Computer Science > QUESTIONS & ANSWERS > CyberRookie CSX Fundamentals – Terms with Complete Elaboration (All)
CyberRookie CSX Fundamentals – Terms with Complete Elaboration
Document Content and Description Below
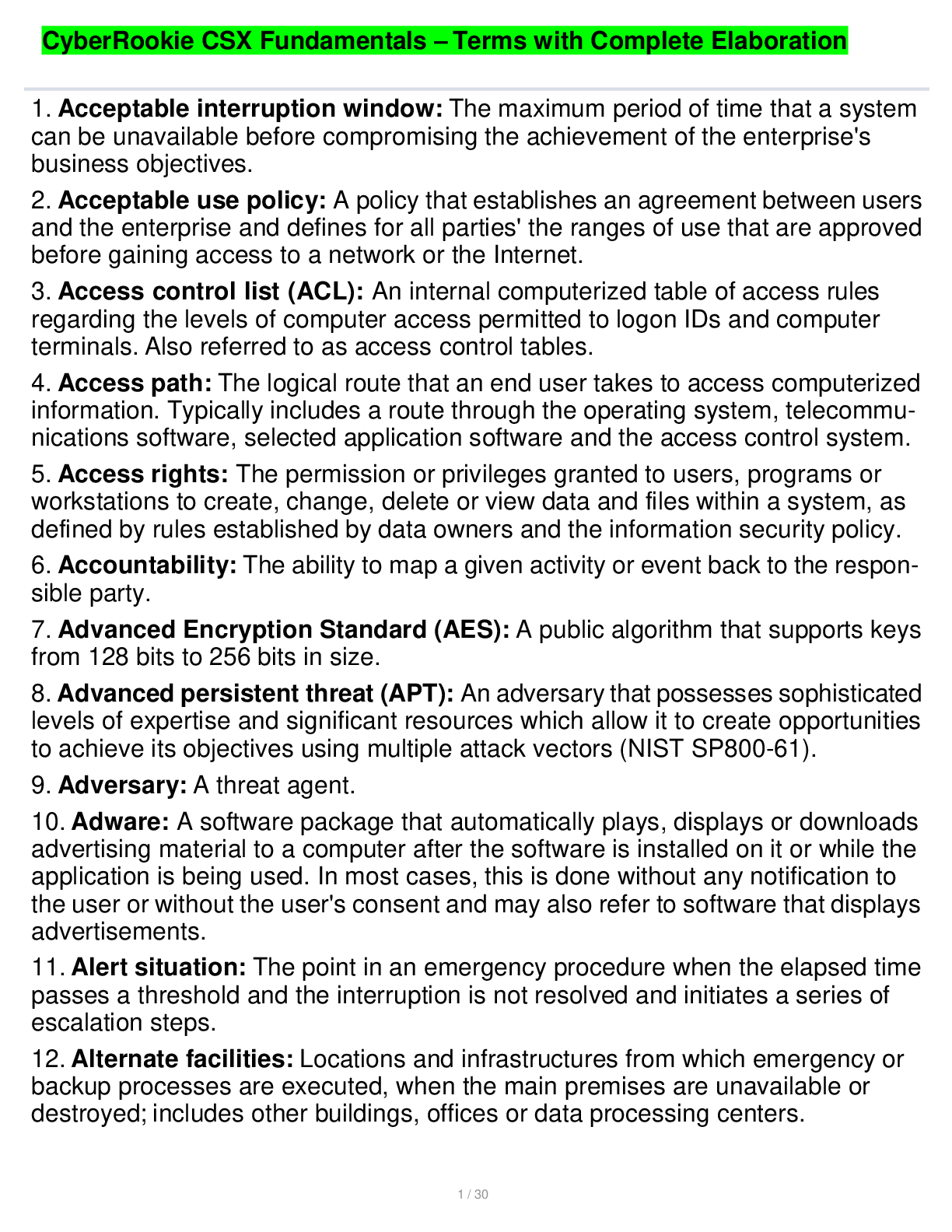
CyberRookie CSX Fundamentals – Terms with Complete Elaboration 1 / 30 1. Acceptable interruption window: The maximum period of time that a system can be unavailable before compromising the achiev... ement of the enterprise's business objectives. 2. Acceptable use policy: A policy that establishes an agreement between users and the enterprise and defines for all parties' the ranges of use that are approved before gaining access to a network or the Internet. 3. Access control list (ACL): An internal computerized table of access rules regarding the levels of computer access permitted to logon IDs and computer terminals. Also referred to as access control tables. 4. Access path: The logical route that an end user takes to access computerized information. Typically includes a route through the operating system, telecommunications software, selected application software and the access control system. 5. Access rights: The permission or privileges granted to users, programs or workstations to create, change, delete or view data and files within a system, as defined by rules established by data owners and the information security policy. 6. Accountability: The ability to map a given activity or event back to the responsible party. 7. Advanced Encryption Standard (AES): A public algorithm that supports keys from 128 bits to 256 bits in size. 8. Advanced persistent threat (APT): An adversary that possesses sophisticated levels of expertise and significant resources which allow it to create opportunities to achieve its objectives using multiple attack vectors (NIST SP800-61). 9. Adversary: A threat agent. 10. Adware: A software package that automatically plays, displays or downloads advertising material to a computer after the software is installed on it or while the application is being used. In most cases, this is done without any notification to the user or without the user's consent and may also refer to software that displays advertisements. 11. Alert situation: The point in an emergency procedure when the elapsed time passes a threshold and the interruption is not resolved and initiates a series of escalation steps. 12. Alternate facilities: Locations and infrastructures from which emergency or backup processes are executed, when the main premises are unavailable or destroyed; includes other buildings, offices or data processing centers. [Show More]
Last updated: 1 year ago
Preview 1 out of 30 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$7.00
Document information
Connected school, study & course
About the document
Uploaded On
Nov 01, 2022
Number of pages
30
Written in
Additional information
This document has been written for:
Uploaded
Nov 01, 2022
Downloads
0
Views
98


.png)
.png)