Health Care > EXAM > WGU C838 MANAGING CLOUD SECURITY FINAL EXAM OA 100 QUESTIONS AND VERIFIED ANSWERS 2024. (All)
WGU C838 MANAGING CLOUD SECURITY FINAL EXAM OA 100 QUESTIONS AND VERIFIED ANSWERS 2024.
Document Content and Description Below
WGU C838 MANAGING CLOUD SECURITY FINAL EXAM OA 100 QUESTIONS AND VERIFIED ANSWERS 2024. 1) You are the security subject matter expert (SME) for an organization considering a transition from t... he legacy environment into a hosted cloud provider 's data center. One of the challenges you 're facing is whether the cloud provider will be able to comply with the existing legislative and contractual frameworks your organization is required to follow. This is a issue. a. Resiliency b. Privacy c. Performance d. Regulatory - ANSWER- D 2. You are the security subject matter expert (SME) for an organization considering a transition from the legacy environ ment into a hosted cloud provider 's data center. One of the challenges you 're facing is whether the cloud provider will be able to allow your organization to substantiate and determine with some assurance that all of the contract terms are being met. This is a(n) issue. a. Re ulatory b. Privacy c. Resiliency d. Auditability - ANSWER- D 3. Encryption is an essential tool for affording security to cloud-based operations. While it is possible to encrypt every system, piece of data, and transaction that takes place on the cloud, why might that not be the optimum choice for an organization? a. K ey length variances don 't provide any actual additional security. b. It would cause additional processing overhead and time delay. c. It might result in vendor lockout. d. The data subjects might be upset by this. - ANSWER- B 4. Encryption is an essential tool for affording security to cloud-based operations. While it is possible to encrypt every system, piece of data, and transaction tha takes place on the cloud, why might that not be the optimum choice for an organization? a. It could increase the possibility of physical theft. b. Encryption won 't work throughout the environment. c. The protection might be disproportionate to the value of the asset(s). d. Users will be able to see everything within the organization. - ANSWER- C 5. Which of the following is not an element of the identification component of identity and access management (IAM)? a. Provisioning b. Management c. Discretion d. Deprovisioning - ANSWER- C 6. Which of the following