Data Systems > Quiz > SEC-360 Week 5 Quiz ( QUESTIONS AND ANSWERS) - 100 %CORRECT ANSWERS (All)
SEC-360 Week 5 Quiz ( QUESTIONS AND ANSWERS) - 100 %CORRECT ANSWERS
Document Content and Description Below
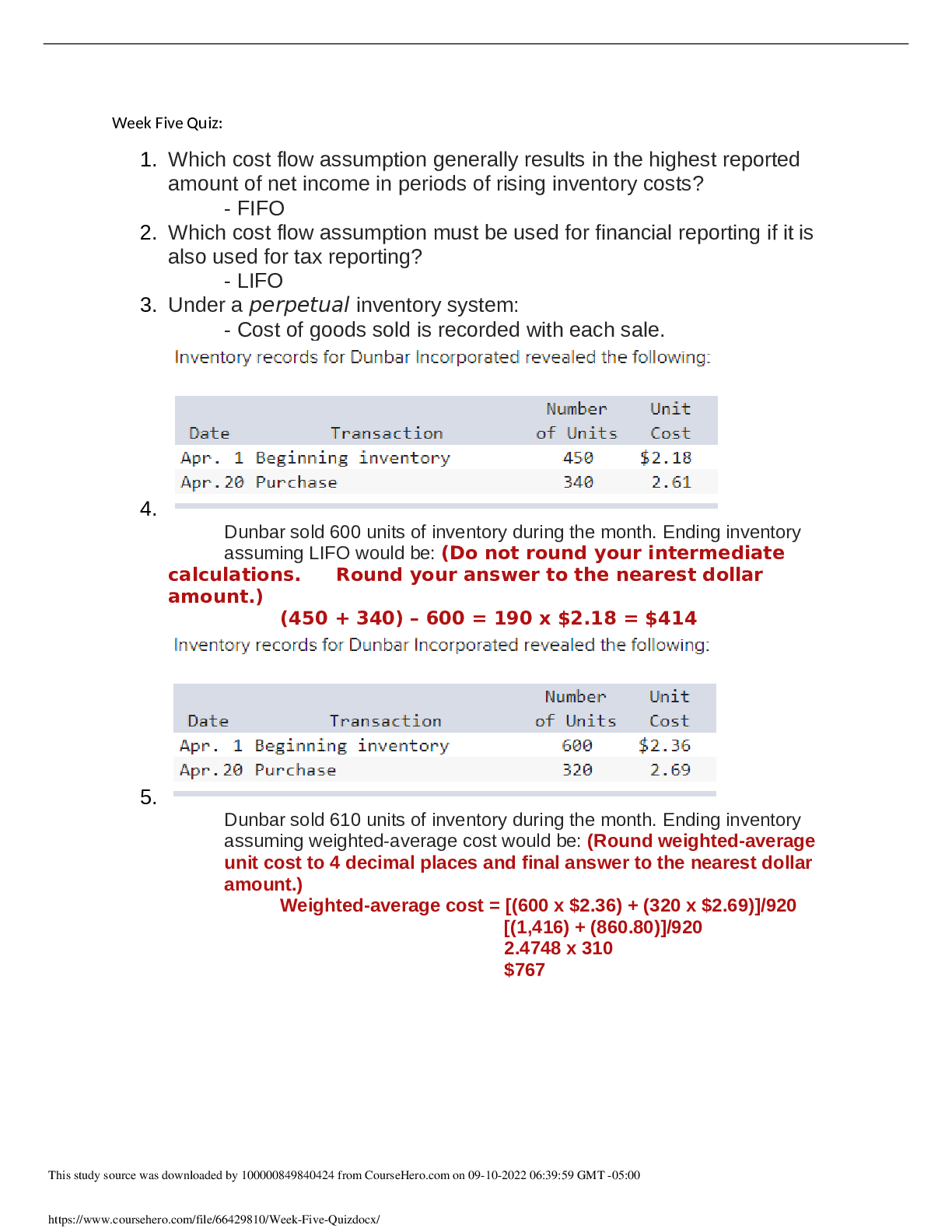
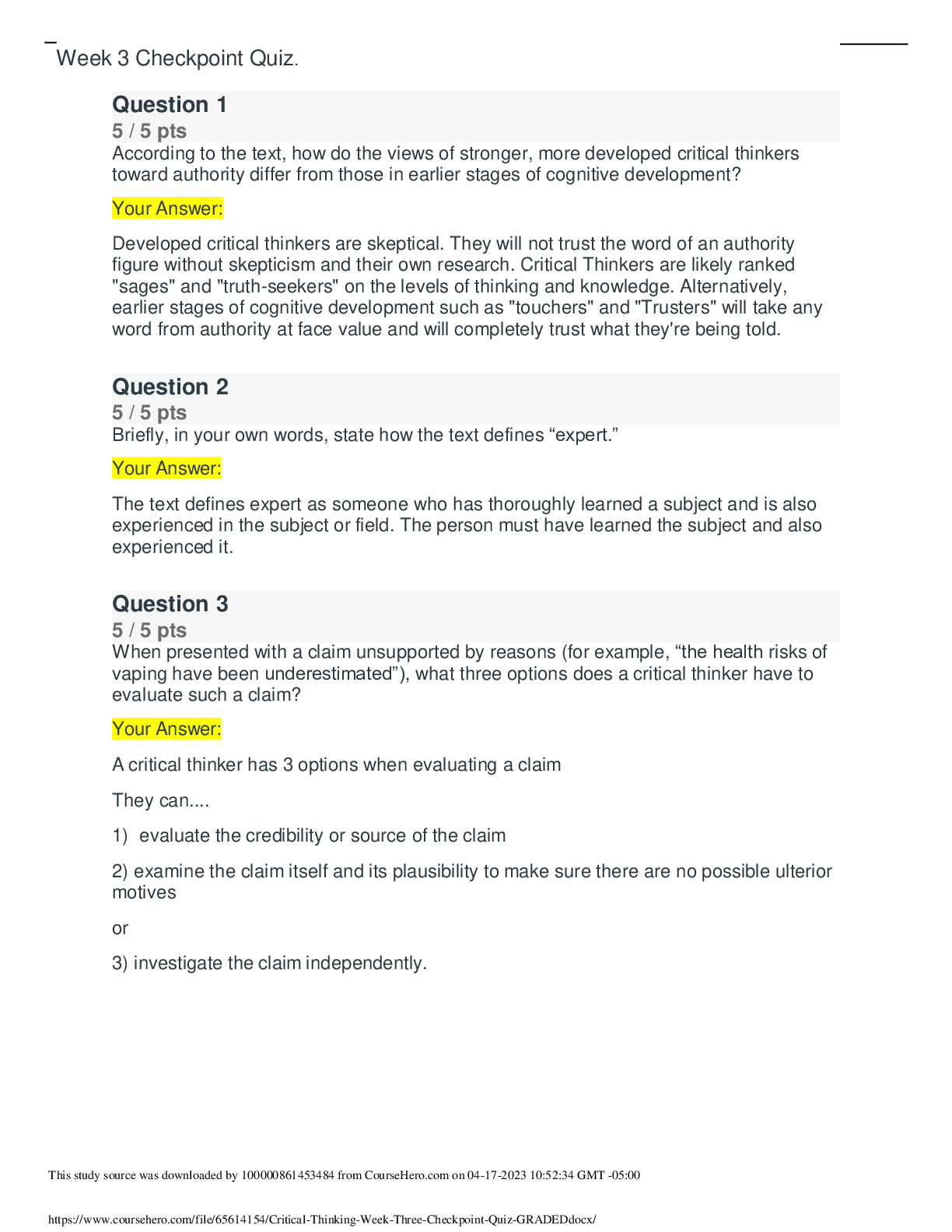
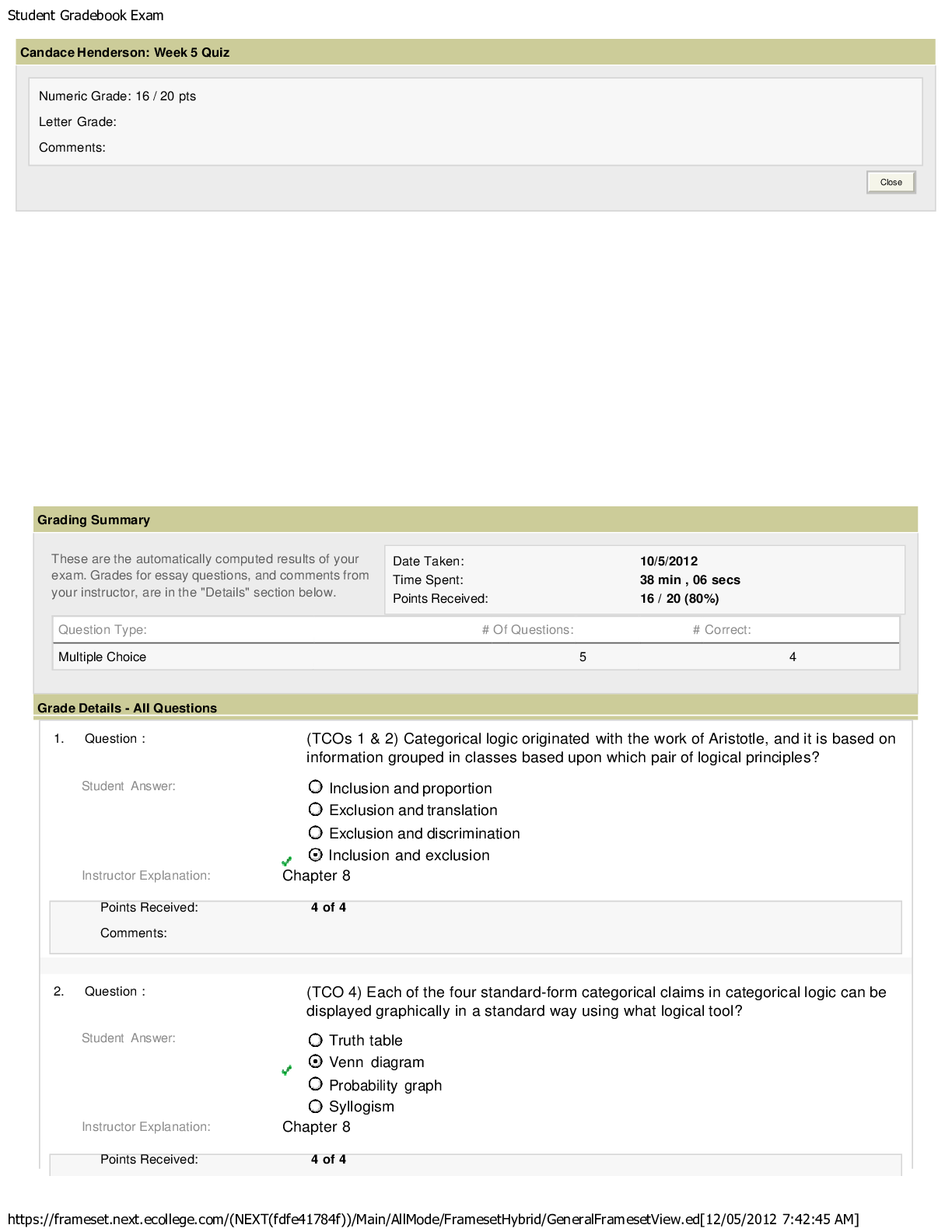
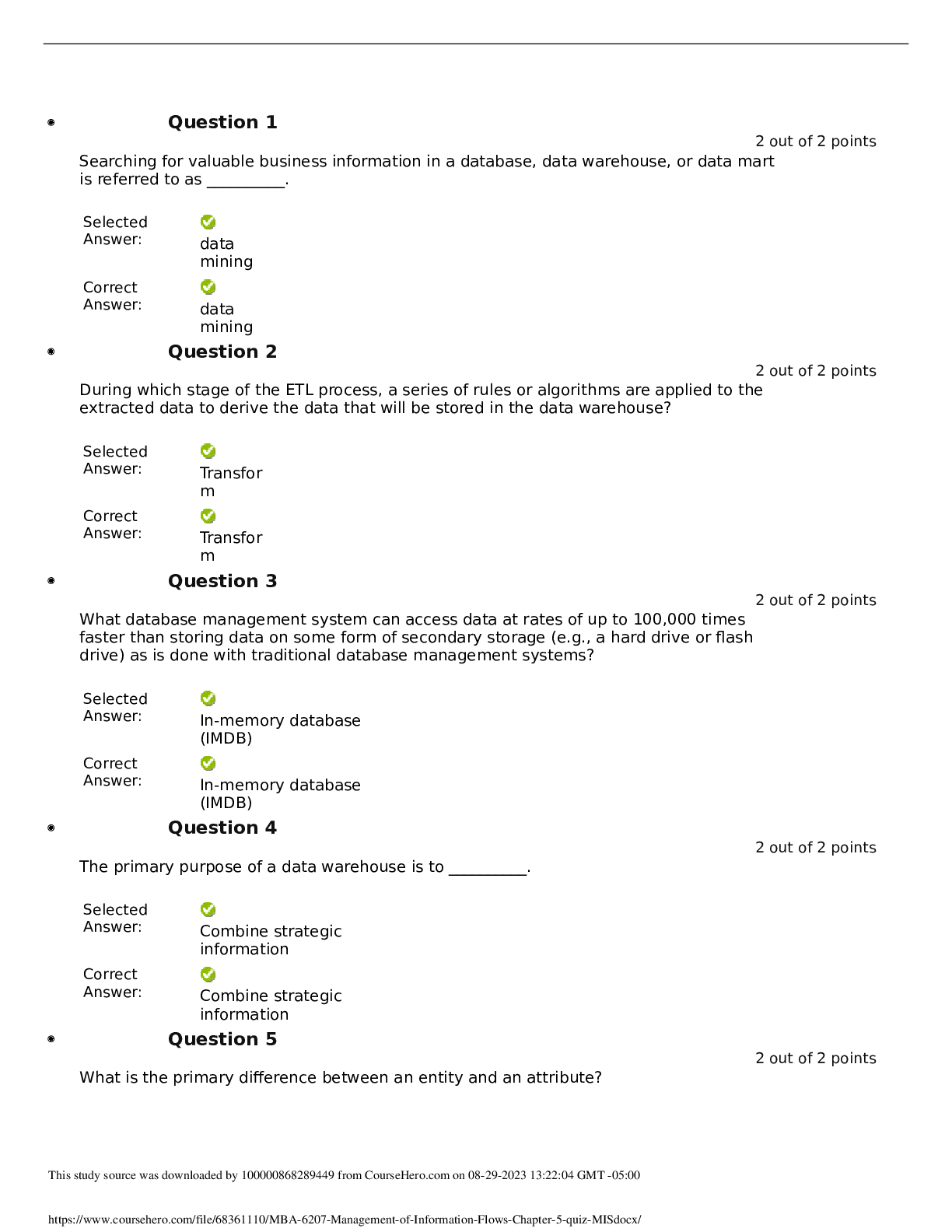
SEC360 - Week 5: Quiz (TCO 6) The media control that includes locked doors, desks, file cabinets, or safes is . environmental protection physical access protection integrity verification ... disposition identification Text, page 195 (TCO 6) What is the best weapon a company can have against physical