Business > QUESTIONS & ANSWERS > University of Maryland IFSM 201 Quiz 7 (All)
University of Maryland IFSM 201 Quiz 7
Document Content and Description Below
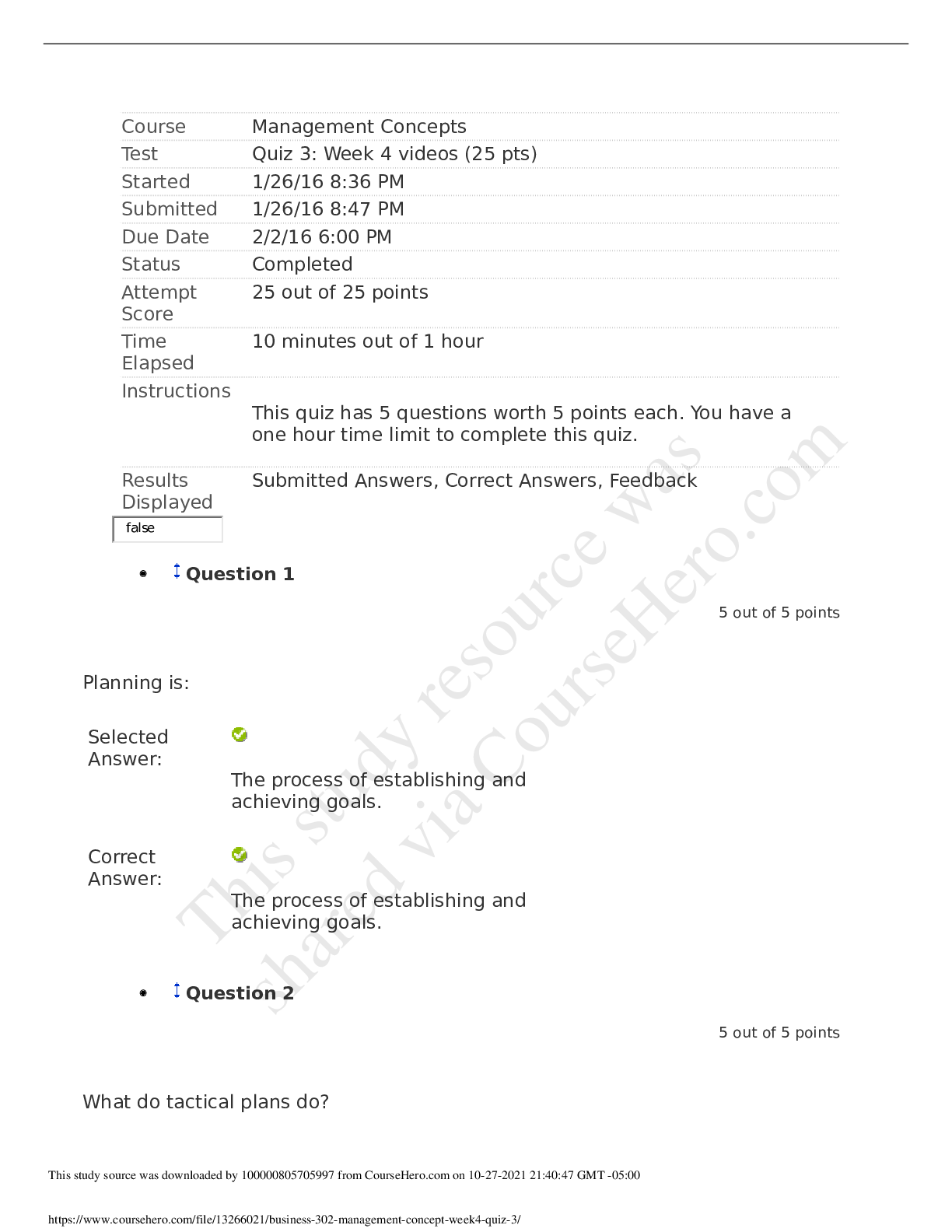
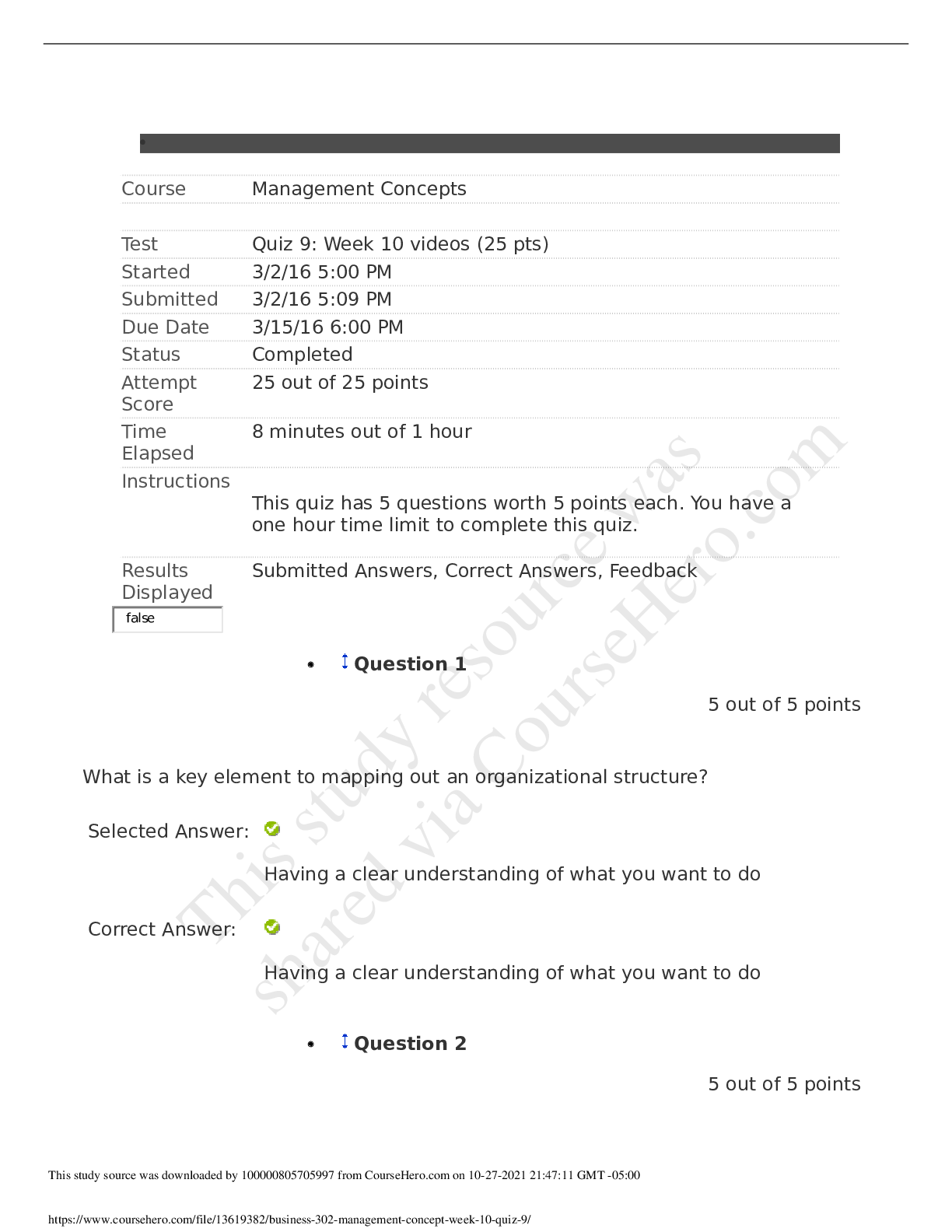
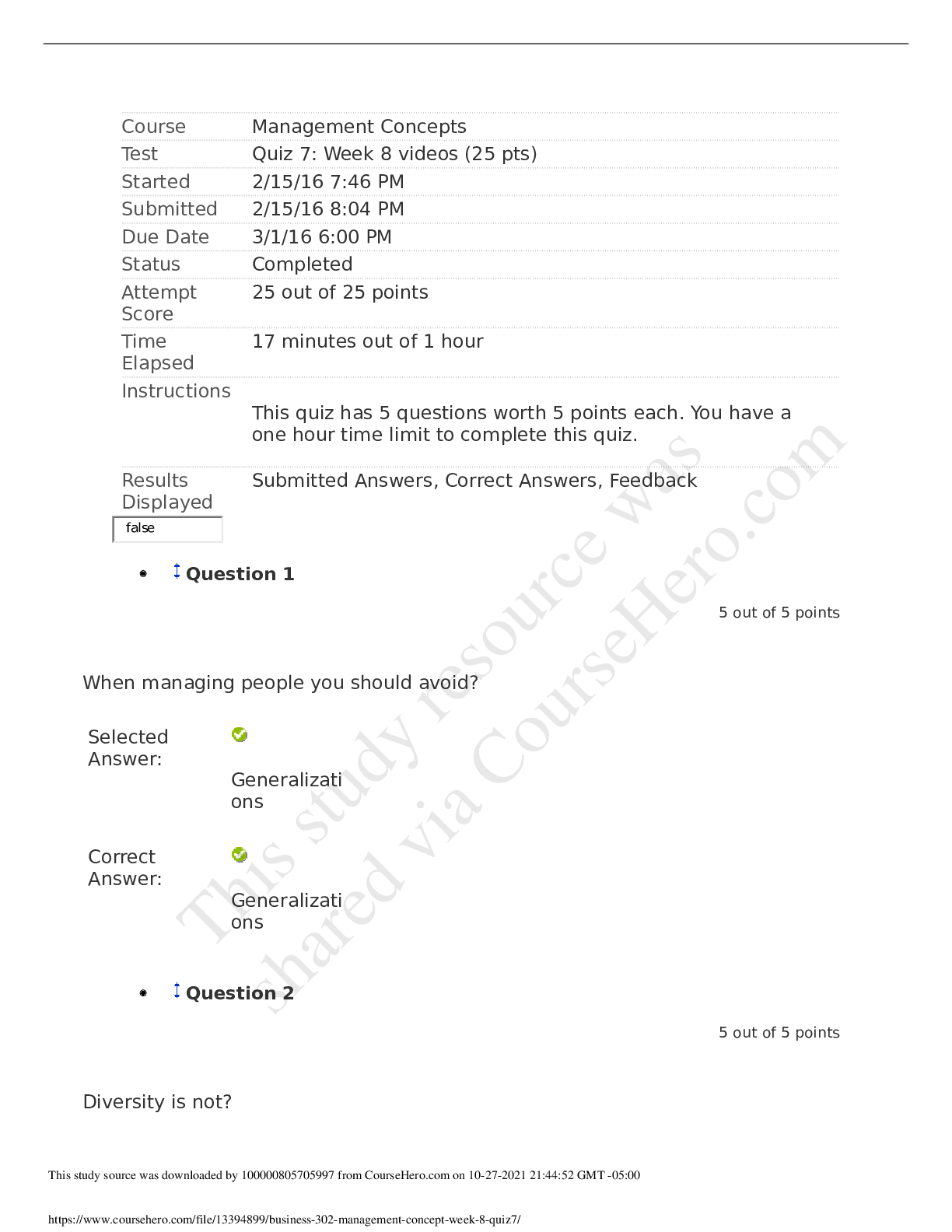
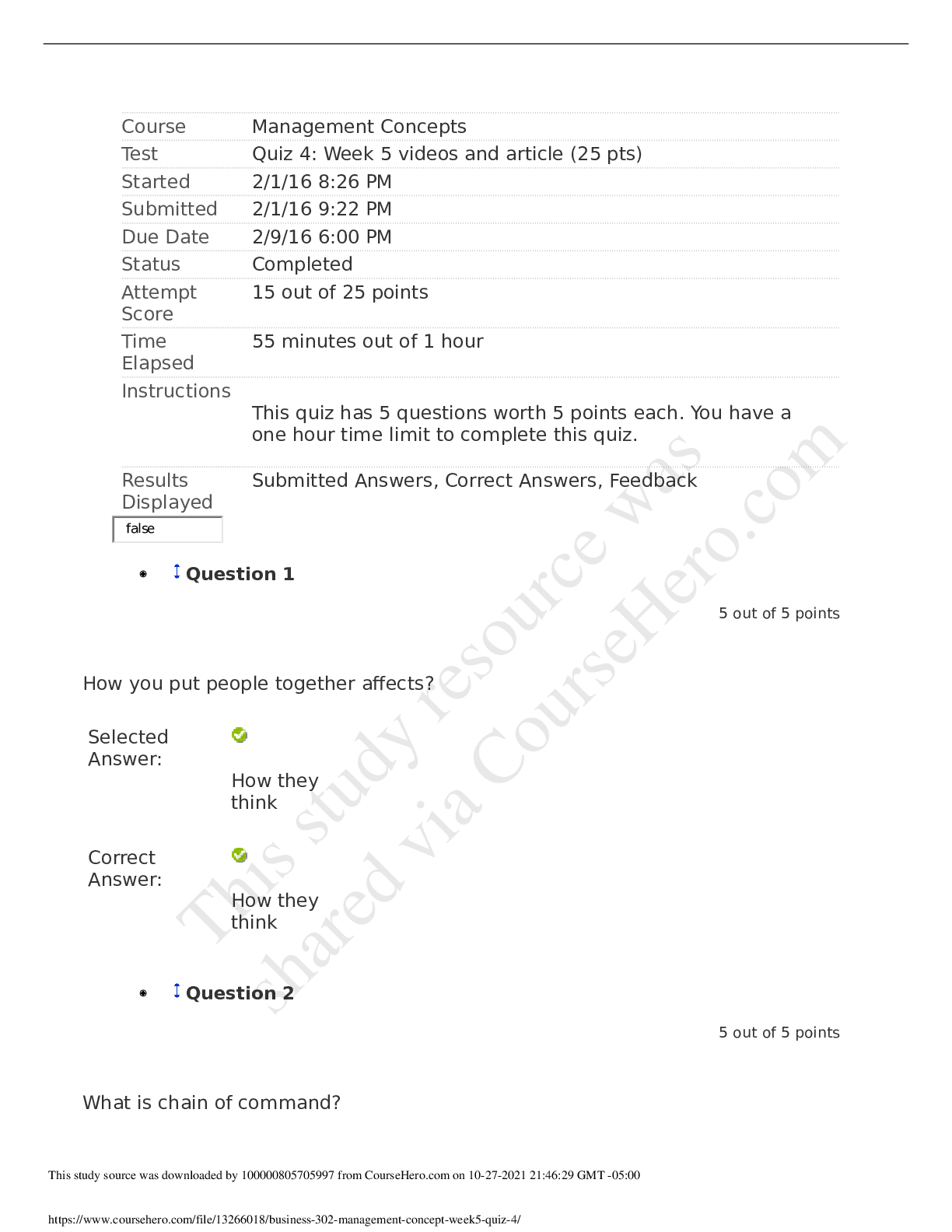
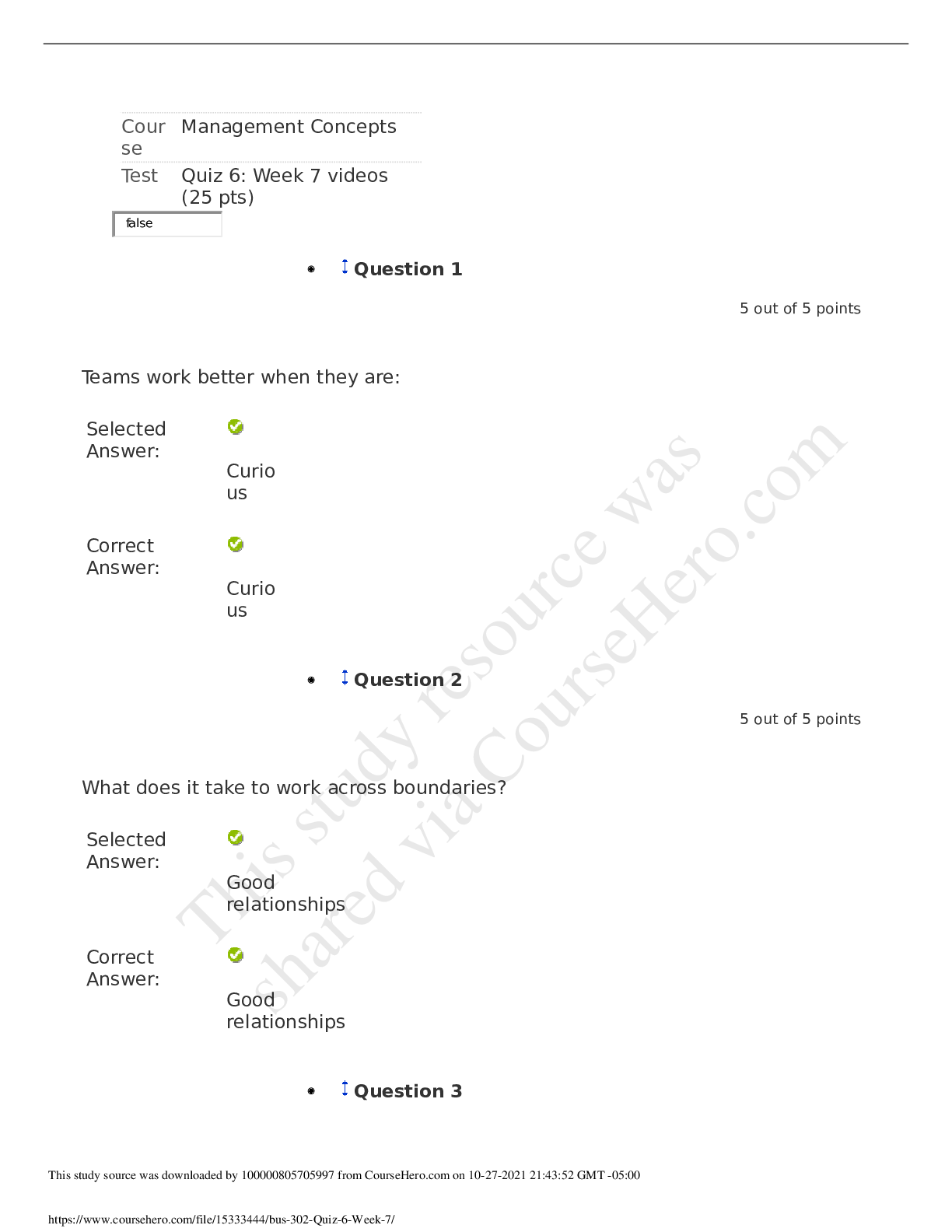
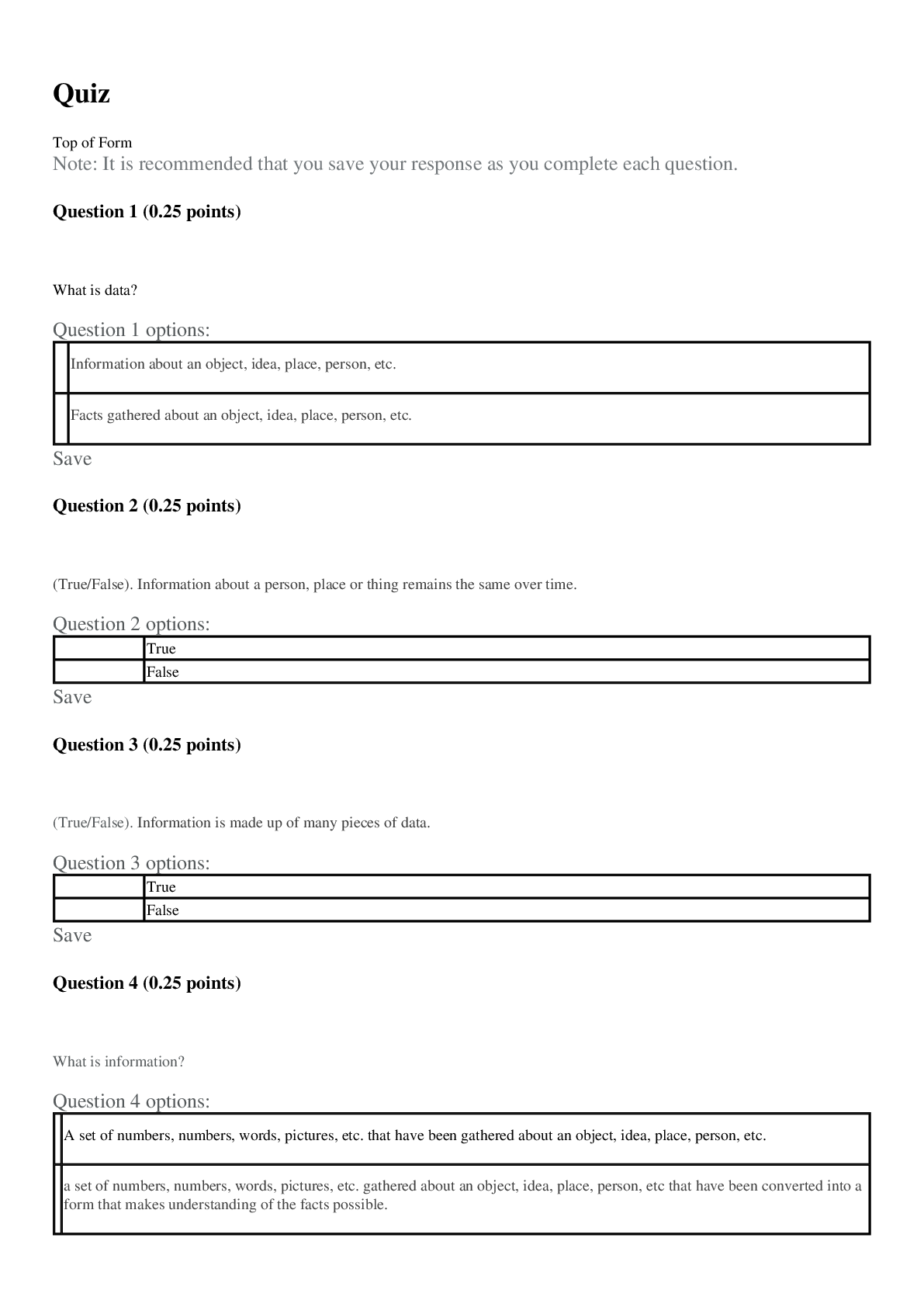
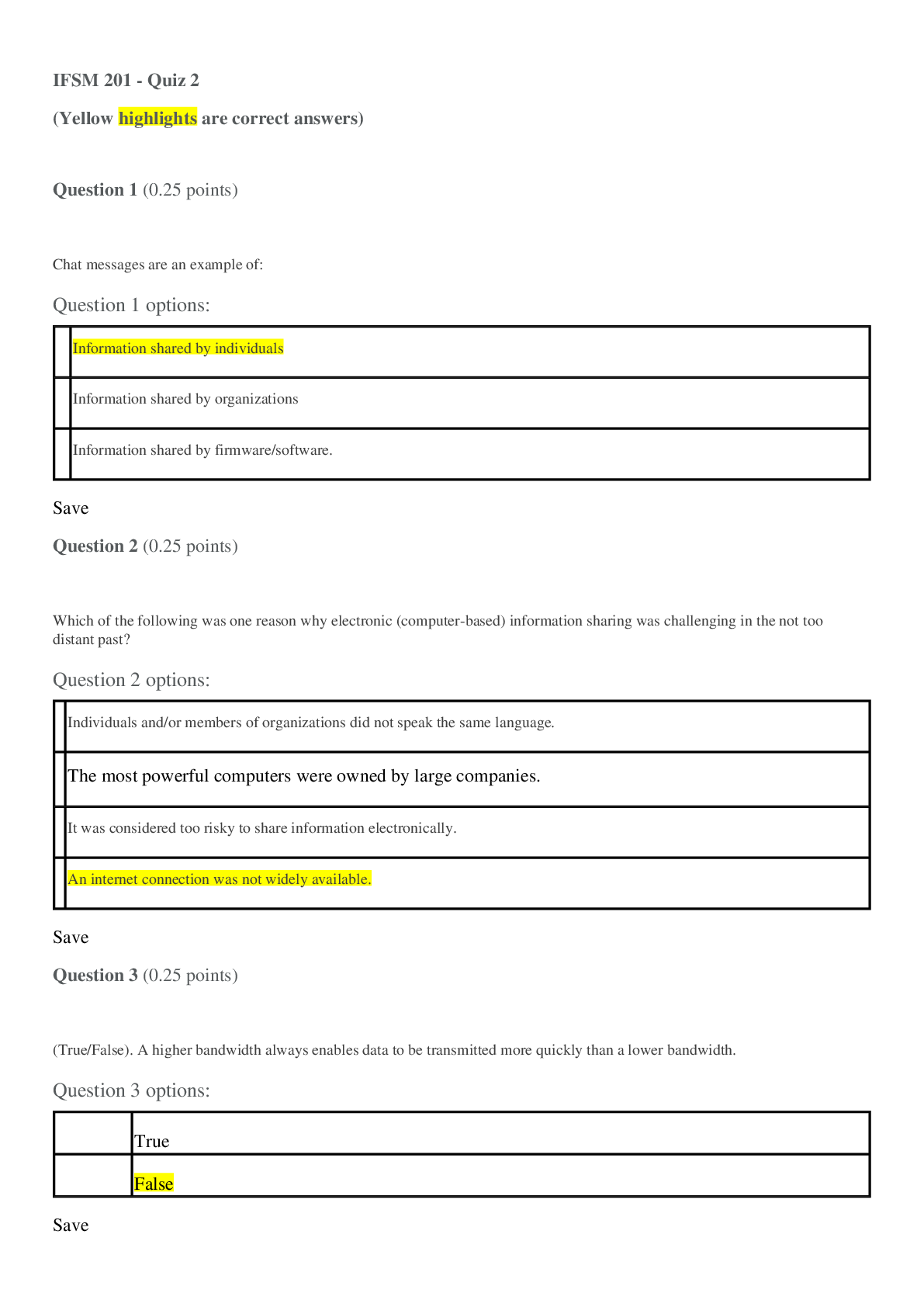
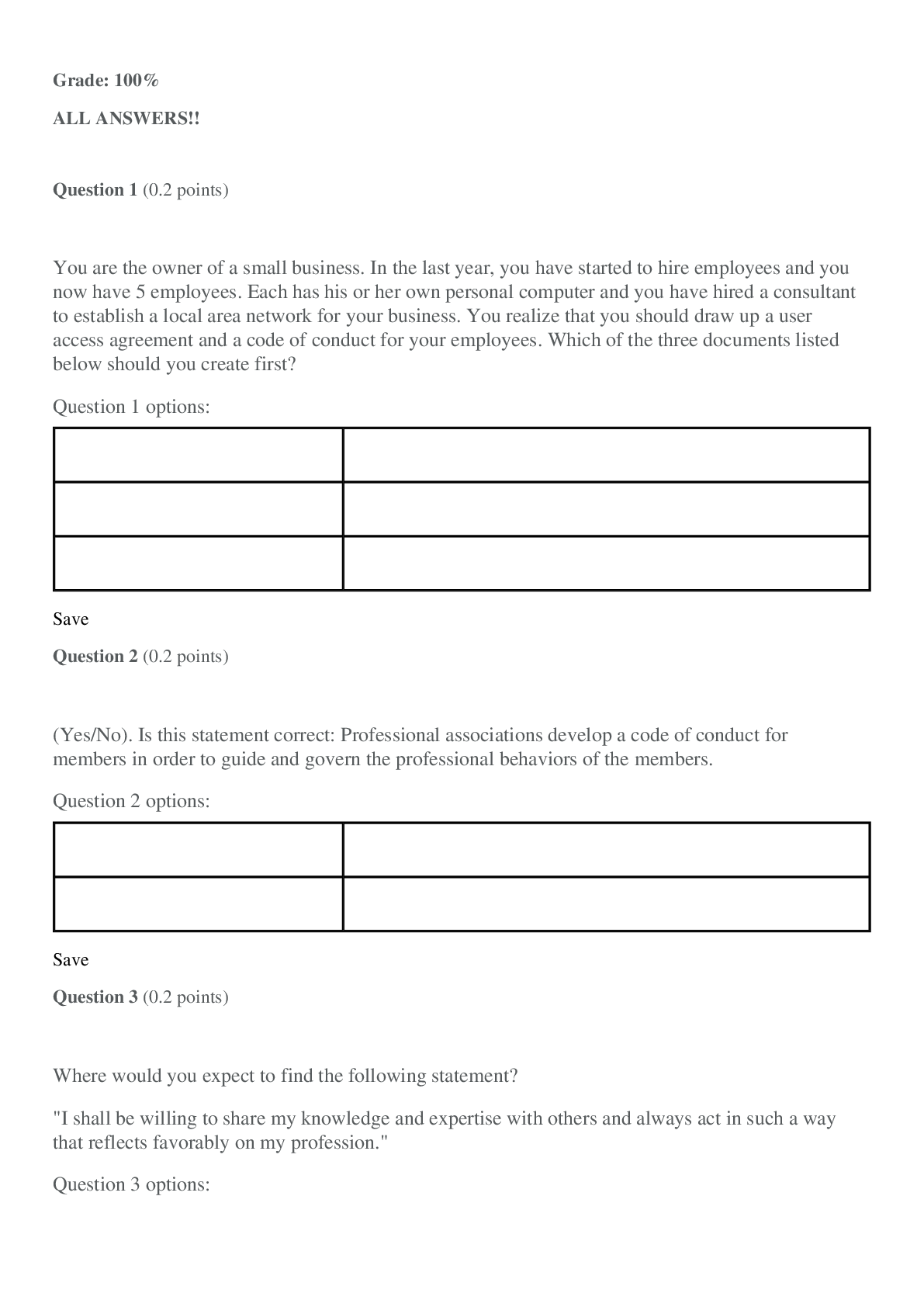
University of Maryland IFSM 201 Quiz 7 Question 1 Points: 10 out of 10 What might a member of a professional organization be doing when they refer to the organization’s code of ethics? F... inding out how one becomes a member of the professional