Information Technology > EXAM > SOPHIA PATHWAY Information Technology Unit 3 - Milestone 3. (Already Passed) 100% Correct (Fall 2020 (All)
SOPHIA PATHWAY Information Technology Unit 3 - Milestone 3. (Already Passed) 100% Correct (Fall 2020)
Document Content and Description Below
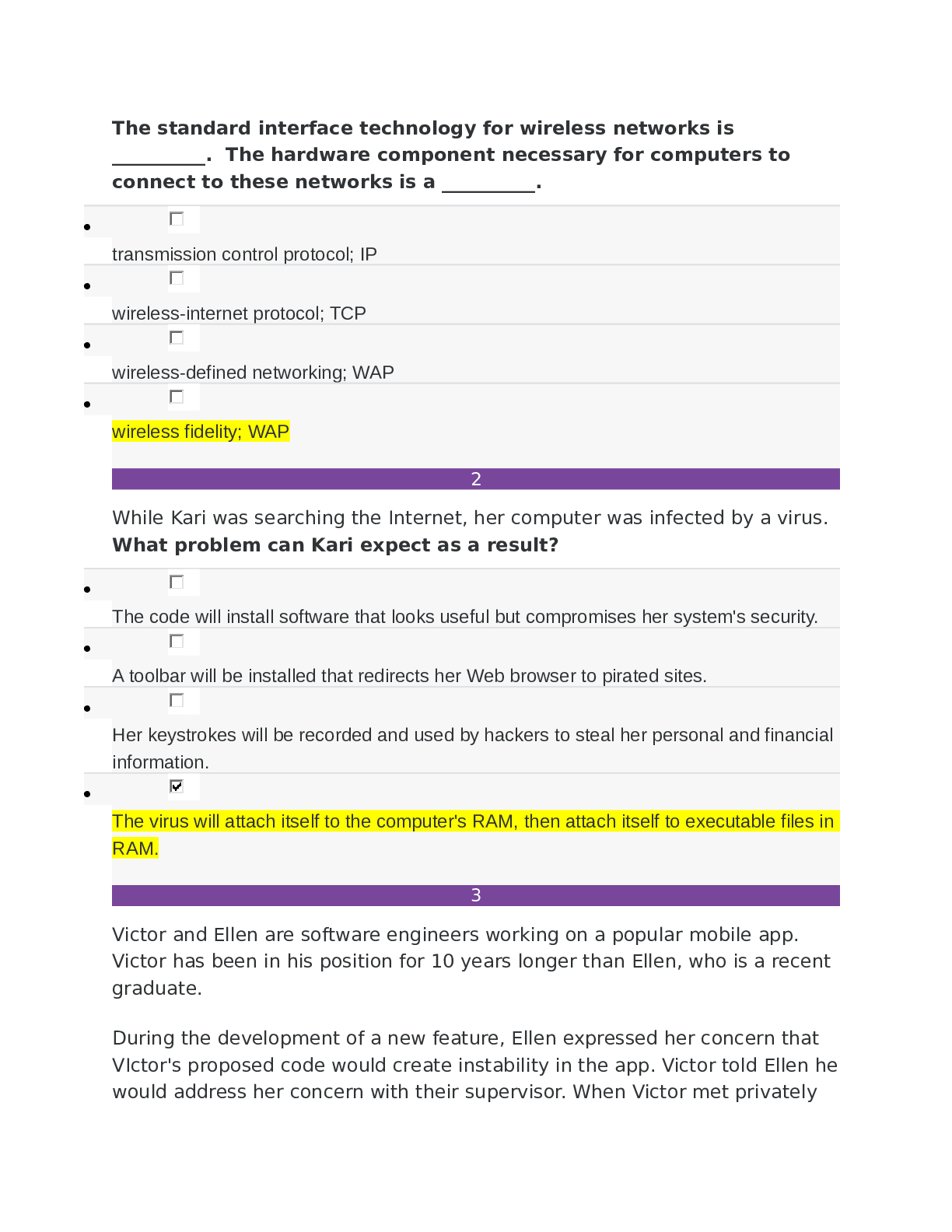
SOPHIA PATHWAY Information Technology Unit 3 - Milestone 3. The standard interface technology for wireless networks is __________. The hardware component necessary for computers to connect to thes... e networks is a __________. • transmission control protocol; IP • wireless-internet protocol; TCP • wireless-defined networking; WAP • wireless fidelity; WAP 2 While Kari was searching the Internet, her computer was infected by a virus. What problem can Kari expect as a result? • The code will install software that looks useful but compromises her system's security. • A toolbar will be installed that redirects her Web browser to pirated sites. • Her keystrokes will be recorded and used by hackers to steal her personal and financial information. • The virus will attach itself to the computer's RAM, then attach itself to executable files in RAM. 3 Victor and Ellen are software engineers working on a popular mobile app. Victor has been in his position for 10 years longer than Ellen, who is a recent graduate. During the development of a new feature, Ellen expressed her concern that VIctor's proposed code would create instability in the app. Victor told Ellen he would address her concern with their supervisor. When Victor met privately with his supervisor, he claimed that he had discovered the problem, and that Ellen had dismissed it. Which principle of the Software Engineering Code of Ethics has Victor violated? • Principle 8: Self • Principle 7: Colleagues • Principle 3: Product • • Principle 6: Profession 4 Select the true statement about COPPA. • The COPPA regulations state that websites may not collect information from minors under the age of 13. • The COPPA regulations apply to websites that collect information from children. • The COPPA regulations require that parents of children under the age of 13 be given instructions on how to maintain privacy. • The COPPA regulations restrict a child's access to harmful content. - Protecting Minors from Online Dangers 5 Select the sign of computer addiction that indicates a lack of control. • While driving his car, Mitch rear-ended another car when he was checking his social media account. • After moving to a new town, Sal spends most of his time online to keep his mind off the friends he misses. • Ever since his mother died, Charlie stays up late every night playing an online game. • Even though she knows that she should, Jacqueline cannot stop playing her favorite online game. Computer Addiction 6 Kirby visited a sweepstakes website and agreed to download a new program. Later, when he tried to use a word processing program, his document files became corrupted. How can Kirby try to remove the offending program and prevent future attacks? • Kirby should run an antivirus program. • Kirby should install a biometric reader. • Kirby should use WPA network encryption. • Kirby should change the password on his computer. Network Security 7 Select the FALSE statement about the history of the Internet. • The Internet means “an interconnected network of networks.” • ARPANET began transmission in 1969, when it connected computers at UCLA, Stanford, MIT, and the University of Utah. • The U.S. government created ARPA in response to the successful launch of a satellite by the Soviet Union. • The invention of HTML enabled computers on different networks to communicate with each other. The World Wide Web 8 Which of the following can be controlled by copyright? • The team logo for a minor league baseball team • A new type of engine for pickup trucks • The slogan for a business • A writer’s new murder mystery on the New York Times bestsellers list Copyright, Trademark and Intellectual Property 9 Select the true statement about HTML. • HTML stands for hidden transfer markup language. • The web consists of documents written in HTTP and transmitted by HTML. • An HTML tag initiates a protocol known as HTTP. • The final product transmitted to a browser is in HTML. Website Development 10 In which of the following scenarios can a trademark be applied? • Merle designs a web page for Peter’s business. • Mark writes and records a new song for his rock band. • Peter names his new business “Garden Ornaments.” • Twila paints a picture of Hawaiian scenery. Copyright, Trademark and Intellectual Property 11 Select the scenario that