Information Technology > EXAM > PHGO C724 PRE-ASSESSMENT - INFORMATION SYSTEMS MANAGEMENT PHGO (GRADED A+) (All)
PHGO C724 PRE-ASSESSMENT - INFORMATION SYSTEMS MANAGEMENT PHGO (GRADED A+)
Document Content and Description Below
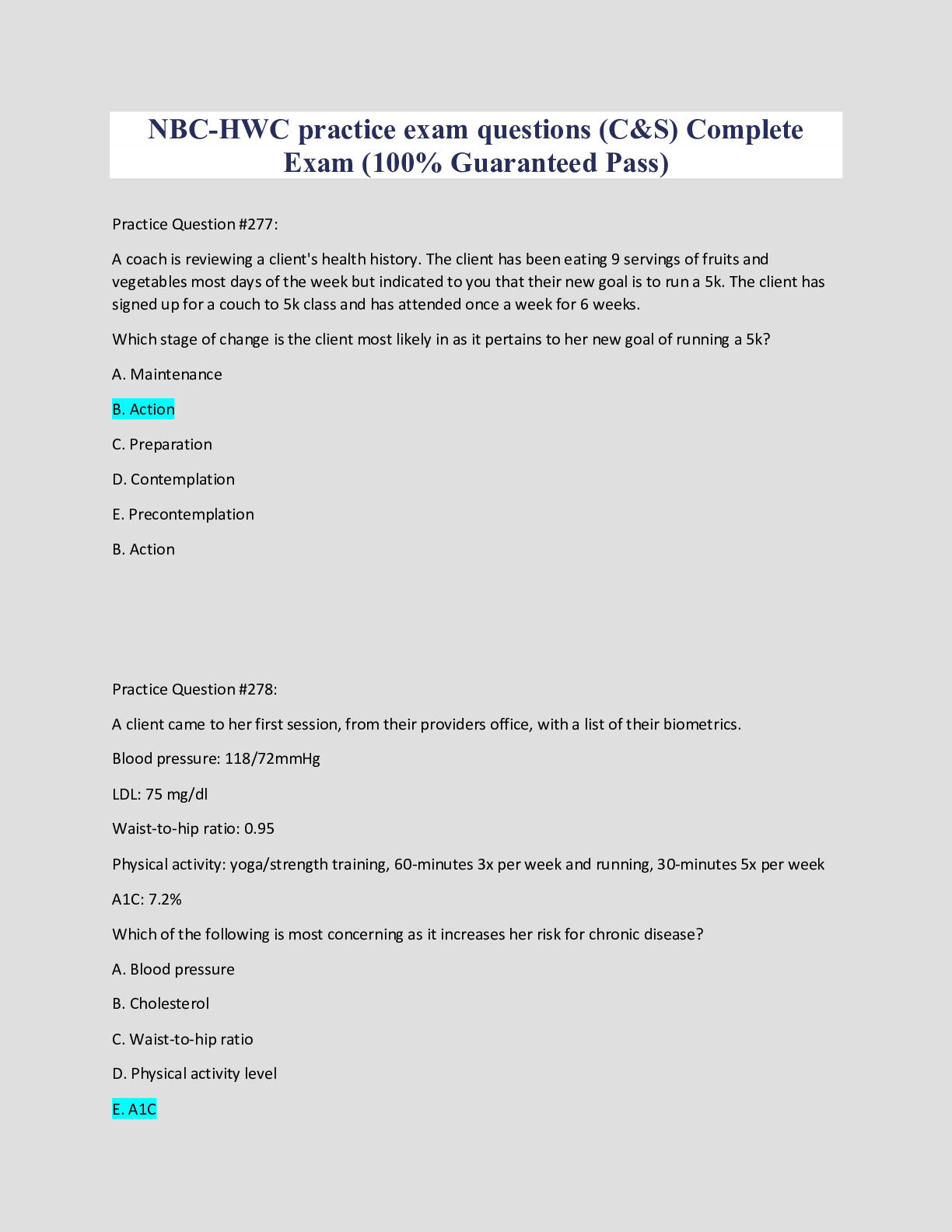
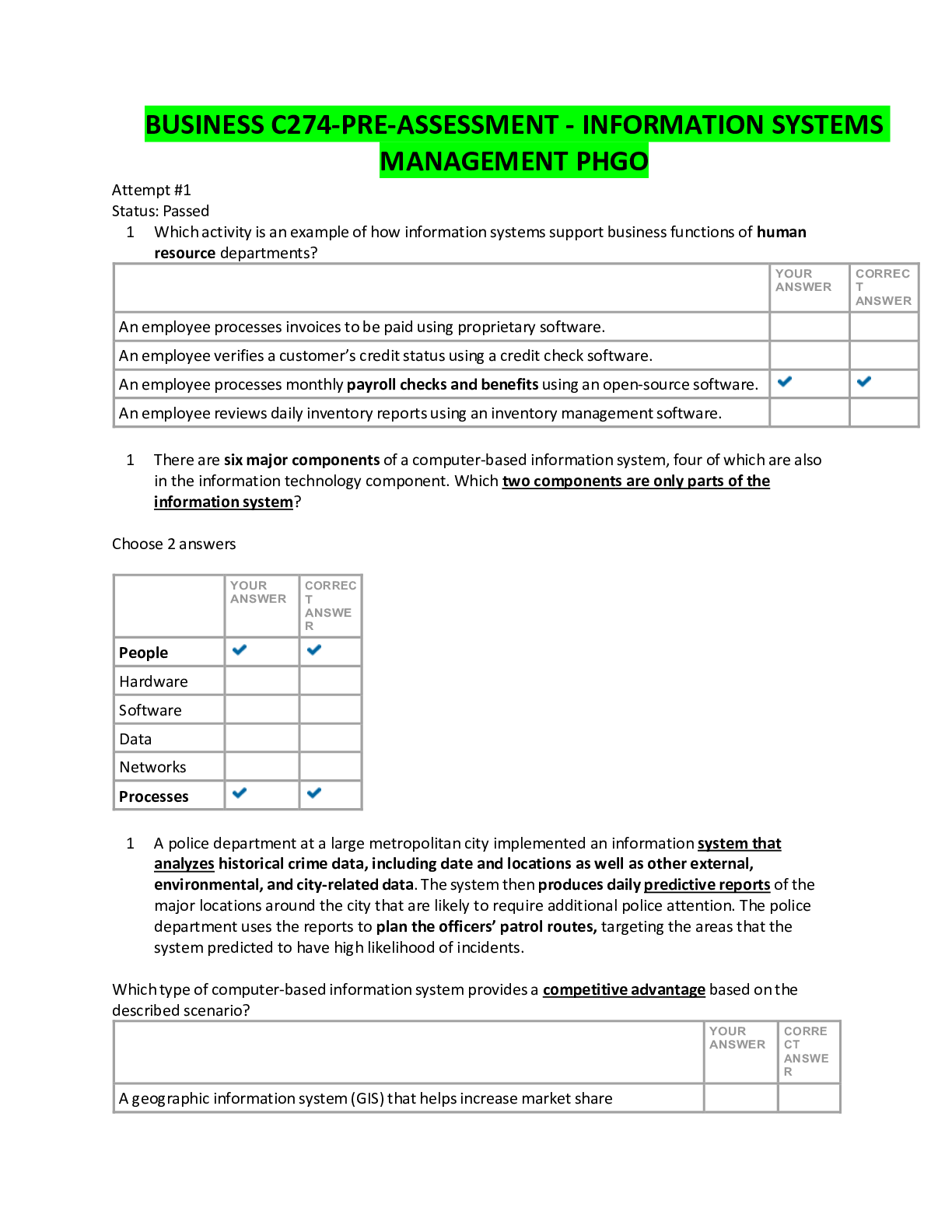
PRE-ASSESSMENT - INFORMATION SYSTEMS MANAGEMENT PHGO Attempt #1 Status: Passed 1. Which activity is an example of how information systems support business functions of human resource departmen... ts? An employee processes invoices to be paid using proprietary software. An employee verifies a customer’s credit status using a credit check software. An employee processes monthly payroll checks and benefits using an open-source software. An employee reviews daily inventory reports using an inventory management software. 2. There are six major components of a computer-based information system, four of which are also in the information technology component. Which two components are only parts of the information system? People Hardware Software Data Networks Processes 3. A police department at a large metropolitan city implemented an information system that analyzes historical crime data, including date and locations as well as other external, environmental, and city-related data. The system then produces daily predictive reports of the major locations around the city that are likely to require additional police attention. The police department uses the reports to plan the officers’ patrol routes, targeting the areas that the system predicted to have high likelihood of incidents. 4. Which type of computer-based information system provides a competitive advantage based on the described scenario? A geographic information system (GIS) that helps increase market share A decision support system (DSS) that improves decision-making A transaction processing system (TPS) that promotes product differentiation A management information system (MIS) that enhances the customer experience 5. A police department at a large metropolitan city implemented an information system that integrates historical crime data, including date and locations to other external, environmental, and city-related data. The system then produces daily predictive reports of the major locations around the city that are likely to require additional police attention. The police department uses the reports to plan the officers’ patrol routes, targeting the areas that the system predicted to have high likelihood of incidents. Which two strategies does the information system at the police department aim to accomplish? Improving decision-making Cost saving Product differentiation Customer satisfaction Operational efficiency 6. Which business function is primarily the responsibility of production and operations information systems? Accounts payable Quality control Recruiting and training Product pricing 7. A small company that is growing quickly into a medium-sized company is facing the challenge of consolidating and storing information received from multiple sources from the ground up in order to ensure that operations run efficiently. The company needs to hire an expert who will, in addition to the above, maintain security and apply upgrades as needed. Which IT professional does the company need to hire in order to address this challenge? Chief technology officer Database administrator Computer programmer Web developer 8. A university is looking for ways to customize its courses to the unique needs of its students by creating various levels of hybrid online courses, such as 80% online for one student, whereas only 30% online for another. Which IT management challenge is addressed in this scenario? Achieve operational excellence Develop new products and services Develop strong relationships with suppliers Improve decision-making 9. A ride-sharing cab company is looking for ways to generate more business by attracting more customers, both on the supply (driver) and demand (passenger) side, via a strategy of tracking their monthly miles and offering “frequent flier” bonuses, just like airline companies have done. Which IT management challenge is addressed in this scenario? Attain operational efficiency Improve decision making Promote competitive advantage Develop strong relationships with suppliers 10. An automobile manufacturer is considering equipping the engines of its new models with the capability of detecting early symptoms of an imminent mechanical or electric failure, automatically transmitting that warning to the dealership from which the customer purchased the car, and the dealership automatically contacting the customer to schedule a repair appointment. It is facing the challenge of whether all this is technically feasible and operationally viable. Who needs to address this challenge of value creation through technology use? Database administrator Chief information officer Chief technology officer Web administrator 11. A car dealership has been receiving complaints from its customers about its inflexible repair system in which customers who drop off their cars the previous evening are not properly placed in the queue and tend to be placed behind those who drop off their cars the morning of the scheduled repair. It needs technical staff members who understand the scheduling/drop-off operation so it can determine and articulate precise customer needs to the programmers who would then build the code behind the system. What type of challenge is this? Security Coding Project risk User requirements 12. An international company is facing the challenge of its software development team working on a specific application spread across the globe in 16 countries in 12 different time zones. Flying them to the same location once a week or even once a month for coordination purposes would be prohibitively expensive. Moreover, the issues that arise tend to be urgent and in need of almost immediate resolution in communication with team members in other countries. Which communication style is necessary to resolve the issues in the given scenario? Multichronous Synchronous Dyschronous Asynchronous 13. What business strategy relies heavily on efficient and secure software implementations? Vendor selection IS staff training High-quality products Web sales 14. What business function benefits from both wireless networks and cellular technologies? Corporate hiring standards Consideration of product retirement Product sales support Evaluating technology trends 15. In 1965, computers had .092 MIPS, and today’s computer have about 238,000 MIPS. What business practices have taken advantage of this massive increase in computer speed? Internal auditing schedule Network management systems Executive management hiring Database management systems 16. A marketing manager uses a desktop publishing software to create advertising brochures that will be mailed to potential customers. To which major software category does the desktop publishing software in this scenario belong? System software Application software Utility software Simulation software 17. A company needs to allow multiple computers to have access to a shared printer. Which type of computer is required to manage the print requests to a shared printer? A laptop computer A client computer A server computer A supercomputer 17. A large online retail store needs a computer system that can quickly process sales orders, inventory, payment, and shipping. Which computer system is required to accomplish these tasks? Personal computer Mainframe computer Supercomputer Handheld computer 18. Which development methodologies respond to a need to expedite and scale software development, with concepts that are concerned with the reuse of one or many software objects? Component-based development Rapid application development Object-oriented development End-user development 19. Which approach to systems development has a limited emphasis on the planning process and uses prototypes in lieu of predetermined specifications? Traditional software development life cycle Computer-assisted software engineering Rapid application