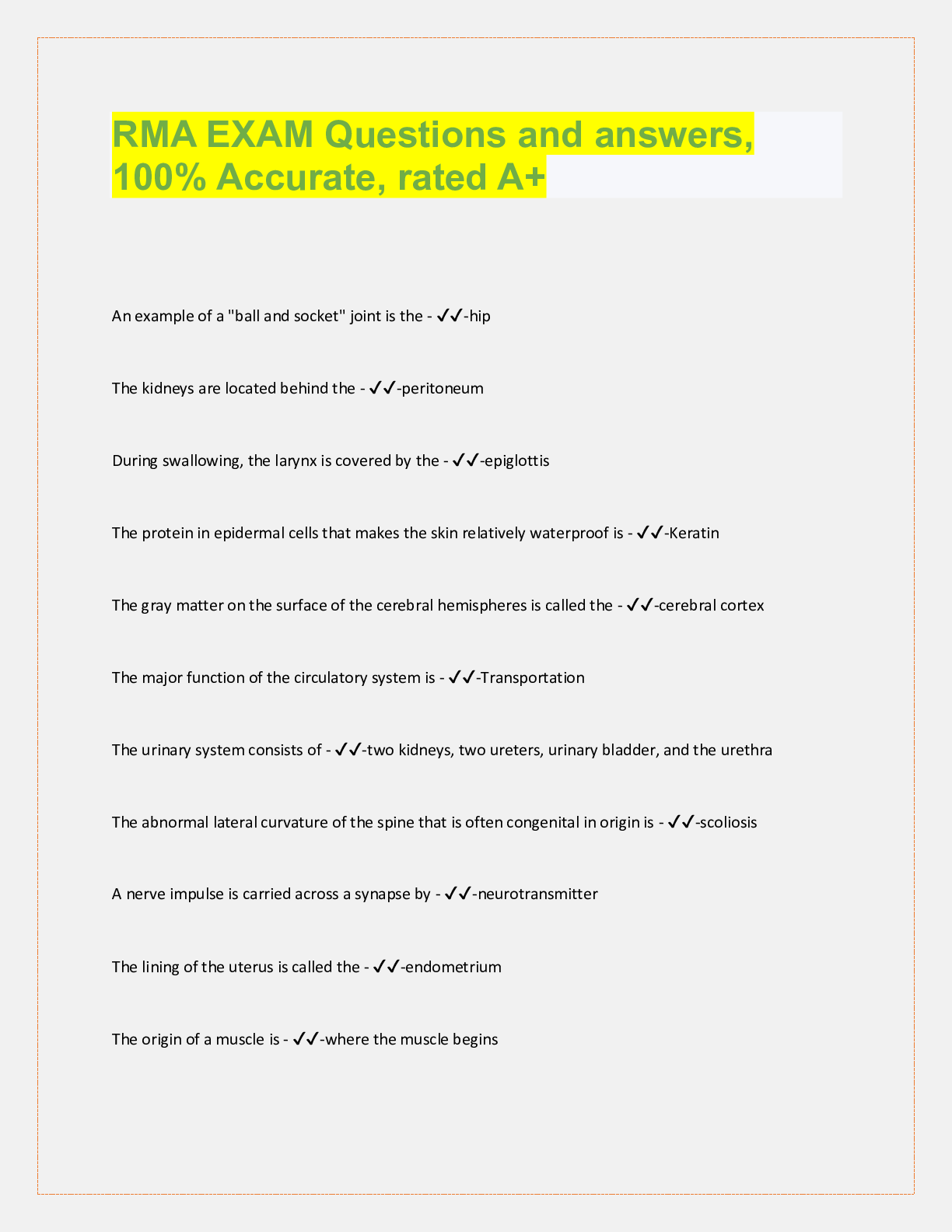
Public Health > QUESTIONS & ANSWERS > Find an example of a security risk assessment Request for Proposal (RFP) (All)
Find an example of a security risk assessment Request for Proposal (RFP)
Document Content and Description Below
Find an example of a security risk assessment Request for Proposal (RFP) online. Review the required services and discuss if this is truly a security risk assessment or a related activity. How would... you modify or amend the RFP to align it with the goals of a security risk assessment? Answer & Explanation Solved by a verified expert The following is an example of the security risk assessment RFP or Request for the proposal: A security risk assessment defines, evaluates, and implements key device safety controls. This also focuses on avoiding security bugs and vulnerabilities in software. The scope of risk assessment models is influenced by variables such as scale, growth rate, capital, and asset portfolio. Organizations may perform general evaluations while they are facing budget or time constraints. However, generic evaluations do not typically include comprehensive mappings between properties, related hazards, defined risks, impacts, and controls to mitigate. Request for Proposal or RFP for an Evaluation of Information Security System to identify the Agency's information security program's protection posture and to define security control and device gaps. The following are the required services that can be a security risk assessment: The HIPAA Compliance Toolkit Program, developed by the National Institute of Standard and Technology or NIST is designed to help companies better understand the HIPAA Compliance Rule specifications, enforce those standards, and analyze those implementations in their operating situation. Goal users involve, but are not limited to, HIPAA-protected companies, business associates as well as other organizations like those providing the application, evaluation and enforcement services of the HIPAA Protection Regulation. The following are the reasons to modify the RFP that can be aligned with the goals of the security risk assessment: The HIPAA Security Law focuses primarily on safeguarding EPHI. While FISMA refers to all federal agencies and to all kinds of information, based on their roles and use of EPHI, only a set of agencies are subject to the HIPAA Protection Regulation. All organizations protected by HIPAA, including certain federal agencies, must comply with the Protection Code. The Security The rule focuses primarily on protecting EPHI's privacy, integrity, and availability as specified in the Security Rule. In addition, the Security Rule criteria, guidelines, and specifications for implementation refers to the following protected entities: Protected healthcare providers- Any clinical or other health service provider or supply a provider that transmits some health information in digital form in connection with such a transaction for which HHS has implemented a standard. Health Insurance- Any patient or community scheme covering or paying medical care expenses (for example, a health insurance provider and Medicare and social security programs). [Show More]
Last updated: 1 year ago
Preview 1 out of 6 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$7.00
Document information
Connected school, study & course
About the document
Uploaded On
Aug 05, 2022
Number of pages
6
Written in
Additional information
This document has been written for:
Uploaded
Aug 05, 2022
Downloads
0
Views
79










.png)


.png)