Database Management > EXAM > University of Maryland, University College - IFSM 201 Module 11- Basics of Databases Latest (Attempt (All)
University of Maryland, University College - IFSM 201 Module 11- Basics of Databases Latest (Attempt Score 79% 150/190}
Document Content and Description Below
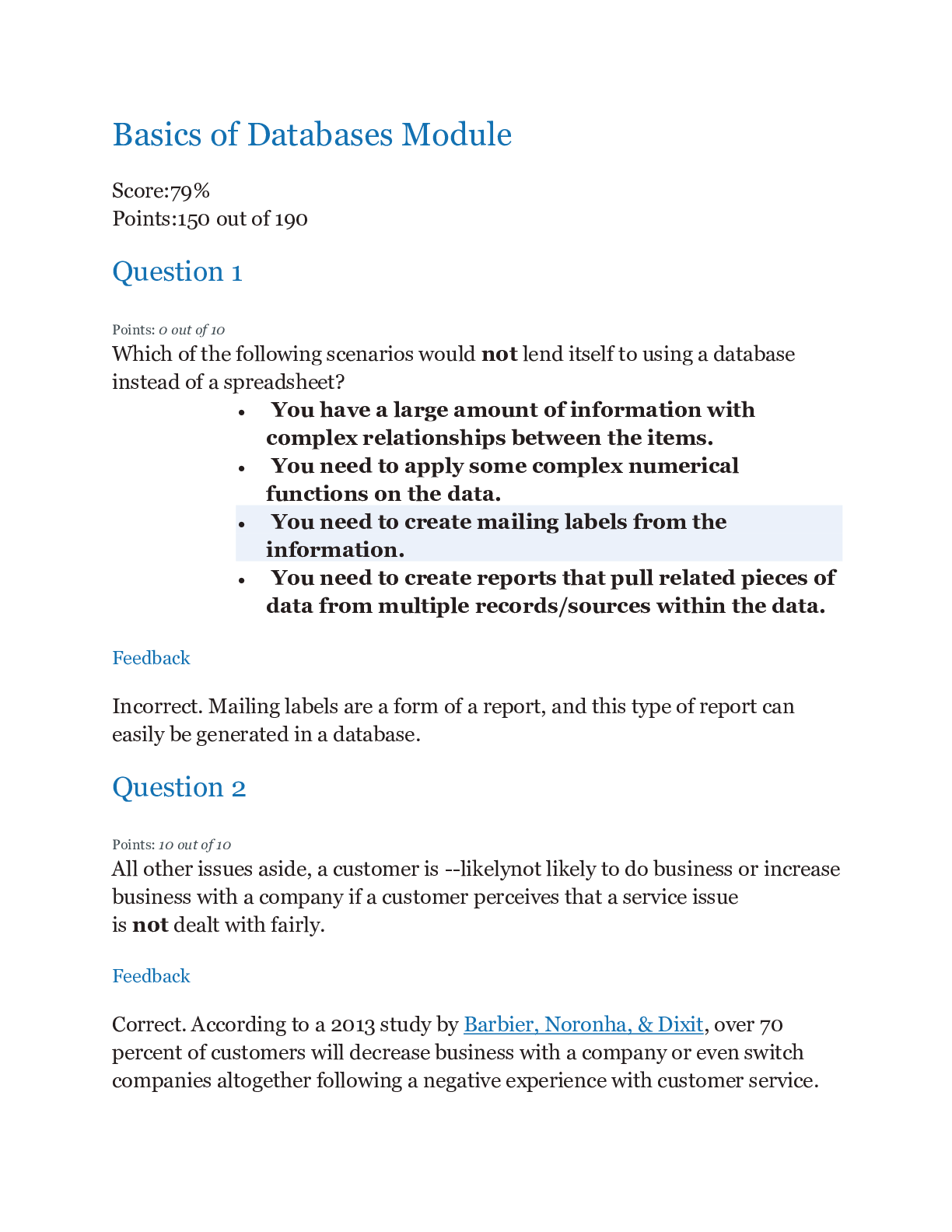
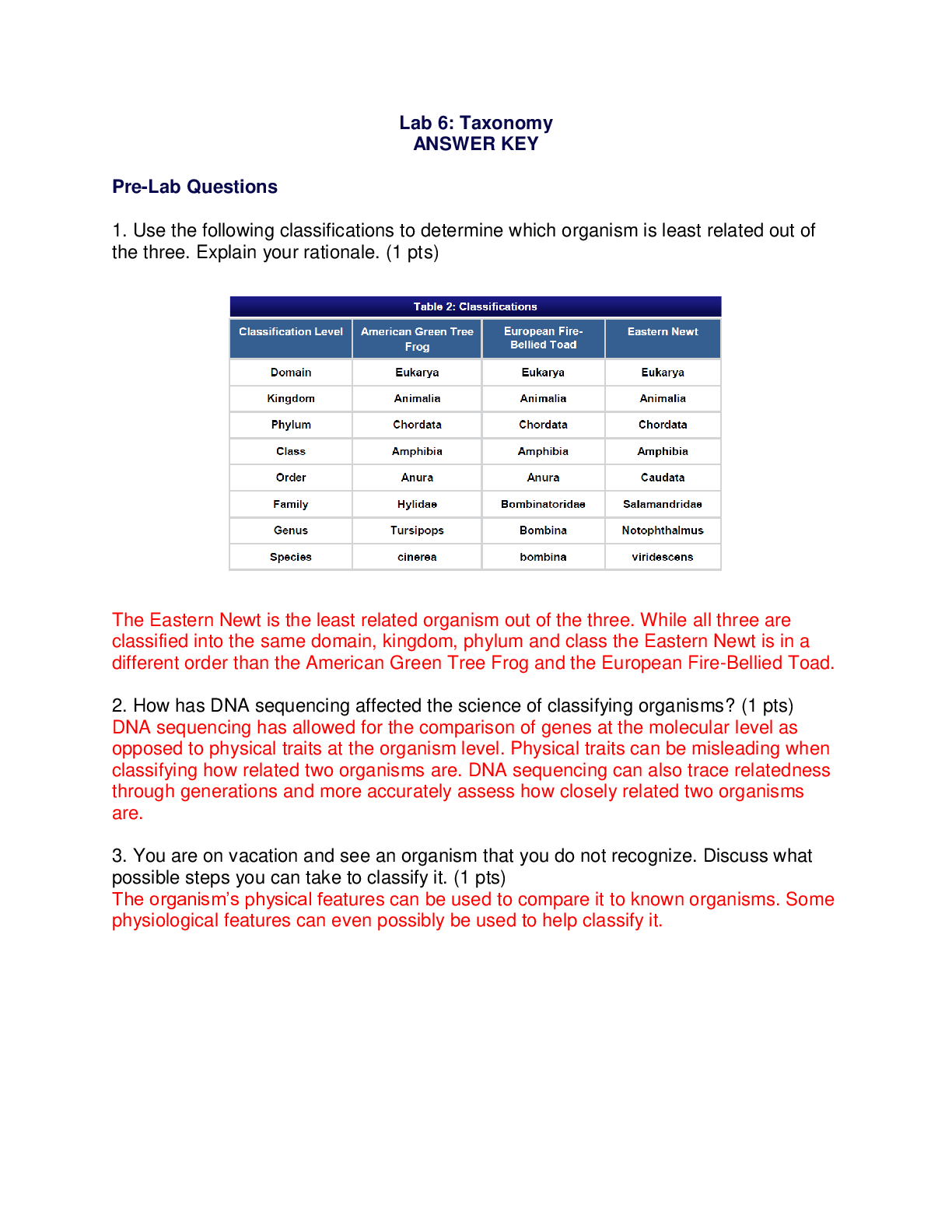
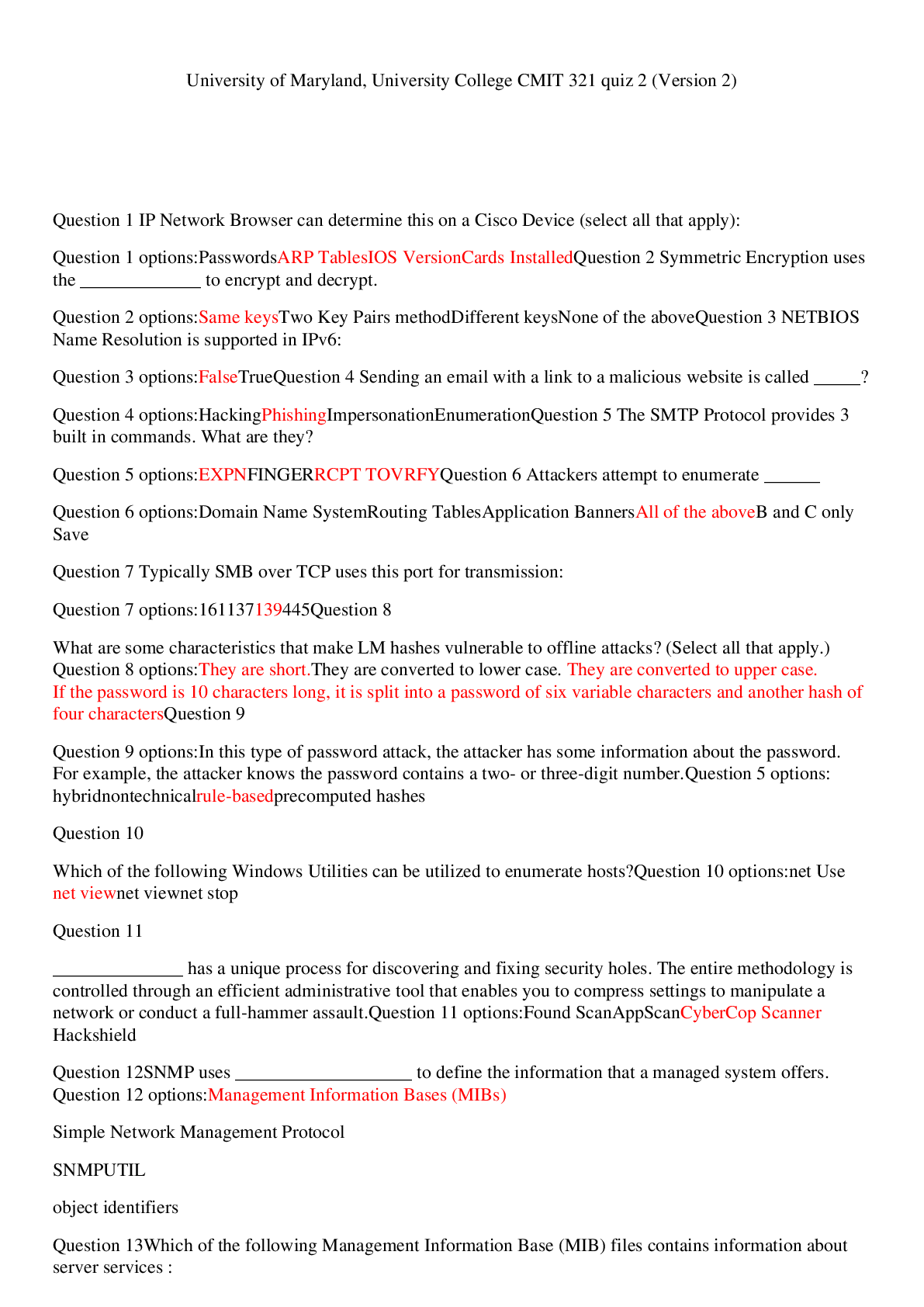
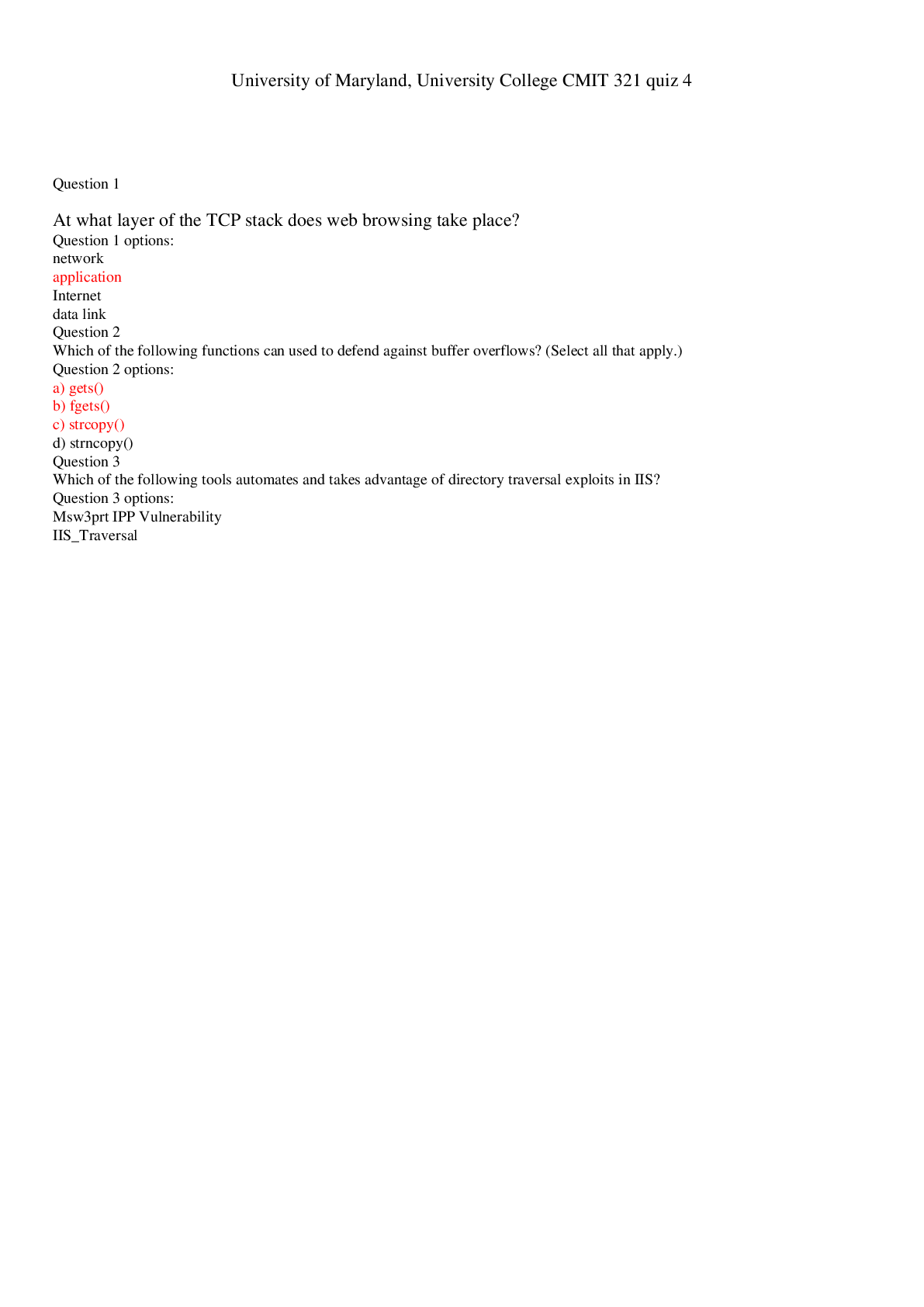
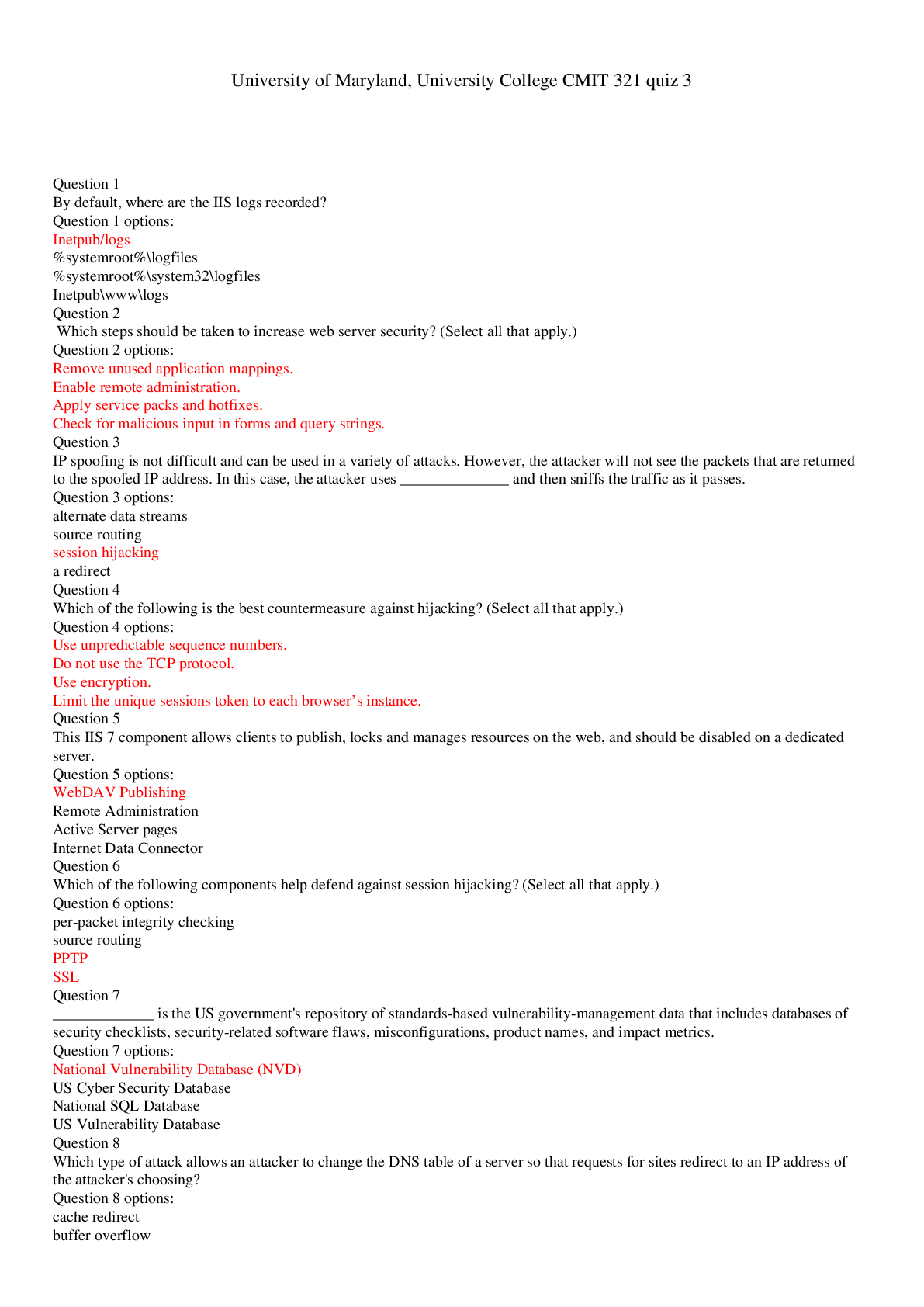
Which of the following scenarios would not lend itself to using a database instead of a spreadsheet? • You have a large amount of information with complex relationships between the items. • You ne... ed to apply some complex numerical functions on the data. • You need to create mailing labels from the information. • You need to create reports that pull related pieces of data from multiple records/sources within the data. Question 2 Select one answer. 10 points In terms of customer service issues, which of the following is the least likely reason for using a robust CRM? • A CRM can enable members of pertinent departments to have access to all the