Computer Science > EXAM > iSACA Cybersecurity Fundamentals Certification Exam Questions and Answers (All)
iSACA Cybersecurity Fundamentals Certification Exam Questions and Answers
Document Content and Description Below
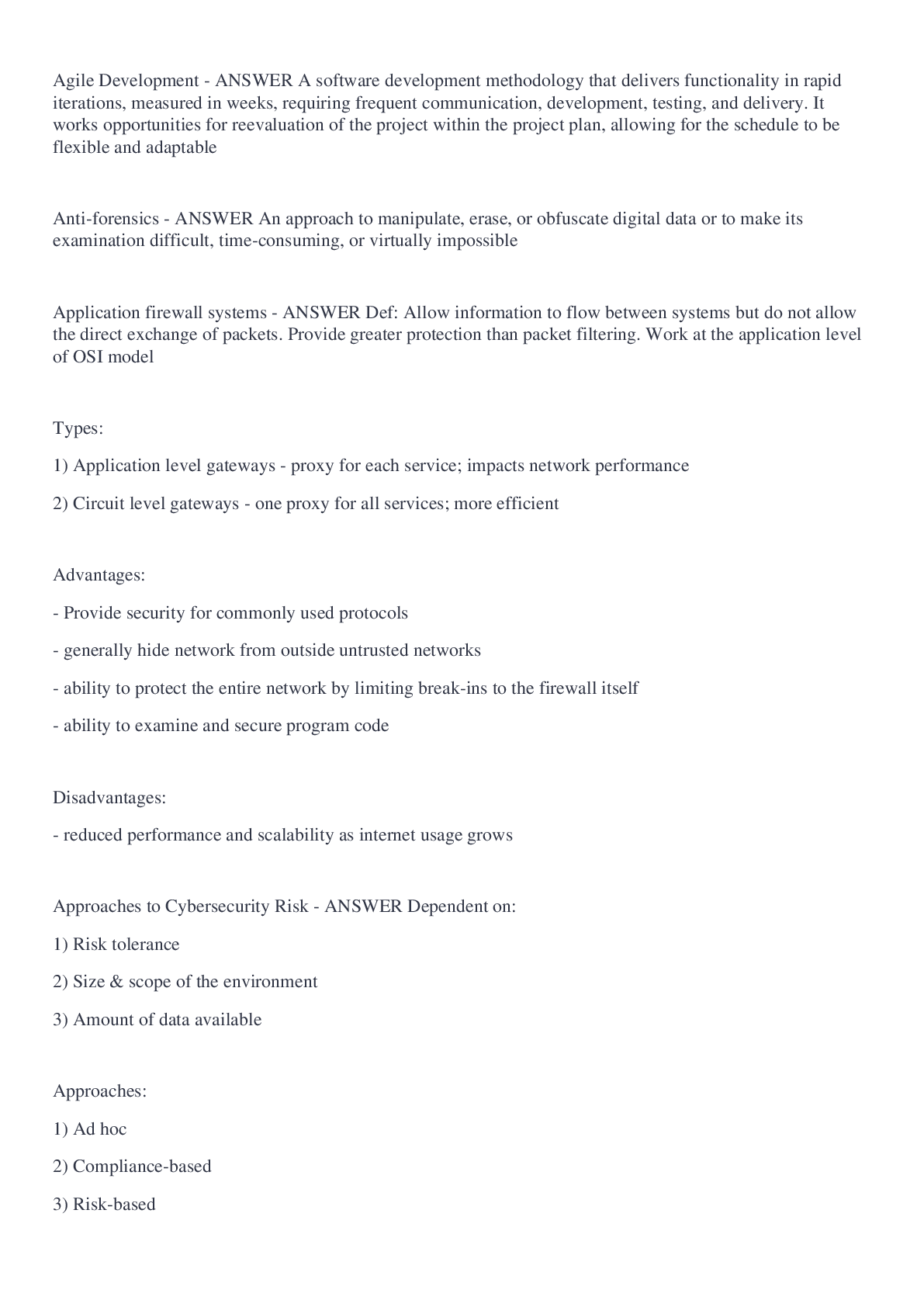
Agile Development - ANSWER A software development methodology that delivers functionality in rapid iterations, measured in weeks, requiring frequent communication, development, testing, and delivery. ... It works opportunities for reevaluation of the project within the project plan, allowing for the schedule to be flexible and adaptable Anti-forensics - ANSWER An approach to manipulate, erase, or obfuscate digital data or to make its examination difficult, time-consuming, or virtually impossible Application firewall systems - ANSWER Def: Allow information to flow between systems but do not allow the direct exchange of packets. Provide greater protection than packet filtering. Work at the application level of OSI model Types: 1) Application level gateways - proxy for each service; impacts network performance 2) Circuit level gateways - one proxy for all services; more efficient Advantages: - Provide security for commonly used protocols - generally hide network from outside untrusted networks - ability to protect the entire network by limiting break-ins to the firewall itself - ability to examine and secure program code Disadvantages: - reduced performance and scalability as internet usage grows Approaches to Cybersecurity Risk - ANSWER Dependent on: 1) Risk tolerance 2) Size & scope of the environment 3) Amount of data available Approaches: 1) Ad hoc 2) Compliance-based 3) Risk-based Asset - ANSWER something of either tangible or intangible value that is worth protecting Asymmetric key - ANSWER pairs of unidirectional, complementary keys that only encrypt or decrypt; one of these is secret and the other is publically known; ideal for short messages (i.e. digital signatures, distribute symmetric keys) Advantages: 1) Easier distributing keys to untrusted, unknown users 2) Provides authentication/nonrepudiation - sender only knows the private key Disadvantages: 1) computationally intensive and slow Attack Attributes - ANSWER 1) Attack Vector 2) Payload 3) Exploit 4) Vulnerability 5) Target (Asset) Attack vector - ANSWER The path or route used to gain access to the target (asset) Types: 1) Ingress - intrusion 2) Egress - Data removal Attack-signature-detection tools - ANSWER These look for an attack signature, which is a specific sequence of events indicative of an unauthorized access attempt. A simple example would be repeated failed logon attempts. Attrition - ANSWER An attack that employs brute force methods to compromise, degrade, or destroy systems, networks or services Audit reduction tools - ANSWER Preprocessors designed to reduce the volume of audit records to facilitate manual review. Used to analyze large log files Availability - ANSWER protection from disruptions in access Business Continuity Plan - ANSWER A plan for how an organization will recover and restore partially or completely interrupted critical function(s) within a predetermined time after a disaster or extended disruption Involves identifying business processes of strategic importance and creating a business impact analysis (BIA) 1) What are the business processes? 2) What are the critical information resources related to these processes? 3) What is the critical recovery time period for resources to be resumed before losses are suffered? Certificate Authority (CA) - ANSWER A trusted third-party agency that is responsible for issuing digital certificates. Chain of custody - ANSWER documenting, in detail, how evidence is handled and maintained, including its ownership, transfer and modification; this is necessary to satisfy legal requirements and mandate high level of confidence regarding integrity of evidence Common Firewall issues - ANSWER 1) Configuration errors 2) Monitoring demands 3) Policy maintenance 4) Vulnerability to application/input-based attacks concentric rings - ANSWER A.K.A. Nested layering Creates a series of nested layers that must be bypassed in order to complete an attack. Each layer delays the attacker and provides opportunities to detect and attack Confidentiality - ANSWER Protection from unauthorized access cyberrisk assessment - ANSWER process of analyzing the different risk attributes: 1) Examine risk sources (threats/vulnerabilities) for positive/negative consequences 2) Rank risks according to likelihood and impact 3) Evaluate existing controls to determine effectiveness of risk mitigation Cybersecurity - ANSWER the protection of information assets (digital assets) by addressing threats to information processed, stored, and transported by internetworked information systems Cybersecurity incident - ANSWER an adverse event that negatively impacts the confidentiality, integrity an availability of data; can be technical or physical events cybersecurity incident investigations - ANSWER Collection and analysis of evidence with the goal of identifying the perpetrator of an attack or unauthorized use/access; sometimes the goals of the investigation can conflict with the incident response (i.e. destroying evidence unintentionally) Evidence preservation is very important and may be dependent on data type, investigator skills/experiences, and tools available; chain of custody needs to be maintained for evidence to be admissible in court of law Data at rest - ANSWER Stored data Data classification - ANSWER tagging data with metadata based on a classification taxonomy, enabling data to be found quickly and efficiently and cuts back on storage and backup costs and helps to allocate and maximize resources Data in transit - ANSWER Data traveling over a network Data in use - ANSWER data movement at the user workstation level Data Loss Prevention (DLP) - ANSWER A system that helps an organization protect its information and prevent the exfiltration of sensitive data. The system covers data at rest, data in transit, and data in use. Database controls - ANSWER 1) Authentication and authorization of access 2) Access controls 3) Logging and other transactional monitoring 4) Encryption and integrity controls 5) Backups Database vulnerabilities - ANSWER 1) Unauthorized activity by authorized users 2) Malware infections or interactions 3) Capacity issues 4) Physical damage 5) Design flaws 6) Data corruption Defense in Depth - ANSWER Layering defenses to provide added protection Types: 1) Concentric rings 2) Overlapping Redundancy 3) Segregation Demilitarized Zone (DMZ) - ANSWER A separate network located outside the organization's internal information system that permits controlled access from the internet. Functions as a small, isolated network for an organization's public servers, VPN, modem pools. Development and IT Operations (DevOps) - ANSWER Combines Agile development, infrastructure and flexible operations to enable rapid and continuous releases and ongoing improvement in IT value creation; breaks large projects into small deliverables and multiple deployments, which are easier to manage Digital certificate - ANSWER composed of a public key and information on the owner of the public key; purpose is to associate a public key with an individual's identity to prove the sender's authenticity Elements: 1) Username 2) public key 3) algorithm used to compute the digital signature 4) certificate validity period Digital forensic tools - ANSWER 1) Computer (nonvolatile digital media) 2) Memory (volatile data) 3) Mobile device 4) Network digital forensics - ANSWER the process of identifying, preserving, analyzing, and presenting digital evidence in a manner that is legally acceptable in any legal proceedings Digital Signature - ANSWER electronic identification of a person or entity created by using a public key algorithm; provides a way for the recipient to verify the integrity of the data (hashing - checksum) and identity of the sender vulnerable to man in the middle attacks where the sender's digital signature private/public key may be faked disasters - ANSWER disruptions that cause critical information resources to be inoperative for a period of time, adversely impacting organizational operations dual-homed firewall - ANSWER a host that resides on more than one network and possesses more than one network card dynamic/private ports - ANSWER 49152 to 65535; not listed because of their dynamic nature Elliptical Curve Cryptography - ANSWER Type of public key cryptography is a method that increases security while using minimum resources; less computational power is required for a more secure encryption Ideal for networked computers requiring strong cryptography. Limited in bandwidth and processing power Encapsulation - ANSWER Process of adding addressing information to data as they are