demonstrates plagiarism. • In a blog post, Katriana paraphrases portions of an interview about her favorite author, and includes a hyperlink to the interview. • In his essay, James rewords a paragraph about an idea that he got from another author, without naming the author. • Savasha uses open source software to develop a new web design manual for her sales company. • Carissa downloads an entire album of music from a file-sharing website. Ethical Behavior in the Digital World 12 Select the true statement about network protocols. • Communication cannot take place unless the protocol is executed in the same way on all devices. • One function of a protocol is to decompress data when it is delivered to the receiving computer. • Computers that are distributed across a large geographic area need a special protocol to resolve errors. • Using a protocol other than TCP/IP can result in data loss. Introduction to Computer Networks 13 Amanda and her family recently moved into a new home. Everyone has their own tablet, and wants to connect to the same network, no matter where they are in the house. Which type of network is best for Amanda and her family? • PAN • MAN • WAN • LAN Computer Network Types 14 Genevieve is a student who attends classes at a campus downtown. She likes to study in the college's coffee shop, where she often accesses the Internet through the college's wireless network. Which network type is Genevieve using? • MAN • PAN • LAN • WAN Computer Network Types 15 Select the social media site that is an idea-sharing website. • Pinterest • Google+ • QQ • QZone In which of the following scenarios can a trademark be applied? • Mark writes and records a new song for his rock band. • Twila paints a picture of Hawaiian scenery. • Peter names his new business “Garden Ornaments.” • Merle designs a web page for Peter’s business. RATIONALE The main difference between copyright and trademark is that a copyright protects content and a trademark protects a brand. Twila, Merle, and Mark are protected by copyright because they are the creators of particular content. Peter's business brand is protected by trademark. CONCEPT Copyright, Trademark and Intellectual Property 2 Select the scenario that demonstrates plagiarism. • Dylan contributes some of his own research to an entry on Wikipedia, and includes a citation for his recent book. • Allison makes a video of herself using sound effects that she clipped from the soundtrack of a popular action movie to market her business. • Summer finds a recent magazine article about an issue that she wants to discuss with her class, so she makes copies of it for the students. • Joseph finds a written passage about a new idea to stop cyberbullying and pastes it into his blog entry without giving credit to its author. RATIONALE Joseph is guilty of plagiarism because he copied a written passage about a new idea to stop cyberbullying into his own blog entry without citation. It is important to cite sources when referring to the work of another. Allison could be guilty of copyright infringement because she used the soundtrack of a popular action movie without prior consent. Because she is sharing a recent article with students, Summer's actions likely fall under fair use. Dylan is not at risk for copyright infringement because he cites his own work. CONCEPT Ethical Behavior in the Digital World 3 Amanda and her family recently moved into a new home. Everyone has their own tablet, and wants to connect to the same network, no matter where they are in the house. Which type of network is best for Amanda and her family? • LAN • PAN • WAN • MAN RATIONALE The most suitable network for Amanda and her family is a LAN (Local Area Network) because it connects devices in a small area (e.g., a home or group of homes). A LAN would enable Amanda and other family members to take their tablets anywhere in the house and remain connected. CONCEPT Computer Network Types 4 Select the FALSE statement about the history of the Internet. • The U.S. government created ARPA in response to the successful launch of a satellite by the Soviet Union. • ARPANET began transmission in 1969, when it connected computers at UCLA, Stanford, MIT, and the University of Utah. • The invention of HTML enabled computers on different networks to communicate with each other. • The Internet means “an interconnected network of networks.” RATIONALE The launch of Sputnik by the Soviet Union motivated the U.S. to develop technology that enabled data transmission between computers. APRANET connected computers at UCLA, Stanford, MIT and the University of Utah in 1969. ARPANET was