relevant information, enabling them to answer queries and resolve problems quickly and easily. • A CRM can provide a company's marketing department with information needed to identify and target new customers. • A CRM can optimize the information shared among departments, resulting in better management of existing accounts. • A CRM can provide a more rapid response to queries and concerns by forwarding the query to the right department. Question 3 Select one answer. 10 points True or false? A data warehouse will typically contain the history of all previous interactions with specific users (including product use and transactions), but rarely includes other types of data. • True • False Question 4 Select one answer. 10 points A staff/faculty member uses proprietary (owned and protected by the university) data from the university's student financial records database in a graph that is part of a presentation at a computer education conference. Which of the following best describes the data issue? • Intentional data leak • Malicious data loss • Accidental data loss • Malicious data leak Question 5 Fill in the blanks by selecting one option from each menu. 10 points Cloud storage for database contents is more efficient in terms of easy access by employees anytime, anywhere. The updated information for the database is generated with real-time information sent to a central server within the company. Updates to the cloud are made every hour during normal working hours. This could be considered a potential database . Question 6 Select one answer. 10 points True or false? The largest component of a database is a field. • True • False Question 7 Select one answer. 10 points What are procedures that help keep a database current? • Database query procedures • Report generation procedures • File maintenance procedures • Data entry procedures Question 8 Select one answer. 10 points You have voluntarily resigned from your company where you were the database administrator. But you find that you still have access to the databases six months after leaving the company. Which threat best describes this database breach? • Accidental breach resulting from incorrect (but not malicious) usage • Exploiting weaknesses in an operating system or network • Unprotected personal hardware collection • Weak authentication Question 9 Select one answer. 