SPēD SFPC: All Areas Exam Questions and Answers (Graded A)
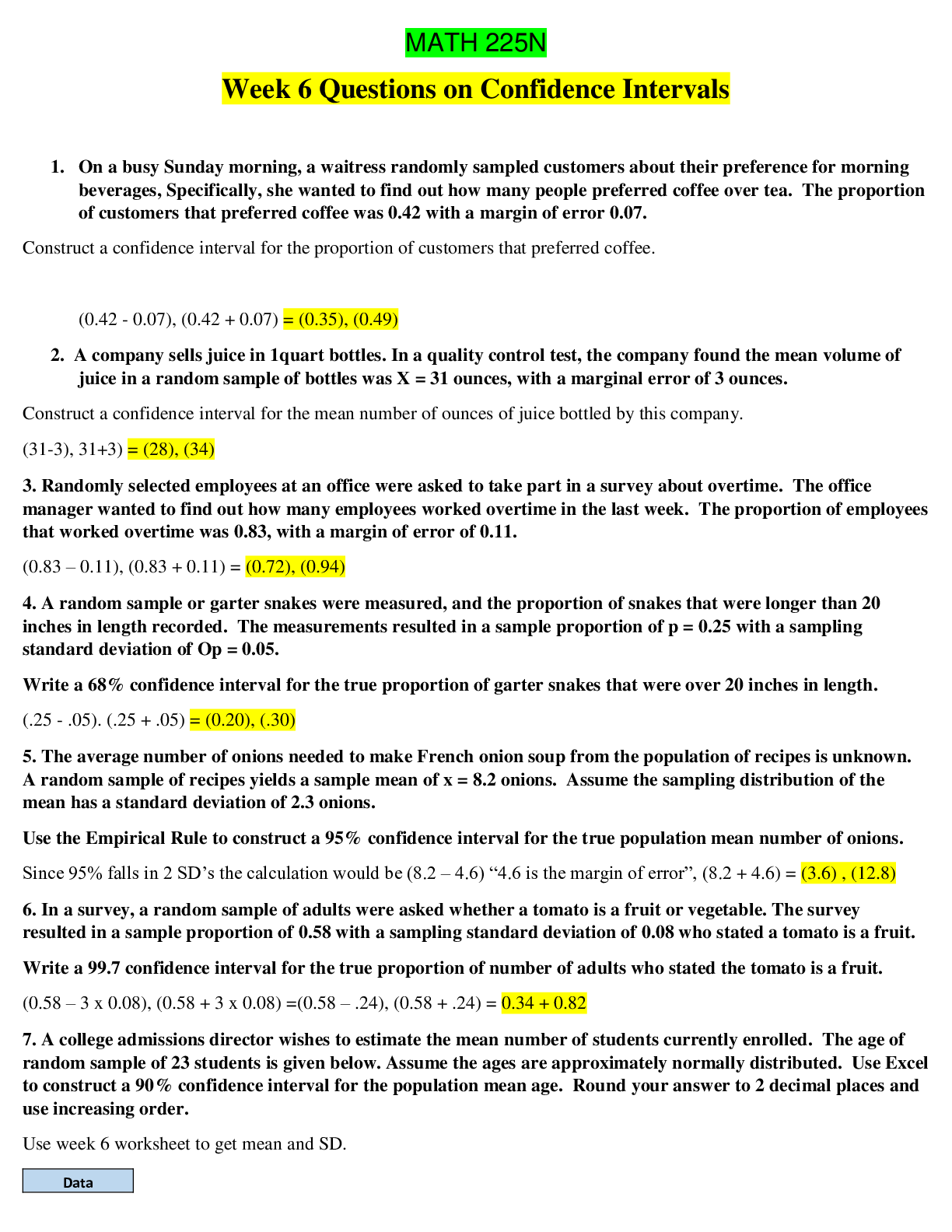
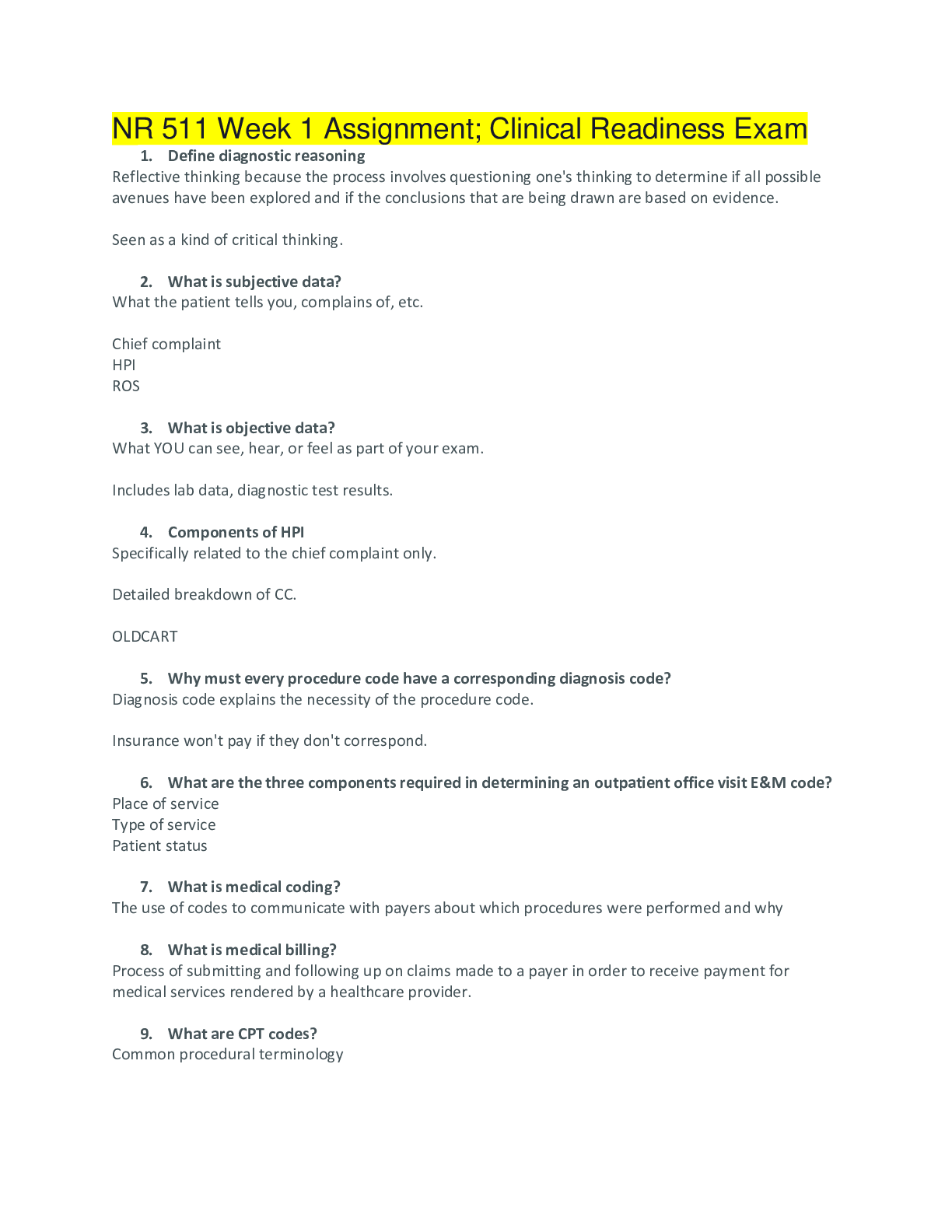
Document Content and Description Below
Principle incident/ events required to be reported to DoD counterintelligence (CI) organizations - ANSWER espionage, sabotage, terrorism, cyber Indicators of insider threats - ANSWER 1. Failure to... report overseas travel or contact with foreign nationals 2. Seeking to gain higher clearance or expand access outside the job scope 3. Engaging in classified conversations without a need to know 4. Working hours inconsistent with job assignment or insistence on working in private 5. Exploitable behavior traits 6. Repeated security violations 7. Attempting to enter areas not granted access to 8. Unexplainable affluence/living above one's means 9. Anomalies (adversary taking actions which indicate they are knowledgeable to information) 10. Illegal downloads of information/files Elements that should be considered in identifying Critical Program Information - ANSWER Elements which if compromised could: 1. cause significant degradation in mission effectiveness, 2. shorten the expected combat-effective life of the system 3. reduce technological advantage 4. significantly alter program direction; or 5. enable an adversary to defeat, counter, copy, or reverseengineer the technology or capability. asset, threat, vulnerability, risk, countermeasures - ANSWER Elements that a security professional should consider when assessing and managing risks to DoD assets The three categories of Special Access Programs - ANSWER acquisition, intelligence, and operations and support Three different types of threats to classified information - ANSWER Insider Threat, Foreign Intelligence Entities (FIE) and Cybersecurity Threat The concept of an insider threat - ANSWER An employee who may represent a threat to national security. These threats encompass potential espionage, violent acts against the Government or the nation, and unauthorized disclosure of classified information, including the vast amounts of classified data available on interconnected United States Government computer networks and systems. The purpose of the Foreign Visitor Program - ANSWER To track and approve access by a foreign entity to information that is classified; and to approve access by a foreign entity to information that is unclassified, related to a U.S. Government contract, or plant visits covered by ITAR. Special Access Program - ANSWER A program established for a specific class of classified information that imposes safeguarding and access requirements that exceed those normally required for information at the same classification level. Enhanced security requirements for protecting Special Access Program (SAP) information - ANSWER Within Personnel Security: • Access Rosters; • Billet