a predecessor of the Internet — "an interconnected network of networks." The invention of TCP/IP in 1982 provided an intermediary protocol that enabled computers on different networks to communicate with each other. HTML (Hypertext Markup Language) is the language in which most web content is written, and is a fundamental component of the "World Wide Web." CONCEPT The World Wide Web 5 Select the true statement about network protocols. • Protocols determine the best method for resolving errors with data encryption. • Every computer uses the same protocol to communicate, regardless of the network type. • The primary function of a protocol is to compress data to reduce storage requirements. • A protocol is a rule for transmitting data between computing devices. RATIONALE A protocol is a rule for transmitting data between devices. A protocol specifies how data is transmitted, but does not resolve errors or process data. To communicate, connected devices must execute the protocol in the same way, but there are different protocols for different networks. CONCEPT Introduction to Computer Networks 6 While Kari was searching the Internet, her computer was infected by a virus. What problem can Kari expect as a result? • The code will install software that looks useful but compromises her system's security. • A toolbar will be installed that redirects her Web browser to pirated sites. • The virus will attach itself to the computer's RAM, then attach itself to executable files in RAM. • Her keystrokes will be recorded and used by hackers to steal her personal and financial information. RATIONALE A computer virus is a program that is usually hidden within another, seemingly-innocuous program. Viruses produce copies of themselves, and insert those copies into other programs or files. Viruses usually perform a malicious action (e.g., destroying data). CONCEPT Network Security 7 Select the true statement about HTML. • HTML is a language that is used to create Web pages. • HTML tags tell a web browser when to run HTTP sequences. • HTML is used to distribute websites. • HTML supports the delivery of Web pages through HTTP. RATIONALE Hypertext markup language (HTML) is the most basic building block of the Web. It is used to apply structure and format to the content of Web pages. In addition to HTML, other tools are used to add interactivity and other functionality to Web pages. CONCEPT Website Development 8 Select the true statement about COPPA. • The COPPA regulations require that parents of children under the age of 13 be given instructions on how to maintain privacy. • The COPPA regulations state that websites may not collect information from minors under the age of 13. • The COPPA regulations restrict a child's access to harmful content. • The COPPA regulations apply to websites that collect information from children. RATIONALE The Children's Online Privacy Protection Act (COPPA) manages regulations that apply to websites which collect information from children. The Act establishes criteria to be used to determine whether a website or online service is directed at children. These include the following: the subject matter of the site or service, its visual content, the use of animated characters or child-oriented activities and incentives, music or other audio content, the age of models, the presence of child celebrities or celebrities who appeal to children, language or other characteristics of the website or online service, and whether advertising promoting or appearing on the website or online service is directed at children. CONCEPT Protecting Minors from Online Dangers 9 Which of the following can be controlled by copyright? • The name of a college football team • A song written by the Beatles • The Adidas stripe logo • The advertising slogan for a national car sales chain RATIONALE Copyright cannot protect the Adidas stripes logo, the advertising logo, or the football team name, but all three can be trademarked. Copyright can protect a song written by the Beatles. Copyright protects original works of authorship including literary, dramatic, musical, and artistic works (e.g., poetry, novels, movies, songs, photographs, drawings, computer software, and architecture). CONCEPT Copyright, Trademark and Intellectual Property 10 The standard interface technology for wireless networks is __________. The hardware component necessary for computers to connect to these networks is a __________. • wireless fidelity; WAP • wireless-internet protocol; TCP • transmission control protocol; IP • wireless-defined networking; WAP RATIONALE Wireless fidelity (Wi-Fi) is the standard