development Joint application design 20. A company has many separate departments that focus on different business aspects and uses data warehouse subsets to hold data specific to each individual department. The company started a new department and created a new subset. What is this new subset called? Primary data Data tuple Data mart Secondary data 21. An auto parts manufacturer is creating a new relational database to more accurately identify their customers and vendors. The manufacturer’s database design team decided to use “vendorID” to link a given vendor to a specific product, as illustrated in the diagram shown. What type of attribute is “vendorID”? Primary key in record “Vendor” Primary key in record “Product” Foreign key in record “Vendor” Master key in record “Product” 22. Which database type, used frequently in early style databases but much less frequently today, contained inflexible data relationships that formed a treelike structure? Hierarchical database Relational database Object-oriented database Analytical database 23. Amanda has been asked to regularly extract and process databases from many sources into a data warehouse, which will be used by several divisions within the company. Which data type should Amanda recognize is prevented by her data warehouse design? Historical External Static Variable 24. A national publisher of newspapers wants to mine its data warehouse (including inputs from social media) to identify which of its publications customers believe provides reliable reporting. Which tool is used for this initiative? Sentiment analysis Predictive analysis Text analysis Clickstream analysis 25. A marketing research firm is planning a study involving consumer preferences toward new coffee flavors. The company needs to analyze coffee data from the coffee manufacturer, as well as preference data from consumers in order to discover whether certain flavors are more or less popular among certain segments of the population. Which database technology would help the company conduct this research project? Business intelligence system utilizing data mining technology Multi-user transactional database that integrates data from various sources Data reporting tool capable of generating ad hoc managerial reports Non-relational analytical platform that can quickly process a large amount of data 26. A fast food restaurant chain is in the process of adding more restaurants in an overseas market. One of the requirements is to have a reliable and scalable database technology that allows the local restaurants, as well as the corporate office, data access regardless of the platforms and locations. Which database technology supports these business data requirements? Cloud-based database Data warehouse Online analytical processing database Data mart 27. Which aspect of data governance is used to ensure that once an online payment transaction is successfully processed, the credit card information is removed from the company servers? Data are properly recorded. Data are properly stored. Data are properly destroyed. Data are properly retrieved. 28. Which aspect of data governance is used to ensure that the customer data and payment information saved in the company server are properly encrypted? Data are properly recorded. Data are properly stored. Data are properly destroyed. Data are properly retrieved. 29. A marketing manager would like to study customer behavior and how it relates to customer’s purchase products from its online store. Specifically, she would like to know which website page the majority of customers spent the most time on, when and where they decided to abandon the shopping cart, and how long (on average) a customer takes to complete a sales transaction. Which database technology supports this study? Data mining Clickstream analysis Cloud-based database Smart Grid service 30. Which telecommunication protocol is used to connect devices in a wireless local area network (LAN)? Bluetooth Wi-Fi Ethernet Token ring 31. Which telecommunication protocol is used to retrieve email