Computer Science > QUESTIONS & ANSWERS > CIS MISC Conslidated day 11 to day 20 questions (All)
CIS MISC Conslidated day 11 to day 20 questions
Document Content and Description Below
CIS MISC Conslidated day 11 to day 20 questions Day 11 Questions 1. GPO is a collection of? a) A user b) A computer c) Group policy setting d) A & b 2. _____ defines a specific configuration... change a. GPO b. Group policy setting c. Both a & b d. None of the above 3. GPO can be applied to a. A user b. A computer c. User and computer d. User or computer 4. Group policy container is stored in a. AD DS b. SYSVOL c. Group policy settings d. None of the above 5. Group policy Template is stored in a. AD DS b. SYSVOL c. Group policy settings d. None of the above 6. Which is/are not true for group policy preferences a. Are not enforced b. Are removed when the GPO no longer expires c. Can be used in local group policies d. Are not removed when the GPO no longer expires 7. GPP are used for a. Configure os and application settings b. Deploy os and application settings c. Manage os and application settings d. All the above 8. A starter GPO: a. Has preconfigured administrative template b. Can be exported to .cab files c. Both a & b d. None of the above 9. Which one of this is not the user configurations layer? a. Administrator b. Standard user c. User-specific d. User-control 10.How many layers in user configuration layers are? a. 3 b. 4 c. 6 d. 2 11.Which of these is two default GPOs. a. Default domain policy b. Default controllers policy c. Default domain controllers policy d. Default GPO policy 12.What is a central repository for ADMX and ADML files? a. SYSVOL b. Central store c. GPO d. Default domain policy 13.Central store is stored in ______________. a. GPO b. Active directory c. SYSVOL d. ADMX file 14.In ___________policy user cannot make a change to the setting and changes are made in one or four reserved registry keys. a. Control b. Managed c. Unmanaged d. Advanced 15.In __________ policy UI is not locked and changes made are persistent. a. Managed b. Unmanaged c. Control d. Advanced 16. __________ are a feature of Group Policy, a Microsoft technology for centralized management of machines and users in an Active Directory environment. a. Administrative Templates b. Active directory c. SYSVOL d. None of the above Day 12 Questions 1. In Find what version of Windows did Microsoft adopt Kerberos as an authentication policy? A. Windows NT B. Windows Server 2003 R2 C. Windows Server 2000 D. Windows 2008 Ans:- C 2. Authentication across this type of trust is Kerberos based (as opposed to ________). A. LM hash B. NTLM C. Samba (software) D. Integrated Windows Authentication Ans:- B 3: Which feature enables administrators to create application restriction rules? A. AppLocker B.Group Catalog C.Domain Controller D.Windows Installer ANSWER: AppLocker 4. Which of the following strategies prevents all applications from running except those that are specifically allowed? A.Basic user B.Disallowed C.Power user D.Unrestricted ANSWER: A 5. Applocker applies______policies in______ A. Application control B.Transport control C.Windows server2012 and windows 8 D. All of the above ANSWER: A, C 6. App locker capabilities and extensions administrators control how users access and use files A. exe files B. Scripts C. DLLS D. Windows installers files E. Package apps F. All of the above Answer: F 7. Srp allows administrator to identify apps are allowed to run on client computers A. Hash B. Certificate C. Path D. Zone E. All of the above Answer: E 8. App locker defines rule based on file attributes A. publisher name B. File name C. File version D. Document version E. All the above Answer: A,B,C 9. What are configuring account policy settings are ? A. Password B. Account lockout C. Kerberos D. Login account E. All of the above Answer: A, B, C 10.Example while doing in lab section In password policy complexity and lifetime passwords are max password age____,min password age_____min password length,complex password_____ and reversible encryption_______ Answer: max password age:42 days ,min password age :1day,min password length:7 characters, Complexity password: enabled 11. In account lockout how many incorrect attempts can be made A. lockout duration :not defined B. Lockout threshold:0 invalid logon attempts C. Reset account lockout after: not defined D. All of the above Answer: D 12. In security compliance manager is a tool from Microsoft that helps you______ and____computers A. Local B. Remote or virtualized C. Domain controller D. Workgroup E. All of the above Answer: A, B 13. A firewall protects which of the following attacks? a) Phishing b) Dumpster diving c) Denial of Service (DoS) d) Shoulder surfing Answer: c 14. There are __ types of firewall. a) 5 b) 4 c) 3 d) 2 Answer: b 15. The ____ defines the packet filtering firewall rules. a) Access Control List b) Protocols c) Policies d) Ports Answer: a 16. A firewall is installed at the point where the secure internal network and untrusted external network meet which is also known as ____ a) Chock point b) Meeting point c) Firewall point d) Secure point Answer: a 17. A proxy firewall filters at ___ a) Physical layer b) Data link layer c) Network layer d) Application layer Answer: d 18. A firewall is a ____security system: a) Network b) File c) Program d) None of These Answer: a 19. ACL stands for _____ a) Access Condition List b) Anti-Control List c) Access Control Logs d) Access Control List Answer: d 20. While deploying firewall system rules are? A. Manually B. By using group policy C. By exporting and importing D. Normally E. All of the above Answers: A, B, C 21. In firewall profiles are a set of configuration settings that apply to a particular network types A. Domain B. Public C. Private D. All of the above Answer: d 22. Firewall examines each_______ that are entering or leaving the internal network A. emails users B. Updates C. Connections D. Data packets Answers: d 23. A stateful firewall maintains a_______ which is a list of active connections A. Routing table B. Bridged table C. State table D. Connection table Answer: A 24. In which one of it not the firewall profile A .Domain B. Private C. Public D. Incremental Answer: D 25. MSI stands for . . . . . . .? A. Multi software installer B. Manual software installer C. MS Software installer D. Microsoft Installer 26. Which of those are deploying windows firewall rules? A. Manually B. Using group policy C. Exporting and importing D. None of these above 27. Firewall rules allow traffic through, but don’t secure that traffic A. True B. False 28. How firewall rules and connection rules are related: A. Firewall rules allows the traffic but not the secure the traffic B. Connection security rules can be secure the traffic C. Both A and B D. None of these above 29. Windows server 2012 R2 ability to have how many active firewall profiles A. Single active firewall profile B. Double active firewall profile C. Multiple active firewall profile D. No active firewall profiles 30. Which of the following is a scriptable MMC snap-in that provides a single administrative tool to manage Group Policy across an enterprise? A. GPMMC B. GPMC C. GPOCD D. GPOMC 31. Which file is present in Group Policy tools by default? A. ADM B. ADMX C. Group policy D. Security template 32. Which of the following is a way of refining which users and computers will receive and apply the settings in a Group Policy object (GPO)? A. Refined filtering B. Security filtering C. Account filtering D. GPO filtering 33. Which of the following features enables you to restrict the dissemination of Group Policy settings to specific users? A. Security filtering B. Administrative templates C. GPO linking D. Starter GPO 34. Which of the following operations is not supported by Active Directory? A. Assigning applications to users B. Assigning applications to computers C. Publishing applications to users D. Publishing applications to computers 35. Which of the following filename extensions is used primarily for Windows Installer setup programs? A. .msi B. .mst C. .zap D. .aas 36.Full form of UAC a) User account control b) User account computer c) User account computers Answer : a 37. UAC is a ___ Feature a) Security b) Non security Answer : a 38. Default max password age a) 42 days b) 10 days c) 47 days Answer : a 39. Default Min password age is a) 2 days b) 3 days c) 1 day Answer : c 40. Default Min password characters a) 8 b) 7 c) 9 Answer : b 41. SCM Stands for a) Security Compliance manager b) Security Computer Manager c) Security Compiler Manager Answer : a 42. SCM Features are a) Baselines b) Security Guides c) Supports for standalone computers d) All the above Answer : d Day 13 Questions 1.What are the benefits of virtualization with hyper-V? A) service and app isolation. B) invisible to users. C) simplifies server deployment. D)all the above 2.what is the cloud-based platform for hosting virtual machines? A) VMware B) Azure C)hyper-v D) Google cloud 3.we can use Windows Azure to? A) host websites B) host production apps C)host virtual machines D)all the above 4.VDI Stands for? A) virtual dynamic infra B) virtual domain input C) virtual desktop infra. D) none of the above 5.which allows Virtual machines to display rich graphics? A) remoteFX B) desktopFX C) graphicFX D) none of the above 6.requirements of remote FX? A) gpu- directxlX 9.0 or newer B) cpu-slat C) 2TB hdd D) A&B 7.In which type of virtualization the desktop and apps run within virtual machine? A) presentation B) desktop C)A&B D) none of the above 8.presentation virtualization technologies includes? A) remote desktop services B)apps using remote desktop C) remote access through rd gateway D) all the above 9.RDC stands for? A) remote domain controller B) remote desktop computer C) remote desktop connection D) remote desktop control 10.Benifits of app-v? A) app portability B) app streaming C)app isolation D) all the above. 