interface technology for wireless networks. WAP (Wireless Access Point) is a network hardware component that enables computers on a network to connect wirelessly. CONCEPT Computer Network Components 11 Select the sign of computer addiction that indicates neglect. • Fearing she would lose her place in the standings of an online game, Rachel declined to attend her cousin's wedding. • When confronted by her employer about the amount of time she spent checking her social media account at work, Heidi claimed that she only checks it during her breaks, and at lunch. • When confronted by his parents about the excessive amount of time he spent playing video games, Tom claims that he plays for only an hour every day. • While waiting in the light-rail station, David became so absorbed in an online political post that he missed his train and was late for work. RATIONALE Rachel declined to attend her cousin's wedding in order to keep playing an online game. This is clear evidence of neglect. CONCEPT Computer Addiction 12 Select the social media site that is an idea-sharing website. • QZone • Google+ • Pinterest • QQ RATIONALE Pinterest is an online service that enables users to catalog and share websites. Users have "boards" that enable them to categorize ideas and share them with the public. CONCEPT Benefits and Risks of Social Media 13 Genevieve is a student who attends classes at a campus downtown. She likes to study in the college's coffee shop, where she often accesses the Internet through the college's wireless network. Which network type is Genevieve using? • LAN • MAN • WAN • PAN RATIONALE A metropolitan area network (MAN) is a computer network that connects users with computer resources in a geographic area that is larger than the area covered by a local area network (LAN), but smaller than the area covered by a wide area network (WAN). CONCEPT Computer Network Types 14 Gilbert is an independent consultant who helps organizations select the right accounting software for their needs. After evaluating a local nonprofit organization, Gilbert recommended an accounting software package that he believes meets specifications, secures documents, and satisfies user requirements. Gilbert did not tell his client that he owns a 25% share in the business that developed the software, and that he will benefit if the organization decides to purchase the software he recommends. Which principle of the Software Engineering Code of Ethics has Gilbert violated? • Principle 4: Judgment • Principle 3: Product • Principle 1: Public • Principle 2: Client and Employer RATIONALE Gilbert has violated the "judgment" principle established by the Software Engineering Code of Ethics. This principle states that software engineers must maintain integrity and independence in their professional judgment. This includes disclosing conflicts of interest. GIlbert's selection of this product involves an obvious conflict of interest. He should have informed his client about his ties to the software development company. CONCEPT Professional Code of Ethics 15 Eva downloaded an audio file from a file-sharing website. The download contained a file that recorded her computer usage without her knowledge or consent. What should Eva do to remove the offending program, and prevent future attacks? • Eva should run an anti-spyware program. • Eva should change her method of user authentication. • Eva should upgrade her system to WPA encryption. • Eva should run an antivirus program. [Show More]
Last updated: 1 year ago
Preview 1 out of 18 pages
Reviews( 0 )
Recommended For You
Human Resource Management> EXAM > Sophia Art History I Unit 3 - Milestone 3, Questions with Complete Answers (All)

Sophia Art History I Unit 3 - Milestone 3, Questions with Complete Answers
Sophia Art History I Unit 3 - Milestone 3, Questions with Complete Answers
By [email protected] , Uploaded: Jul 06, 2021
$20
Human Resource Management> EXAM > Sophia Art History I Unit 3 - Milestone 3, Questions with Complete Answers (All)

Sophia Art History I Unit 3 - Milestone 3, Questions with Complete Answers
Sophia Art History I Unit 3 - Milestone 3, Questions with Complete Answers
By merit95 , Uploaded: Jul 06, 2021
$19
Public Relations> EXAM > CONCEPTS 1101 Unit 3 milestone, Latest 100% all answered correct (Fall 2020) (All)
CONCEPTS 1101 Unit 3 milestone, Latest 100% all answered correct (Fall 2020)
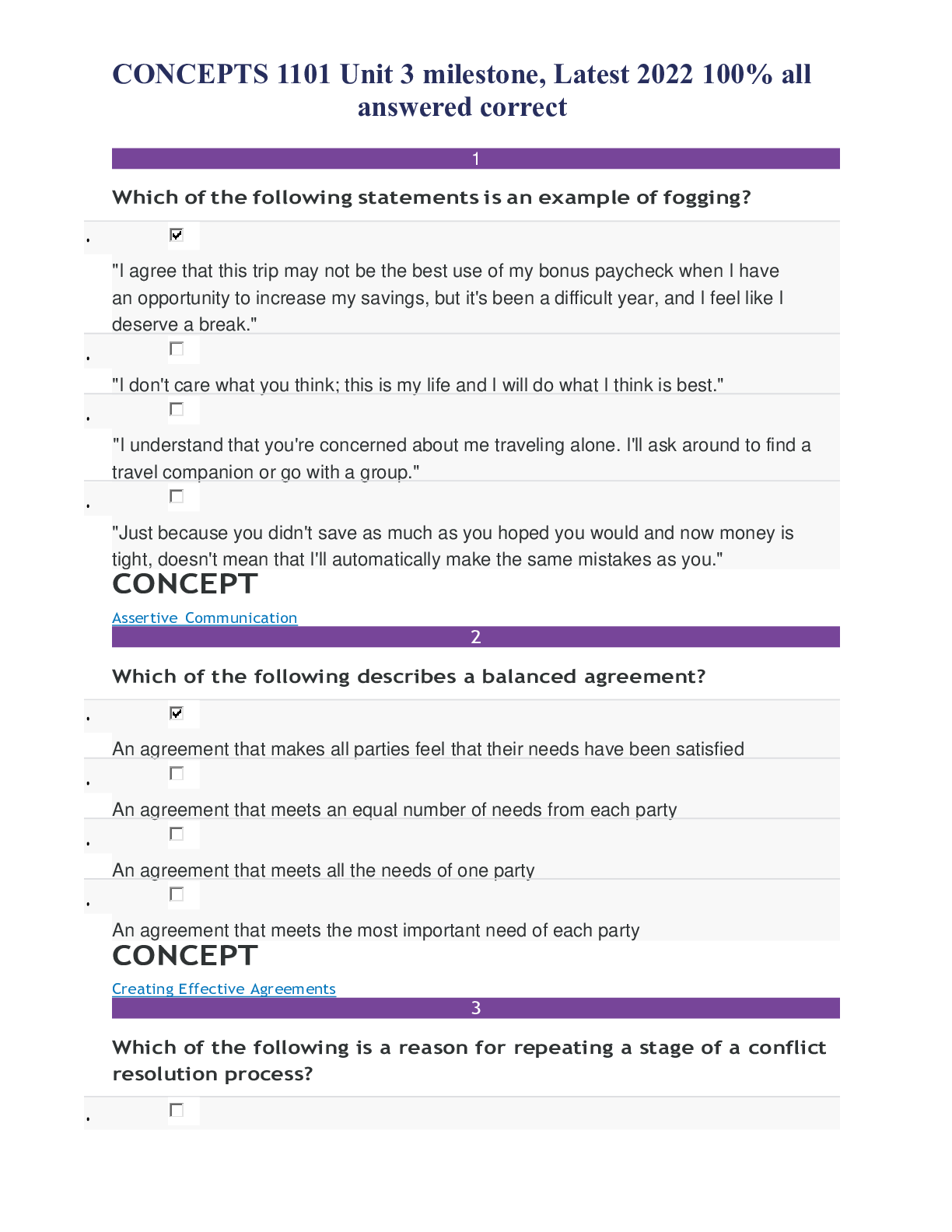
CONCEPTS 1101 Unit 3 milestone 1 Which of the following statements is an example of fogging? • "I agree that this trip may not be the best use of my bonus paycheck when I have an opportunity to...
