Biology > STUDY GUIDE > BEST NETWORK+ N10-007 STUDY GUIDE 2019 (All)
BEST NETWORK+ N10-007 STUDY GUIDE 2019
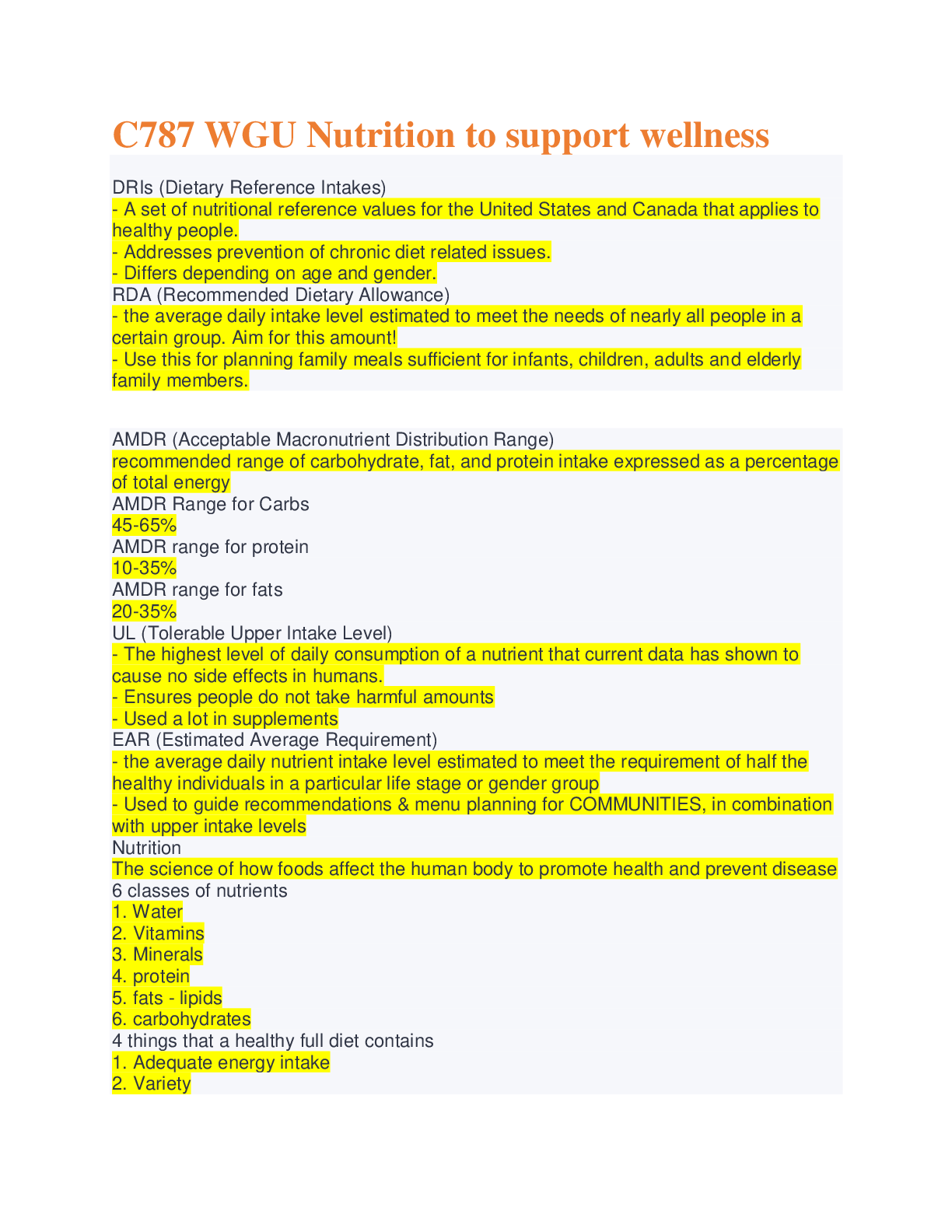
Document Content and Description Below
BEST NETWORK+ N10-007 STUDY GUIDE 2019 Which of the following physical LAN topologies requires the most cabling? A Star B WLAN C Bus D Ring Answer- A A network formed by interconnect... ing a PC to a digital camera via a USB cable is considered what type of network? A MAN B PAN C CAN D WAN Answer- B Which type of network is based on network clients sharing resources with one another? A Peer-to-peer B Client-peer C Client/Server D Peer-to-server Answer- A Which of the following provides the media (wired or wireless) to facilitate the transfer of data? A Router B Server C LAN D Client Answer- C What network type would help facilitate communications when large video or audio files need to be housed and transferred through the network? A WLAN B CAN C PAN D SAN Answer- D A company has various locations in a city interconnected using Metro Ethernet connections. This is an example of what type of network? A WAN B CAN C PAN D MAN Answer- D How many WAN links are required to create a full mesh of connections between five remote sites? A 20 B 5 C 10 D 15 Hint: Remember, the formula for the number of connections required for the full-mesh topology is n(n-1)/2, where n is the number of nodes. So, in this case, 5(5-1)/2 is 10. Answer- C Which of the following is an advantage of a peer-to-peer network, as compared with a client/server network? A Better performance B Simplified administration C More scalable D Less expensive Answer- D What type of wireless topology features the use of access points to facilitate network communications? A Mesh B Ad hoc C Ring D Infrastructure Answer- D Which of the following topologies offers the highest level of redundancy? A Hub and spoke B Bus C Partial mesh D Full mesh Answer- D Which device makes traffic-forwarding decisions based on MAC addresses? A Multiplexer B Switch C Router D Hub Answer- C Identify two advantages of a hub-and-spoke WAN topology as compared to a full-mesh WAN topology. 1) More scalable 2) Optimal routes 3) Lower cost 4) More redundancy A 1,2 & 3 B 1 & 3 Answer- B What is the range of well-known TCP and UDP ports? A 16,384-32,768 B Below 1024 C Below 2048 D Above 8192 Answer- B Identify the well-known UDP port number for NTP. A 143 B 123 C 69 D 53 Answer- B IP addresses reside at which layer of the OSI reference model? A Network layer B Transport layer C Data link layer D Session layer Answer- A Identify three e-mail protocols. 1) POP3 2) SMTP 3) SNMP 4) IMAP4 A) 1, 3 & 4 B) 1, 2 & 4 Answer- B Which protocol supports a secure connection to a remote host via terminal emulation software? A SFTP B FTP C SSH D Telnet Answer- C Which layer of the OSI reference model contains the MAC and LLC sublayers? A Physical layer B Transport layer C Network layer D Data link layer Answer- D Identify the four layers of the TCP/IP stack. 