11.UE-V stands for user experience virtualization. 12.hyper-v is hardware virtualization role started from? A) Windows server 2008 B) windows server 2012 C) windows server 2012 r2 D) windows server 2019 13.processor characteristics for hyper-v? A)32bit B)64bit C)A or B D)none of the above 14.what are the default simulated hardware in virtual machines? A) bios B) scsi controller C)IDE controller D)all the above 15.how Many scsi controller we can add to virtual machine? A) upto 8 B) upto 6 C) upto 4 D) upto 2 16.which generation virtual machines used UEFI instead of BIOS? A) gen 1 B) gen 2 C) both a&b D)none 17.UEFI stands for Unified extensible firmware interface. 18.supported os for generation2 virtual machines? A) windows server 2012 r2 B) 32-bit windows 8.1 C) Windows server 2012 D) windows server 2008 19.virtual machine integration services includes? A) heartbeat B) time synchronization C)data exchange D)all the above 20.what are the possible stop actions of virtual machines? A) save virtual machines state B) turn off virtual machine C)both a&b D) none of the above 21.hyper-v resource metering can measure? A)average Cpu usage B)max disk space allocation C) ip address ranges D) average memory usage 22.new features of hyper-v in windows server 2012 r2? A) shared virtual disk B) automatic activation C) storage quality of service D)all the above 23.benifits of vhdx over vhd? A) disk is upto 64TB B) disk corruption is less likely to occur C)both A and B. D) none of the above 24.what tool is used to reconnect differencing disk to a missing parent? A) reconnect disk B) renew disk C) inspect disk D) suspect disk 25.what are static images of the data on a virtual machine at a given moment? A) static points B) checking points C) check points D)snap points 26.which virtual switch is used to map a n/w to specific n/w adapter? A) internal B) external C) private D) none of the above 27.which is not used to communicate b/w virtual machines and host itself? A) private B) internal C) both D) none of the above 28.which is used to logically segment n/w traffic running on the same physical and virtual n/w's? A) NAT B) VLAN C) BRIDGE D)all the above 29.To create virtual switches, virtual switch extensions should enable? A) routers B) third party vendors C)A or B D)none of the above 30.properties of a network adapter? A) VLAN iD B) bandwidth management C) virtual switch D)all the above. 31.NIC stands for? A) new interface control B) next input card C) network interface control D) network interface card 32.IPsec task offloading enables the host's n/w adapter to perform calculation intensive security association tasks. 33.which of the following provides redundancy and aggregates bandwidth? A)vhd B)NIC teaming C)vhdx D) none of the above 34. VRSS balances the n/w processing across multiple virtual processor cores in virtual machine. 35.virtual machine _________ delivers n/w traffic directly to the guest. A) role B) queue C) both A&B D) none of the above Day 14 Questions 1. What are the following components of a DNS solution? a. DNS resolvers b. Resource Record c. DNS servers on the internet d. All of the above 2. What are the types of queries available in DNS server? a. Recurive or Iterative b. Recursive and iterative c. None of the above 3. A non authoritative DNS server for the namespace will do the following? a. Check its cache b. Use forwarders c. Use root hints d. All the above 4. One of the following DNS server that is designated to resolve offsite DNS domain names? a. Forwarder b. Local server c. DNS records d. None of the above 5. The following is the IPV6 host address resource record? a. SRV record b. NS record c. AAAA record d. PTR recoed 6. One of the following is the exchange record? a. PTR b. MX c. SOA d. NS 7. The following are the DNS zone types? a. Primary and secondary b. Stub zone c. Active directory integrated d. All of the above 8. The following is used to create a copy of a zone that contains only records used to locate name servers? a. Primary b. Secondary c. Stub d. None of the above 9. The zone that is used to convert domain name to IP address is called? a. Forward zone b. Reverse zone c. Stub zone d. None of the above 10.The command that is used to get the DNS management console is? a. Dnsmgmt.msc b. Dnsms.msc c. Dnsmgmt.exe d. None of the above 11.The following are the DNS zone transfer securities? a. Encrypt zone transfer traffic b. Restrict zone transfer to specified servers c. None of the above 12.The following feature indicates that how long a DNS record will remain valid? a. TTL b. Aging c. Scavenging d. All of the above 13.One of the following performs DNS resource record grooming for old records in DNS? a. Ging b. Scavenging c. TTL 14.The following are the DNS monitoring features? a. Debug logging b. Event logging c. Monitoring d. All the above 15.The following record is used to convert IP address to domain name in DNS? a. PTR b. CNAME c. MX d. AAAA 16.The entire hostname has a maximum of ___________ A.31 characters B.255 characters C.127 characters D.None of the above 17.Types of DNSzones A. primary B. Secondary C. Stub D. All the above 18.DNS database contains a) name server records b) hostname-to-address records c) hostname aliases d) all of the mentioned 19.If a server has no clue about where to find the address for a hostname then _______ a) server asks to the root server b) server asks to its adjcent server c) request is not processed d) none of the mentioned 20.Which is the synchronization of authoritiveDNS zones data between DNS servers a)Zone transfer security b) DNS zone transfer c)Split DNS Day 15 Questions Q1:- Local security policy account setting is configured with which command? Ipconfig Secpol.msc Ipconfig/renew Ntdsutil Q2:-local security policy account is applicable to? Local user Admin Q3:- Group policy account setting is configured in? Group policy managememt console Command promt Q4:-Group policy accouny setting is applicable to? Users Ous All accounts in ADDS and local accounts on computers joined to the domain None Q5:- Group policy account settings take precedence over? User Local security policy settings Q6:- Fine grained password policies are applicable to? Only to user object and global security obj System Q7:-Fine grained password cant be applied to _______ directly? Domain Ous System Q8:- Tools for configuring PSOs in windows server 2012? Windows power shell cmdlets Active directory administrative center Both Q9:- Which of the following are password policies? Woodgrove bank New account lockout policy Tailspin toys Best practices All of the above. Q10:- Challenges of using std user accounts for services? Extra administrative effort to mangae service account password. Difficulty in determining whwere a domain based account is used as service account Extra administrative effort to manage SPN All of above Q11:- Group manages service accounts requiremnets? Must have atleast 1 windows sever 2012 domain controller Must have a KDS root key created fir domain. Both Q12:-Which graphical tool is used to manage ADDS. a. Active Directory administrative snap-ins b. Active directory administrative center c. Directory service command d. Active directory domain and user Q13.Which Command line tool is used to manage ADDS. a. Active Directory administrative snap-ins b. Active directory administrative center c. Directory service command d. Active directory domain and user Q14.Which setting is used to set password in GPO. a. Min password age b. Password complexity requirement c. Account lockout duration d. All of the above Q15. Who can create site level Group policy. a. Enterprise Admin b. Domain admin c. Both d. d.None Day 16 Questions Q1. Which of these are Administrative Template(s) for a ‘Computer’? Ans. A) Control Panel B) Server C) Start Menu and Taskbar D) Desktop Q2. Which of these is NOT an Administrative Template for a ‘User’? Ans. A) Start Menu and Taskbar B) Windows Components C) Printer D) Shared Folders Q3. What is the file location that is checked by the Group Policy tools and is used to store the Administrative Template files? Ans. A) Central Store B) Information Store C) GPO Specific Store D) Elevates Store Q4. Which of the following is used to provide a graphical user interface to create and modify Administrative templates? Ans. A) Migration Table B) ADMX Migrator C) Group Policy Preference D) Item-level targeting Q5. Which file is present in Group Policy tools by default? Ans. A) Security Template B) Group Policy C) ADM D) ADMX Q6. Which of the following features enables you to restrict the dissemination of Group Policy settings to specific users? Ans. A) Administrative Templates B) GPO Linking C) Security Filtering D) Starter GPO Q7. You are the administrator