security threats? Motion detectors Security plan Unbreakable firewalls Educated staff Lecture; text, page 168 (TCO 6) Physical security deals with all of the following except _ _. buildings logical systems computer rooms computer devices fences Text, Chapter 8, p. 165 (TCO 7) Record retention processes . keep track of changes made by administrators define how long records are retained are needed for retirement of information assets protect company resources protect management from prosecution Text, page 190 (TCO 7) As a security operations rule, policy should be established stating that media should . be sanitized and destroyed be marked and controlled be marked and handled properly never be reused be accounted for Text, page 191 (TCO 8) Disaster recovery planning includes all of the following except _ . IT systems and applications application data data entry users networks communication lines Text, pages 129-133 (TCO 8) A _ _ site provides power, air conditioning, heat, and other environmental systems, but it does not provide hardware or software. shared hot cold warm colocated Text, page 131 (TCO 9) What is the U.S. government classification label that means that unauthorized disclosure may seriously damage national security? CONFIDENTIAL SECRET TOP SECRET NOFORN RESTRICTED Text, page 209 (TCO 9) Which of the following is NOT true for RADIUS? Uses remote access Dial-In User Service Used by AOL to authenticate users Creates a private tunnel between end points Policies can be centrally administered Can use multifactor authentication Text, page 220 (TCO 9) When a transaction requires only a , there is not any actual proof that a particular person conducted that transaction. written signature digital signature password driver's license fingerprint scan Text, page 211 [Show More]
Last updated: 10 months ago
Preview 1 out of 5 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jul 04, 2023
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Jul 04, 2023
Downloads
0
Views
34