Computer Science > EXAM > C@CM Final Exam Answered 100% (All)
C@CM Final Exam Answered 100%
Document Content and Description Below
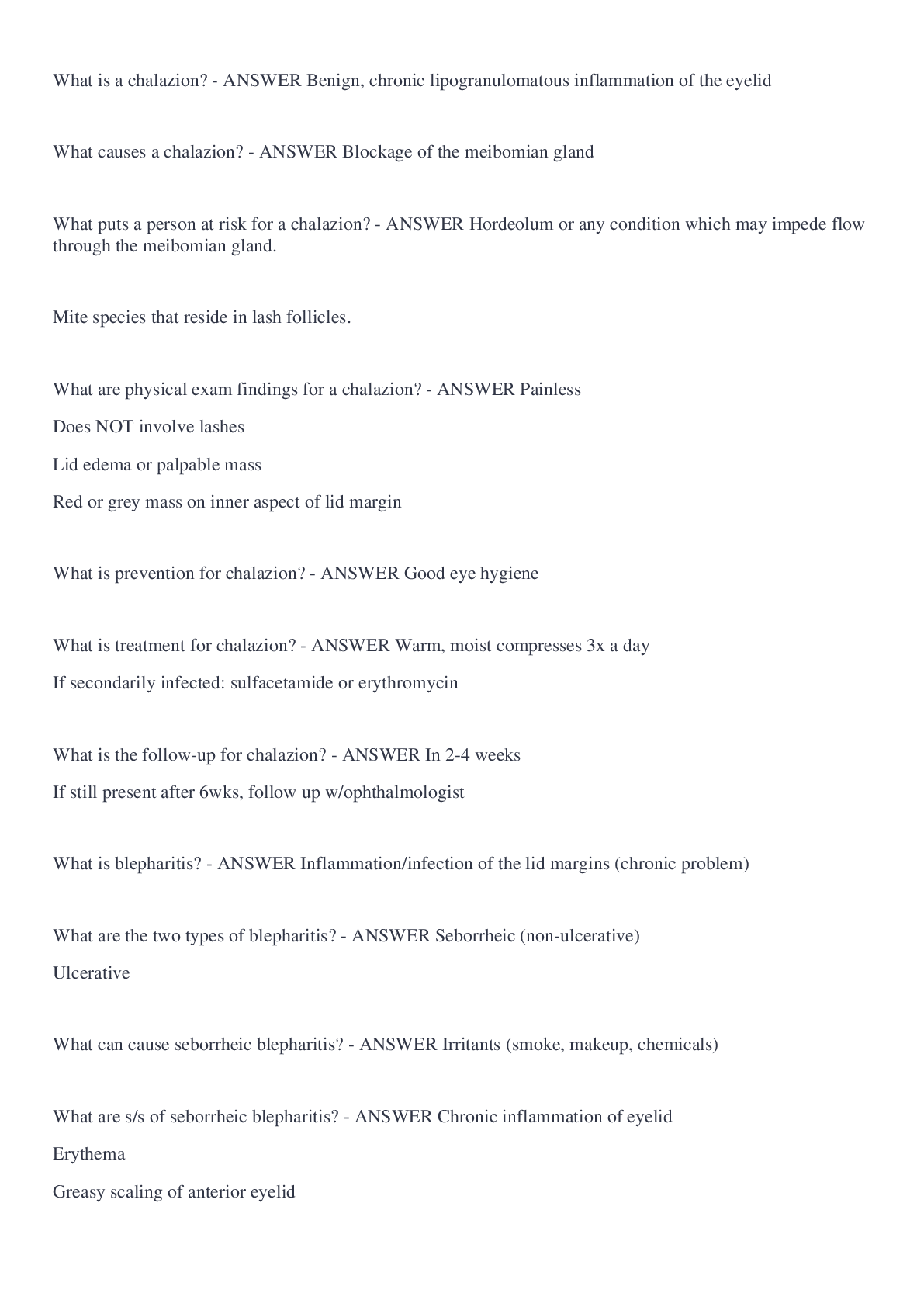
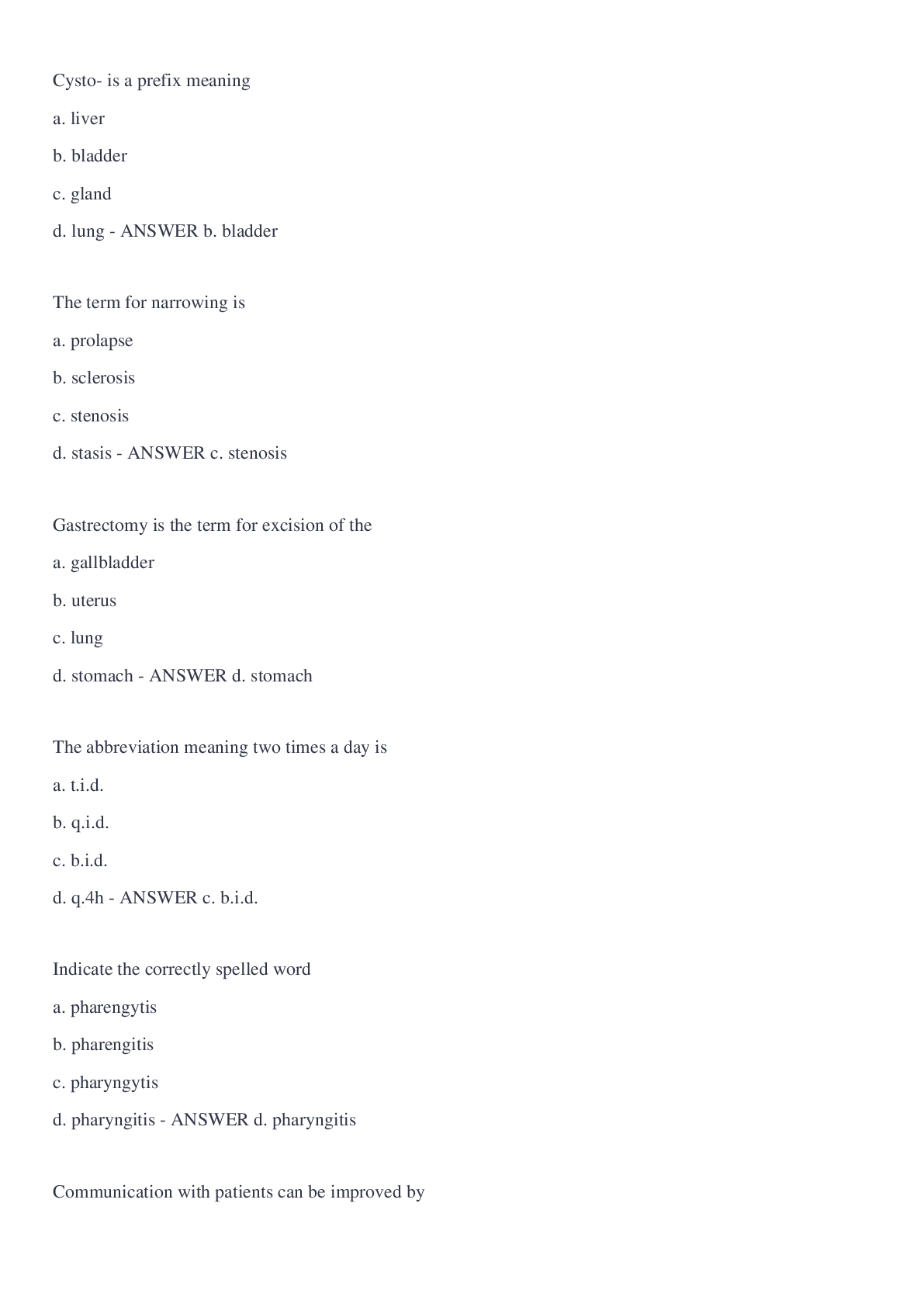
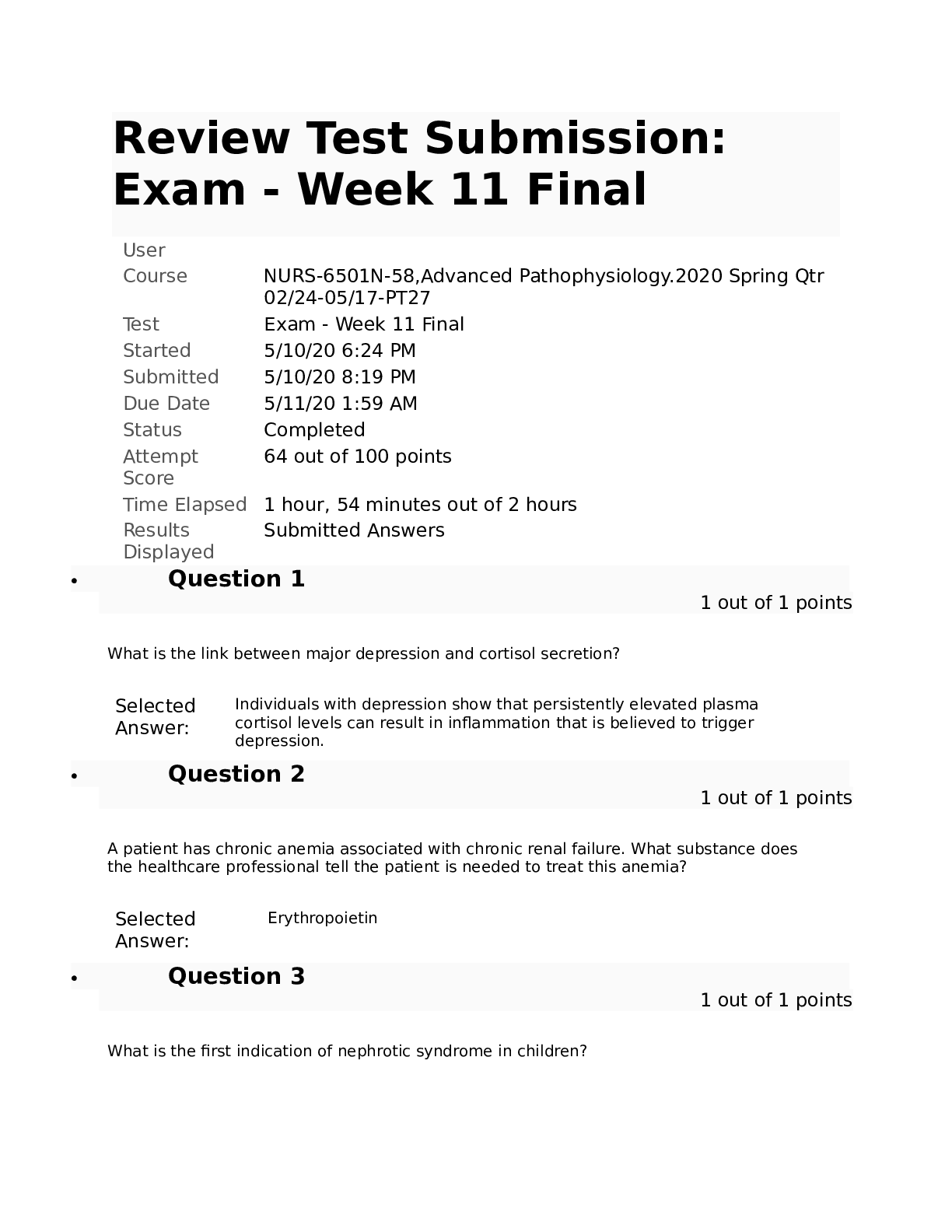
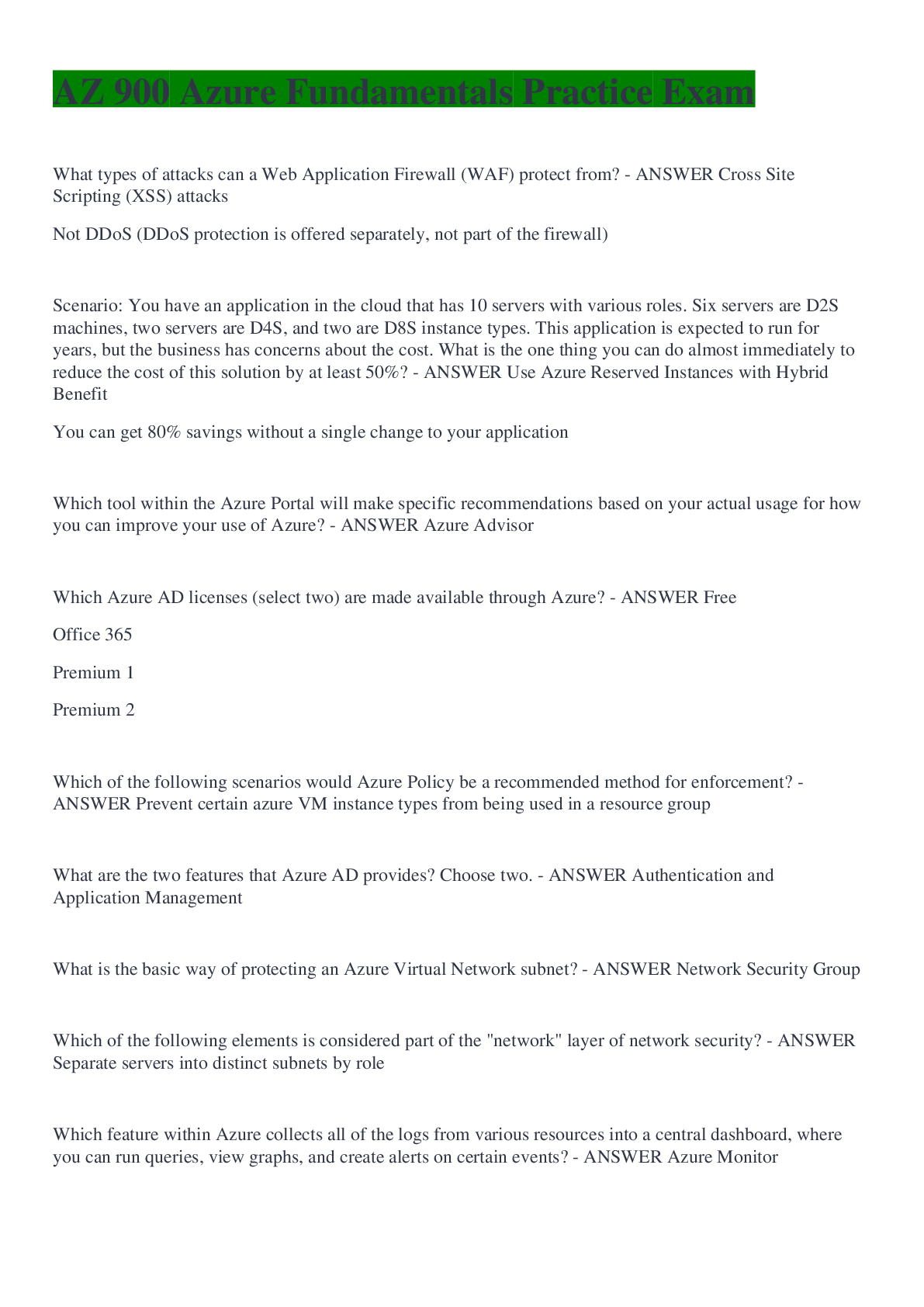
The Digital Millennium Copyright Act: - ANSWER Provides rules for online service providers that can limit their liability for copyright violations. P2P - ANSWER can allow users to exchange files di... rectly with other users; not anonymous whether uploading or downloading DMCA Takedown Notices - ANSWER if illegal activity is detected, the university is obligated to ensure that these illegal transfers of copyrighted materials do not continue. How long is your network access suspended if you exceed the bandwidth limitations the maximum amount of times? - ANSWER 45 days Web Station - ANSWER -15 min time limit -internet kiosks -used to: check emails, print files, search SIO, access Blackboard Cluster - ANSWER -no time limit -can be reserved for class; located in academic buildings (teaching clusters) -located in resident halls (learning clusters) -also have collaborative clusters Box - ANSWER a cloud storage service that allows users to access files from any device with an Internet connection SandBox - ANSWER a temporary storage location on clusters; any files saved to this location will be deleted when you log off the cluster computer Virtual Andrew - ANSWER -makes it possible for you to access a Windows cluster computer remotely from your personal computer or mobile device -you can use a variety of academic software from your own computing devices without having to install the individual software packages. PII - ANSWER personal identifiable information; includes name with social security number, credit card number, driver license number phishing - ANSWER A method used by cyber-criminals to lure you into providing sensitive information. URL may be malicious - ANSWER http:// indicator that data is being transmitted securely on a website - ANSWER https:// VPN - ANSWER a secure service that allows you to access IP-restricted Web services, such as library databases and journals. The VPN provides a convenient solution when you need to access restricted library services. (use when you are off campus) CAMEO - ANSWER CMU's library catalog — it is the place to go when you're looking for books or other materials that they university owns or licenses. course reserves - ANSWER materials your instructors provide for their particular courses that are available through the University Libraries. ProQuest - ANSWER a general database; offers information on a wide array of topics, and are good places to start your search for scholarly content University Library e-Journals A-Z - ANSWER useful if you already have a specific article in mind and want to know whether CMU has access to that journal online Google Scholar - ANSWER one of the broadest and best resources for finding scholarly articles on the Web is Google Scholar. You can use the typical Google search interface to find links to a variety of scholarly articles. One advantage of using Google Scholar over the regular Google search engine is that Google Scholar filters out non-scholarly sources. Databases - ANSWER electronic collections of information, such as periodical and journal articles, data, images or historical documents (databases A-Z vs databases by subject); most useful for retrieving internet subject guides InterLibrary Loan - ANSWER to get access to specific resources from other institutions. InterLibrary Loan is a free service for all students, faculty and staff; You can get a borrower's card at the University of Pittsburgh and the Carnegie Library of Pittsburgh EZ-Borrow - ANSWER to Borrow a book from another Pennsylvania academic library ILLiad - ANSWER Request a book, dissertation, copy of a journal article, etc. from anywhere in the world Academic Development is a program that provides: - ANSWER peer tutors, supplemental instruction and general academic counseling The Global Communication Center is meant to: - ANSWER help you to build the skills that you need to enhance the quality of your written, oral and visual communication skills Which of the following is NOT a responsibility established by the Computing Policy? A.Behave in ways that are respectful of others' property and privacy rights. B.Communicate in proper and legal ways. C.Use computing resources only for academic coursework. [Show More]
Last updated: 1 year ago
Preview 1 out of 11 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 22, 2022
Number of pages
11
Written in
Additional information
This document has been written for:
Uploaded
Nov 22, 2022
Downloads
0
Views
40