from a mail server? Post Office Protocol (POP) Transmission Control Protocol/Internet Protocol (TCP/IP) File Transfer Protocol (FTP) Point-to-Point protocol (PPP) 32. With technology trends such as the Internet of Things (IoT), Big Data, Cloud Computing, eCommerce, and mCommerce, the Internet has become a very important and useful aspect of society. To prepare for these trends and aid in technology evolution, a necessary and critical change in telecommunications was the conversion from IPv4 to IPv6. What was the primary reason to convert to IPv6? To enable the Internet to operate at a higher bandwidth To increase the number of available IP addresses To enable the support of Web 3.0 To complete the conversion from analog networking to digital networking 33. Which tactic defeats a war driver by barring access to secured wireless network? Using an appropriate security solution, such as WEP or PGP Configuring the access point to accept only specific MAC addresses Regularly resetting the router password Configuring the access point to hide the SSID 34. A food truck wants to connect with its customers using a site that enables users and businesses to use public messages to create informed commerce. Which concept describes service to consumers and businesses in closing the feedback loop? Smartphone app integration Social networking Mobile e-commerce Customer relationship management 35. Interactions between buyers and sellers are often more effective when sellers intimately understand the needs of their customers, and when customers have more information to make important decisions. Thanks to the variety of beneficial resources, information, and services made possible by the Internet, such interactions may be highly individualized, and tailored to the buyer’s purchasing capacity, and relative influence. What is another important advantage of a digital market over a traditional market, from a buyer’s perspective? Information asymmetry Less price discrimination Improved transparency Increased search costs 36. Fred is an IT engineer at a small online news agency, where 35 employees carry laptops and print to the wireless printer. Recently, the company has discovered that the many Bluetooth headsets, cordless telephones, and regular usage of the breakroom microwaves are causing long-standing intermittent micro- outages at often predictable times of the day. Which solution to this problem will avoid disruption to the work environment? Change to corded communications devices Change the wireless access points to other another frequency Install traditional network wiring Upgrade the wireless access point antenna shielding 37. Sasha is an IT engineer at a small online news agency, where 35 employees carry laptops and print to the wireless printer. Several wireless access points are installed in the ceiling at appropriate points throughout the office space, though they share the same Service Set Identifier (SSID). In fact, an employee can start a large download, and then carry her laptop from one end of the office space to the other without losing her connection. Which network topology configuration supports this scenario? Star topology Token ring topology Mesh topology Bus topology 38. Which two network devices boost Wi-Fi strength for wireless devices in areas of low signal quality? Wireless bridge Wireless access point Access point client Wireless repeater 39. Broadband has enabled data, voice, and video to be combined and transmitted over one network. What is the name of the standard that allows this convergence between voice and data networks? TCP/IP VoIP IEEE 802.11 Bluetooth 40. Although WPA has been a secure encryption protocol for wireless networks, it is being replaced by a standard that offers even stronger security as the latest Wi-Fi encryption protocol. What is the name of this new standard? WPA1 WPA+ WPA2 WiFi-1 41. The traditional systems development lifecycle (SDLC) consists of six formal phases. Which phase of the SDLC involves developing the plan for capturing data and producing the output? System