organization Finding out whether a business practice is legal Clarifying whether a business practice violates the code of ethics Finding out what fines are imposed for violating the code of ethics Question 2 Points: 10 out of 10 How is “compromise” defined in the context of information technology and information security? A compromise is a security breach that is always perpetrated by a malicious attacker. A compromise is the potential for an intrusion into a computer system or unauthorized access to an online account, file, or other resource. A compromise is a breach in the security of a computer system, an account, a file, or another online resource. A compromise is a security breach that is never the result of an accidental action by a user. Question 3 Points: 0 out of 10 What is a cyberstalker? The intended victim of repeated continuous, unwanted communication One whose online hostile behavior is intended to harm another or others A person whose online hostile behavior avoids confronting the victim face-to-face A person who acts alone and anonymously when targeting others with continuous, unwanted communications. Question 4 Points: 0 out of 10 Using any of several different tools (Online White pages, Peoplefinders, Wink People Finder, etc.) someone has found your name and address. What other information would be needed in order for them to access your ONLINE bank account or credit card account records? Your social security number Your driver's license number Your user ID and password Question 5 Points: 10 out of 10 True or false? The Digital Millennium Copyright Act governs behavior of internet service providers but does not affect individuals on the internet. True False Question 6 Points: 10 out of 10 Would the following behavior most likely be a violation of an employee code of conduct? Using your work computer to invite friends and co-workers to a party at your home. Yes No More information is needed. Question 7 Points: 0 out of 10 Medical records are protected by the Health Insurance Portability and Accountability Act (HIPAA). Can your medical records be made available to others who request this information (employers, insurance