10 points A large travel agency has a customer service group that monitors its Facebook page on a 24/7 basis and responds immediately to posts about operational problems. Which of the following best describes the component of CRM in play here? • Keeping valuable staff • Cleaning up the data • Mining the social media inputs • Privacy Question 10 Fill in the blanks by selecting one option from each menu. 10 points You want to change your cell phone plan and call the company to discuss options. This is a typical example of CRM that focuses on . Question 11 Select one answer. 10 points Which of the following would be an example of a loss of record integrity in a database? • Because the word “mortgage” appears in the subject line of an e-mail you sent to your son or daughter, you begin receiving unsolicited e-mail messages from mortgage companies. • Although you clicked the option to "Do not share information with any other companies or sites" on the bookstore's website, you are getting unsolicited e-mail messages from some of the companies that post ads on that site. • You enter the wrong password three times and find that you are locked out of the site you are trying to access. • You receive a notice from your favorite online shopping site that you have an outstanding balance for items that you did not order. Question 12 Fill in the blanks by selecting one option from each menu. Part 1: 10 points Part 2: 10 points Part 3: 10 points Part 4: 10 points 40 points Are the following examples of increasing brand awareness through groups or fans? Select Yes or No for each option. Your instant messaging service attaches a message to the bottom of each message inviting the recipient to sign up for this same service provider. You "Friend" or "Like" a page on your favorite social media page that advertises a product you approve. Your friends on a social media site receive messages from you that encourages them to start watching a television series that premiered this past week. When you sign on to your favorite social media website, a number of sponsored ads appear on your home page. Question 13 Select one answer. 10 points True or false? A database breach always involves PII. • True • False Question 14 Select one answer. 10 points True or false? In terms of database access, risk assessments should address those who have legitimate credentials for viewing, entering, updating, or removing data from the database and those who are restricted from accessing the database or who have limited rights. • True • False Question 15 Select one answer. 10 points Which of the following database model choices would be best for storing video clips organized by various vacations you have taken? • Network • Flat-file • Hierarchical • Object-oriented Question 16 Select one answer. 10 points True or false? You do not like the fact that your computer “times out” after 10 minutes of non-use and goes into a hibernation state (blank screen). You set the timeout period to 1 hour and allow it to activate without reentering a password. This would be considered a good practice for safeguarding your personally identifiable information. • True • False [Show More]
Last updated: 1 year ago
Preview 1 out of 9 pages
.png)
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Feb 12, 2022
Number of pages
9
Written in
Additional information
This document has been written for:
Uploaded
Feb 12, 2022
Downloads
0
Views
256