By Expert#1 , Uploaded: Aug 20, 2020
$12
Health Care> EXAM > Project management BUS 375| SOPHIA PM UNIT 3 - MILESTONE 3| questions with complete solutions (All)

Project management BUS 375| SOPHIA PM UNIT 3 - MILESTONE 3| questions with complete solutions
Stephon's homeowner's association rejects the roofing material he planned to use when adding a large, covered deck to his home. Which of the following is the next step Stephon will take to manage the...
By Tiara , Uploaded: Nov 23, 2022
$4
Business> EXAM > BTEC L3 Information Technology Unit 1 - Exam Theory (Latest 2023/2024) Verified Answers (All)

BTEC L3 Information Technology Unit 1 - Exam Theory (Latest 2023/2024) Verified Answers
BTEC L3 Information Technology Unit 1 - Exam Theory (Latest 2023/2024) Verified Answers
By kofee , Uploaded: Jan 09, 2023
$15
ATI MED SURG PROCTORED> EXAM > Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN (All)
Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN
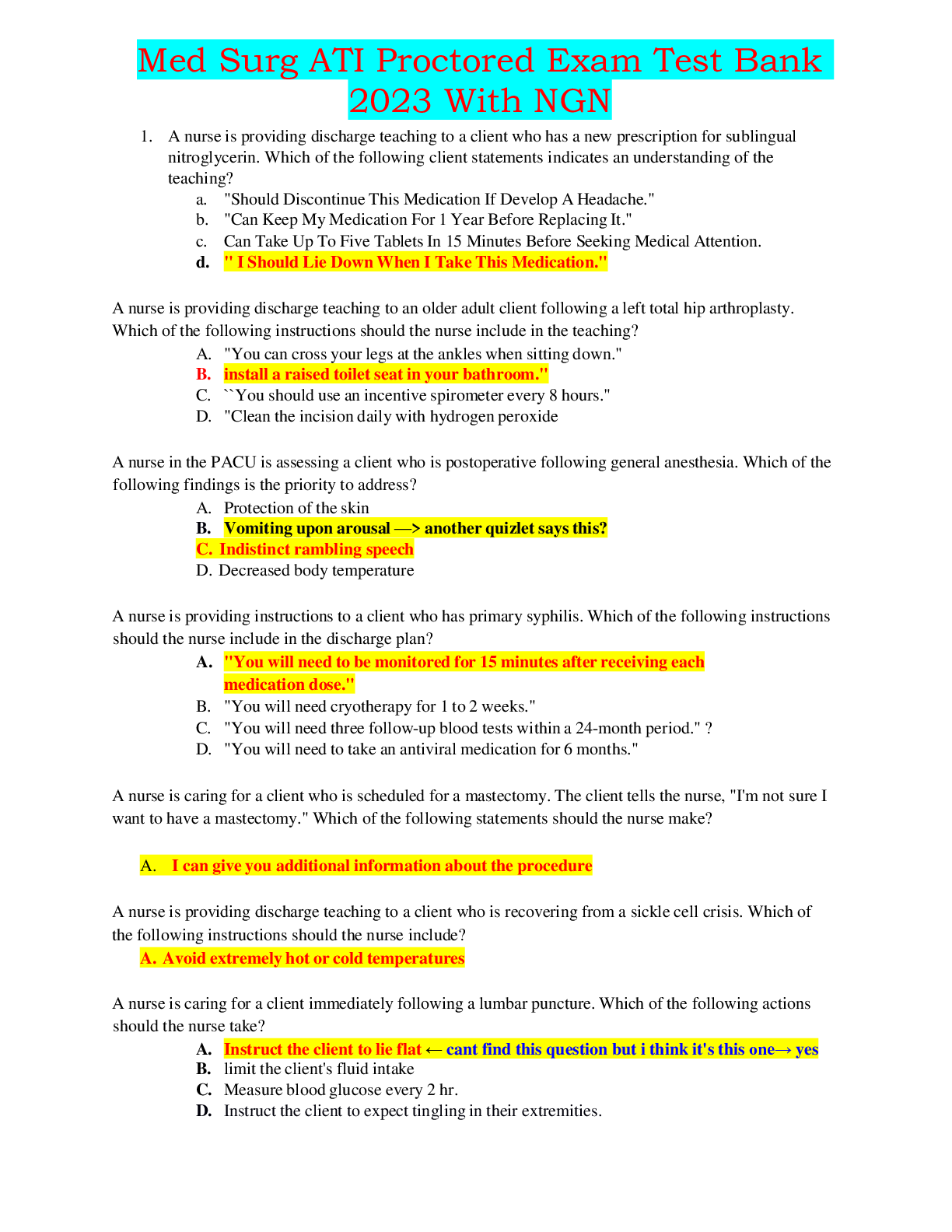
Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN Med Surg ATI Proctored Exam Test Bank 2023/2024 With NGN Med Surg ATI Proctored E...