analysis System design System conversion System maintenance 42. A hotel experiences relatively long checkout lines on Sundays when the majority of its customers check out. Replacing the hotel’s existing checkout system with an expensive state-of-the-art system has crossed the mind of top management, and yet, due to its relative monopoly in that region, the hotel’s customers tend to be rather loyal. The management is wondering whether the costs involved in installing a new system would be recouped by the new system in the long run. Which type of feasibility is presented in this scenario? Economic feasibility Technical feasibility Schedule feasibility Political feasibility 43. A bowling center has implemented a new expensive system in hopes of increasing its clientele. The system stores and tracks patrons’ bowling performance over time and displays for them the extent to which their performance has been improving over time. However, this new system has failed to attract more patrons. During which phase of systems development is this failure discovered? Analysis Documentation Evaluation Support 44. A large hotel chain needs to develop a system that would coordinate its airport shuttle service with its customers’ needs. This requires that their systems analysis staff interacts with both customers and shuttle drivers to identify and document the necessary requirements. In which role would a systems analyst assume to address this issue? Supporting expert Change agent Problem solver Communicator 45. Which tool is appropriate for use in the design phase of information systems development to specify the detailed logic of a business process in narrative form in a manner easily translatable into any programming language? Work Breakdown Structure Unified Modeling Language Flowchart Pseudocode 46. A company is exploring the possibility of a merger with another company and decides to create a system model of the merged companies. In which step of the model will the company create a functional flow diagram? Architectural Process Testing Enterprise 47. A corporation wishes to modify its current distribution system. The management team asks the information systems (IS) team to analyze the proposed distribution change. Upon approval of the proposed IS project, the IS team must choose the project implementation method. Which method allows the old system to operate while the new system is developed and tested? Direct implementation Parallel adoption Prototyping Indirect implementation 48. An organization is planning its yearly budgeting cycle. Management has requested the information systems team to validate current hardware and software performance. Which type of evaluation can the team use to perform this validation? System-oriented Strategic-oriented Function-oriented Object-oriented 49. A business requires large amounts of data that are processed into information and used to maintain a competitive advantage over their competitors. As the business grows, the data storage and processing capabilities are becoming extremely challenging and costly. What external technological environment can be used to help address these issues? Parallel processing RAID storage Service-oriented architecture Cloud computing 50. A company is considering an expansion into a new target market. The company’s management team develops a decision process to analyze current market strengths and to predict needs for the proposed new target market. Which benefit does the company gain by developing this target market decision process? Management travel is reduced. The company reduces debt financing. The company becomes data-centric. Management decisions are easier. 