Computer Networking > EXAM > C795 Cybersecurity Management II - Tactical Questions and Answers 2022/2023 Graded A+ (All)
C795 Cybersecurity Management II - Tactical Questions and Answers 2022/2023 Graded A+
Document Content and Description Below
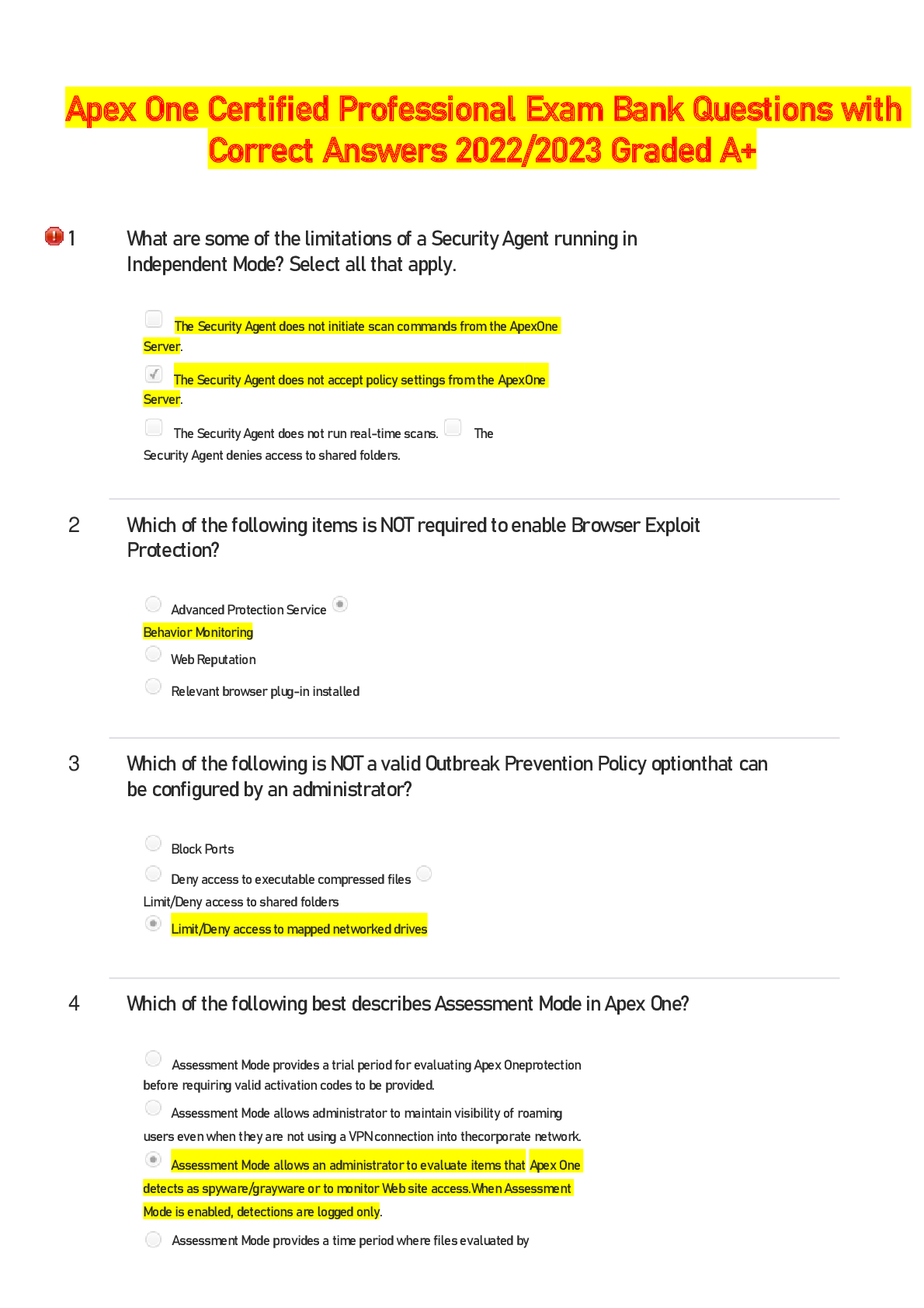
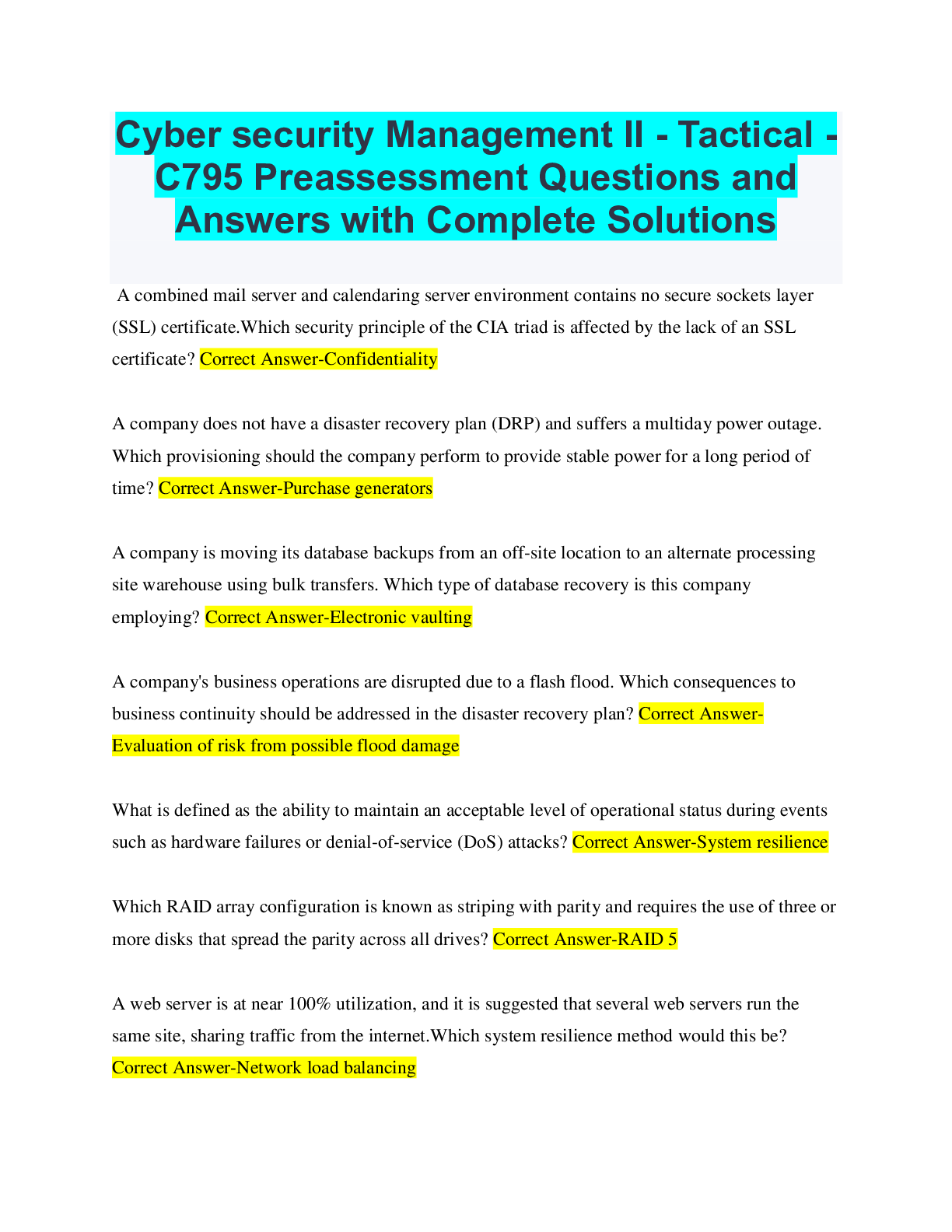
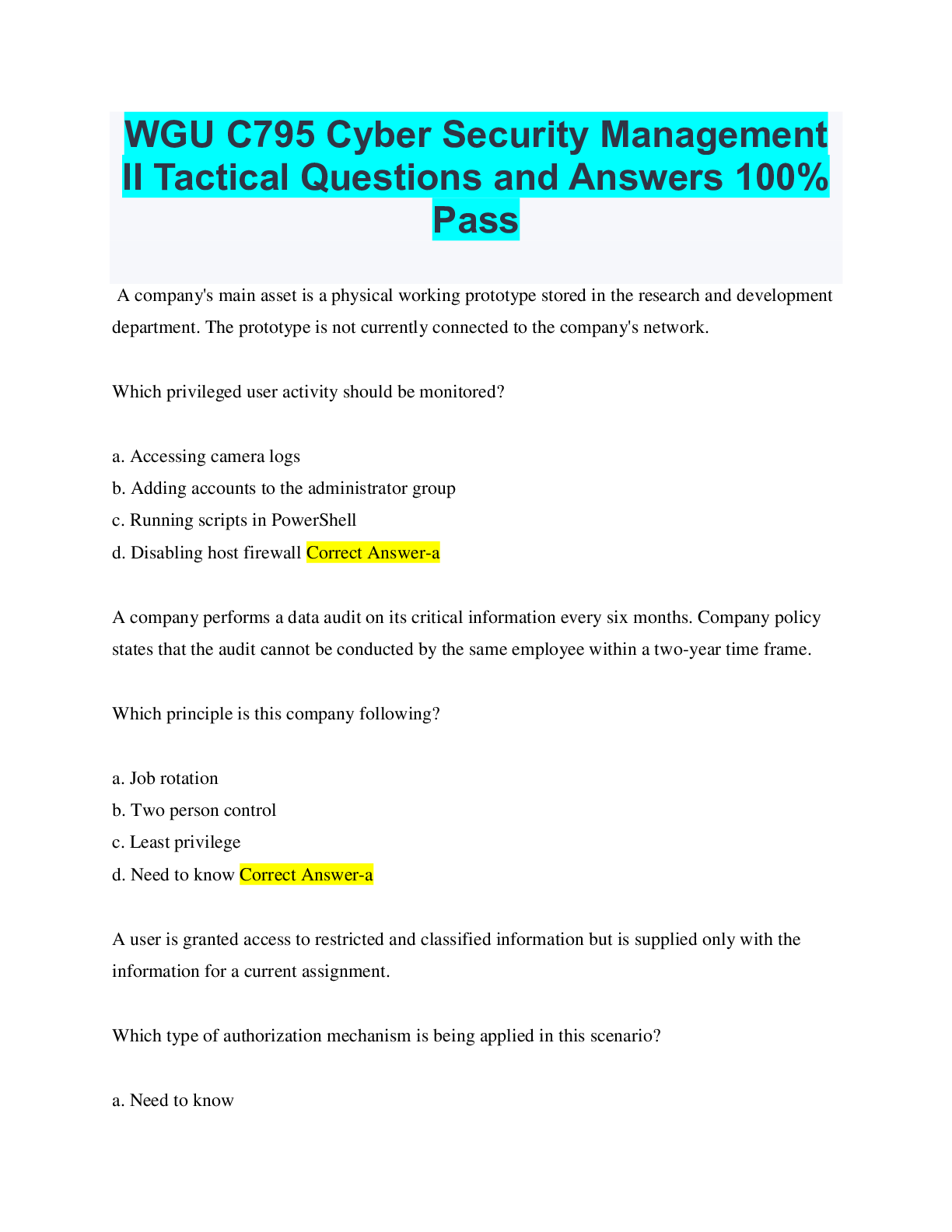
As an IT security professional, you have just been hired by a multisite automotive dealership to protect and manage its computer network. What is your first task in establishing a secure defense syste... m for the company? This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9. A Hire a system security vendor. B Perform a full vulnerability assessment. C Perform an asset inventory and classification audit. D Document all users on the corporate domain. - ANSWER C is correct. A security administrator has to have a complete inventory of systems and equipment connected to the corporate network. Once this information is complete and accurate, a security professional can begin