responsible for security and user desktop settings on your network. You need to configure a custom registry entry for all users. You want to add the custom registry entry into a Group Policy object (GPO) with the least amount of administrative effort What should you do? Ans. A) Configure an ADM template and add the template to the GPO B) Configure an INF policy and add the policy to the GPO C) Configure RIS to include the registry entry D) Configure a Microsoft Windows Installer package and add the package to the GPO Q8. To which directory must you copy the ADMX files from \ %systemroot%\PolicyDefinitions in order to create a Central Store for Group Policy management templates? Ans. A) \\FQDN\SYSVOL\FQDN\policies B) \\FQDN\SYSVOL\FQDN\PolicyDefinitions C) \\FQDN\SYSVOL\policies D) \\FQDN\SYSVOL\PolicyDefinitions 9. The central repository for ADMX and ADML files is Administrative Templates Central store Computer GPO 10. Which feature allows the folders to be located on a network, but appear as if they are located on the local drive Bitlocker Administrative Templates Folder Redirection None 11. ADMX stands for Administrative Template Xml-Based Administratrix Axion Dark Matter Experiment Administrative Template Extensible 12. Folders that can be redirected in Windows Vista and later are Desktop Documents Contacts All of the above 13. Software requirements for folder redirection are :- Client computers must be joined to the ADDS that you are managing A computer must be available with Group Policy Management and Active Directory Administration Center installed. Both None 14. Which type of access is granted to the System under NTFS permission for root folder Read only Full control None Modify 15. We can use scripts to perform tasks such as Mapping drives Clearing temp folders for users Both None 16. Number of scripts supported by a Group Policy 2 3 4 6 17. A set of extensions, introduced in Windows Server 2008, that increase the functionality of Group Policy Objects (GPOs) Group Policy Preference Group Policy Management ADDS None 18. How many categories are targeted by item-level targeting options 36 16 24 27 19. Which of these is not the step involved in group policy software distribution in addressing software cycle ? a. Preparation b. Deployment c. Management d. Removal 20. Which of these are benefits of using windows installer ? a. Custom Installation b. Resilient Application c. Clean Removal d. All Of These 21. What are managing software upgrades by using group policy ? a. Mandatory Upgrade b. Optional Upgrade c. Selective Upgrade d. All Of These Day 17 Questions 1.In radius proxy receives connection attempts from _______and then forwards them to the appropriate __________ A. Radius client B. active directory c. Radius server or another radius proxy routing d. All of the above Answer: A and c 2.In radius proxy is required for service providers offering outsourced are A. Dial-up b. VPN c. Wireless network access d. server and domain network e. All of the above Answer: A, B, C 3. In radius proxy providing authentication and authorization for user accounts A. DNS server b. DHCP server c. active directory members d. radius server e. All of the above Answer: C 4. In radius proxy server performing authentication and authorization by using not in database A. Windows account database b. windows server database c. DNS server database d. Al of the above Answer: A 5. In radius proxy load balancing connections request among _________servers A. single b. double c. multiple d. All of the above Answer: c 6.In Connection request policies are set of conditions and settings that designate which radius server perform the _____ and _______of connection requests that _______ from radius clients A. authentication B. authorization c. NPS receives d. radius proxy server d. All of the above Answer: A, B, C 7.In Connection request policies conditions are used in radius servers and clients are A. framed protocol b. domain type c. service type d. tunnel type e. day and time restriction Answer: A, C, D, E 8.In connection request policies settings can be used A. Authentication b. Accounting c. Attribute manipulation d. Advanced settings e. All of the above Answer: E 9.In configuration connection request processing local authentication where it takes place_______ A. local security account database b. active directory domain service c. local security account database or active directory domain service d. All of the above Answer: c 10.In configuring connection request processing radius server are capable of handling connection request __________ A. load balanced specified criteria b. local authentication c. active directory d. All of the above 11.In configuration connection request processing default port for accounting and authentication by using radius A. Forwarded radius server b. UDP 1812/1645 and UDP 1813/1646 C. Reverse radius server d. All of the above 12.By using certificates to deploy certificate based authentication in NPS _____________ A. CA certificate B. Client computer certificate C. Server certificate D. User certificate E . All of the above 13.By using CA certificate in deploy certificate authentication resides __________authorities A. Trust root certification B. Domain root certification C. Server root certification D. All of the above 14. By using CA certificate to store certificate data _________ and___________ A. Local computer B. Current user C. Domain user D. Server user E. All of the above 15.In client computer certificate in deploy certificate in nps resides __________ A. In store in client B. It stores in domain C. It stores in server D. All of the above 16.By using user certificate in deploy certificate in nps are______ A. Smart card B. Insert card C. Domain users D. All of the above 17.By using certificate for authentication to provide network access ____________ A. It provide strong security B. It eliminate less secure C. It provides password authentication D. All of the above 18.By using password based authentication methods for an ______ from the most secure to the least secure A. NPS server B. Domain server C. Client server D. All of the above 19.By using password based authentication methods for an NPS server from the most secure to the least secure A. Ms chapv2 B. Ms chap C. Chap D. All of the above 20.By using password based authentication methods for an NPS from the most secure to the least secure A. PAP B. Unauthenticated access C. Domain access D. Client access 21. Full form of sql a) Structured query language b) System query language c) System quotation language Answer : a 22.Which of the following has support for transaction? a) sp_monitor b) sp_bind session c) sp_status d) all of the mentioned Answer : b 23. ____create the removable database. a) sp_certify_removable b) sp_certify c) sp_removable d) all of the mentioned Answer: a 24.Which of the following stored procedure is used for error messages? a) sp_add message b) sp_drop message c) sp_alter message d) all of the mentioned Answer : a 25. _____ sets procedure options in SQL Server. a) sp_procoption b) sp_drop message c) sp_alter message d) sp_executesql Answer: a 26. NPS is configured by default to record ___ in the event log a) Failed connections and success full connections b) Failed connections c) Successful connections Answer: a 27.By using windows server 2012 network policy server provides are________ A. Radius server B. Radius proxy C. NAP policy D. All of the above 28.In network policy radius server NPS performs centralized connection ______________and ____________ A. authentication B. Authorization C. Domain D. Client E. All of the above 29.In network policy radius server NPS performs centralized connection for accounting wireless __________and _________ A. Authenticating switch B.Dial up B. Vpn connections C. All of the above 30.By using tool for configuring a network policy settings in which command nps role A. Netsh command line tool B. Gp udate command C. Net dom query command D. All of the above 31.By using tool for configuring a network policy settings in netsh command line tool types in nps role A. NPS server commands B. Radius client commands C. Connection request policy commands D. Remote radius server group commands E. Network policy commands F. Nap policy commands G. Accounting commands H. All of the above 32. You are the administrator of a large organization that contains an Active Directory domain named Stellacon.com. The domain contains a server named Server A that runs Windows Server 2012 R2. Server A has the Network Policy and Access Services server role installed. Your company’s security policy requires that certificate-based authentication be used by some network services. You need to identify which Network Policy Server (NPS) authentication methods comply with the security policy. Which two authentication methods should you identify? (Choose two. a)MS b)PEAP c)CHAP d)EAP 33. You are the network administrator, and you have been asked to set up an accounting system so each department is responsible for their cost of using network services. Your network contains a Network Policy Server (NPS) server named ServerA. The network contains a server named Database1 that has Microsoft SQL server installed. All servers run Windows Server 2012 R2. You configure NPS on ServerA to log accounting data to a database on