51. An online mail order company decides to create its own Customer Relationship Management (CRM) system to help management analyze customer’s purchasing patterns. To be successful at managing relationships with customers, the CRM system must have access to large amounts of customer purchasing data for analysis and report generation. Which MIS tool is also useable by the company’s CRM system? Executive support system Decision support system Group support system Infrastructure support system 52. A decades-old company has several hundred employees and a modern IT infrastructure. An IT security analyst has been hired to provide a layered defense structure and must take measures to ensure confidential information remains confidential. Which activities will help the IT security analyst accomplish this goal? Enforcing document retention and destruction policies Requiring the regular acknowledgement of an acceptable use policy Requiring the use of ID badges at building access points Requiring specific fields be updated only with appropriate data Requiring that redundancies are added to each business critical service component Mandating annual information security training for all employees 53. A company has issued smartphones to its employees with a policy that the devices may not be used off of the company’s campus. An IT analyst has been tasked with finding a way to enforce this policy. Which solution provides a fitting solution to this problem? Cell phone storage lockers near building exits Proximity authentication access control A man trap with a metal detectors Vigilant training and auditing procedures 54. Hostile or intrusive software with harmful intent can take the form of executable code and greatly damage a user’s computer. Which technology can be used to minimize the chances of this happening? Rolling code Biometrics Encryption Anti-malware 55. A regional manager has received an important financial document seemingly sent by a branch manager, but he doubts whether the report was actually sent by that manager. Which technology could be used to verify that the report was indeed sent by the branch manager? Anti hack Firewall Virtual private network Digital signature 56. A corporation needs to improve its security policies and has decided to limit physical access to corporate computers. What value will the corporation realize with this policy? Always-on hardware vulnerability Network Protection System protection Guard against malware 57. A business wished to extend the use of its virus scanning software to the business’ customers. This requires the business to allow customers enough access to the internal network so virus scanning software can be downloaded to a customer’s computer. Which two security measures will the business have to take to ensure customer access for virus scanning downloads, yet protect internal systems from possible unauthorized access? Take steps to detect any presences of malware. Ask each customer to sign a non-disclosure agreement. Reboot every router after each download has completed. Require a username and password for network access. 58. An investment banking corporation utilizes employee passwords as a data privacy measure to secure sensitive data. The IT security team has been tasked with ensuring the data is produced and modified in the way. Which data privacy goal is the IT security team tasked with accomplishing in this scenario? Integrity Availability Duplication 59. The information systems support team is asked to perform an analysis of corporate privacy measurers regarding a centralized relational database. The database is interconnected to several business groups via the internal data network that also supports connectivity to outside organizations. Which ethical risk is identified after a secondary analysis? The financial system is poorly designed and implemented. The financial system introduces unwanted liabilities. The financial system is unavailable to all users. The financial system requires additional storage space. 