Information Technology > STUDY GUIDE > SAPPC Study Guide :Questions & Answers: Guaranteed A+ Score (All)
SAPPC Study Guide :Questions & Answers: Guaranteed A+ Score
Document Content and Description Below
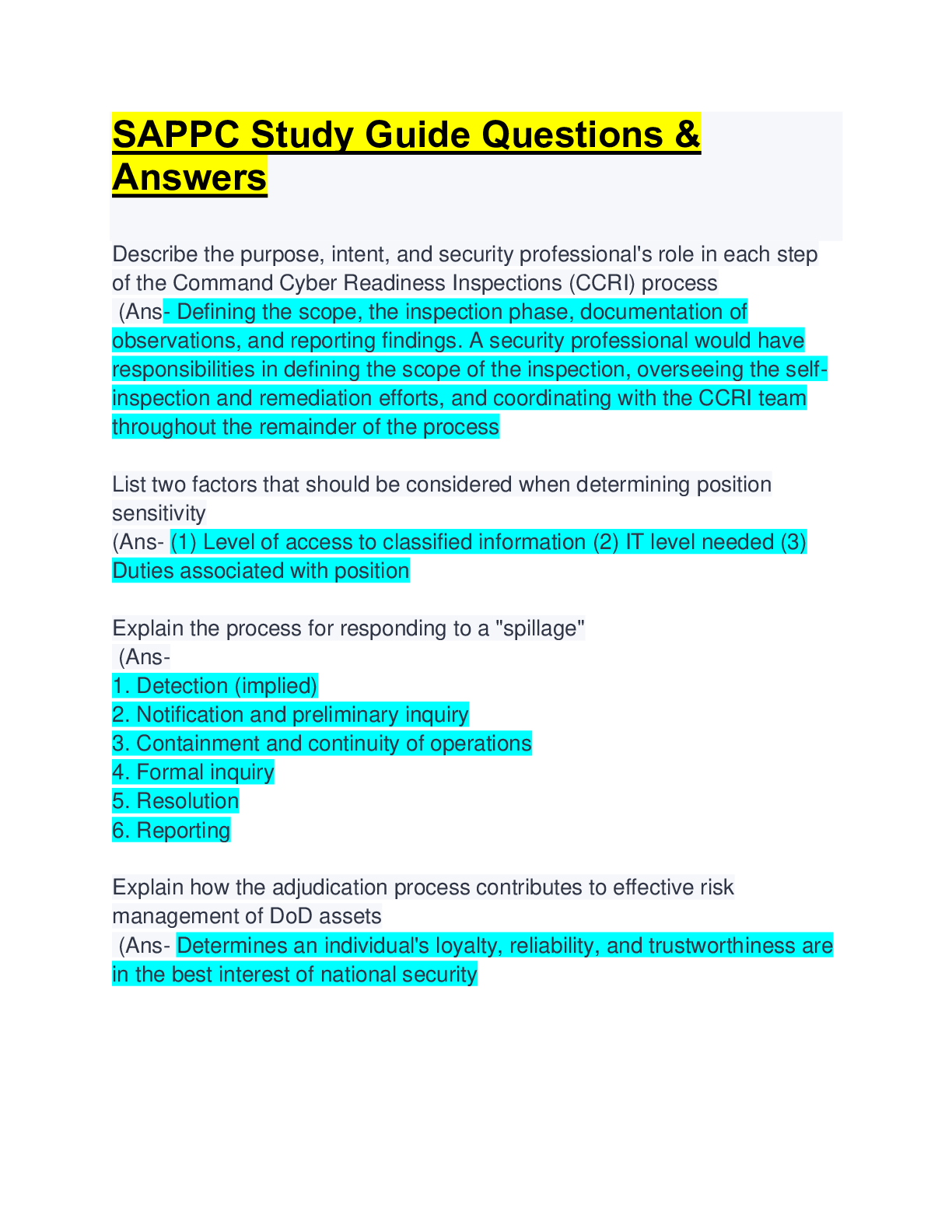
Describe the purpose, intent, and security professional's role in each step of the Command Cyber Readiness Inspections (CCRI) process (Ans- Defining the scope, the inspection phase, documentation of... observations, and reporting findings. A security professional would have responsibilities in defining the scope of the inspection, overseeing the self-inspection and remediation efforts, and coordinating with the CCRI team throughout the remainder of the process List two factors that should be considered when determining position sensitivity (Ans- (1) Level of access to classified information (2) IT level needed (3) Duties associated with position Explain the process for responding to a "spillage" (Ans- 1. Detection (implied) 2. Notification and preliminary inquiry 3. Containment and continuity of operations 4. Formal inquiry 5. Resolution 6. Reporting Explain how the adjudication process contributes to effective risk management of DoD assets (Ans- Determines an individual's loyalty, reliability, and trustworthiness are in the best interest of national security Explain why access control measures are contingent on Force Protection Conditions (Ans- The Force Protection Conditions determine the amount of control measures needed to be taken in response to various levels of threats against military facilities or installations. Define the purpose and function of the militarily critical technologies list (MCTL) (Ans- Serves as a technical reference for the development and implementation of DoD technology, security policies on international transfers of defense-related goods, services, and technologies as administered by the Director, Defense Technology Security Administration (DTSA). Describe how authorization of Limited Access Authority impacts risk to DoD assets (Ans- Increases risk by allowing a foreign national access to classified information. Reduces risk by ensuring Foreign Nationals with a unique or unusual skills set have been properly investigated, adjudicated or vetted before being granted access to specific pieces of classified information only. List three different types of threats to classified information (Ans- (1) Insider threat (2) Foreign Intelligence entities (3) Cybersecurity Threat What is the security professionals' role in pursuing and meeting cyber security goals? (Ans- The role of the cyberspace workforce is to "secure, defend, and preserve data, networks, net-centric capabilities, and other designated systems by ensuring appropriate security controls and measures are in place, and taking internal defense actions" (DoDD 8140.01). Per DoDI 8500.01, Cybersecurity (March 14, 2014), personnel