Database1. You need to ensure that the accounting data is captured if Database1 fails. The solution must minimize cost. What should you do? A) Implement Failover Clustering. B) Implement database mirroring. C) Run the Accounting Configuration Wizard. D) Modify the SQL Server Logging properties 34.Your network contains an Active Directory domain named Stellacon.com. The domain contains a RADIUS server named Server1 that runs Windows Server 2012 R2. You add a VPN server named Server2 to the network. On Server1, you create several network policies. You need to configure Server1 to accept authentication requests from Server2. Which tool should use on server1. A) Set-Remote Access Radius B) CMAK C) NPs D) Routing and Remote Access 35. By using method monitor NPS for auditing and troubleshooting __________________ logging A. event logging B. system logging C. domain logging D. ALL of the above 36. By deploying certificate for for peap and eap in domain computer and user accounts auto enrollment feature in _______________ policy A. Domain policy B. Group policy C. Server policy D. All of the above 37. Full form of EAP __________________ A. Extensible authentication protocol B.Extensible protection protocol C.Protected extensible protocol D. All of the above 38. Full form of PEAP _______________ A. Extensible protection protocol B. Protected extensible protocol C. Protected extensible authentication protocol D. All of the above 39 .Full form of MS-CHAP ____________________ A. Microsoft challenge handshake authentication protocol B. Microsoft handshake authentication C. Microsoft challenge handshake protocol D. All of the above 40 .Full form of MS-CHAP V1______________ A. Microsoft challenge handshake authentication protocol version 1 B.Microsoft handshake authentication C.Microsoft challenge handshake protocol D.All of the above Day 18 Questions 1. NAP stands for A. Non aggression principle B. Network analytics principle C. Network access protection D. Network acesss principle 2. NAP cannot ensure which of the following A. Ensure client computers are complaint with policies B. Prevent authorised users with complaint computers from performing malicious activities on the network C. Enforce health-requirement policies on the client computers D. Offer remediation support for computers that do not meet health requirements 3. Following are the operations carried by NAP A. Ensure client computers are complaint with policies B. Prevent authorised users with complaint computers from performing malicious activities on the network C. Enforce health-requirement policies on the client computers D. Offer remediation support for computers that do not meet health requirements 4. NAP helps you to verify which of the following A. Desktop computers B. Roaming laptops C. Visiting laptops and devices D. All of the above 5. NAP can be enforced by using which of the following methods A. DHCP based configuration B. By creating respective domains C. Direct access D. By allowing users read and write permissions. 6. IPsec enforcement for IPsec-protected communications involves A. The strongest NAP enforcement type and can be applied per IP address or protocol number B. This is the weakest form of enforcement C. Computer must be complaint to obtain unlimited network access D. Computer must be complaint to receive an unlimited access through remote access service connection 7. Which of the NAP enforcement must be complaint to communicate with other complaint computers A. VPN enforcement for remote access connections B. DHCP enforcement for DHCP based address configuration C. 802.1X enforcement for IEEE D. IPsec enforcement for IPsec protected communications 8. For non- complaint computers, access is restricted to a defined group of infrastructure servers in which of the following NPA methods A. DHCP based address configuration B. VPN enforcement for remote access connections C. IPsec enforcement for IPsec protected communications D. Direct access 9. Computer must be complaint to obtain unlimited access through an 802.1x connection in which of the following NPA methods A. DHCP based address configuration B. VPN enforcement for remote access connections C. IPsec enforcement for IPsec protected communications D. 802.1x enforcement for IEEE 10. System health validators are software counter parts to system health agents. 11. Each SHA on the client has a corresponding SHV in NPS 12. SHVs allow NPS to verify the SOH made by its corresponding SHA on its clients. 13. The windows security SHV corresponds to the Microsoft SHA on the client computers. 14. Most NAP client settings can be configured with A. DHCP B. VPN C. GPO 15. Full form of IPSEC A. Internet protocol section B. Intermediate protocol security C. Internet protocol security 16. IPsec is a protocol suite for protecting ______ A. IP communications B. DHCP C. VPN 17. IPSec is designed to provide security at the _________ a) Transport layer b) Network layer c) Application layer d) Session layer 18 In tunnel mode, IPSec protects the ______ a) Entire IP packet b) IP header c) IP payload d) IP trailer 19. Which component is included in IP security? a) Authentication Header (AH) b) Encapsulating Security Payload (ESP) c) Internet key Exchange (IKE) d) All of the mentioned 20. WPA2 is used for security in _______ a) Ethernet b) Bluetooth c) Wi-Fi d) Email 21. IP authentications are a) DES b) Kerberos V5 c) Triple DES d) AES 22. IP authentications are a) DES b) Kerberos V5 c) Triple DES d) AES 23. You can implement NAP with IPsec enforcement by configuring the following components a) Certification authority) b) HRA server c) Computer running NPS role d) All of the mentioned 24. IPsec NAP enforcement includes a) Policy validation, NAP enforcement b) Ongoing monitoring of compliance c) Network restriction, Remediation d) All the above 25. HRA full form a) Higher registration authority b) Heath Resource agent c) Health registration authority d) Heath registration Resource 26. Health Registration Authority (HRA) provides a service for the a) VIP b) DHCP c) NAP 27. To obtain and issue certificates, The _____ must be associated with a CA a) RAC b) NAC c) HRA 28. NAP tracing identifies NAP _______ & ______ a) events b) records 29. Meaning of 6273 event ID a) Successful authentication has occurred b) Successful authentication has not occurred c) A configuration problem exists d) NAP client quarantined 29. NAP Commands is a) Netsh NAP client state b) Netsh NAP client state c) Netsh NAP client show state d) NetshNAPclientshowstate 30. NAP Commands are a) Netsh NAP client show state b) Netsh NAP client show config c) Netsh NAP client show group 31. Meaning of 6272 event ID a) Successful authentication has occurred b) Successful authentication has not occurred c) A configuration problem exists d) NAP client quarantined 32. Meaning of 6273 event ID a) Successful authentication has occurred b) Successful authentication has not occurred c) A configuration problem exists d) NAP client quarantined 33. Meaning of 6276 event ID a) Successful authentication has occurred b) Successful authentication has not occurred c) A configuration problem exists d) NAP client quarantined Day 19 Questions Remote Access options in Windows Server 2012 R2 include: DirectAccess a. VPN b. Routing c. All of the above 1. DirectAccess server deployment options include: a. Supporting multiple domains b. Provisioning Off- premise c. Both a and b d. None of the above 2. DirectAccess tunneling protocols include: a. VPN b. ISATAP c. IP HTTPS d. Routing 3. Planning for internal network configuration requires you to plan for: a. Active Directory b. Firewall Configuration c. Client Deployment d. All of the above 4. Direct Access uses DNS for resolving a. Network Location Server b. Active Directory c. Routing d. VPN 5. You can Configure NRPT by using Group Policy with the a. DNS Suffixes b. Split-brain DNS c. ISATAP d. Both a and b 6. Network location server can be located on a. Direct access server b. Active Directory c. Group Policy Management d. None of the above 7. Requirements for network location server configuration a. Network location server web site certificate b. CA that is trusted by Direct Access Clients c. Both a and b d. None of the above 8. Management servers in DirectAccess are: a. Workgroup b. Domain Controllers c. IPV4 d. IPV6 9. Management servers are detected by DirectAccess a. Automatically b. Manually if modified c. Both a and b d. None of the above 10.Management server requirements a. Must fully support IPv6 b. VPN c. Server d. Active Directory 11.Remote Access Management Console monitoring components a. Dashboard b. Remote Access Reporting c. ISATAP d. VPN 12.You can troubleshoot DirectAccess connectivity by using a. VPN b. Active Directory c. GUI tools d. DNS 13.___________ provides a point to point connection between components of a private network, through a public network such as the internet a. VPN b. Active Directory c. GUI tools d. DNS 14.AD FS includes the following features a. Web SSO b. Enhanced Security c. Extensible Architecture d. All of the above 15.