transmitted down the OSI stack Encryption - ANSWER Process of converting readable data into unreadable characters (ciphertext) to prevent unauthorized access. It is limited in that it cannot prevent the loss of data. Encryption algorithm - ANSWER Mathematically based function or calculation that encrypts or decrypts data Encryption key - ANSWER Piece of information similar to a password that makes the encryption or decryption process unique. A user needs the correct key to access or decipher a message, as the wrong key converts the message into an unreadable form. Event vs incident - ANSWER An event is any change, error, or interruption within an IT infrastructure - an observable occurrence in a system or network. An incident is a violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices. Events are handled in normal course of business vs. incidents that require security/investigative expertise to manage Exploit - ANSWER A method to take advantage of vulnerability by delivering input to gain unintended access or deny service. Firewall - ANSWER combination of systems that enforces a boundary between two or more networks, typically forming a barrier between a secure and an open environment (i.e. internet) Firewall platforms - ANSWER Hardware: - faster - Not as flexible - minimal system overhead Software: - slower - significant system overhead - more flexible w/ additional services Appliance: - significantly faster to setup and recover - hardened operating system Forensic Chain of Events - ANSWER 1) Identify information that is available and might form evidence of an incident 2) Preserve identified information (imaging, chain of custody) 3) Analyze the evidence 4) Present the findings to relevant parties Guidelines - ANSWER Provide general guidance on issues; not requirements but strongly recommended hive - ANSWER logical group of keys, subkeys, and values in the registry that has a set of supporting files and backups of its data Horizontal defense in depth - ANSWER Controls are placed in various places in the path to access an asset. IDS Weaknesses - ANSWER This system is limited in the sense that it cannot help with... 1) weaknesses in the policy definition 2) application-level vulnerabilities 3) back doors into applications 4) Weaknesses in identification and authentication schemes Incident Response - ANSWER formal program that prepares an entity for an incident Phases: 1) Preparation 2) Detection and Analysis 3) Investigation 4) Mitigation and Recovery 5) Postincident Analysis Inherent risk - ANSWER The risk level or exposure without taking into account the actions that management has taken or might take (e.g., implementing controls) integrity - ANSWER Protection from unauthorized modification Internet Perimeter - ANSWER Secure access to the Internet for enterprise employees and guest users, regardless of location. It should... 1) Route traffic between enterprise & internet 2) Prevent executable files from being transferred through email attachments/browsing 3) Monitor internal/external network ports 4) Detect & block traffic from infected internal end point 5) Control user traffic bound for the internet 6) Identify and block malicious packets 7) Eliminate threats such as email spam, viruses 8) Enforce filtering policies to block access to websites containing malware 9) Provide protection for VPNs, WANs, and WLANs Intrusion Detection System (IDS) - ANSWER Operates continuously on the system, running in the background and notifying administrators when it detects a perceived threat. It works in conjunction with routers and firewalls by monitoring network usage anomalies. Can be networked-based or host-based Components: 1) Sensors for collecting data 2) Analyzers that receive input from sensors & determine intrusive activity 3) Administration console Intrusion Protection System - ANSWER A system designed to not only detect attacks, but also to prevent victim hosts from being affected by attacks. It is commonly placed at the perimeter of the enterprise network. Biggest advantage of this system is that is can help block an attack, not just detect it IRP Containment - ANSWER incident management team (IMT) is activated and will attempt to limit exposure of incident 1) Notifying stakeholders of incident 2) Implement containment procedures 3) Obtaining and preserving evidence 4) Taking backups of actions IRP Eradication - ANSWER Determine the root cause of