60. A corporation is using the encryption illustrated in the diagram below to protect business-sensitive information. What type of encryption is the corporation using? Character ordering Word substitution Exclusive bit shifting Character shifting 61. Interactive online communications, such as instant messaging, email, and video teleconferencing, have allowed managers at a large retailer to boost efficiency by enabling collaboration between geographically separate employees. However, such technologically assisted interactions have led to inappropriate conduct by employees, requiring the employer to implement processes or technological controls to reduce risk and encourage professionalism, but potentially invade employee privacy. Which technological action, if used, will represent an ethical challenge for this large retailer? Filtering Internet content Reviewing instant message logs Archiving all email Blocking access to video streaming sites 62. Widespread use of the Internet caused disruption and quick evolution within the music industry. Responses to widespread Internet usage included technological evolutions, such as uniquely identifiable digitally tagged files, and the passage of laws that penalized file sharing. Which type of e-commerce put music industry artists, publishers, and retailers at risk of losing potential revenue due to widespread use of the Internet? Business to consumer Business to business Consumer to consumer Peer to peer 63. Large established businesses often have networks of other businesses within their supply chains in order to maintain the flow of information and materials. Company A is an organization that hosts its own marketplace of suppliers in order to facilitate the pursuit of its own interests. Which network describes Company A’s example of e-commerce? Public exchange Net marketplace Private industrial Direct marketplace 64. To help facilitate business in areas without traditional infrastructure, some companies offer devices that allow businesses to accept credit cards with their tablets and cell phones. Which business model category do these companies fall in? Service provider Market creator Brokerage Community 65. Mary purchased a digital camera from an online store for her upcoming road trip. What is the e-commerce model of the online store? Business to Business (B2B) Business to Consumer (B2C) Consumer to Consumer (C2C) Business to Government (B2G) 66. Company A ordered printer toner cartridges from Company B. Company B ships the products to Company A every two months. What is the e-commerce model described in this scenario? Business to Business (B2B) Business to Consumer (B2C) Consumer to Consumer (C2C) Business to Government (B2G) 67. Although printed catalogues are still produced and mailed by specialty retailers, for most of these retailers a customer can place an order immediately at the website instead of mailing an order form. Which specific feature of e-business enables this opportunity? Customer ratings Mobile computing Micropayment Online order entry 68. Customers wish to have the capability of performing tasks anytime, anywhere, without being tethered to a desktop computer. Which term describes computer programs designed specifically for this purpose? Mobile apps Shopping cart Smart phones Search engine 69. Which two benefits can a business realize by using social media to connect to customers? Detailed marketing research Technology deployment schedules Stagnant marketing costs Targeted sales promotions 70. A candidate is applying for a job at a local company. His resume listed the most recent position as a supervisor at XYZ Corp. However, his social media profile indicated the position during the same time period as a manager at XYZ Corp. Which aspect of the job candidate’s qualification can negatively affect his hiring potential? Discriminatory comments Poor communication skills Inconsistent experience Provocative image 71. Which feature of social media websites can a job seeker use to convince prospective employers that the job seeker’s talents are real and are already valued by a number of other individuals and organizations? Profile recommendation Update-me Profile creation Talent update [Show More]
Last updated: 1 year ago
Preview 1 out of 13 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jun 24, 2021
Number of pages
13
Written in
Additional information
This document has been written for:
Uploaded
Jun 24, 2021
Downloads
0
Views
50




.png)