Information Technology > EXAM > CMIT 321 My week 5 quiz questions with the correct answers (All)
CMIT 321 My week 5 quiz questions with the correct answers
Document Content and Description Below
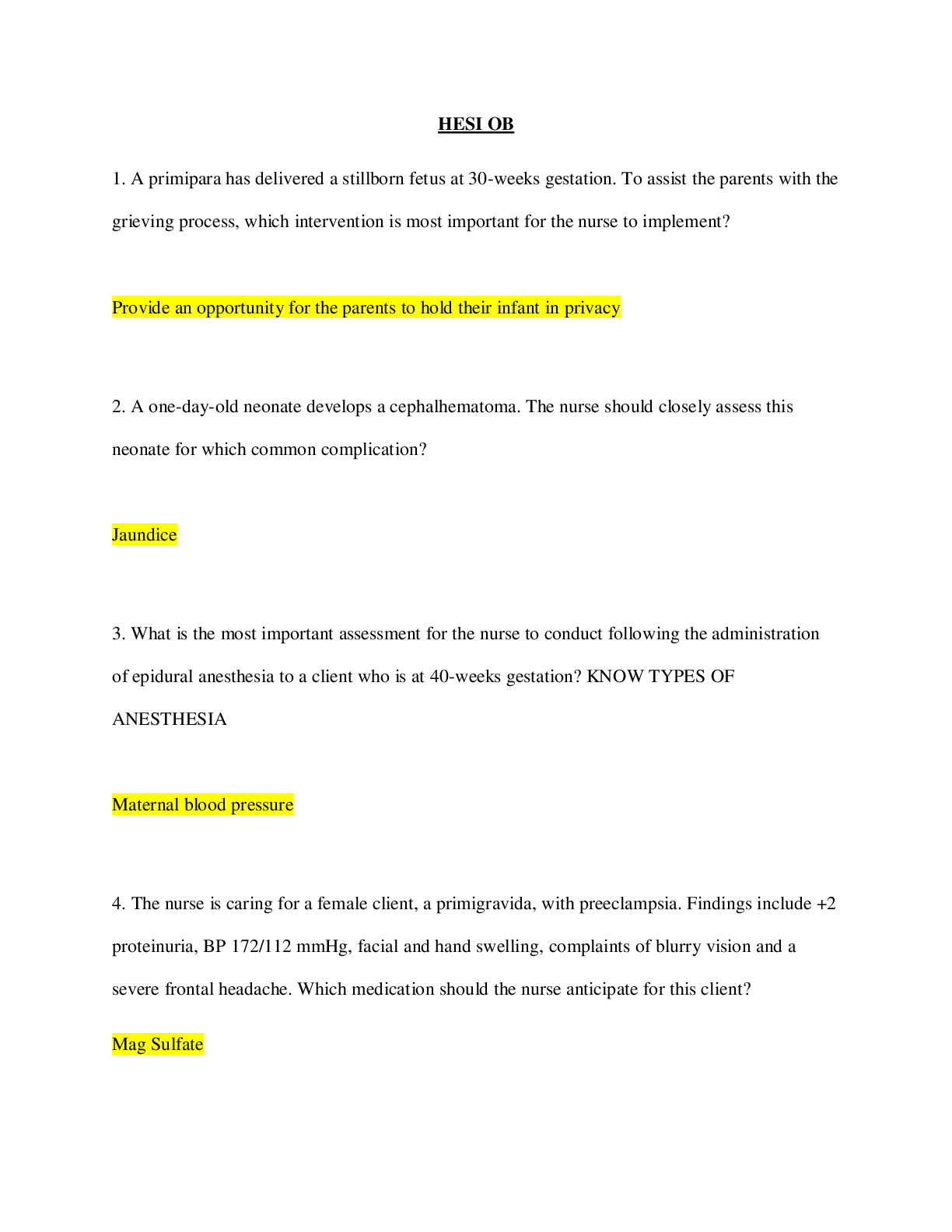
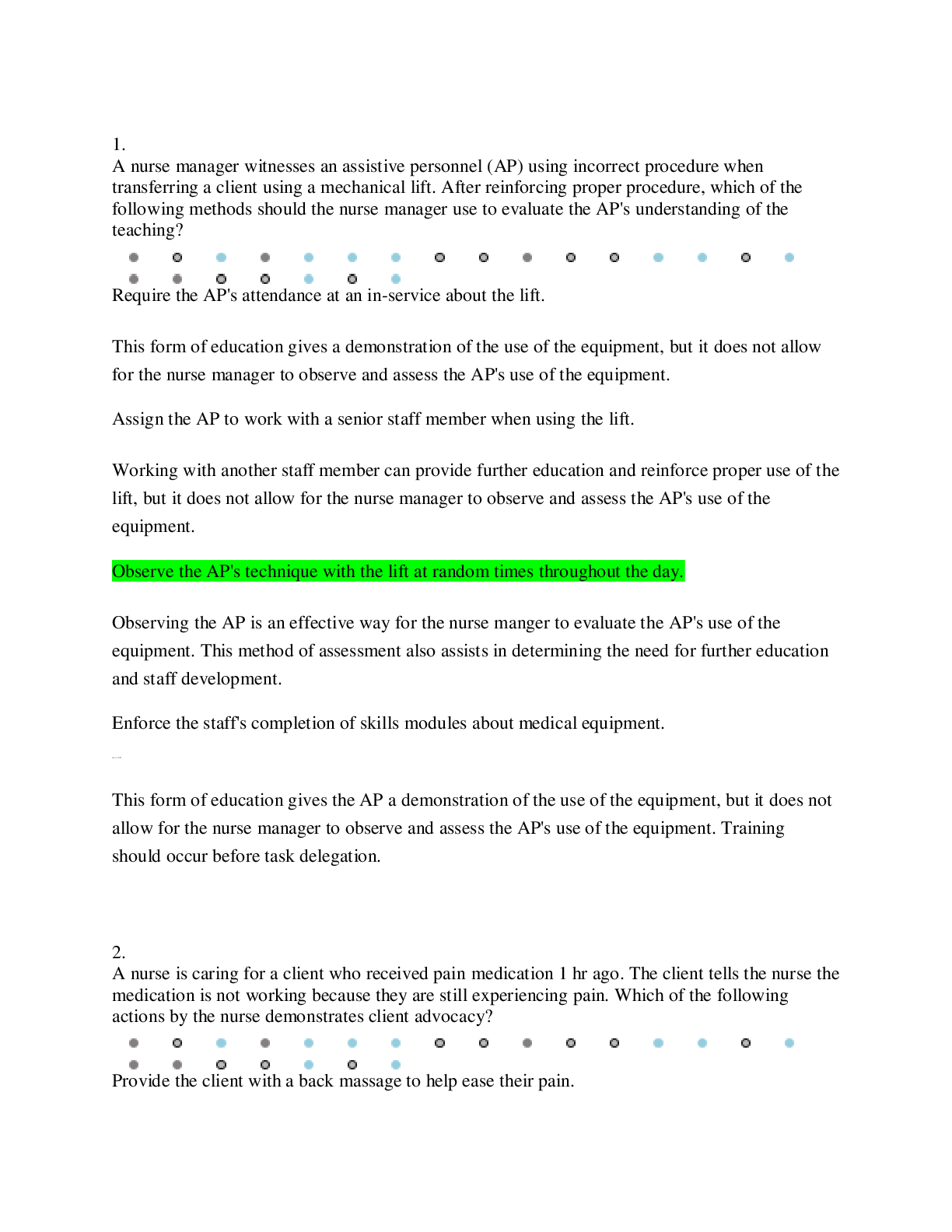
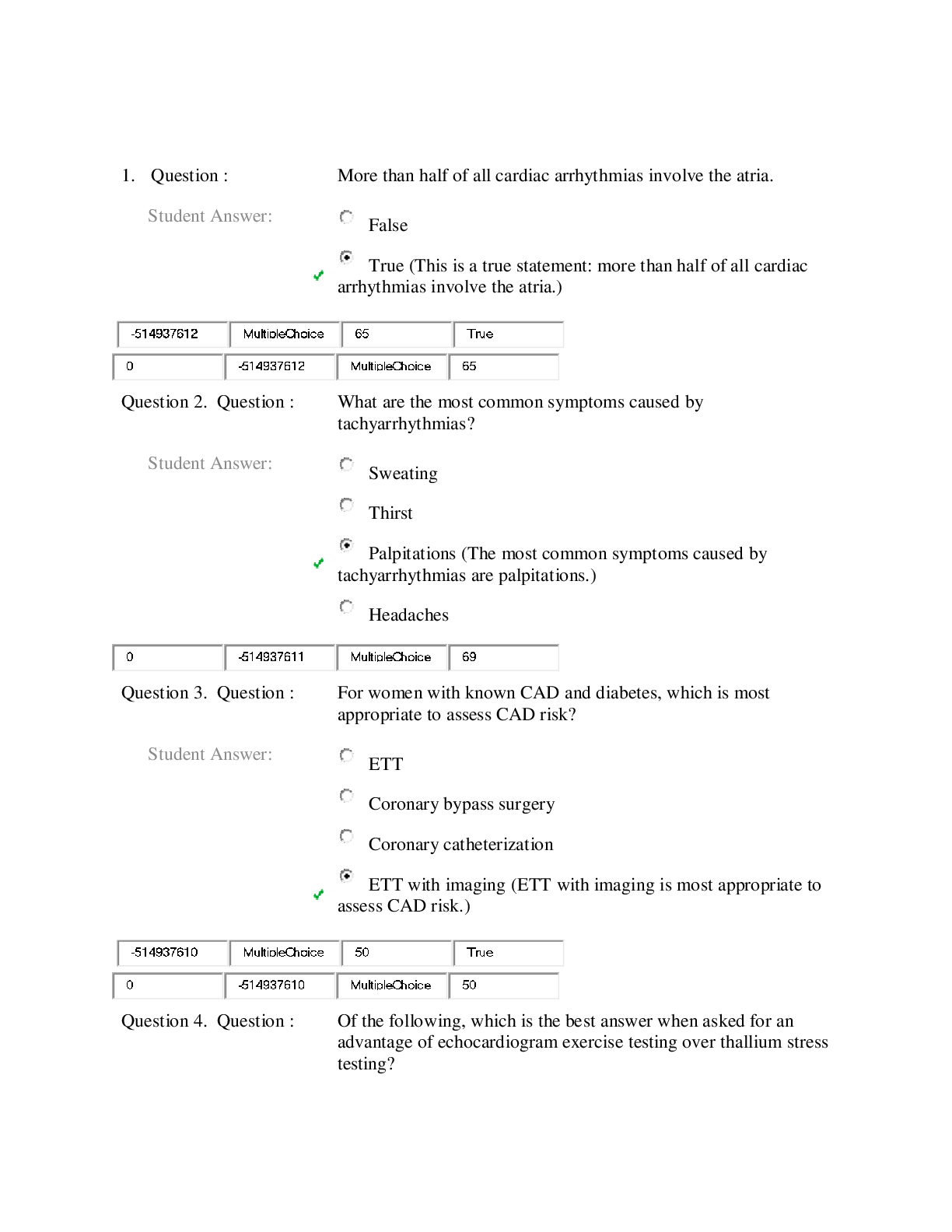
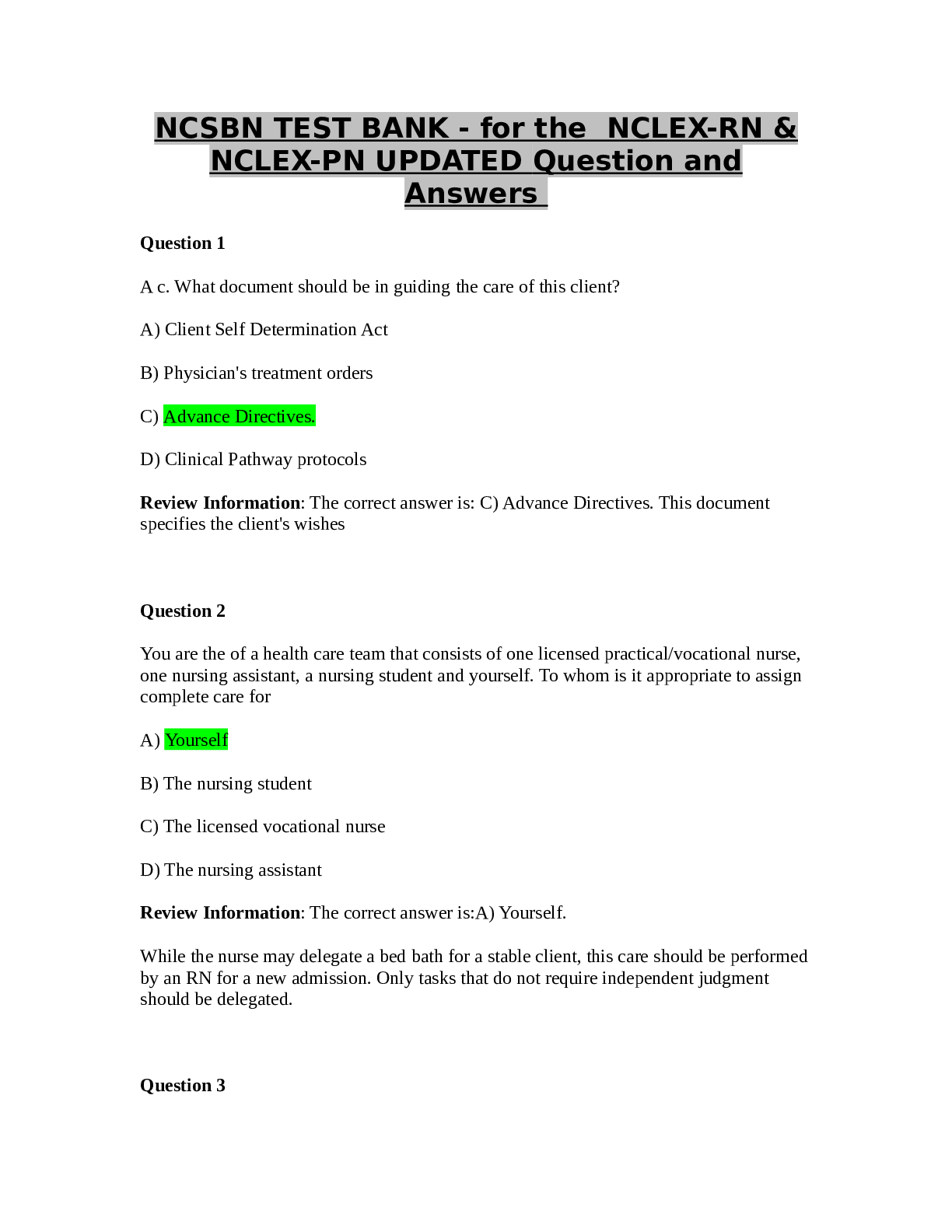
CMIT 321 My week 5 quiz questions with the correct answers Quiz Note: It is recommended that you save your response as you complete each question. ________________________________________ Question... 1 (5 points) Which of the following is true about the 802.11i standard? Question 1 options: It operates at both 2.4 GHZ and 5 GHZ It operates at 2.4 GHZ only It defines WPA-2 Enterprise and Personal It operates at 5 GHZ only Save Question 2 (5 points) Which of the following is a tool that will allow you decrypt traffic? Question 2 options: Aircrack-ng Packetforge-ng Airodump-ng Airdecap-ng Save Question 3 (5 points) Blue Tooth attacks include (Choose all that