By EXAMHUB SOLUTIONS , Uploaded: Apr 15, 2024
$30.5
NURSING.> EXAM > ATI RN CUSTOM; MENTAL HEALTH NEXT GEN (All)
ATI RN CUSTOM; MENTAL HEALTH NEXT GEN
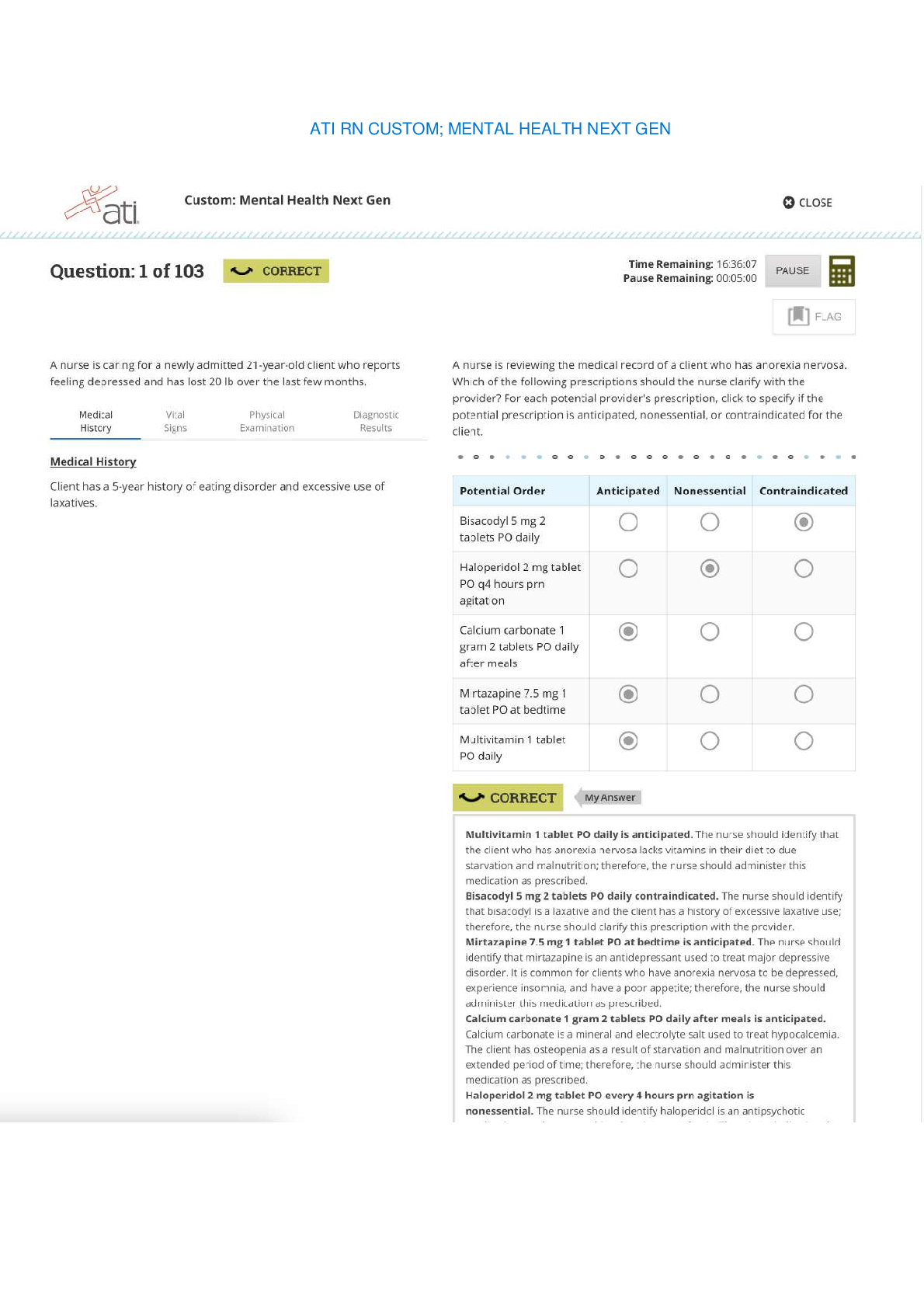
ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GEN ATI RN CUSTOM; MENTAL HEALTH NEXT GE...
By EXAMHUB SOLUTIONS , Uploaded: Apr 05, 2024
$45.5
ATI Med Surg> EXAM > RN ATI MED SURG ALTERATIONS IN KIDNEY FUNCTION AND ELIMINATION ASSESSMENT. (All)
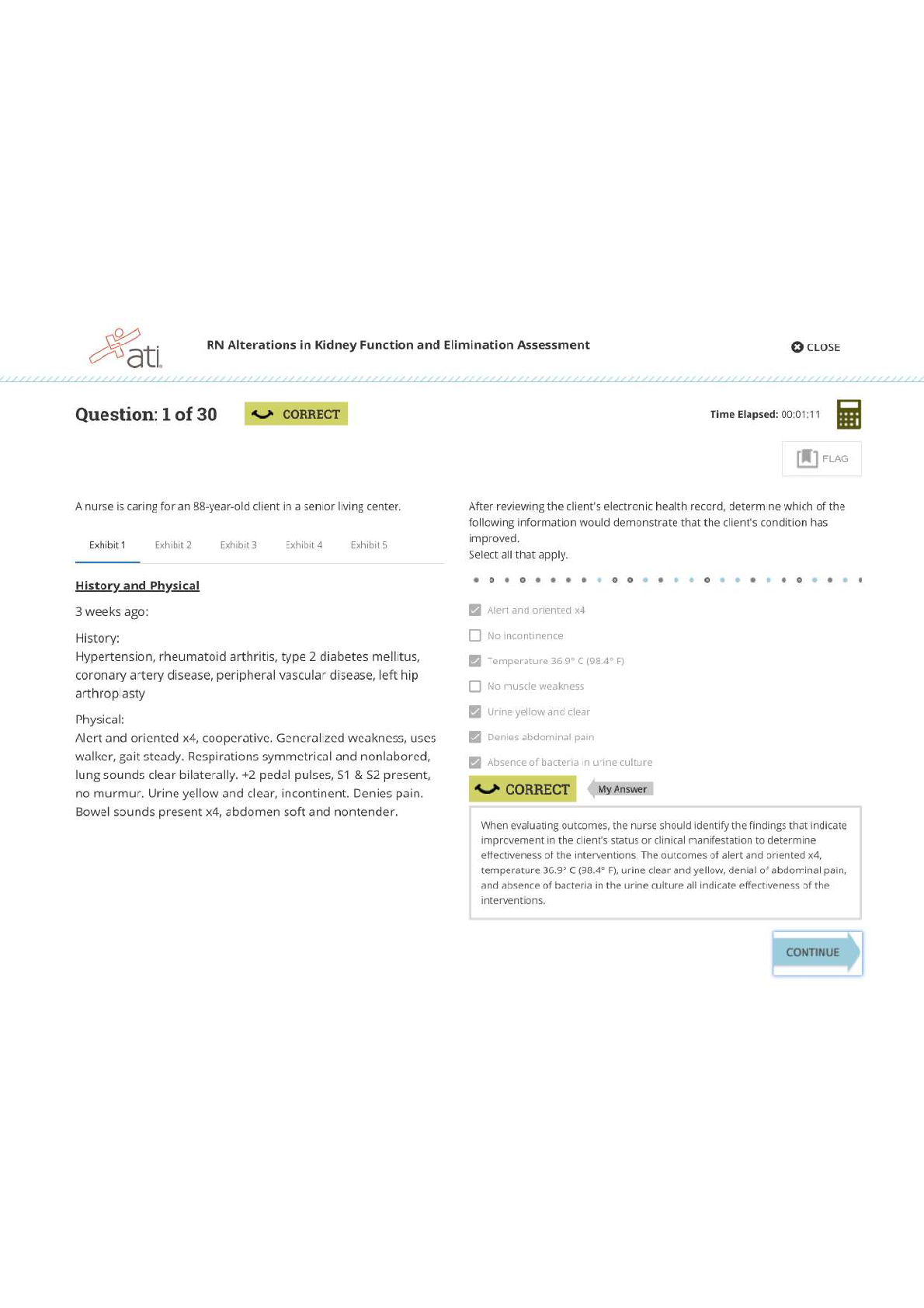
RN ATI MED SURG ALTERATIONS IN KIDNEY FUNCTION AND ELIMINATION ASSESSMENT.