mapping vulnerabilities to the known systems. Which characteristic most accurately describes a zero-day exploit vulnerability? This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9. A It is only known to hackers and a few security professionals. B It is only known to the hacker. C It was a major concern in the late 1990s, but current technology has eliminated them. D It is widely known, but ineffective and only used occasionally. - ANSWER Explanation: Answer B is correct. A zero-day exploit is a flaw in an operating system or program code that is discovered by a threat actor with the intention of exploiting the vulnerability before authors of the code can patch or rewrite the code to eliminate the vulnerability. CVE - ANSWER MITRE Corporation National Vulnerability Database (NVD) - ANSWER National Institute of Standards and Technology's (NIST) Computer Security Division, these days the NVD is brought to you by your friends at the Department of Homeland Security's National Cybersecurity Division. According to them Which organizations provide vulnerability-mapping services, tools, or resources that can be accessed for free? This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9. A AARP B OWASP C NIST D ACLU E MITRE - ANSWER Explanation: Answers B, C, and E are correct. The Open Web Application Security Project (OWASP), National Institute of Standards and Technology (NIST), and MITRE Corporation all provide free vulnerability-mapping services, tools, or resources. One of the main purposes of a cybersecurity professional is to help a company establish its security requirements. Which critical components of an application risk assessment accomplish this objective? Select all that apply.This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9. A Understanding the application type B [Show More]
Last updated: 1 year ago
Preview 1 out of 24 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 13, 2022
Number of pages
24
Written in
Additional information
This document has been written for:
Uploaded
Aug 13, 2022
Downloads
0
Views
45











.png)


.png)

.png)
.png)