Recommended For You
Computer Science> EXAM > Palo Alto PCNSE Certification Exam Sample Questions and Answers (All)

Palo Alto PCNSE Certification Exam Sample Questions and Answers
Start your Preparation for Palo Alto PCNSE and become Network Security Engineer certified with NWExam.com. Here you get online practice tests prepared and approved by Palo Alto certified experts based...
By Nancylect , Uploaded: Aug 22, 2022
$6
Computer Science> EXAM > Palo Alto PCNSE Certification Exam Sample Questions and Answers (All)

Palo Alto PCNSE Certification Exam Sample Questions and Answers
Start your Preparation for Palo Alto PCNSE and become Network Security Engineer certified with NWExam.com. Here you get online practice tests prepared and approved by Palo Alto certified experts based...
By MARKALLAN , Uploaded: Aug 22, 2022
$6
Computer Science> EXAM > Palo Alto PCNSE NGFW Questions And Answers 2022/2023 (All)

Palo Alto PCNSE NGFW Questions And Answers 2022/2023
Palo Alto PCNSE NGFW Questions And Answers 2022/2023
By Axeldee , Uploaded: Oct 24, 2022
$13.5
Computer Science> EXAM > Palo Alto PCNSE NGFW Questions With Verified Answers (All)

Palo Alto PCNSE NGFW Questions With Verified Answers
Palo Alto PCNSE NGFW Questions When creating a custom admin role, which four types of privileges can be defined? (Choose four.) Global user authentication is supported by which three authenticatio...
By browseAgrades , Uploaded: Nov 17, 2022
$15
Computer Science> EXAM > Palo Alto PCNSE NGFW Exam - Q & A with Complete Solutions (All)
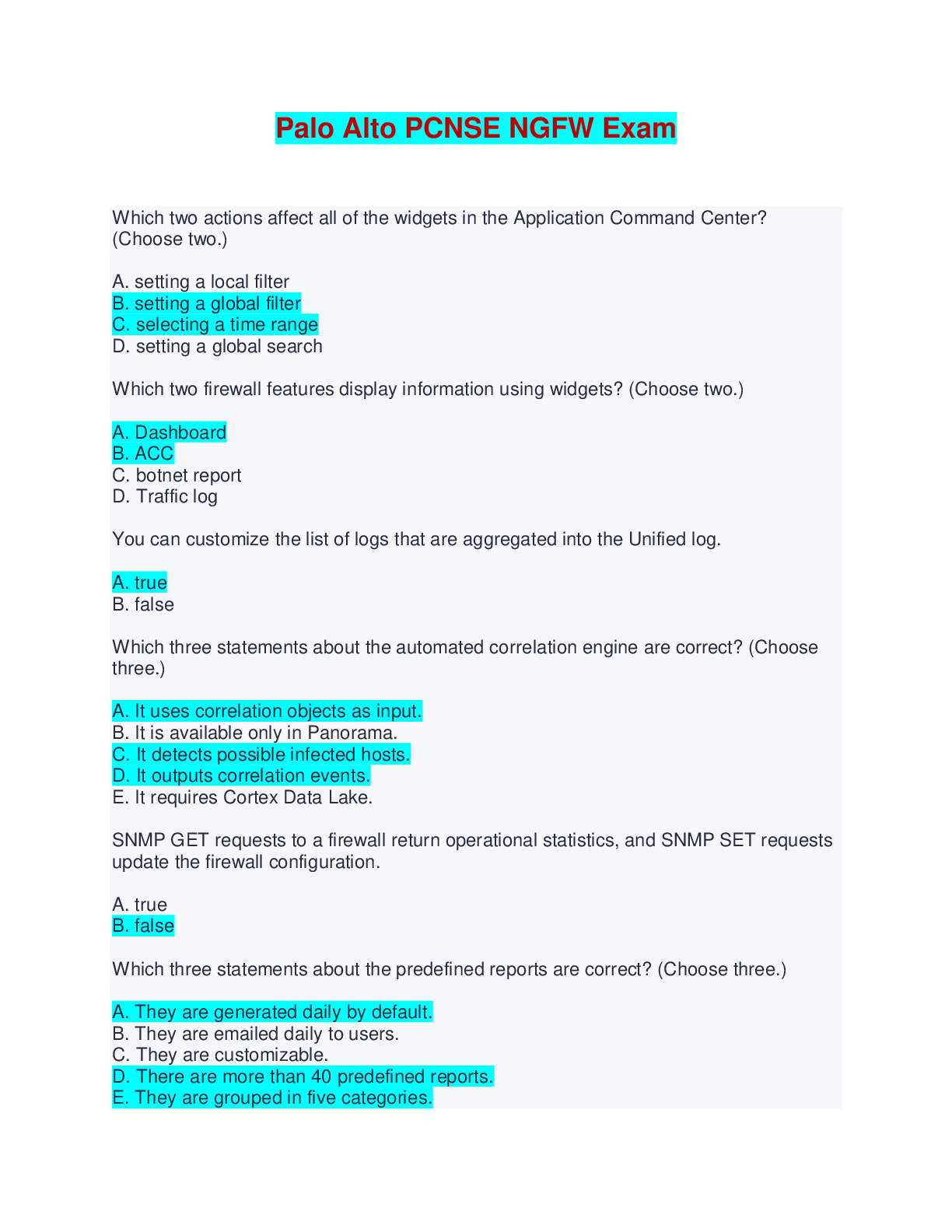
Palo Alto PCNSE NGFW Exam - Q & A with Complete Solutions
Palo Alto PCNSE NGFW Exam - Q & A with Complete Solutions Which two actions affect all of the widgets in the Application Command Center? (Choose two.) A. setting a local filter B. setting a global f...
By Ajay25 , Uploaded: Jan 30, 2024
$18
Health Care> EXAM > Ethics for Health Professions HCA-200 Final Exam Questions with Answers 100% Correct (All)