RN ATI MED SURG ALTERATIONS IN KIDNEY FUNCTION AND ELIMINATION ASSESSMENT. RN ATI MED SURG ALTERATIONS IN KIDNEY FUNCTION AND ELIMINATION ASSESSMENT. RN ATI MED SURG ALTERATIONS IN KIDNEY FUNCTI...
By EXAMHUB SOLUTIONS , Uploaded: Apr 10, 2024
$28.5
Nutrition> EXAM > Nutrition Through the Life Cycle EXAM 2. 50 Questions & Answers. (Score 100%) (All)
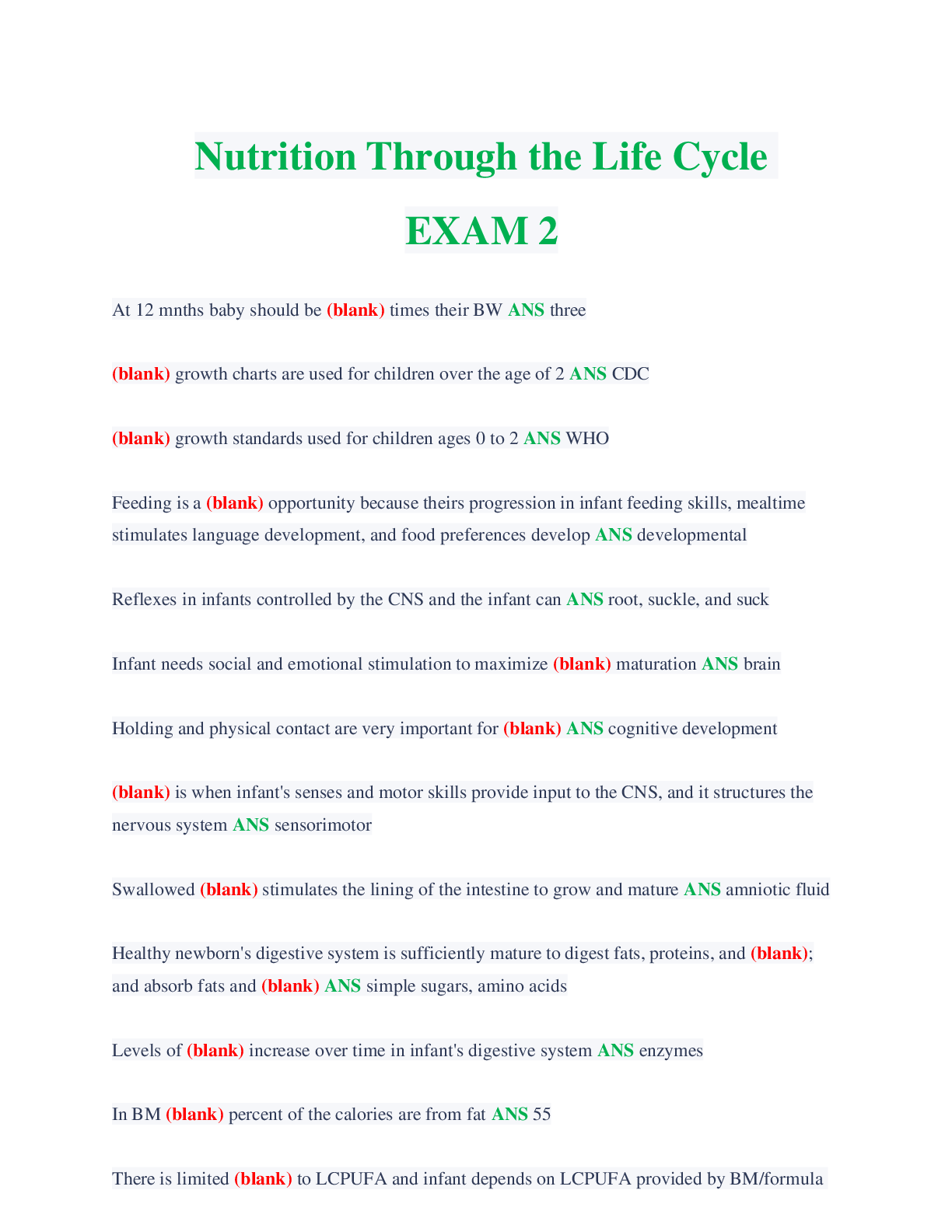
Nutrition Through the Life Cycle EXAM 2. 50 Questions & Answers. (Score 100%)
Nutrition Through the Life Cycle EXAM 2 Latest
By Academic mines , Uploaded: Apr 27, 2023
$10
*NURSING> EXAM > NGR 6172 Pharm Midterm Exam- Questions and Answers. Score 98% (All)