Structures (if required); • Indoctrination Agreement; • Clearance based on an appropriate investigation completed within the last 5 years; • Individual must materially contribute to the program in addition to having the need to know; • All individuals with access to SAP are subject to a random counterintelligence scope polygraph examination; • Polygraph examination, if approved by the DepSecDef, may be used as a mandatory access determination; • Tier review process; • Personnel must have a Secret or Top Secret clearance; • SF-86 must be current within one year; • Limited Access; • Waivers required for foreign cohabitants, spouses, and immediate family members. Within Industrial Security: The SecDef or DepSecDef can approve a carve-out provision to relieve Defense Security Service of industrial security oversight responsibilities. Within Physical Security: • Access Control; • Maintain a SAP Facility; • Access Roster; • All SAPs must have an unclassified nickname/ Codeword (optional). Within Information Security: • The use of HVSACO; • Transmission requirements (order of precedence). Responsibilities of the Government SAP Security Officer/Contractor Program Security Officer (GSSO/ CPSO) - ANSWER From Revision 1 Department of Defense Overprint to the National Industrial Security Program Operating Manual Supplement - 1 April 2004: • Possess a personnel clearance and Program access at least equal to the highest level of Program classified information involved. • Provide security administration and management for his/her organization. • Ensure personnel processed for access to a SAP meet the prerequisite personnel clearance and/or investigative requirements specified. • Ensure adequate secure storage and work spaces. • Ensure strict adherence to the provisions of the NISPOM, its supplement, and the Overprint. • When required, establish and oversee a classified material control program for each SAP. • When required, conduct an annual inventory of accountable classified material. • When required, establish a SAPF. • Establish and oversee a visitor control program. • Monitor reproduction and/or duplication and destruction capability of SAP information • Ensure adherence to special communications capabilities within the SAPF. • Provide for initial Program indoctrination of employees after their access is approved; rebrief and debrief personnel as required. • Establish and oversee specialized procedures for the transmission of SAP material to and from Program elements • When required, ensure contractual specific security requirements such as TEMPEST Automated Information System (AIS), and Operations Security (OPSEC) are accomplished. • Establish security training and briefings specifically tailored to the unique requirements of the SAP. The four Cognizant Security Agencies (CSAs) - ANSWER Department of Defense (DoD), Director of National Intelligence (DNI), Department of Energy (DoE), and the Nuclear Regulatory Commission (NRC). Cognizant Security Agencies (CSA)s' role in the National Industrial Security Program (NISP). - ANSWER Establish an industrial security program to safeguard classified information under its jurisdiction. Critical Program Information in DoD - ANSWER 1. U.S. capability elements that contribute to the warfighter's advantage throughout the life cycle, which if compromised or subject to unauthorized disclosure, decrease the advantage. 2. Elements or components of a Research, Development, and Acquisition (RDA) program that, if compromised, could cause significant degradation in mission effectiveness; shorten the expected combat-effective life of the system; reduce technological advantage; significantly alter program direction; or enable an adversary to defeat, counter, copy, or reverse engineer the technology or capability. Includes information about applications, capabilities, processes and end-items. Includes elements or components critical to a military system or network mission effectiveness. Includes technology that would reduce the U.S. technological advantage if it came under foreign control. Primary authorities governing foreign disclosure of classified military information - ANSWER 1. Arms Export Control Act 2. National Security Decision Memorandum 119 3. National Disclosure Policy-1 4. International Traffic in Arms Regulation (ITAR) 5. E.O.s 12829, 13526 6. Bilateral Security Agreements 7. DoD 5220.22-M, "NISPOM," The purpose of the DD Form 254 - ANSWER Convey security requirements, classification guidance and provide handling procedures for classified material received and/or generated on a classified contract. Factors for determining whether U.S. companies are under Foreign Ownership, Control or Influence (FOCI) - ANSWER 1. Record of economic and government espionage against the U.S. targets 2. Record of enforcement/engagement in unauthorized technology transfer 3. Type and sensitivity of the information that shall be accessed 4. The source, nature and extent of FOCI 5. Record of compliance with pertinent U.S. laws, regulations and contracts 6. Nature of bilateral & multilateral security & information exchange agreements 7. Ownership or control, in whole or part, by a foreign government The purpose and the function of the Militarily Critical Technologies List (MCTL). - ANSWER 1. Serves as a technical reference for the development and implementation of DoD technology, security policies on international transfers of defense-related goods, services, and technologies as administered by the Director, Defense Technology Security Administration (DTSA). 