Data Systems > Quiz > SEC-360 Week 7 Quiz - 100% Correct Answers (All)
SEC-360 Week 7 Quiz - 100% Correct Answers
Document Content and Description Below
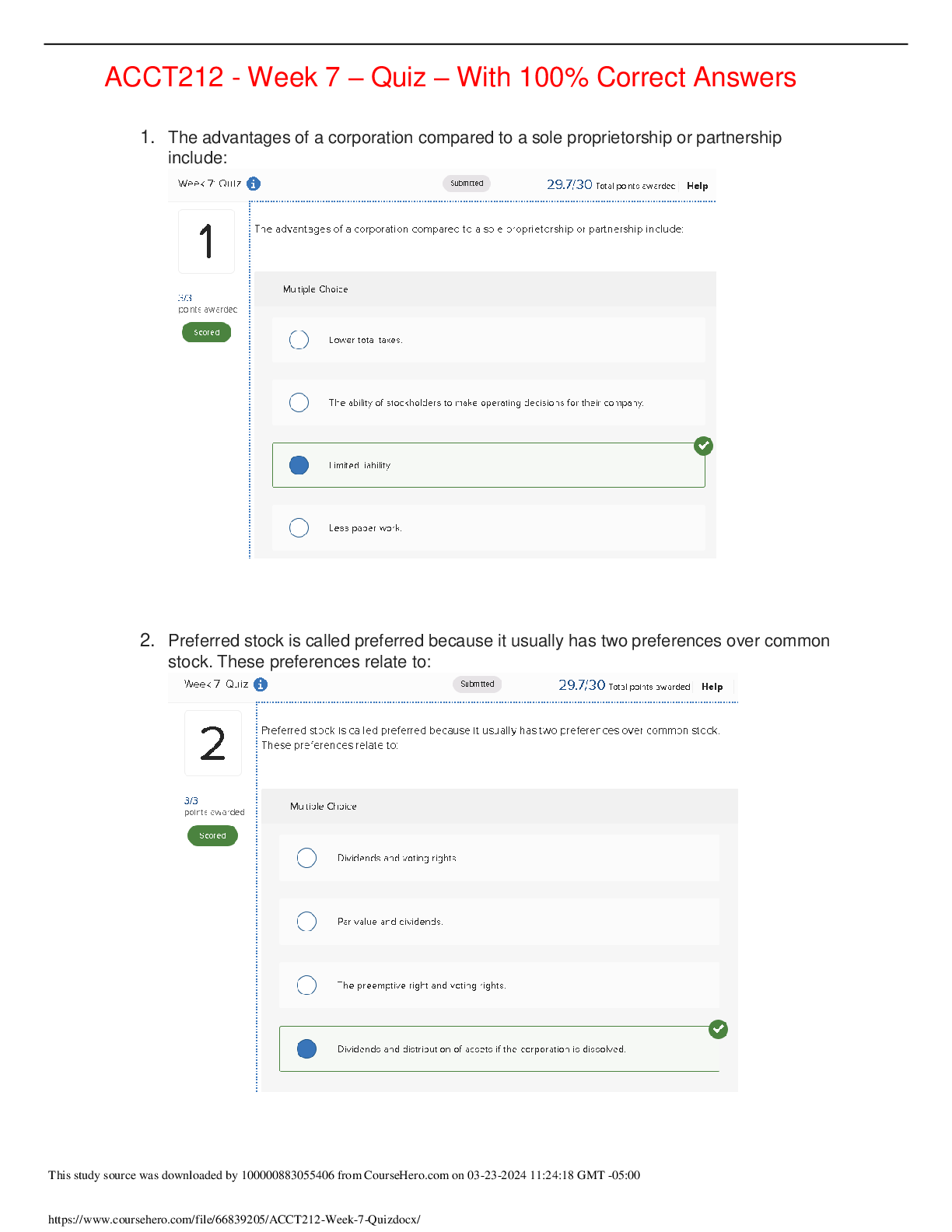
1. (TCO 10) Generally, symmetric cryptography is used to encrypt , and asymmetric cryptography is used to encrypt . (Points : 5) images, text data, messages messages, data text, images messages, d... igital signatures 2. (TCO 10) Cryptography is used to do all of the following, except . (Points : 5) keep messages private authenticate the sender test the integrity of messages maintain the receiver's privacy nonrepudiate senders 3. (TCO 11) A packet filter that keeps track of the state of a connection is called a . (Points : 5) stateful inspection firewall stateful inspection filter stateful inspection router stateful inspection bridge stateful inspection gateway 4. (TCO 11) Which of the following is not a characteristic of a proxy server? (Points : 5) Configured to allow access only to specific systems Maintains detailed audit information Dependent on all other proxies on the bastion host Runs as a nonprivileged user Any service that is not supported by the proxy server is blocked. 5. (TCO 12) Modern intrusion detection systems act as sensors for hosts and network devices and work in a centrally controlled distributed fashion using . (Points : 5) software remote procedure calls agent technology common interfaces access to local audit records 6. (TCO 12) The Internet Engineering Task Force Intrusion Detection working group has developed a standard called the . (Points : 5) Intrusion Detection Standard Intrusion Detection Framework Intrusion Detection Data Model Intrusion Detection Exchange Format Intrusion Detection Data Format 7. (TCO 12) An event where seemingly harmless data is forwarded by the router to a host on an internal network is known as a . (Points : 5) drive-by attack proxy-server attack data-driven attack penetration testing steganography 8. (TCO 13) Which form of malware is independent of the operating system and replicating? (Points : 5) Trap door Virus Worm Trojan Logic bomb 9. (TCO 13) Which of the following is not an example of a software agent? (Points : 5) Active-X component Java applet Proxy server JavaBean Corba object 10. (TCO 13) Which form of malware contains hidden code that is triggered by meeting or reaching a specific condition? (Points : 5) Trap door Virus Worm Trojan horse Logic bomb [Show More]
Last updated: 10 months ago
Preview 1 out of 3 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jul 10, 2023
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Jul 10, 2023
Downloads
0
Views
30











.png)