1) Session 2) Transport 3) Internet 4) DLL 5) Network 6) Application 7) Network Interface layer A 2, 3, 6 & 7 B 1, 2, 3 & 4 Answer- A Which approach to bandwidth usage consumes all the available frequencies on a medium to transmit data? A Baseband B Broadband C Simplex D Time-division multiplexing Answer- A Windowing is provided at what layer of the OSI reference model? A DLL B Network C Transport D Physical Answer- C Which of the following is a connectionless transport layer protocol? A IP B TCP C UDP D H.323 Answer- C Which of the following categories of UTP cabling are commonly used for 1000BASE-T networks? (Choose two.) 1) Cat 6f 2) Cat 5 3) Cat 5e 4) Cat 6 A 1 & 4 B 3 & 4 Answer- B Identify two differences between an Ethernet bridge and an Ethernet switch. (Choose two.) 1) bridges typically oprerate faster than switches 2) switches use ASICS to make forwarding decisions where as Bridges make their own forwarding decisions in software 3) Bridges can base their forwarding decision on logical Network layer addresses 4) switches usually have higher port densities than bridges A 1 & 3 B 2 & 4 Answer- B A router has 12 ports. How many broadcast domains does the router have? A 1 B 2 C 12 D none Answer- C A router operating at Layer 3 primarily makes its forwarding decisions based on what address? A Source MAC B Source IP C destination Mac D destination IP Answer- D What IoT technology is specialized for monitoring sensor data and is ultimately led by Garmin? A Bluetooth B Ant+ C Zwave D RFID Answer- B Which network infrastructure device primarily makes forwarding decisions based on Layer 2 MAC addresses? A Switch B Hub C Multilayer switch D Router Answer- A A switch has 12 ports. How many collision domains does the switch have? A 12 B none C 1 D 2 Answer- A Automating the management and configuration of many different network devices, thanks to a centralized controller, refers to what technology? A software-defined networking B virtualized networking C Content distribution D Internet of things Answer- A Which of the following is a VoIP signaling protocol used to set up, maintain, and tear down VoIP phone calls? A MX B IMAP C SIP D RJ-45 Answer- C Which type of cable might be required for installation in a drop ceiling, which is used as an open-air return duct? A Twin-axial B Riser C Plenum D Multimode Answer- C What is the first DHCP message sent by a client attempting to obtain IP address information from a DHCP server? A DHCPOFFER B DHCPACK C DHCPDISCOVER D DHCPREQUEST Answer- C What specialized network device is commonly used to load-balance traffic across multiple servers in a group? A Content Switch B Firewall C DNS Server D Content Engine Answer- A What switch feature allows you to connect a network sniffer to a switch port and tells the switch to send a copy of frames seen on one port out the port to which your network sniffer is connected? A Port mirroring B Port redirect C Port interception D Port duplexing Answer- A What is the maximum amount of power a switch is allowed to provide per port according to the IEEE 802.3af standard? A 15.4W B 26.4W C 32.4W D 7.7W Answer- A If two devices simultaneously transmit data on an Ethernet network and a collision occurs, what does each station do in an attempt to resend the data and avoid another collision? A Each device randomly picks a priority value and the device with the highest value transmits B Each device that's a random back off timer and the device will attempt retransmit after the timer expires C Each device compares it's priority value (determined by IP address) with it's own and the device with the highest priority value transmits D Each device waits for Clear to Send (CTS) signal from the