companies, other doctors)? Yes No Question 8 Points: 10 out of 10 Unsolicited e-mail messages sent from advertisers or cyber criminals are . Question 9 Points: 10 out of 10 Which of the following is good practice to ensure that you do not get malware on your computer from an online source? Do not open email attachments. Block all popups (activate the popup blocker for all sites). Use only the latest version(s) of the browser(s) you normally use to access the internet. Update your antivirus software either manually or automatically each time you connect to the internet. Question 10 Part 1: 0 out of 10 Part 2: 10 out of 10 Part 3: 10 out of 10 Points: 20 out of 30 Which of the following statements are true regarding PII? Select True or False for each option. PII is information that uniquely identifies you in records that can be obtained online. PII is always used to illegally gain access to your online records. PII is safe because only you have this combination of name, social security number, and bank account, credit card numbers, or driver’s license number. Feedback Part 1 Incorrect. PII contains unique information about you that is tied to online records. Part 2 Correct. Not all use of PII is for illegal access purposes. Part 3 Correct. Your PII must be protected in order to keep it safe. Question 11 Points: 0 out of 10 Which option here would be a way to remember the user IDs and passwords that poses less risk than other options listed. Use the same ID and password for all, and change them frequently (every 30 days). Use the same ID but a different password for all. Scramble the IDs and passwords among the sites and keep a secure record somewhere. Create a base word/phrase and change the same 2-3 characters in that word/phrase for each site. Question 12 Points: 0 out of 10 Would the following incident be an example of social engineering/phishing? You receive an e-mail from the local police department asking you to update your information so that alerts can be sent out to you. The information requested includes your driver’s license number and telephone number. Yes No Question 13 Points: 10 out of 10 Which of the following is the biggest risk of using social networking? An increase in ability to connect with others online An increase in charges from the social networking provider An increase in likelihood of private information being disclosed An increase in spam delivered to your email account Question 14 Points: 10 out of 10 True or false? User access agreements (acceptable use policies) generally outline the acceptable uses of IT resources, but seldom mention unacceptable uses. True False [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$7.00
Document information
Connected school, study & course
About the document
Uploaded On
Mar 17, 2021
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Mar 17, 2021
Downloads
0
Views
30