the incident and get rid of it 1) locating backups 2) removing root cause 3) improving defenses by implementing protecting techniques 4) vulnerability analysis IRP Identification - ANSWER Aims to verify if an incident has happened and find out info about it 1) assign ownership of incident 2) verify that reports/events qualify as incidents 3) Establish chain of custody 4) Determine severity IRP Postincident Activity - ANSWER Report is prepared on lessons learned and what happened during the phases of the incident IRP Preparation - ANSWER prepares organization to develop an IRP prior to incident 1) establish incident approach 2) establish policies and warning banners 3) establish communication plan to stakeholders 4) Ensure equipment, location, resources IRP Recovery - ANSWER Ensures that affected systems or services are restored to a condition specified in the service delivery objectives (SDO) or business continuity plan (BCP) Kernel mode - ANSWER Type of operation for an OS for executing privileged instructions for the internal operation of the system; in this mode there are no protections from errors or malicious activity and all parts of the system and memory are accessible Ex: Operating system and device drivers Likelihood - ANSWER A.K.A probability measure of frequency of which an event may occur, which depends on the threat and vulnerability Local Area Network (LAN) - ANSWER a computer network that covers a small area; bandwidth has increased for this network type, causing more need to monitor and control network traffic Susceptible to people/virus related threats due to large number of people who have access rights Components: 1) Repeater 2) Hubs 3) Switches 4) Routers 5) Bridges log - ANSWER record of events that occur within the systems and networks of an organization; they help monitor controls and detect risk Malware - ANSWER Def: software designed to infiltrate or damage a computer system without the user's informed consent Examples: Viruses, network worms, Trojan horses Network Access Control (NAC) - ANSWER aims to control the access to a network using policies that describe how devices can secure access to network nodes when they first try to access a network Network management - ANSWER process of assessing, monitoring, and maintaining network devices and connections; consists of 5 functional areas (FCAPS): 1) Fault management 2) Configuration management 3) Accounting management 4) Performance management 5) Security management Next Generation Firewalls - ANSWER Firewall capable of content-level filtering and application-level monitoring. Use application awareness, maintaining information about connected applications to optimize their performance NIST Functions to Protect Digital Assets - ANSWER IPDRR 1) Identify 2) Protect 3) Detect 4) Respond 5) Recover Nonrepudiation - ANSWER Def: ensuring that a message or other piece of information is genuine Examples: digital signatures and transaction logs Open Systems Interconnection (OSI) model - ANSWER a seven-layer architecture for defining how data is transmitted from computer to computer in a network, from the physical connection to the network to the applications that users run. It also standardizes interactions between network computers exchanging information. APSTNDP 7) Application - Mediates between software applications and other layers of network services 6) Presentation - Formats, encrypts, and compresses data 5) Session - Coordinates and manages user connections 4) Transport - Ensures that data are transferred reliably in the correct sequence 3) Network - Translates network addresses/routes data form sender to receiver 2) Data Link - Divides data into frames that can be transmitted by the physical layer 1) Physical - Manages signals among network systems overlapping redundancy - ANSWER Two or more controls that work in parallel to protect an asset. Provides multiple, overlapping points of detection. This is most effective when each control is different. packet-filtering firewall - ANSWER Def: A firewall that examines each packet and [Show More]
Last updated: 1 year ago
Preview 1 out of 19 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$6.00
Document information
Connected school, study & course
About the document
Uploaded On
Jul 20, 2022
Number of pages
19
Written in
Additional information
This document has been written for:
Uploaded
Jul 20, 2022
Downloads
1
Views
84











.png)