___________ is the Microsoft identity federation solution that can use claims-based authentication a. AD FS b. DNS c. VPN 16.AD FS benefits are a. Workplace join b. SSO c. Both a and b d. None of the above 17.User Settings for Remote Access include a. Network Access Permission b. Verify Caller ID c. Callback options d. All of the above 18.Advanced Direct Access Configuration options include: a. Scalable and customized PKI infrastructure b. Customized network configuration options c. Both a and b d. None of the above 19.VPN server configuration requirements include a. Two network interfaces b. IP Address allocation c. Active Directory d. None of the above 20. You can manage the remote access role by using (A) Remote access management console (B) Routing and Remote access console (C) Windows power shell cdmlets (D) All of the above 21. What is the full form of NAT ? (A) Net Address Translation (B) Network Address Translation 22. What are the permissions for accessing a network access (A) Allow Access (B) Deny Access (C) Control access through NPS network policy (D) All of the above 23. Teredo protocol used by (A)direct access clients with a private IP address behind a NAT device (B)direct access clients with a public IP address (C)Tunnels IPv6 traffic over IPv4 network (D)None of these 24. Direct access tunneling protocols include (A) ISATAP (B) 6to4 (C) Teredo (D) IP HTTPS (E) All of the above 25. Management server requirements are (A) must be accessible for the infrastructure tunnel (B) must fully support IPv6 (C)None of these (D) both b and c 26. By using which connectivity we can troubleshoot direct access connectivity (A) A troubleshooting methodology (B) Command-line tools (C) GUI tools (D) All of the above 27 A VPN provides ___________________ (A) A point - to - point connection between components of a private network, through a public network such as the internet (B) point-to-point configuration 28. How many tunneling protocols are supporting for Windows Server 2012 (A) 4 (B) 2 (C) 1 (D) 0 29. What is the full form of IKEv2 (A) Inter Key Exchange (B) Intermediate Exchange (C) Internet Key Exchange (D) Internet Protocol Key Exchange 30. What is the full form of L2TP (A) Layer 2 Tunneling Protocol (B) Layer to Tunneling Protocol (C) Layer 2 Tunneling Processing 31. What is the security level for the MS-CHAPv2 (A) It provides improvement over PAP (B) It provides stronger security than CHAP (C) It offers the strongest security (D) None of these 32. What is VPN Reconnect? (A) It maintains connectivity across network outages (B) It doesn’t maintain connectivity (C) Transfer the network 33. The VPN server configuration includes (A) IP address allocation and DHCP relay agent consideration (B) Public and Private (C) Membership in the local administrators groups or equivalent (D) All of the above 34. What is the full form of CMAK (A) Complex Manager Administrator Kit (B) Connection Manager Administration Kit (C) Connection Messaging Administration Kit (D) Connection Manager Advanced Kit 35. Web Application Proxy is located in a (A) Perimeter Network (B) Area Network (C) Domain Network (D) Server Network 36. What are the benefits for ADFS (A) Work place join and SSO (B) Multifactor Authentication (C) Multifactor Access Control (D) All of the above 37 VPN is abbreviated as __________ a) Visual Private Network b) Virtual Protocol Network c) Virtual Private Network d) Virtual Protocol Networking 38__________ provides an isolated tunnel across a public network for sending and receiving data privately as if the computing devices were directly connected to the private network. a) Visual Private Network b) Virtual Protocol Network c) Virtual Protocol Networking d) Virtual Private Network 39 Which of the statements are not true to classify VPN systems? a) Protocols used for tunnelling the traffic b) Whether VPNs are providing site-to-site or remote access connection c) Securing the network from bots and malwares d) Levels of security provided for sending and receiving data privately 40 What types of protocols are used in VPNs? a) Application level protocols b) Tunnelling protocols c) Network protocols d) Mailing protocols 41 For secure connection, Remote access VPNs rely on ___________ and ____________ a) IPSec, SSL b) L2TP, SSL c) IPSec, SSH d) SSH, SSL 42 There are ________ types of VPN protocols. a) 3 b) 4 c) 5 d) 6 43 A ______ can hide a user’s browsing activity. a) Firewall b) Antivirus c) Incognito mode d) VPN 44 Using VPN, we can access _______________ a) Access sites that are blocked geographically b) Compromise other’s system remotely c) Hide our personal data in the cloud d) Encrypts our local drive files while transferring 45 A proxy server is used for which of the following? A. To provide security against unauthorized users B. To process client requests for Web pages C. To process client requests for database access D. To provide TCP/IP 46 Which of the following is true concerning Web services standards? A. Led by only one group. B. Helped by cooperation between companies. C. Not necessary at this time. D. Important so that the web can flourish. 47 Whar are the Remote Access server role DirectAccess Routing and Remote Access Web Application Proxy 48 The Routing and Remote Access service (RRAS) supports remote user or siteto-site connectivity by using virtual private network (VPN) or dial-up connections. 49 The Routing and Remote Access service (RRAS) RRAS Multitenant GatewayRemote AccessRouting 50 Web Application Proxy is a new Remote Access role service in Windows Server 2012 R2 Day 20 Questions Q1. Data deduplication optimizes volume by? a. redirecting redundant data to multiple storage point b. redirecting redundant data to single storage point c. concentrating the data on multiple location d. none of above Q2. Data deduplication provide ? a. capital optimization b. scale and performance. c.either a or b d. neither a nor b Q3. Which of the follwing is not provided by data deduplication? a. Reliability and data integrity b. bandwidth efficiency c.simple optimization d. renaming Q4. What are the method of optimizing namespace. a. Renaming or moving a folder b. capital optimization c.scale d. disabling referrals to a folder Q5. In troubleshooting DFS health report tool is used to? a. Generate a test file to verify replication b.Report on the propagation test and provide replication statistics c. Report replication statistics and general health of the topology d.Monitor replication state of the DFS replication service Q6. In troubleshooting DFS Propagation test tool is used to? a. Generate a test file to verify replication b.Report on the propagation test and provide replication statistics c. Report replication statistics and general health of the topology d.Monitor replication state of the DFS replication service Q7. In troubleshooting DFS Dfsrdiag.exe is used to? a. Generate a test file to verify replication b.Report on the propagation test and provide replication statistics c. Report replication statistics and general health of the topology d.Monitor replication state of the DFS replication service Q8. In troubleshooting DFS Propagation report tool is used to? a. Generate a test file to verify replication b.Report on the propagation test and provide replication statistics c. Report replication statistics and general health of the topology d.Monitor replication state of the DFS replication service Q9. Storage Report provides information about………..usage on a file server. A .file B. system C. package Q10. Types of storage reports include ….. A. Duplicate file B. File screening Audit C .Quota usage D. all of the above Q11. Report task specifies … A. the volume and folder to report on B .which report to generate C. both a and b Q12 .File classification allow you to use an automated mechanism to ___ and ____classification Properties to file. A. Create , assign B .delete, assign C. none Q13. what are the characteristics of distributed file system? A . Its user ,servers and storage devices are dispersed. B. Service activity is not carried out across the network. C. They have single centralized data repository D. they are multiple dependent storage devices. Q14. What are not the characteristics of a DFS ? A. login transparency and access transparency B. files need not contain information about their physical location. C. No multiplicity of users. D. No multiplicity of files. Q15. What is the advantage of caching in remote file access? A. Reduced network traffic by retaining recently accessed disk blocks. B. faster network access C. copies of data creates backup automatically D. none of above Q16. What are the advantage of file replication? A. improves availability & performance B. decrease performance C. they are consistent D. improve speed Q17. The implementation of caching and replication does not lead to consistency problems. A. true B. false C. may be D. can’t say Q18. A ——————the group is a group that contains the same users as an OU. (Fill in the blank) A. Operation B. Administration C. Primary D. Shadow Q19. ACL stands for Access Control List A. True B. False Q20. How do you create a group by using Active Directory Users and Computers snap- in? A. Left click the OU in Find which you want to create a group, select New, and choose Group. B. Right-click the OU in Find which you want to create a group, select New, and choose Group. C. This can only be done in the registry editor. D. You can create a group by typing MSCONFIG in the Run box. Q21. LDIFDE is a defragment tool in all versions of Windows Server. A. False B. True Q22. The Dsadd command –secgrp {yes | no} specifies group type: security (yes) or distribution (no). A. False B. True Q23. Find what option can you use to prevent deleting a group in Windows Server 2008? A. You could prevent this by formatting the hard drive. B. You can prevent deleting a group by restarting the computer. C. Protect object from accidental deletion. D. Use /reboot to prevent deleting a group. Q24. There are two types of groups in Active Directory. A. True B. False 8. Find what default group has the right to log on locally, start and stop services, perform backup and restore operations, format disks, create or delete shares, and even power down domain controllers? A. Server Operators B. Schema Admins C. Enterprise Admins D. Backup Operators 9. How many group scopes are there in Active Directory? A. Three B. Zero C. Ten D. Five 10. Find what is the basic syntax for Dsrm? A. dsrm ObjectND.,,(subtree-(+exclude)) (+yesprompt) (*c) B. dsrn ObjectDN. noprompt – c C. dsrm ObjectDN…[-subtree [-exclude]] [-noprompt] [-c] D. dsrm ObjectN…. [-subtree [-exclude]] [noprompt] [c-] 11. Find which is not one of the four divisions or container structures in Active Directory? A. Forests B. Domain C. Webs D. Organizational units E. Sites 12. Find what is a forest? A. Physical groupings are independent of the domain and OU structure. Sites distinguish between locations connected by low- and high-speed connections and are defined by one or more IP subnets. B. The collection of every object, its attributes and attribute syntax in the Active Directory. C. Containers in Find which domains can be grouped. They create a hierarchy for the domain and create the structure of the Active Directory’s company in geographical or organizational terms. D. A collection of computers that share a common set of policies, a name and a database of their members. 13. Find what do domain controllers do? A. Store the database, maintain the policies and provide the authentication of domain logons. B. Control granular settings in a domain environment. C. Receive and relay domain commands 14. Find what are Group Policy Objects? A. A set of folder rules that determine where Outlook will save email messages. B. Affords the capability for secure extension of network operations to the Web C. They determine the hierarchy of a domain, Find which can fit the operational structure of an organization. D. A collection of settings that define Find what a system will look like and how it will behave for a defined group of users. 15. In Windows Server 2012 and Windows 8, Group Policy Objects give administrators the ability to select new Internet Explorer policies. A. True B. False 16. Active Directory Rights Management Services is designed to give complete control of all documents stored in RMS-enabled applications. A. True B. False 17. According to Jonathan Hassell, Find what is a good practice to follow with forest trusts? A. Use shortcut trusts B. Keep a current list of all trust relationships in the forest C. Back up and ensure you have restore capability D. All of the above 18. According to Gary Olsen, domain controller load can be insufficient for the following reason(s): A. Inefficient LDAP queries can put an unpredictable load on DC. B. The number of authenticated clients is unpredictable because multiple DCs share the load for clients in and out of the site. C. Active Directory (AD) analysis and monitoring tools put additional load on the DC. D. A and C only E. A, B, and C 18. About how many settings are in a single Group Policy Object A. 1,800 B. 3,200 C. 900 D. 5,000 19. In Find what version of Windows did Microsoft adopt Kerberos as an authentication policy? A. Windows NT B. Windows Server 2003 R2 C. Windows Server 2000 D. Windows 2008 20. Between Sites, you can also choose to use ________ for replication, but only for changes in the Schema or Configuration. A. Internet Message Access Protocol B. Post Office Protocol C. Simple Mail Transfer Protocol D. E-mail 21. Active Directory and a Windows-based file server are not required to implement ________ on client Windows computers. A. Windows Registry B. Internet Explorer C. Windows 2000 D. Roaming user profile 22. Authentication across this type of trust is Kerberos based (as opposed to ________). A. LM hash B. NTLM C. Samba (software) D. Integrated Windows Authentication 23. Unlike earlier versions of Windows Find which used ________ to communicate, Active Directory is fully integrated with DNS and TCP/IP— indeed DNS is required. A. NetBIOS B. NetBIOS Frames protocol C. Server Message Block D. Ethernet 24. Another option is to use ________ with its translucent overlay, Find which can extend entries in any remote LDAP server with additional attributes stored in a local database. A. Mac OS X B. Berkeley DB C. Berkeley Software Distribution D. OpenLDAP 25. A different ‘cost’ can be given to each link (e.g., DS3, T1, ________, etc.) and the site link topology will be altered accordingly by the KCC. A. OSI model B. Integrated Services Digital Network C. Universal Serial Bus D. Physical Layer 26. AGDLP (implementing ________ using nested groups) A. Mandatory access control B. Active Directory C. Microsoft SQL Server D. Role-based access control 27. Active Directory is a technology created by ________ that provides a variety of network services, including: A. Microsoft B. Internet Explorer C. Microsoft Office D. Microsoft Windows 28. ADAM is capable of running as a service, on computers running Microsoft ________ or Windows XP Professional. A. Windows Server 2003 B. Windows Server 2008 C. Windows 2000 D. Microsoft Windows 29. In ________, ADAM has been renamed AD LDS (Lightweight Directory Services). A. Microsoft Windows B. Windows Vista C. Windows Server 2008 D. Windows 2000 30. To Find which of the following Active Directory containers can Group Policies be applied? A. sites B. OUs C. domains D. all of the above 31. To create a GPO for a domain or an organizational unit, you use either the Active Directory Users and Computers console or the __________. A. Group Policy Maintenance console B. Domain Policy Management console C. Group Policy Management Console D. Active Directory Sites and Services console 32. For each GPO, there is a GPC container stored in the system policies folder in the __________. A. Active Directory Domains and Trusts console B. Active Directory GPO and Sites console C. Active Directory Users and Computers console D. Active Directory Group Policy console 33. Each GPT folder is identified by the ___________ for the GPO. A. GPCID B. GPTID C. GPID D. GUID 34. Group Policy settings are divided into two categories: Computer Configuration settings and __________. A. Policy Configuration settings B. Organizational Configuration settings C. Group Configuration settings D. User Configuration settings 35. Find which of the following containers contains all Registry-based Group Policy settings, including settings for Windows Components, System, and Network? A. Administrative Templates B. Software Templates C. Windows Templates D. Login Settings 36. Find which of the following is a function of the GPMC? A. It can be used to link sites, search for sites, and to delegate Group Policy-related features. B. It can be used to sign and encrypt all LDAP communications. C. It provides administrators with the ability to back up, restore, import, and copy/paste GPOs, as well as to create, delete, and rename them. D. It can be used to view all Group Policy management functions. 37. Find which of the following are exceptions to the order in Find which GPOs are processed? A. The default order for processing Group policy settings is also affected by selecting the Enforced setting. B. You can modify the default behavior by using the Block Inheritance option. C. If a computer belongs to a workgroup, it processes only local GPOs. D. all of the above 38. when you configure loopback in ________ mode, the Computer Configuration GPO settings are appended to the default list of GPOs. A. Replace B. Merge C. Default D. Append 39. In order to delegate permissions for a GPO, you must have the ___________ permission for the GPO. A. Edit user, context, menu B. Edit settings, delete and modify the security C. Edit group, delete, modify user D. none of the above 40. The GPMC combines the functionality of the ACL Editor, Delegation Wizard, and Resultant Set of the Policy tool. A. True B. False 41. The GPT contains all of the Registry entries, as well as associated files and folders required to implement the various GPO functions. A. True B. False 42. Administrative settings are used to determine the applications that will be distributed to computers or users via a GPO. A. True B. False 43. The User Group Policy loopback processing mode is used when both the user account and the computer account are members of a Windows 2000 or later domain. A. True B. False 44. You assign permissions to delegate administrative control over a GPO on the Delegation tab in the GPMC. A. True B. False [Show More]
Last updated: 1 year ago
Preview 1 out of 69 pages

Reviews( 0 )
Recommended For You
Business> QUESTIONS & ANSWERS > CLM 031 EXAM (All)

CLM 031 EXAM
CLM 031 = 100% Question 1: 5b Select the statement that is correct concerning performance work statement (PWS) requirements: - All answers are correct. - PWS should describe requirements necessary...