apply): Question 3 options: Blue Snarfing Blue Bugging Bluesmacking Blue Cracking Save Question 4 (5 points) The MAC Address of an access point is referred to as the ____. Question 4 options: ESSID BSSID OFDM SSID Save Question 5 (5 points) Which of the following tools will allow you crack WPA Passphrases and WEP keys? (Choose one) Question 5 options: Airdecap-ng Airodump-ng Aircrack-ng Packetforge-ng Save Question 6 (5 points) Which version of Wired Equivalent Privacy (WEP) uses a 104-bit key size? Question 6 options: 128 bit WEP 64 bit WEP 256 bit WEP 152 bit WEP Save Question 7 (5 points) An SSID (select all that apply): Question 7 options: Is part of the frame header Will be encrypted if WEP or WPA/WPA2 is utilized Is Case Sensitive Can be up to 32 characters Save Question 8 (5 points) Blue Tooth modes include (Choose all that apply): Question 8 options: Airplane Pairable Non-pairable Hotspot Save Question 9 (5 points) SQL Databases include (Choose all that apply): Question 9 options: MS Access Oracle My SQL Microsoft SQL Save Question 10 (5 points) Wi-Fi Chalking includes which of the following? (choose all that apply) Question 10 options: War Walking War Chalking War Driving War Flying Save Question 11 (5 points) Which of the following are part of the aircrack-ng suite? (Choose all that apply) Question 11 options: Packetforge-ng Aircrack-ng Airdecap-ng Airodump-ng Save Question 12 (5 points) This Blue tooth attack occurs because an oversized ping packet: Question 12 options: Blue Bugging Blue Cracking Bluesmacking Blue Snarfing Save Question 13 (5 points) According to the text, by 2018, what percent of enterprises will specify Wi-Fi as the default connection? Question 13 options: 60% 40% 75% 25% Save Question 14 (5 points) An SSID is NOT (Choose one )? Question 14 options: Case Sensitive up to 32 characters encrypted if WEP or WPA/WPA2 is utilized part of the frame header Save Question 15 (5 points) This Blue tooth attack tries to get sensitive data: Question 15 options: Blue Bugging Blue Snarfing