2. Formulation of export control proposals and export license review Security Infraction - ANSWER This event cannot reasonably be expected to and does not result in the loss, compromise, or suspected compromise of classified information DoD Manual 5200.01, Volumes 1-4 - ANSWER The manual that governs the DoD Information Security Program E.O. 13526 - ANSWER The executive order that governs the DoD Information Security Program 32 CFR Parts 2001 & 2003, "Classified National Security Information; Final Rule" - ANSWER The Information Security Oversight Office (ISOO) document that governs the DoD Information Security Program Security Violation - ANSWER An event that results in or could be expected to result in the loss or compromise of classified information Unauthorized Disclosure - ANSWER Communication or physical transfer of classified or controlled unclassified information to an unauthorized recipient SSBI - ANSWER Initial investigation for military, contractors, and civilians: · Special-Sensitive positions · Critical-Sensitive positions1 · LAA · Top Secret clearance eligibility · IT-I duties ANACI - ANSWER Initial investigation for civilians: · Noncritical-Sensitive positions2 · Confidential and Secret clearance eligibility · IT-II duties NACLC - ANSWER Initial National Agency Check with Law and Credit for military and contractors: · Secret or Confidential clearance eligibility · All military accessions and appointments · IT-II duties · IT-III duties (military only) NACI - ANSWER National Agency Check with Inquiries for civilians and contractors: · Non-Sensitive positions · Low Risk · HSPD-12 Credentialing NAC - ANSWER The fingerprint check portion of a PSI The purpose of due process in Personnel Security Program (PSP) - ANSWER Ensures fairness by providing the subject the opportunity to appeal an unfavorable adjudicative determination The key procedures for initiating Personnel Security Investigations (PSIs) - ANSWER 1. Validate the need for an investigation 2. Initiate e-QIP 3. Review Personnel Security Questionnaire (PSQ) for completeness 4. Submit electronically to OPM DoD position sensitivity types and their investigative requirements. - ANSWER 1. Critical Sensitive 2. Non-Critical Sensitive 3. Non-Sensitive Investigative requirement for a Critical- Sensitive position - ANSWER SSBI, SSBI-PR, or PPR Investigative requirement for a Non-Critical Sensitive position - ANSWER ANACI or NACLC Investigative requirement for a Non-Sensitive position - ANSWER NACI Revocation - ANSWER The term when current security clearance eligibility determination is rescinded Denial - ANSWER The term when an initial [Show More]
Last updated: 1 year ago
Preview 1 out of 20 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$9.00
Document information
Connected school, study & course
About the document
Uploaded On
Nov 22, 2022
Number of pages
20
Written in
Additional information
This document has been written for:
Uploaded
Nov 22, 2022
Downloads
0
Views
30











.png)