*NURSING > QUESTIONS & ANSWERS > AHIMA RHIA Exam Prep (7th Edition) | 158 Questions with 100% Correct Answers | 46 Pages (All)
AHIMA RHIA Exam Prep (7th Edition) | 158 Questions with 100% Correct Answers | 46 Pages
Document Content and Description Below
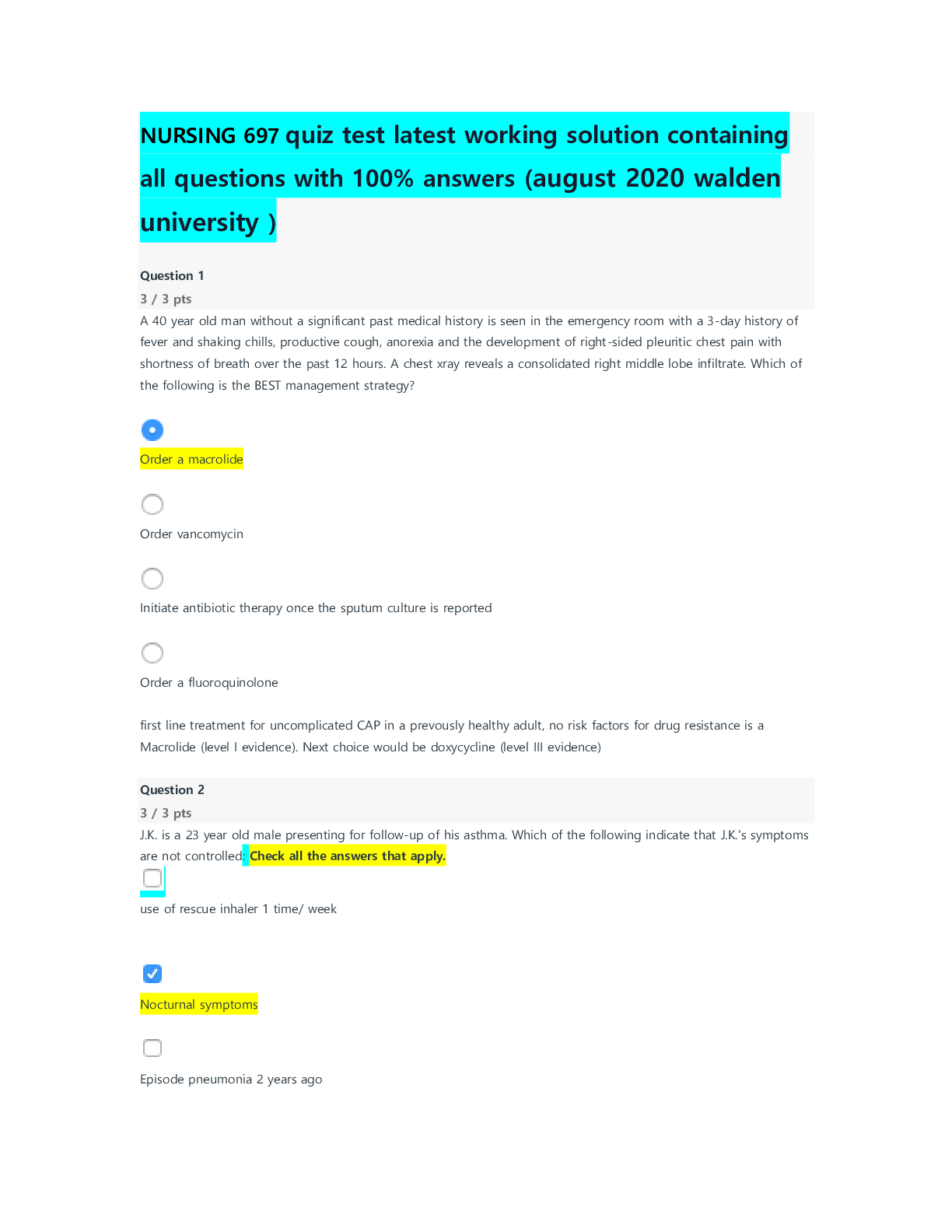
A patient requests copies of her medical records in an electronic format. The hospital maintains a portion of the designated record set in a paper format and a portion of the designated record set i... n an electronic format. How should the hospital respond? a. Provide the records in paper format only b. Scan the paper documents so that all records can be sent electronically c. Provide the patient with both paper and electronic copies of the record d. Inform the patient that PHI cannot be sent electronically Correct Answer: c. Provide the patient with both paper and electronic copies of the record The HIPAA Privacy Rule states that the covered entity must provide individuals with their information in the form that is requested by the individuals, if it is readily producible in the requested format. The covered entity can certainly decide, along with the individual, the easiest and least expensive way to provide the copies they request. Per the request of an individual, a covered entity must provide an electronic copy of any and all health information that the covered entity maintains electronically in a designated record set. If a covered entity does not maintain the entire designated record set electronically, there is not a requirement that the covered entity scan paper documents so the documents can be delivered electronically (Thomason 2013, 102). For an EHR to provide robust clinical decision support, what critical element must be present? a. Structured data b. Internet connection c. Physician portal d. Standard vocabulary Correct Answer: If an EHR is to provide clinical decision support it requires two things: structured data and a clinical data repository (Sandefer 2016a, 364). Which of the following is considered a two-factor authentication system? a. User ID and password b. User ID and voice scan c. Password and swipe card d. Password and PIN Correct Answer: c. Password and swipe card The three methods of two-factor authentication are something you know, such as a password or PIN; something you have, such as an ATM card, token, or swipe/smart card; and something you are, such as a biometric fingerprint, voice scan, iris, or retinal scan (Sayles and Trawick 2014, 219). Under RBRVS, which elements are used to calculate a Medicare payment? [Show More]
Last updated: 1 year ago
Preview 1 out of 39 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$15.00
Document information
Connected school, study & course
About the document
Uploaded On
Nov 03, 2022
Number of pages
39
Written in
Additional information
This document has been written for:
Uploaded
Nov 03, 2022
Downloads
0
Views
139












.png)