switch Answer- B Which IEEE 802.1X component checks the credentials of a device wanting to gain access to the network? A Authentication server B Supplicant C Authenticator D Access point Answer- A Which of the following statements are true regarding VLANs? (Choose two.) 1) For traffic to pass between two vlans, traffic must be routed 2) Because of the switch's MAC address table traffic does not need to be routed between the vlans 3) A Vlan has a single collision domain 4) A Vlan has a single broadcast domain A 1 & 4 B 2 & 3 Answer- A What is the IEEE standard for link aggregation? A 802.3ad B 802.1d C 802.3af D 802.1q Answer- A Identify the distance limitation of a 1000BASE-T Ethernet network. A 500 m B 2 km C 100 m D 185 m Answer- C In a topology running STP, every network segment has a single ______________ port, which is the port on that segment that is closest to the root bridge in terms of cost. A Non-designated B Non-root C Root D Designated Answer- D What name is given to a VLAN on an IEEE 802.1Q trunk whose frames are not tagged? A Default VLAN B Management VLAN C VLAN 0 D Native VLAN Answer- D What type of IPv4 address is 239.1.2.3? A Multicast B Unicast C Experemental D Private use only Answer- A What is the prefix notation for a subnet mask of 255.255.255.240? A /28 B /29 C /20 D /24 Answer- A Which of the following are dynamic approaches to assigning routable IP addresses to networked devices? (Choose two.) 1) APIPA 2) BOOTP 3) DHCP 4) Zeroconf A 2 & 3 B 1 & 4 Answer- A What is the binary representation of the decimal number 117? A 01101001 B 10110110 C 01110101 D 10110101 Answer- C A client with an IP address of 172.16.18.5/18 belongs to what network? A 172.16.128.0/18 B 172.16.96.0/18 C 172.16.64.0/18 D 172.16.0.0/18 Answer- D What technology allows for the automatic assignment of the host portion of an IPv6 address? A EUI64 B Neighbor Discovery C Anycast D Dual stack Answer- A The binary number 10110100 has what decimal equivalent? A 180 B 172 C 190 D 114 Answer- A How can the following IPv6 address be condensed? 2009:0123:4040:0000:0000:000:000A:100B A 2009::123:404:A:100B B 2009:0123:4040::0::000A:100B C 2009:123:4040::A:100B D 2009::123:404:A:1B Answer- C What is the class of IP address 192.168.1.0 /24? A Class D B Class C C Class B D Class A Answer- B Your company has been assigned the 192.168.30.0/24 network for use at one of its sites. You need to use a subnet mask that will accommodate seven subnets while simultaneously accommodating the maximum number of hosts per subnet. What subnet mask should you use? A /28 B /24 C /26 D /27 Answer- D What is the maximum number of possible nodes for /27 CIDR mask? A 14 B 64 C 30 D 32 Answer- C What NAT variation automatically assigns an inside global address from a pool of available addresses? A PAT B GNAT C SNAT D DNAT Answer- D Which of the following is a distance-vector routing protocol with a maximum usable hop count of 15? A RIP B IS-IS C BGP D OSPF Answer- A What multicast protocol is used between clients and routers to let routers know which of their interfaces are connected to a multicast receiver? A SPT switchover B IGMP C PIM-DM D PIM-SM Answer- B Which of the following are distance-vector routing protocol features that can prevent routing loops? (Choose two.) 1) Reverse path forwarding check (rpf) 2) Split horizon 3) Poison reverse 