By Book Worm, Certified , Uploaded: Nov 03, 2022
$5
*NURSING> QUESTIONS & ANSWERS > PHIL 347 Week 6 Checkpoint Quiz. Score 100/100 (All)
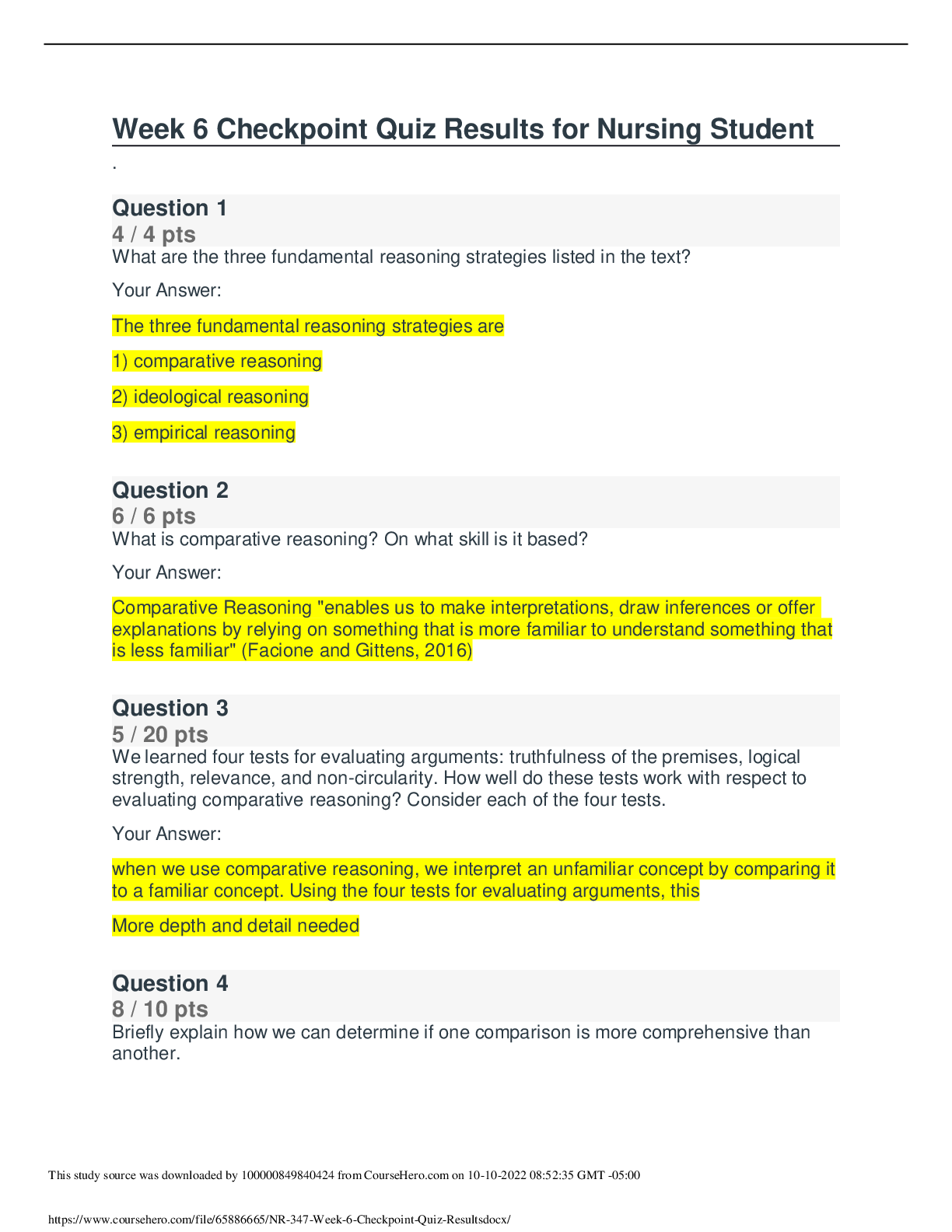
PHIL 347 Week 6 Checkpoint Quiz. Score 100/100
Question: What are the three fundamental reasoning strategies listed in the text? Question: What is comparative reasoning? On what skill is it based? Question: We learned four tests for evaluating...
By Amanda Rosales , Uploaded: Mar 24, 2021
$7
Business> QUESTIONS & ANSWERS > BUSINESS 1007 (All)
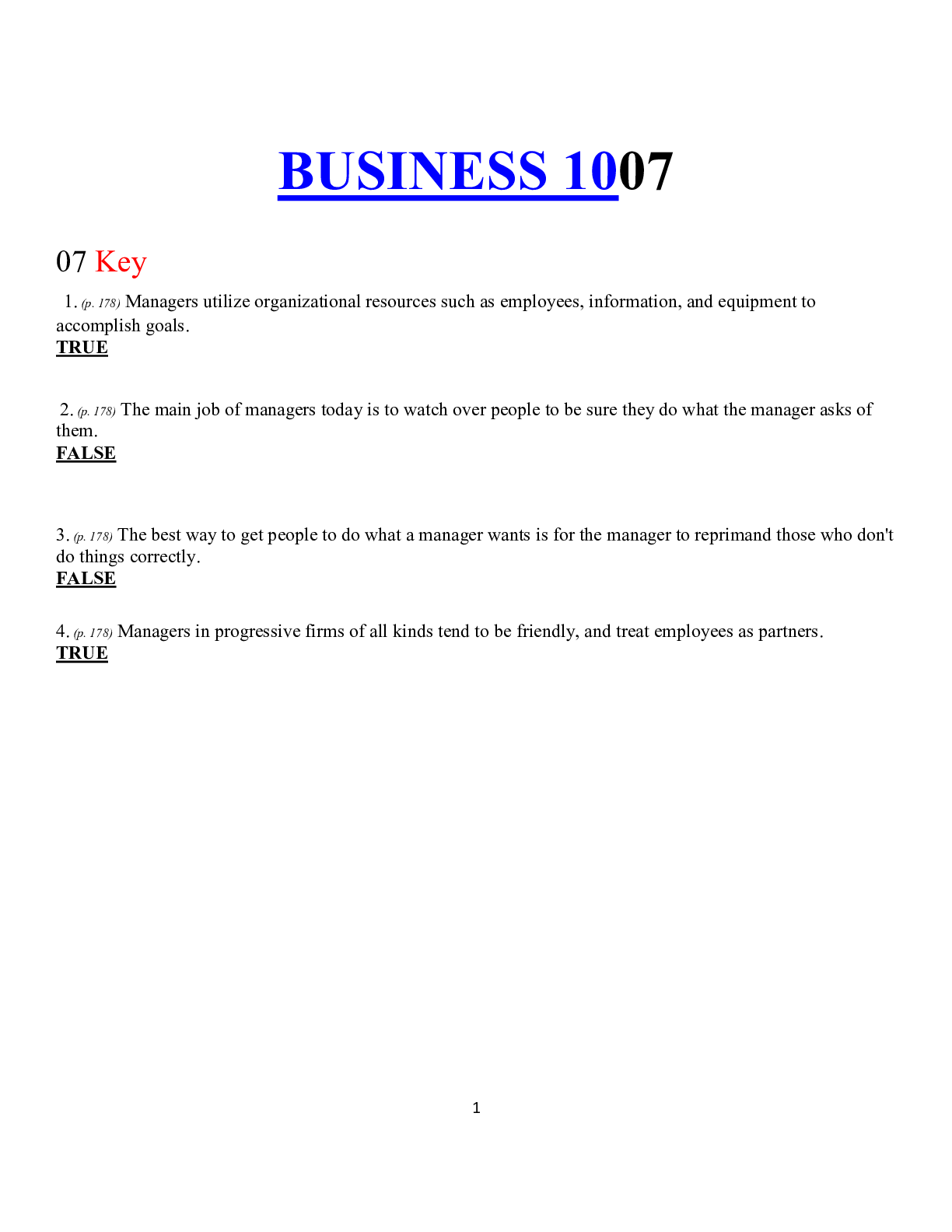
BUSINESS 1007
BUSINESS 1007 07 Key 1. (p. 178) Managers utilize organizational resources such as employees, information, and equipment to accomplish goals. 2. (p. 178) The main job of managers today is to w...
