Computer Science > EXAM > Cybersecurity Essentials Final Quiz | Questions with complete solutions (All)
Cybersecurity Essentials Final Quiz | Questions with complete solutions
Document Content and Description Below
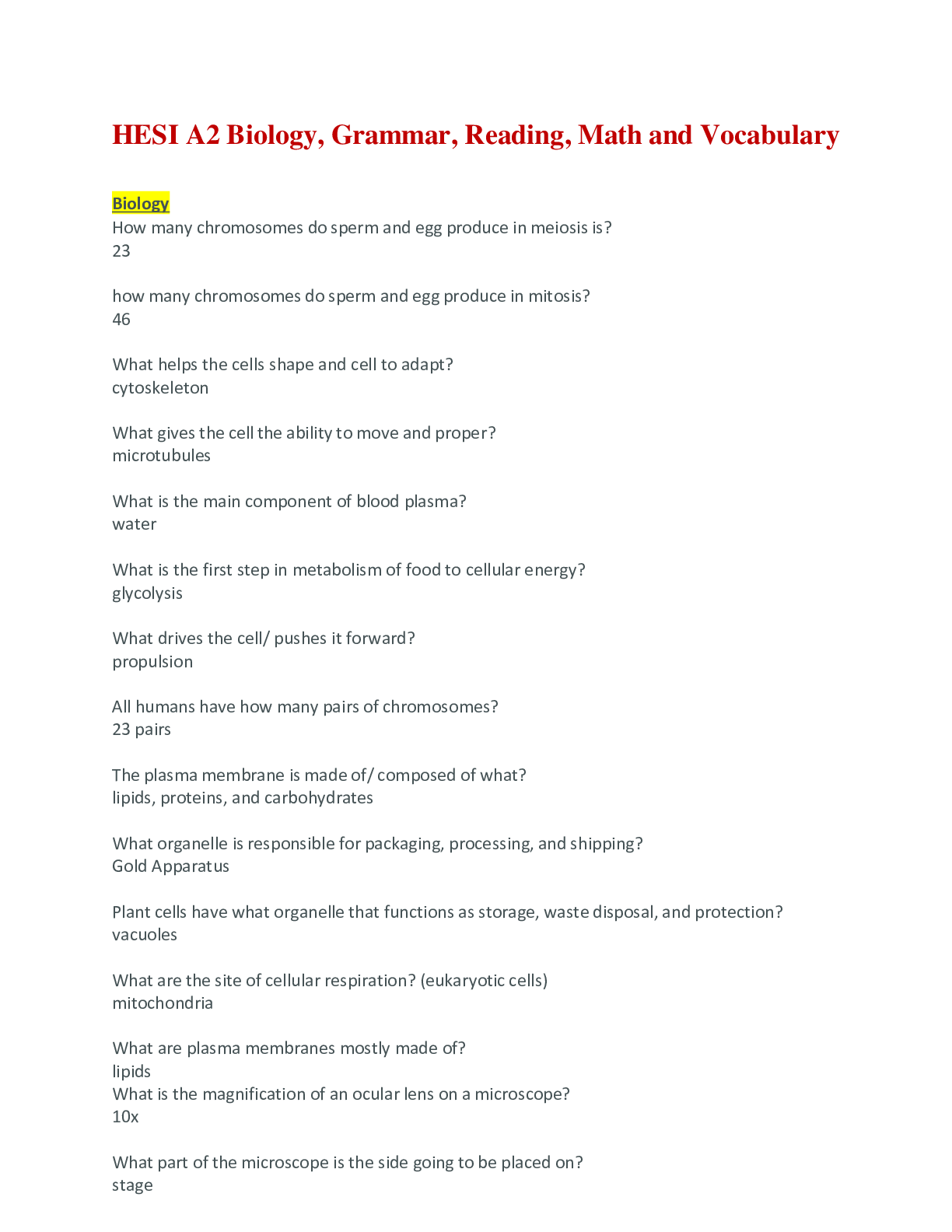
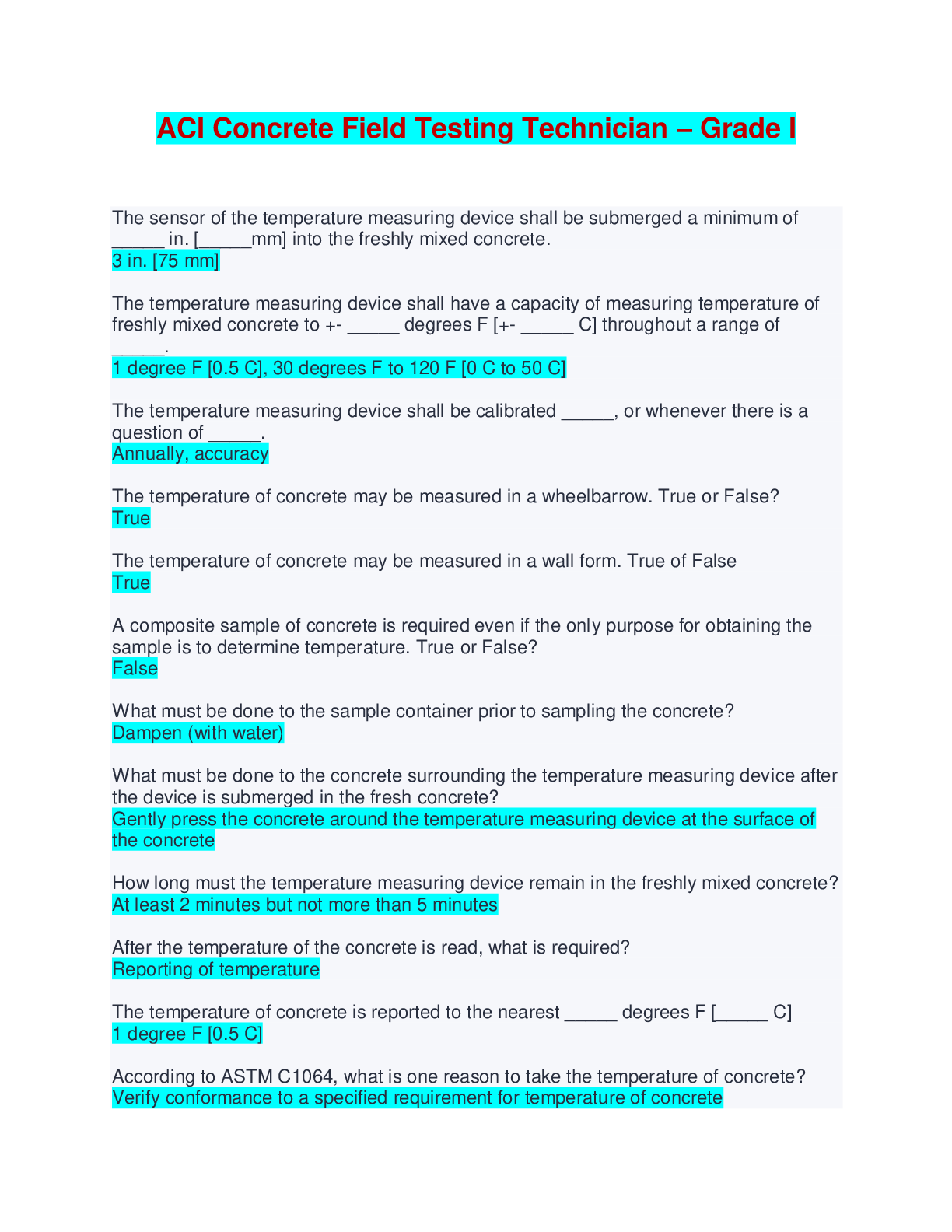
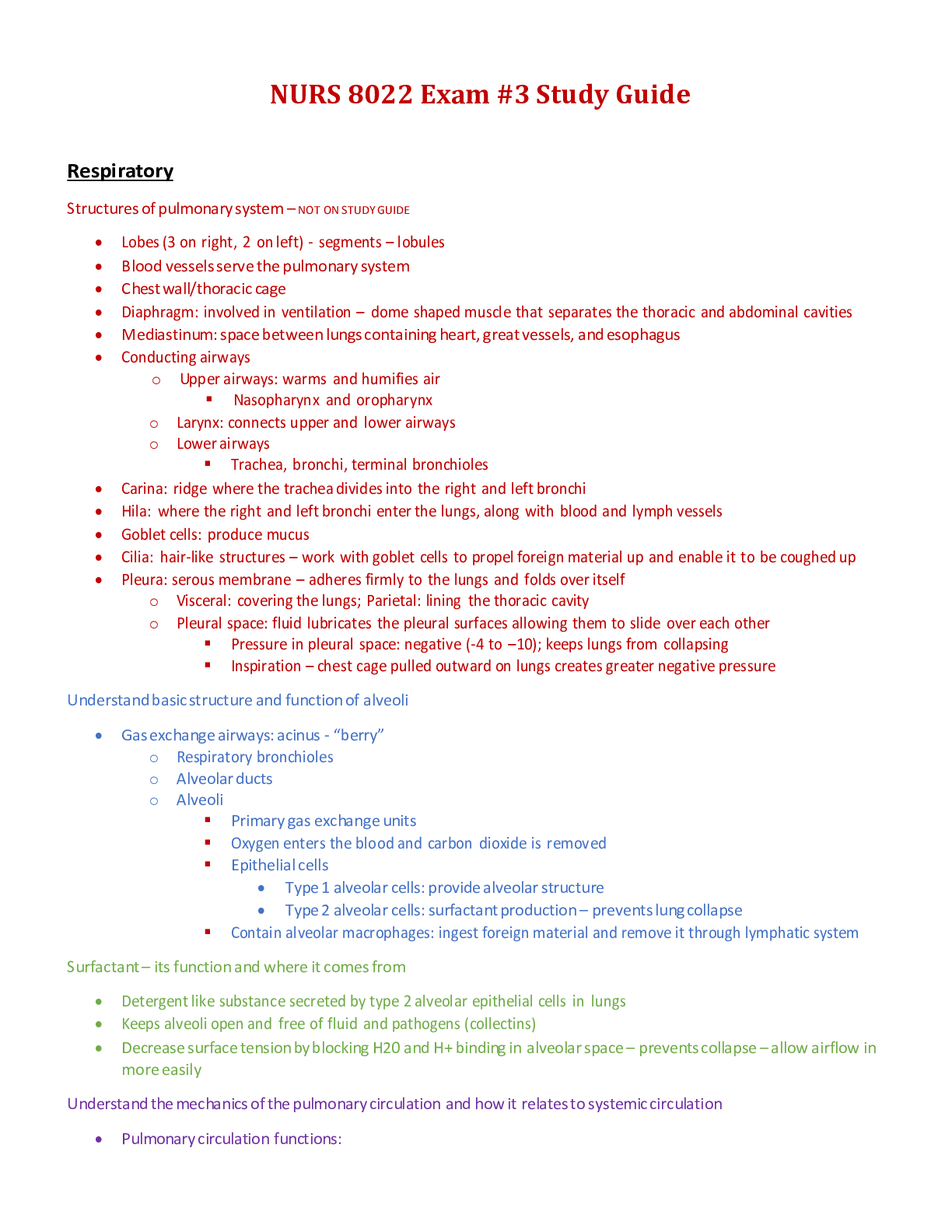
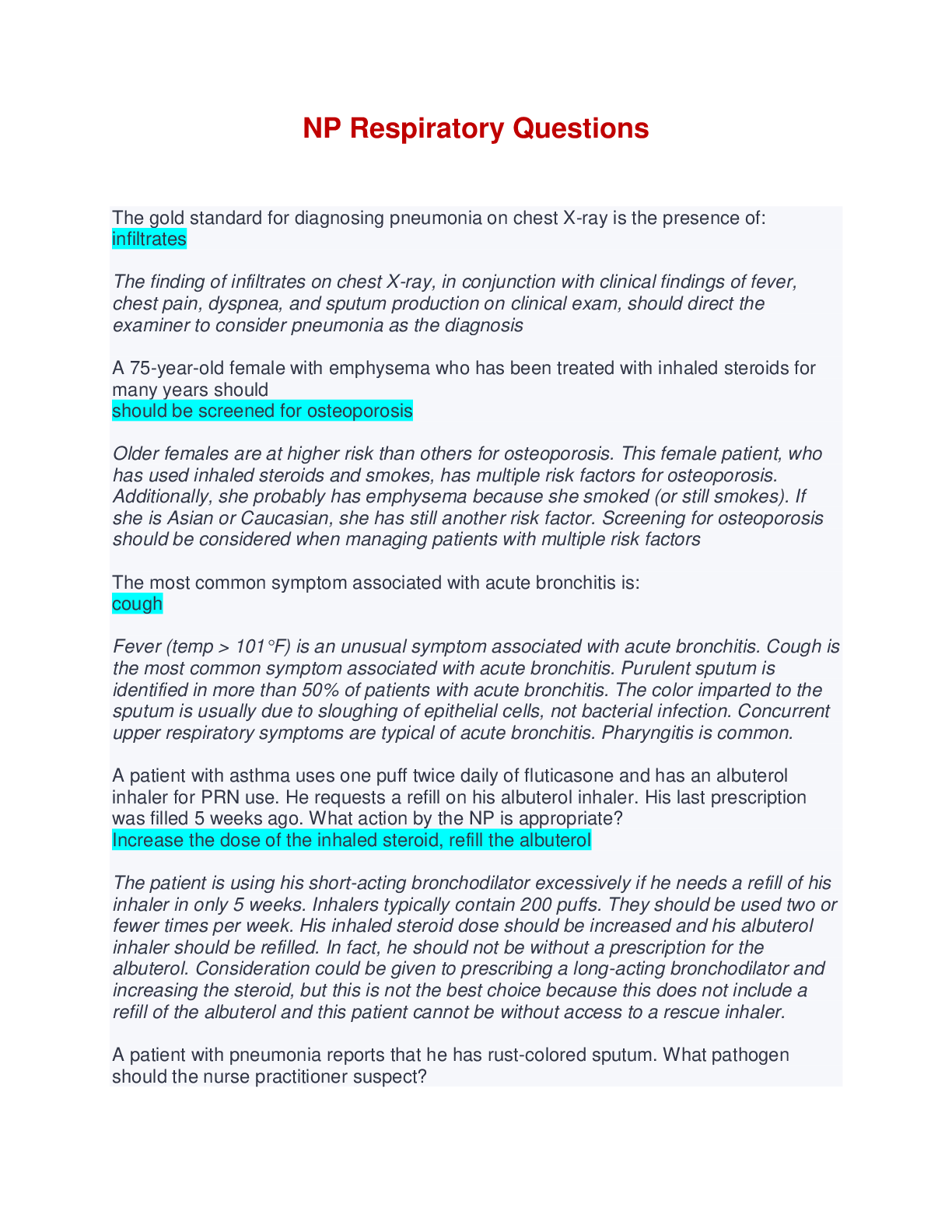
Cybersecurity Essentials Final Quiz | Questions with complete solutions A cybersecurity specialist is asked to identify the potential criminals known to attack the organization. Which type of hacker... s would the cybersecurity specialist be least concerned with? black hat hackers gray hat hackers script kiddies white hat hackers Which statement best describes a motivation of hacktivists? They are trying to show off their hacking skills. They are interested in discovering new exploits. They are curious and learning hacking skills. They are part of a protest group behind a political cause. What is an example of early warning systems that can be used to thwart cybercriminals? Infragard ISO/IEC 27000 program Honeynet project CVE database Which technology should be used to enforce the security policy that a computing device must be checked against the latest antivirus update before the device is allowed to connect to the campus network? SAN VPN NAC NAS Which data state is maintained in NAS and SAN services? stored data data in-transit encrypted