occupying cybersecurity positions must be assigned in writing and trained / qualified in accordance with their role. Identify specific baseline administrative and/or physical security controls applicable to each system categorization (Ans- Controls are identified by enumerating the common controls, identifying those relevant to the categorization level as defined in NIST SP 800-53, potentially tailored by the Authorizing Official, and overlays are applied based on the nature of the system. List three (3) factors for determining whether US companies are under Foreign Ownership Control of Influence (FOCI) (Ans- 1. Record of economic and government espionage against the US targets. 2. Record of enforcement/engagement in unauthorized technology transfer. 3. Type and sensitivity of the information that shall be accessed. 4. The source, nature and extent of FOCI. 5. Record of compliance with pertinent US laws, regulations and contracts. 6. Nature and bilateral and multilateral security and information exchange agreements. 7. Ownership or control in whole or part, by a foreign government. How does lack of attention to the concept of compilation of information introduce risks to DoD assets? (Ans- 1. Unauthorized disclosure 2. Misclassification 3. Security Violation 4. Improper safeguarding 5. Improper dissemination 6. Improper handling 7. Improper destruction 8. Data Spill List at least three indicators of insider threats (Ans- 1. Failure to report overseas travel or contact with foreign nationals. 2. Seeking to gain higher clearance or expand access outside the job scope. 3. Engaging in classified conversations without a need to know. 4. Working hours inconsistent with job assignment or insistence on working in private. 5. Exploitable behavior traits. 6. Repeated security violations. 7. Attempting to enter areas not granted access to. 8. Unexplained affluence/living above one's means. 9. Anomalies (adversary taking actions which indicate they are knowledgeable to information). 10. Illegal downloads of information/files. What is the difference between physical security surveys and physical security inspections? (Ans- A physical security survey is a formal record assessment of an installation's overall security posture; whereas a physical security inspection is a formal record of compliance of physical procedures and measures implemented by a unit or activity to protect its assets Describe the security professional's possible roles in handling a security incident (*hint SSRII*) (Ans- 1. Secure 2. Safeguard 3. Report 4. Inquire 5. Investigate [Show More]
Last updated: 1 year ago
Preview 1 out of 14 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 18, 2022
Number of pages
14
Written in
Additional information
This document has been written for:
Uploaded
Nov 18, 2022
Downloads
0
Views
46













 Study Guide.png)
 Exam Study Guide.png)




.png)