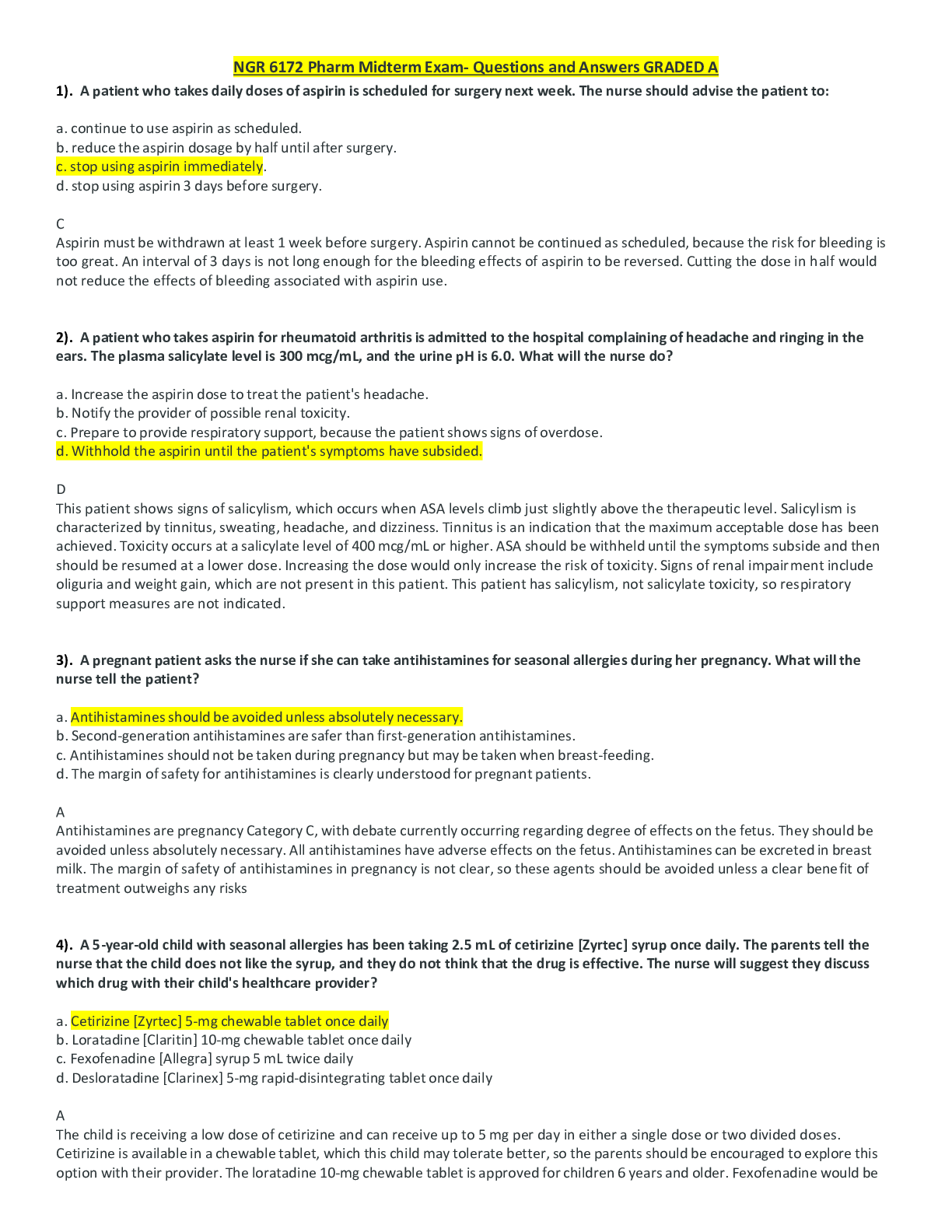
NGR 6172 Pharm Midterm Exam- Questions and Answers. Score 98%
NGR 6172 Pharm Midterm Exam- Questions and Answers GRADED A-1). A patient who takes daily doses of aspirin is scheduled for surgery next week. The nurse should advise the patient to: a. continue to...
By PROF , Uploaded: Feb 01, 2022
$11
Document information
Connected school, study & course
About the document
Uploaded On
Aug 14, 2020
Number of pages
18
Written in
Additional information
This document has been written for:
Uploaded
Aug 14, 2020
Downloads
0
Views
246