data data in-process What are three states of data during which data is vulnerable? (Choose three.) purged data stored data data in-process data encrypted data decrypted data in-transit Which technology can be used to ensure data confidentiality? hashing identity management encryption RAID A cybersecurity specialist is working with the IT staff to establish an effective information security plan. Which combination of security principles forms the foundation of a security plan? secrecy, identify, and nonrepudiation confidentiality, integrity, and availability technologies, policies, and awareness encryption, authentication, and identification What are the two most effective ways to defend against malware? (Choose two.) Implement strong passwords. Implement a VPN. Implement RAID. Update the operating system and other application software. Implement network firewalls. Install and update antivirus software. What is an impersonation attack that takes advantage of a trusted relationship between two systems? man-in-the-middle spoofing spamming sniffing Users report that the network access is slow. After questioning the employees, the network administrator learned that one employee downloaded a third-party scanning program for the printer. What type of malware might be introduced that causes slow performance of the network? virus worm spam phishing Which statement describes a distributed denial of service attack? An attacker views network traffic to learn authentication credentials. An attacker builds a botnet comprised of zombies. An attacker sends an enormous quantity of data that a server cannot handle. One computer accepts data packets based on the MAC address of another computer. What type of application attack occurs when data goes beyond the memory areas allocated to the application? buffer overflow RAM Injection SQL injection RAM spoofing What type of attack has an organization experienced when an employee installs an unauthorized device on the network to view network traffic? sniffing spoofing phishing spamming A penetration testing service hired by the company has reported that a backdoor was identified on the network. What action should the organization take to find out if systems have been compromised? Look for policy changes in Event Viewer. Scan the systems for viruses. Look for unauthorized accounts. Look for usernames that do not have passwords. The IT department is tasked to implement a system that controls what a user can and cannot do on the corporate network. Which process should be implemented to meet the requirement? user login auditing a biometric fingerprint reader observations to be provided to all employees a set of attributes that describes user access rights Smart cards and biometrics are considered to be what type of access control? administrative technological logical physical Which access control should the IT department use to restore a system back to its normal state? compensative preventive corrective detective A user has a large amount of data that needs to be kept confidential. Which algorithm would best meet this requirement? 3DES ECC RSA Diffie-Hellman Alice and Bob use a pre-shared key to exchange a confidential message. If Bob wants to send a confidential message to Carol, what key should he use? the private key of Carol the public key of Bob the same pre-shared key he used with Alice a new pre-shared key What happens as the key length increases in an encryption application? Keyspace increases proportionally. Keyspace decreases exponentially. Keyspace decreases proportionally. Keyspace increases exponentially. In which situation would a detective control be warranted? when the organization needs to repair damage when the organization needs to look for prohibited activity when the organization cannot use a guard dog, so it is necessary to consider an alternative after the organization has experienced a breach in order to restore everything back to a normal state [Show More]
Last updated: 1 hour ago
Preview 3 out of 9 pages
Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$12.00
Document information
Connected school, study & course
About the document
Uploaded On
Jul 17, 2024
Number of pages
9
Written in
Additional information
This document has been written for:
Uploaded
Jul 17, 2024
Downloads
0
Views
2