Computer Science > PROJECT REPORT > Iowa State University_CPR E MISC Microcontrollers and Digital Design Systems_ Installation of MITRE (All)
Iowa State University_CPR E MISC Microcontrollers and Digital Design Systems_ Installation of MITRE CALDERA (Att@ck framework) within the testbed environment.
Document Content and Description Below
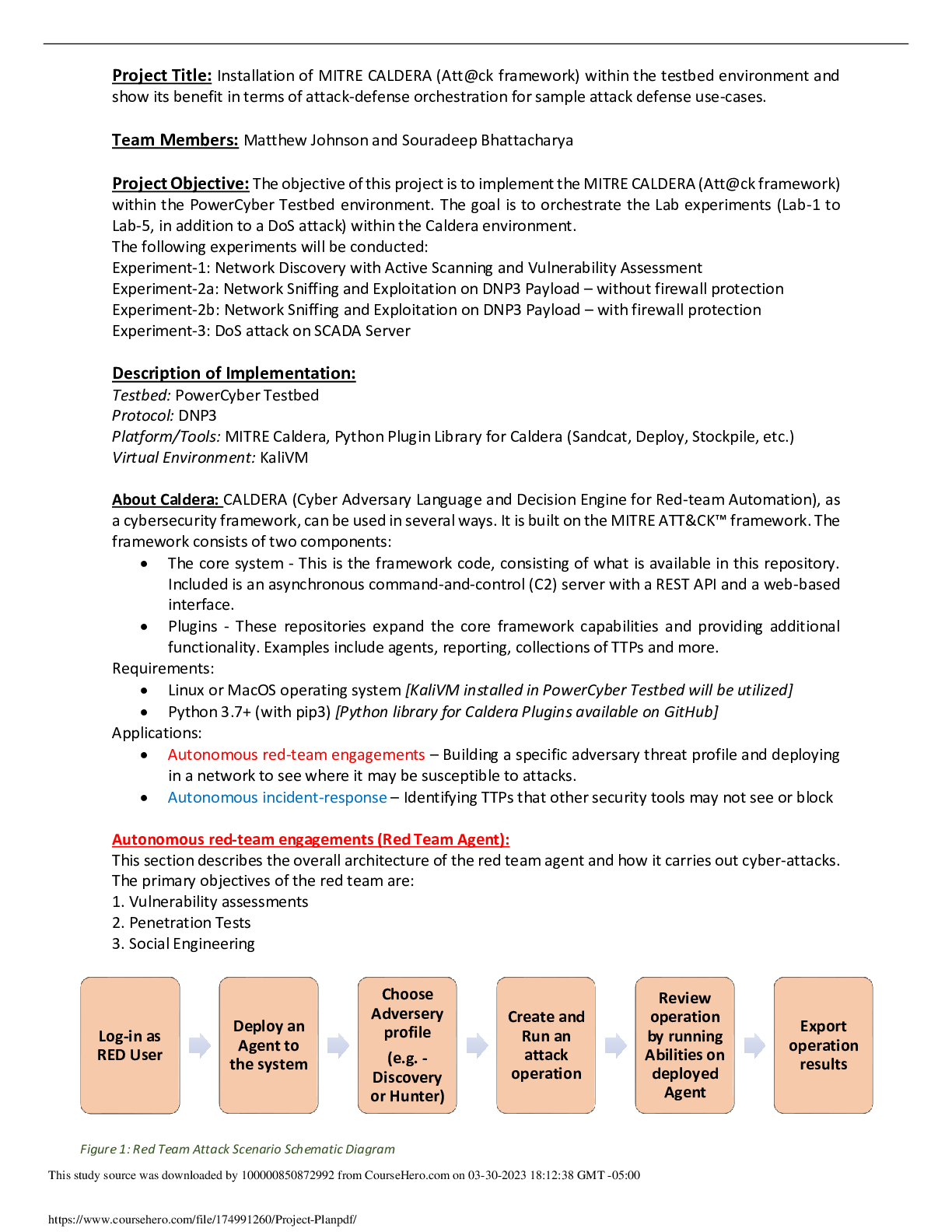
Project Title: Installation of MITRE CALDERA (Att@ck framework) within the testbed environment and show its benefit in terms of attack-defense orchestration for sample attack defense use-cases. Team... Members: Matthew Johnson and Souradeep Bhattacharya Project Objective: The objective of this project is to implement the MITRE CALDERA (Att@ck framework) within the PowerCyber Testbed environment. The goal is to orchestrate the Lab experiments (Lab-1 to Lab-5, in addition to a DoS attack) within the Caldera environment. The following experiments will be conducted: Experiment-1: Network Discovery with Active Scanning and Vulnerability Assessment Experiment-2a: Network Sniffing and Exploitation on DNP3 Payload – without firewall protection Experiment-2b: Network Sniffing and Exploitation on DNP3 Payload – with firewall protection Experiment-3: DoS attack on SCADA Server Description of Implementation: Testbed: PowerCyber Testbed Protocol: DNP3 Platform/Tools: MITRE Caldera, Python Plugin Library for Caldera (Sandcat, Deploy, Stockpile, etc.) Virtual Environment: KaliVM About Caldera: CALDERA (Cyber Adversary Language and Decision Engine for Red-team Automation), as a cybersecurity framework, can be used in several ways. It is built on the MITRE ATT&CK™ framework. The framework consists of two components: • The core system - This is the framework code, consisting of what is available in this repository. Included is an asynchronous command-and-control (C2) server with a REST API and a web-based interface. • Plugins - These repositories expand the core framework capabilities and providing additional functionality. Examples include agents, reporting, collections of TTPs and more. Requirements: • Linux or MacOS operating system [KaliVM installed in PowerCyber Testbed will be utilized] • Python 3.7+ (with pip3) [Python library for Caldera Plugins available on GitHub] Applications: • Autonomous red-team engagements – Building a specific adversary threat profile and deploying in a network to see where it may be susceptible to attacks. • Autonomous incident-response – Identifying TTPs that other security tools may not see or block Autonomous red-team engagements (Red Team Agent): This section describes the overall architecture of the red team agent and how it carries out cyber-attacks. The primary objectives of the red team are: 1. Vulnerability assessments 2. Penetration Tests 3. Social Engineering [Show More]
Last updated: 1 year ago
Preview 1 out of 3 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Mar 31, 2023
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Mar 31, 2023
Downloads
0
Views
48