4) Rendezvous point A 1 & 2 B 2 & 3 Answer- B What routing protocol characteristic indicates the believability of the routing protocol (as opposed to other routing protocols)? A Weight B SPF Algorithm C Administrative distance D Metric Answer- C What is the network address and subnet mask of a default route? A 0.0.0.0/0 B 255.255.255.255/32 C 0.0.0.0/32 D 255.255.255.255/0 Answer- A Which of the following routing protocols is an EGP? A IS-IS B RIP C OSPF D BGP Answer- D What NAT IP address is a public IP address that maps to an inside device? A Outside local B Inside global C Inside local D Outside global Answer- B What protocol is used to request a MAC address that corresponds to a known IPv4 address on the local network? A ICMP B ARP C IGMP D TTL Answer- B What DSL variant has a distance limitation of 18,000 ft. between a DSL modem and its DSLAM? A ADSL B SDSL C VDSL D HDSL Answer- A ISDN is considered to be what type of WAN connection? A Circuit switched connection B Dedicated leased line C Cell-switched connection D Packet-switched connection Answer- A What is the data rate of an OC-3 connection? A 155.52 Mbps B 159.25 Gbps C 51.84 Mbps D 622 Mbps Answer- A Which PPP authentication method offers one-way authentication and sends credentials in clear text? A WEP B CHAP C PAP D MS-CHAP Answer- C Which of the following WAN technologies use unshielded twisted pair (UTP)? (Choose three.) 1) DSL Modem 2) POTS dialup modem 3) Cable modem 4) IDSN A 1,2,4 B 1,3,4 Answer- A What is the size of an MPLS header? A 16 bits B 32 bits C 4 bits D 8 bits Answer- B What kind of network is used by many cable companies to service their cable modems and has both fiber-optic and coaxial cabling? A DOCSIS B Composite C HFC D Head-end Answer- C How big is the payload part of an ATM cell? A 64 bytes B 5 bytes C 48 bytes D 53 bytes Answer- C What locally significant identifier is used by a Frame Relay network to reference a virtual circuit? A DLCI B TEI C MAC D VPI/VCI Answer- A What is the most common topology seen with a DMVPN? A Hub & Spoke (partial mesh) B Full mesh C Ring D Bus Answer- A How many channels on an Ē circuit are available for voice, video, or data? A 30 B 24 C 23 D 32 Answer- A Which of the following is used by IEEE 802.11n to achieve high throughput using multiple antennas for transmission and reception? A LACP B MIMO C DSSS D FHSS Answer- B Which IEEE 802.11 variant supports a maximum speed of 54Mbps and uses the 2.4GHz band? A 802.11n B 802.11a C 802.11b D 802.11g Answer- D WLAN formed directly between wireless clients (without the use of a wireless AP) is referred to as what type of WLAN? A Enterprise mode B BSS C Personal mode D IBSS Answer- D When you're using the 2.4GHz band for multiple access points in a WLAN found in the United States, which nonoverlapping channels should you select? (Choose three.) 1) 10 2) 6 3) 5 4) 1 5) 0 6) 14 7) 11 A 2,4,7 B 1,2,4 Answer- A What technology do WLANs use to decide when they gain access to the wireless media? A SPF B DUAL C RSTP D CSMA/MA Answer- D What type of antenna, used in wireless APs and wireless routers in SOHO locations, radiates equal power in all directions? A Parabolic B Yagi C Unidirectional D Omnidirectional Answer- D When extending the range for a 2.4GHz WLAN, you can use nonoverlapping channels for adjacent coverage cells. However, there should