By Kirsch , Uploaded: Oct 19, 2019
$6
Anthropology> QUESTIONS & ANSWERS > KOR 352 FA19 101 week 8 Quiz. Already Graded A (All)

KOR 352 FA19 101 week 8 Quiz. Already Graded A
KOR 352 FA19 101: Week 8 Quiz Question 1 (0.25 points) Which of the following is not true of Kim and Finch’s observations during their field research in South Korea from 1997 to 2000? Question 1 o...
By Kirsch , Uploaded: Oct 17, 2019
$9
E-Commerce> QUESTIONS & ANSWERS > ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score (All)
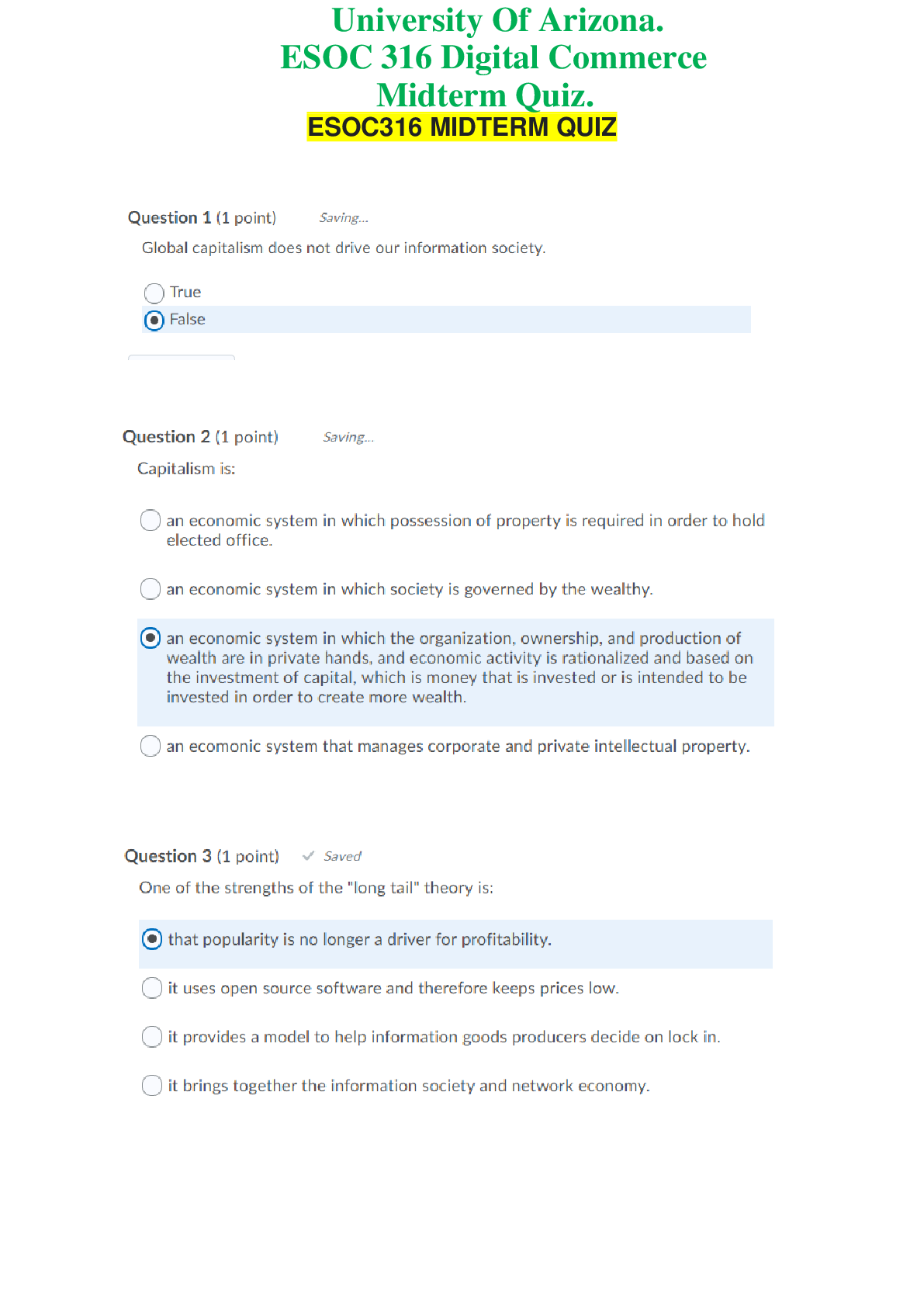
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score
ESOC 316 Digital Commerce - University Of Arizona. Midterm Quiz. 20 Q&A. 100% Score ESOC316 MIDTERM QUIZQuestion 6 (1 point) Saved Information has several properties that make information goods...
By Kirsch , Uploaded: Oct 15, 2019
$9.5
Marketing> QUESTIONS & ANSWERS > Marketing Management Chapter 2 to Chapter 10 Q&A (All)

Marketing Management Chapter 2 to Chapter 10 Q&A
Chapter 2 to Chapter 10 Chapter 2: Developing Marketing Strategies and Plans GENERAL CONCEPT QUESTIONS Multiple Choice 66 Chapter 1: Marketing: Managing Profitable Customer Relationships...
By Kirsch , Uploaded: Oct 14, 2019
$10
Marketing> QUESTIONS & ANSWERS > MKT 530 Customer Relationship Management. 155 Questions and Answers (All)

MKT 530 Customer Relationship Management. 155 Questions and Answers
MKT 530 All Questions and Answers MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) As the manager of an organization that is att...
By Kirsch , Uploaded: Oct 14, 2019
$10
Art> QUESTIONS & ANSWERS > MAS 337 Exam 1. Graded A (All)

MAS 337 Exam 1. Graded A
MAS 337 Exam 1 Match the son with its corresponding region. 1.Oaxaca 2.Veracruz 3.Michoacan 4.Jalisco 5.Hidalgo 1. Son istemeno 2. Son Jarocho 3. Son Abajeno 4. Son Jalisciense 5. Son Huast...
By Kirsch , Uploaded: Oct 14, 2019
$6
Art> QUESTIONS & ANSWERS > MUS 337 Final Exam Graded 100%. (All)

MUS 337 Final Exam Graded 100%.
MUS 337 Final Daisy Moreno-Cota Fri Dec 11 12:59:42 PST 2015 Tone or aural color Volume and articulation of sounds Frequency of the tone Phonic structure or relationships between the sounds Dura...
By Kirsch , Uploaded: Oct 12, 2019
$9
Art> QUESTIONS & ANSWERS > MUS 337 Final. Graded 100%. (All)

MUS 337 Final. Graded 100%.
MUS 337 Final Daisy Moreno-Cota Fri Dec 11 12:59:42 PST 2015 Tone or aural color Volume and articulation of sounds Frequency of the tone Phonic structure or relationships between the sounds Dura...
By Kirsch , Uploaded: Oct 12, 2019
$9
Document information
Connected school, study & course
About the document
Uploaded On
Nov 16, 2022
Number of pages
69
Written in
Additional information
This document has been written for:
Uploaded
Nov 16, 2022
Downloads
0
Views
132