entities is most likely to play a vital role in the identity provisioning aspect of a user 's experience in an organization? a. The accounting department b. The human resources (HR) office c. The maintenance team d. The purchasing office - ANSWER- B 7. Why is the deprovisioning element of the identification component of identity and access management (IAM) so important? a. Extra accounts cost so much extra money. b. Open but unassigned accounts are vulnerabilities. c. User tracking is essential to performance. d. Encryption has to be maintained. - ANSWER- B b. To determine whether the user is still with the organization c. To determine whether the data set is still applicable to the user 's role d. To determine whether the user is still performing well - ANSWER- D 9. Who should be involved in review and maintenance of user accounts/access? a. The user 's manager b. The security manager c. The accounting department d. The incident response team - ANSWER- A 10. Which of the following protocols is most applicable to the identification process aspect of identity and access management (IAM)? a. Secure Sockets Layer (SSL) b. Internet Protocol security (IPsec) c. Lightweight Directory Access Protocol (LDAP) d. Amorphous ancillary data transmission (AADT) - ANSWER- C 11. Privileged user (administrators, managers, and so forth) accounts need to be reviewed more closely than basic user accounts. Why is this? a. Privileged users have more encryption keys. b. Regular users are more trustworthy. c. There are extra controls on privileged user accounts. d. Privileged users can cause more damage to the organization. - ANSWER- D d. Pat-down checks of privileged users to deter against physical theft - ANSWER- D 13. If personal financial account reviews are performed as an additional review control for privileged users, which of the following characteristics is least likely to be a useful indicator for review purposes? a. Too much money in the account b. Too little money in the account c. The bank branch being used by the privileged user [Show More]
Last updated: 4 months ago
Preview 1 out of 39 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jan 31, 2024
Number of pages
39
Written in
Additional information
This document has been written for:
Uploaded
Jan 31, 2024
Downloads
0
Views
36



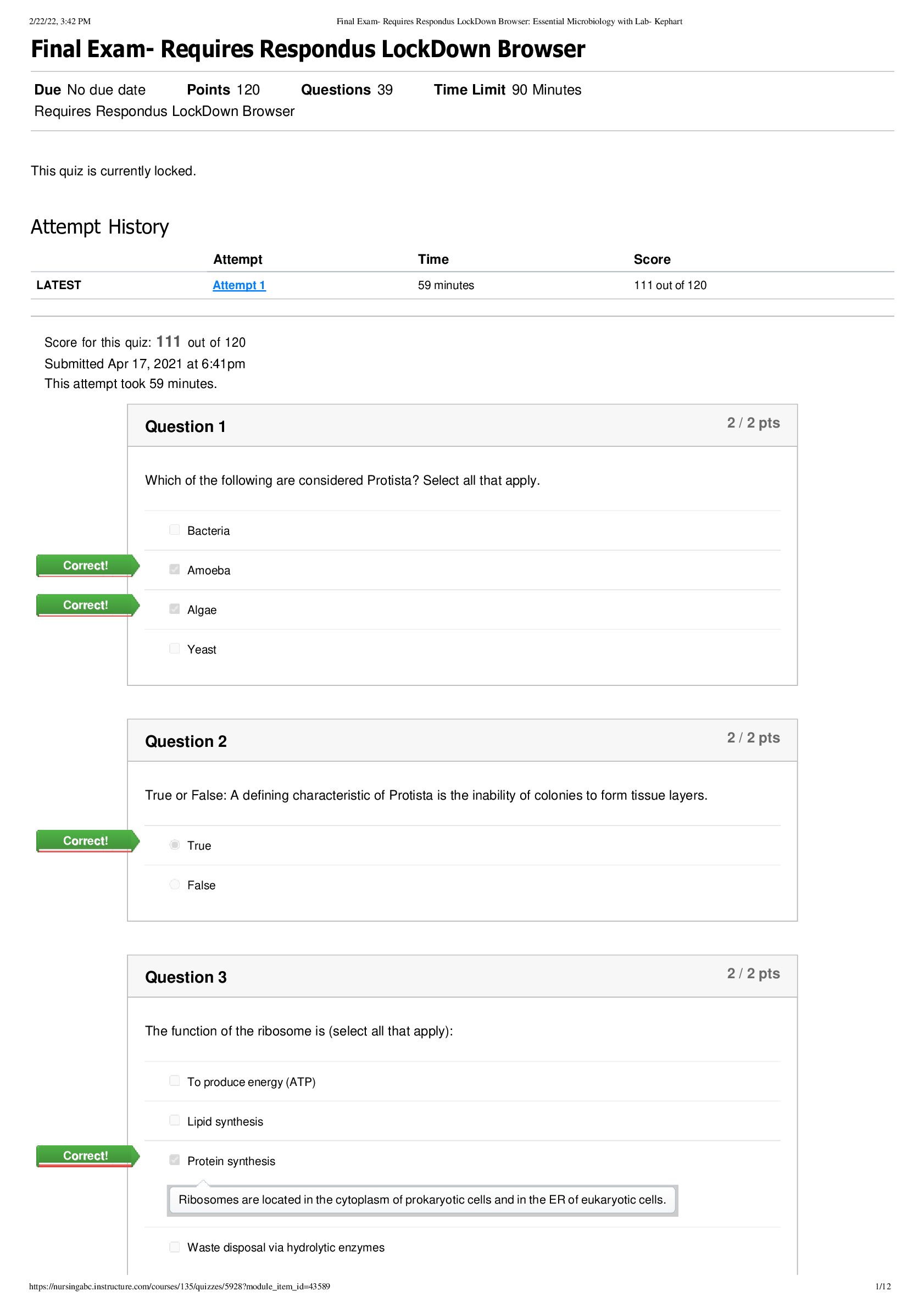











 _ Dermatology Prescription (100 Questions and Answers) – South University Savannah.png)