be some overlap in coverage between those cells (using nonoverlapping channels) to prevent a connection from dropping as a user roams from one coverage cell to another. What percentage of coverage overlap should you recommend for these adjacent cells? A 5-10% B 20-25% C 15-20% D 10-15% Answer- D WEP's RC4 approach to encryption uses a 24-bit string of characters added to transmitted data, such that the same plain-text data frame will never appear as the same WEP-encrypted data frame. What is this string of characters called? A Initialization vector B Chips C Orthagonol Descriptor D Session key Answer- A Which standard developed by the Wi-Fi Alliance implements the requirements of IEEE 802.11i? A TKIP B WPÁ C WEP D MIC Answer- B Which security technique uses wireless technologies to create an invisible boundary around some point? A Geofencing B War driving C TKIP D WPÁ Answer- A If a WLAN does not need a user to give credentials to associate with a wireless AP and access the WLAN, what type of authentication is in use? A WEP B SSID C Open D IV Answer- C What site provides a nearly identical level of service with virtually no downtime? A Warm B Remote C Hot D Cold Answer- C If a network has the five nines of availability, how much downtime does it experience per year? A 26 mins B 12 mins C 5 mins D 30 mins Answer- C What type of backup solution is a point-in-time, read-only copy of data? A Snapshot B Virtual C Differential D Incremental Answer- A What is the maximum recommended one-way delay for voice traffic? A 75 ms B 100 ms C 150 ms D 25 ms Answer- C What mode of NIC redundancy has only one NIC active at a time? A Publisher/subscriber B Active-subscriber C Active-standby D Client-server Answer- C Which of the following QoS mechanisms is considered an IntServ mechanism? A RED B cRTP C LLQ D RSVP Answer- D A lack of bandwidth can lead to which QoS issues? (Choose three.) 1) packet drops 2) prioritization 3) jitter 4) delay A 1,3,4 B 1,2,4 Answer- A Identify the congestion-avoidance mechanism from the following list of QoS tools. A RSVP B LLQ C cRTP D RED Answer- D What performance optimization technology uses a network appliance, which can receive a copy of content stored elsewhere (for example, a video presentation located on a server at a corporate headquarters), and serves that content to local clients, thus reducing the bandwidth burden on an IP WAN? A Load balancer B LACP C Carp D Content Engine Answer- D What command produced the following snippet of output? OUTPUT OMITTED... lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> mtu 16384 inet 127.0.0.1 netmask 0xff000000 inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x1 inet6 fd4e:f9d5:c34e:acd1:5a5:caff:fefa:1551 prefixlen 128 gif0: flags=8010<POINTOPOINT,MULTICAST> mtu 1280 stf0: flags=0<> mtu 1280 en0: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500 ether 58:55:ca:fa:15:51 inet6 fe80::5a5:caff:fefa:1551%en0 prefixlen 64 scopeid 0x4 inet 192.168.1.245 netmask 0xffffff00 broadcast 192.168.1.255 media: autoselect status: active OUTPUT OMITTED... A ipconfig /all B ifconfig /all C ifconfig Answer- C Which of the following Windows commands enables you to display NetBIOS over TCP/IP information? A dig B nbtstat C route D netstat Answer- B What command produced the following snippet of output? OUTPUT OMITTED... ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 62169 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;pearsonitcertification.com. IN A ;; ANSWER SECTION: pearsonitcertification.com. 10800 IN A 64.28.85.25 ;; Query time: 202 msec ;; SERVER: 192.168.1.1#53(192.168.1.1) ;; WHEN: Wed Jun 1 20:41:57 2011 ;; MSG SIZE rcvd: 60 OUTPUT OMITTED... A dig pearsonitcertification.com B traceroute -d pearsonitcertification.com C nbtstat pearsonitcertification.com D netstat -a pearsonitcertification.com Answer- A What option would you specify after the ipconfig command to display the IP address of a Windows PC's DNS server? A /fqdn B /all C None of these is needed D /full Answer- B Which of the following commands would you issue on a UNIX host to send five ICMP echo messages to a device with an IP address of 10.1.1.1? A ping 10.1.1.1 (none of these are required bc the default is five already) B ping -c 5 10.1.1.1 C ping -t 5 10.1.1.1 D ping 10 10.1.1.1 Answer- B Which of the following commands is used on a UNIX host to generate information about each router hop along the path from a source to a destination? A traceroute B ping -r C tracert D ping -t Answer- A What protocol is used by the ping command? A IGMP B PIM C ICMP D RTP Answer- C Which Windows commands could have produced the following output? (Choose two.) ========================================================================= Interface List 20...00 0c 29 3a 21 67 ......Intel(R) PRO/1000 MT Network Connection #2 11...00 0c 29 3a 21 5d ......Intel(R) PRO/1000 MT Network Connection 1........................... Software Loopback Interface 1 12...00 00 00 00 00 00 00 e0 Microsoft ISATAP Adapter 13...00 00 00 00 00 00 00 e0 Teredo Tunneling Pseudo-Interface ========================================================================= IPv4 Route Table ========================================================================== Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 172.16.202.2 172.16.202.128 10 0.0.0.0 0.0.0.0 172.16.202.2 172.16.202.129 10 127.0.0.0 255.0.0.0 On-link 127.0.0.1 306 127.0.0.1 255.255.255.255 On-link 127.0.0.1 306 127.255.255.255 255.255.255.255 On-link 127.0.0.1 306 172.16.202.0 255.255.255.0 On-link 172.16.202.128 266 172.16.202.0 255.255.255.0 On-link 172.16.202.129 266 172.16.202.128 255.255.255.255 On-link 172.16.202.128 266 172.16.202.129 255.255.255.255 On-link 172.16.202.129 266 172.16.202.255 255.255.255.255 On-link 172.16.202.128 266 172.16.202.255 255.255.255.255 On-link 172.16.202.129 266 224.0.0.0 240.0.0.0 On-link 127.0.0.1 306 224.0.0.0 240.0.0.0 On-link 172.16.202.129 266 224.0.0.0 240.0.0.0 On-link 172.16.202.128 266 255.255.255.255 255.255.255.255 On-link 127.0.0.1 306 255.255.255.255 255.255.255.255 On-link 172.16.202.129 266 255.255.255.255 255.255.255.255 On-link 172.16.202.128 266 1) netstat -a 2) nbtstat -r 3) netstat -r 4) route print A 1,2 B 3,4 Answer- B Which of the following UNIX commands can be used to check FQDN-to-IP-address resolution? (Choose three.) 1) host 2) nslookup 3) netstat 4) dig A 1,3,4 B 1,2,4 Answer- B Consider the following output: C:\> arp -a Interface: 172.16.202.128 --- 0xb Internet Address Physical Address Type 172.16.202.2 00-50-56-fd-65-2c dynamic 172.16.202.255 ff-ff-ff-ff-ff-ff static 224.0.0.22 01-00-5e-00-00-16 static 224.0.0.252 01-00-5e-00-00-fc static 255.255.255.255 ff-ff-ff-ff-ff-ff static What is the MAC address corresponding to the IP address of 172.16.202.2? A XXXX0016 B XXXX00FC C XXXXFFFF D XXXX652C Answer- D Identify the broad categories of SNMP message types. (Choose three.) 