Ethics for Health Professions HCA-200 Final Exam Questions with Answers 100% Correct
Ethics for Health Professions (HCA- 200) Final Examination Part 1: Multiple Choice (1 points each) ● Identify the choice that best completes the statement or answers the question. ● Clearly circ...
By Quiz Merchant , Uploaded: Apr 19, 2021
$9
*NURSING> EXAM > ENPC Test Questions & Answers (All)

ENPC Test Questions & Answers
ENPC Test Questions & Answers-An unresponsive 2-year-old child was found by his mother with a bottle labeled "Elavil 50 mg" by his side. Which piece of information is important to obtain from his moth...
By PROF , Uploaded: Apr 25, 2024
$9.5
Religious Studies> EXAM > CWV TOPIC 2 QUIZ. QUESTIONS AND ANSWERS LATEST UPDATED. (Score 100%) (All)
CWV TOPIC 2 QUIZ. QUESTIONS AND ANSWERS LATEST UPDATED. (Score 100%)
CWV TOPIC 2 QUIZ QUESTIONS AND ANSWERS LATEST UPDATED
By ELIANA , Uploaded: Aug 01, 2022
$9
ATI MED SURG PROCTORED> EXAM > Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN (All)
Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN
Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN Med Surg ATI Proctored E...
By EXAMHUB SOLUTIONS , Uploaded: Apr 15, 2024
$30.5
NURSING.> EXAM > ATI RN CUSTOM; MENTAL HEALTH NEXT GEN (All)
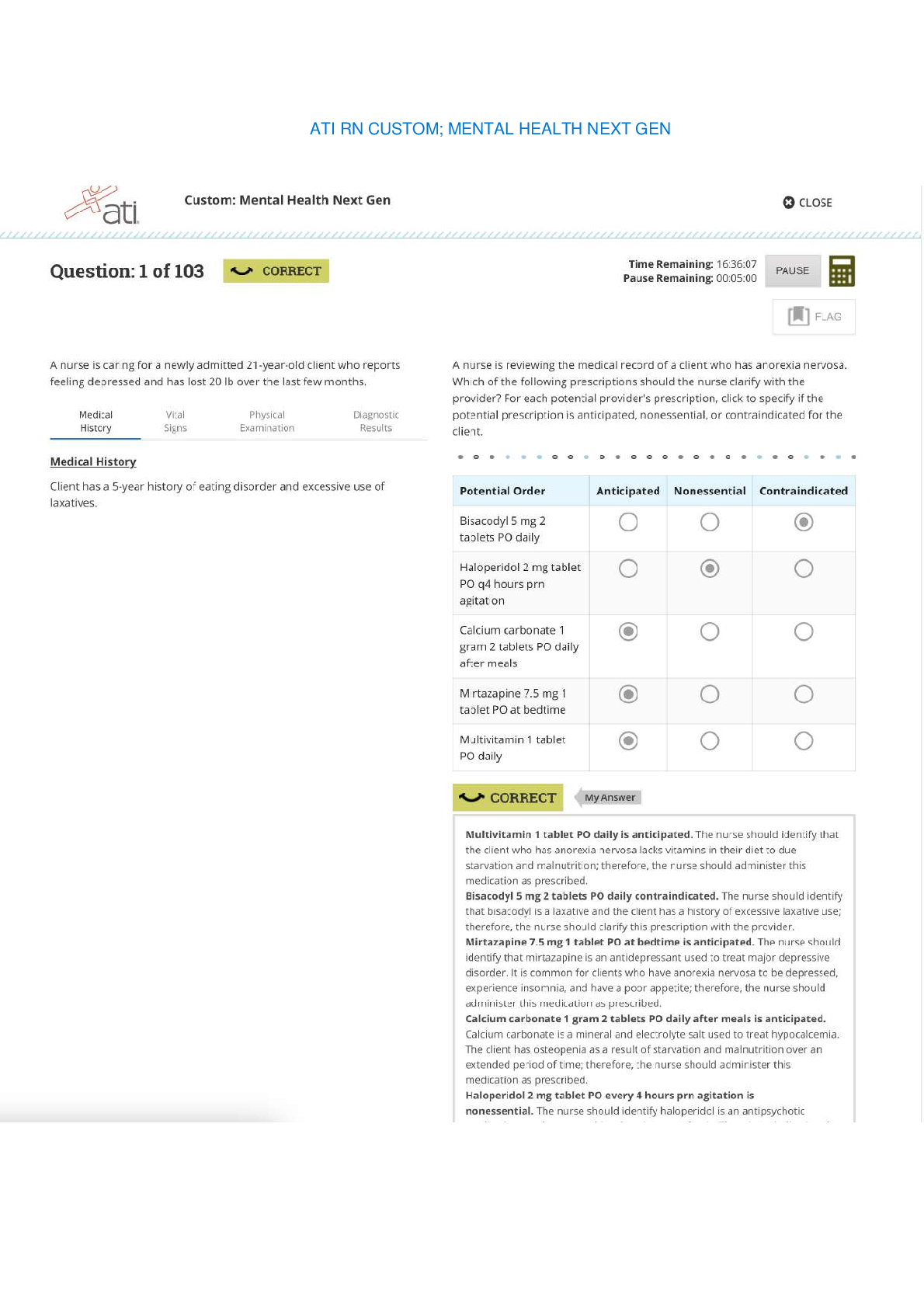
ATI RN CUSTOM; MENTAL HEALTH NEXT GEN
ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GE...
By EXAMHUB SOLUTIONS , Uploaded: Apr 05, 2024
$45.5
Document information
Connected school, study & course
About the document
Uploaded On
Oct 15, 2022
Number of pages
25
Written in
Additional information
This document has been written for:
Uploaded
Oct 15, 2022
Downloads
0
Views
350