Bluesmacking Blue Cracking Save Question 16 (5 points) Which of the following is a tool that will allow you to capture packets? Question 16 options: Airdecap-ng Airodump-ng Aircrack-ng Packetforge-ng Save Question 17 (5 points) Wired Equivalent Privacy (WEP) keys can be (Choose all that apply): Question 17 options: 512 bits 256 bits 104 bits 40 bits Save Question 18 (5 points) Phonesnoop is a (Choose all that apply): Question 18 options: Andriod hack Wi-Fi hack Bluetooth hack Blackberry hack Save Question 19 (5 points) Blue sniff is a Bluetooth wardriving tool that works on Windows. Question 19 options: False True Save Question 20 (5 points) Which of the following uses Orthogonal Frequency Division Multiplexing? (choose all that apply) Question 20 options: 802.11g 802.11b 802.11a 802.11n Save ________________________________________ Question 1 (5 points) This antenna is based on the principal of a satellite dish and can pick up Wi-Fi signals from 10 miles away: Question 1 options: Omni Directional Dipole Parabolic Yagi Save Question 2 (5 points) Best Wireless Security Practices include (Choose all that apply): Question 2 options: Disable SSID Broadcast Use WEP Change the Default SSID Change the Router Access Password Save Question 3 (5 points) This transmission method of digital data uses a pseudo random noise spreading code: Question 3 options: FHSS IR DSSS OFDM Save Question 4 (5 points) In this Blue tooth attack, the attacker takes control of the device: Question 4 options: Blue Bugging Blue Cracking Bluesmacking Blue Snarfing Save Question 5 (5 points) Which of the following are types of wireless attacks? (Choose all that apply) Question 5 options: ARP Poisoning MAC Spoofing Attacks Denial of Service Attacks Fragmentation Attacks [Show More]
Last updated: 1 year ago
Preview 1 out of 8 pages
Instant download
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jan 01, 2021
Number of pages
8
Written in
Additional information
This document has been written for:
Uploaded
Jan 01, 2021
Downloads
0
Views
34



.png)