1) trap 2) get 3) put 4) set A 1,2,4 B 1,3,4 Answer- A What Microsoft Windows application enables you to view a variety of log types, including application, security, and system logs? A Performance Monitor B MMC C Control Panel D Event Viewer Answer- D You must send commands to a remote router and you are communicating over an unsecure channel. What protocol should you use? A HTTP B SSH C Telnet D FTP Answer- B What piece of test equipment enables you to locate a break in a fiber-optic cable? A TDR B Cable certifier C Crimper D OTDR Answer- D What device, traditionally used by telephone technicians, enables you to tap into a phone line to, for example, check a line for dial tone? A Butt set B Tester C Fox and Hound D TDR Answer- A One error occurred during the transmission of 8 bits. What is the BER? A .0125 B .25 C .125 D .025 Answer- C A toner probe is also known as what? A OTDR B Tip and Ring C Fox and Hound D TDR Answer- C What is a snapshot of performance on a typical usage level for the network? A Incremental report B SLA C Baseline D Differential report Answer- C SNMP uses a series of objects to collect information about a managed device. The structure, similar to a database, containing these objects is referred to as what? A RIB B MIB C DUAL D LSA Answer- B Which piece of test equipment can you use to test the throughput of a Cat 5 cable? A Cable certifier B BERT C Multimeter R OTDR Answer- A A notification that a specific operation failed to complete successfully is classified as what syslog severity level? A Critical (2) B Errors (3) C Warnings (4) D Informational (6) Answer- C What is a best practice to prevent you from damaging a circuit board with static from your body? A Ground the circuit board B Stand on a carpeted floor while working on the circuit board C Wear an esd wrist strap D Apply antistatic spray on the circuit board Answer- C From the following list, identify the detection methods commonly used by IPS sensors. (Choose three.) 1) Policy-based 2) Distribution based 3) Signature based 4) Behavioral based A 1,3,4 B 1,2,4 Answer- A In what type of attack does the attacker compromise multiple systems and then instruct those compromised systems, called zombies, to simultaneously flood a target system with traffic? A Buffer overflow B DDoS C DoS D TCP SYN Flood Answer- B Which of the following security solutions consists of software running on a host to protect that host against a collection of well-known attacks? A NIPS B HIPS C NIDS D L2F Answer- B Which of the following are characteristics of RADIUS? (Choose two.) 1) UDP 2) TCP 3) Only encrypts password in an Authentication packet 4) Encrypts an entire authentication packet A 1 & 3 B 1 & 2 Answer- A Which of the following is an IPSec protocol that provides authentication and integrity services but does not support encryption? A ESP B IKE phase I C IKE phase III [Show More]
Last updated: 1 year ago
Preview 1 out of 142 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
May 18, 2022
Number of pages
142
Written in
Additional information
This document has been written for:
Uploaded
May 18, 2022
Downloads
0
Views
40















.png)