Health Care > EXAM > WGU C468 INFORMATION MANAGEMENT AND APPLICATION OF TECHNOLOGY (All)
WGU C468 INFORMATION MANAGEMENT AND APPLICATION OF TECHNOLOGY
Document Content and Description Below
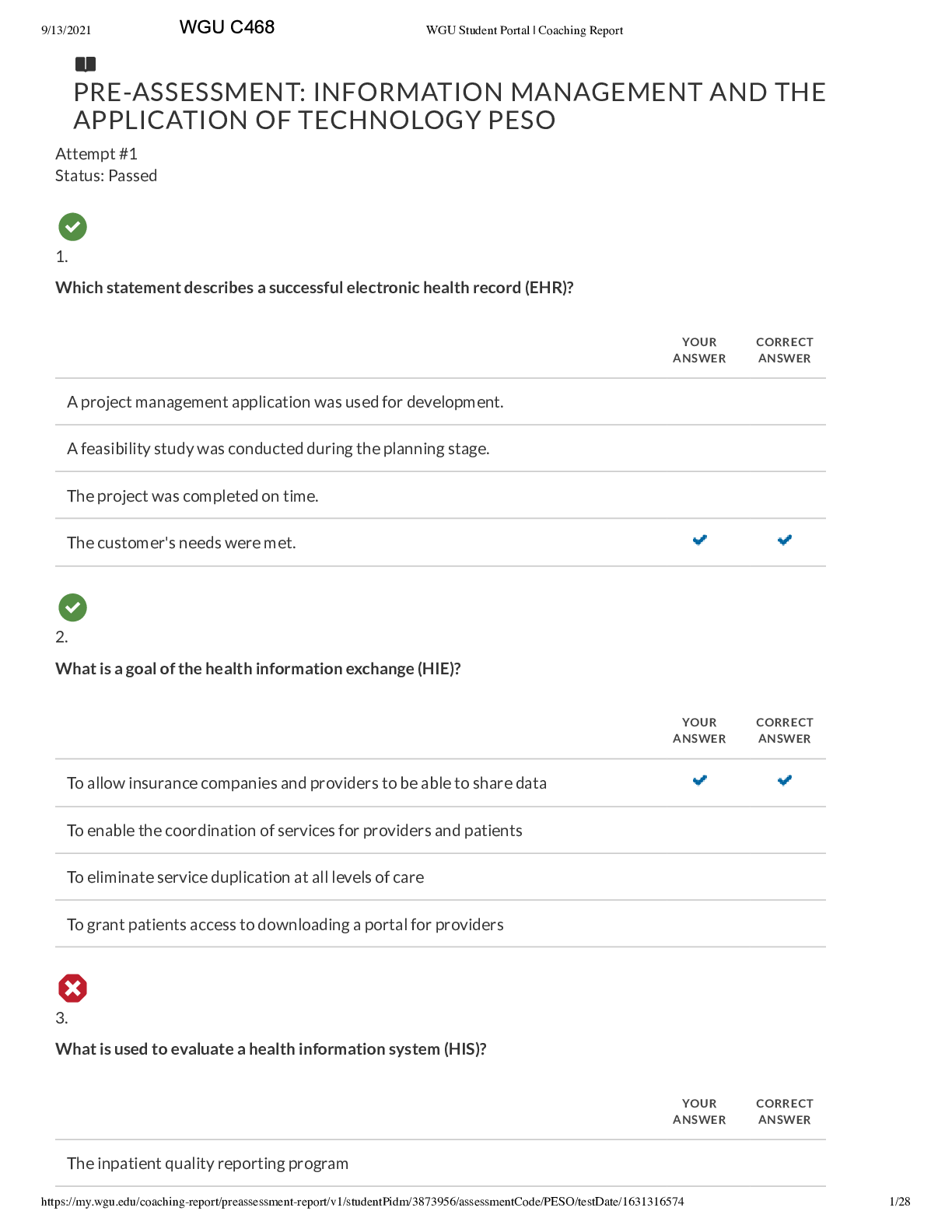
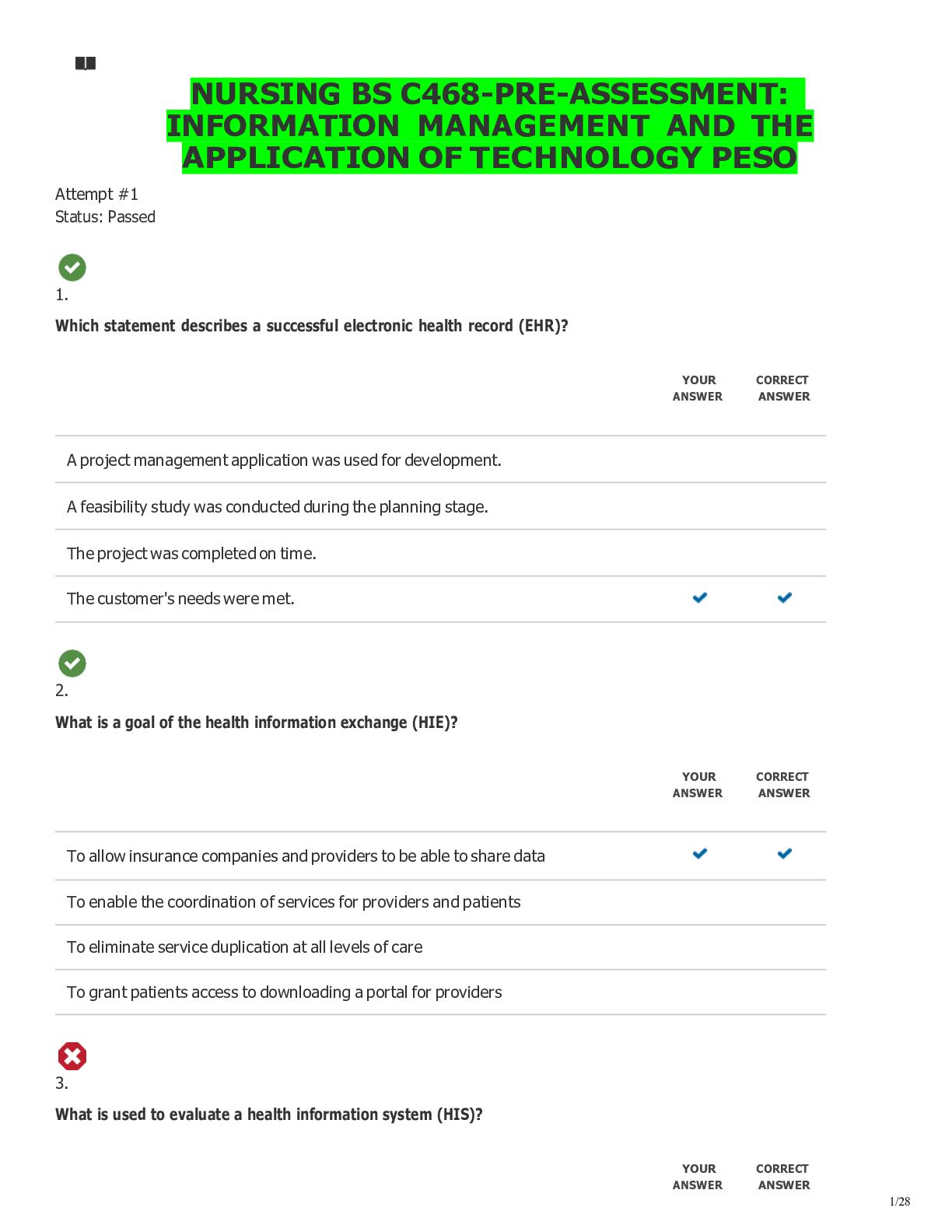
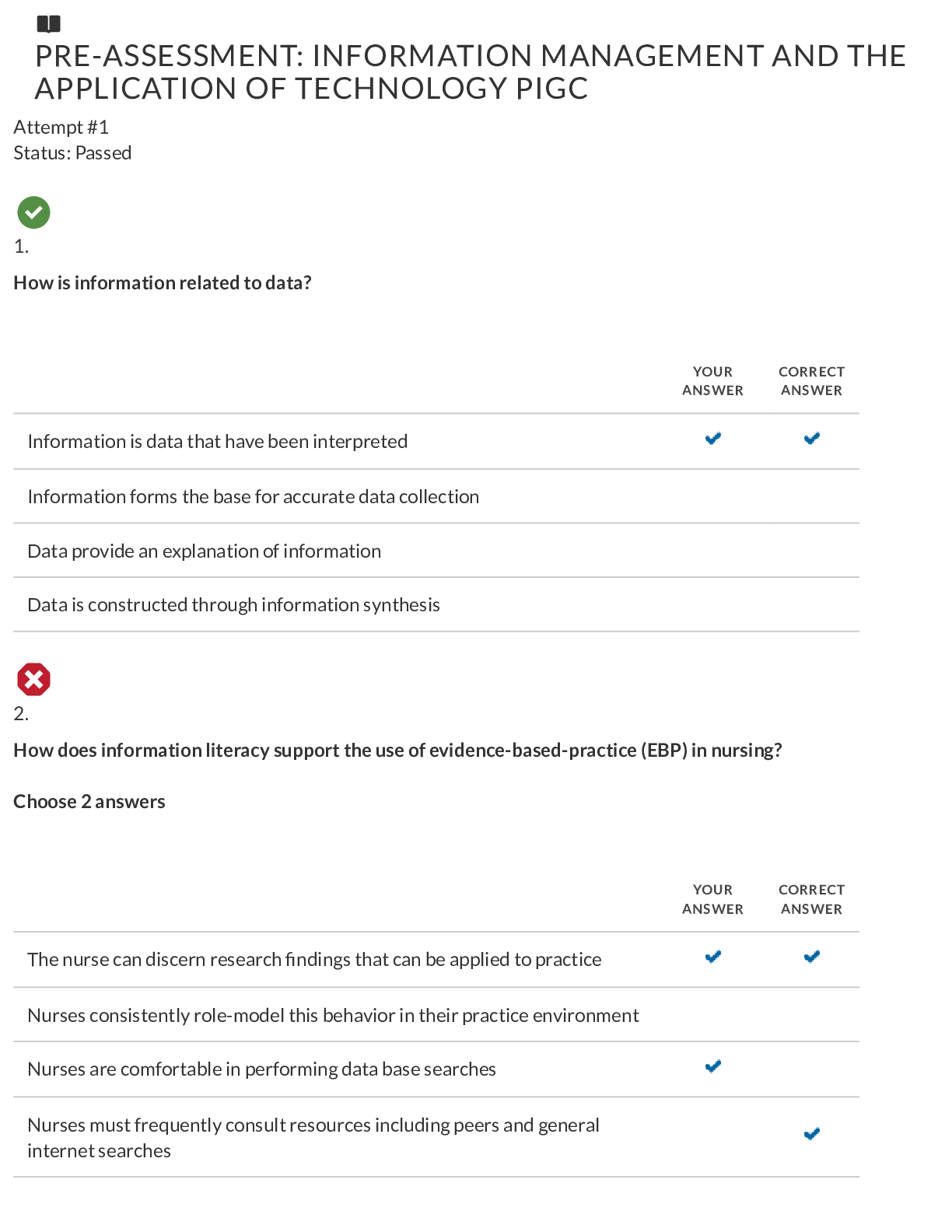
WGU C468 INFORMATION MANAGEMENT AND APPLICATION OF TECHNOLOGY System security involves protection against A) poor system design B) noncompliant users C) deliberate attacks, errors, omissions, dis... asters, and viruses D) vendor breech of support contract ANSWERS: C) deliberate attacks, errors, omissions, disasters, and viruses Which of the following is a mechanism that logs a user off the system after a specified period of inactivity on the terminal or computer? A) automatic sign-off B) remote access C) automatic access D) automatic password protection ANSWERS: A) automatic sign-off The sharing of private information in a situation in which a relationship has been established for the purpose of treatment, or delivery of services, with the understanding that this information will remain protected is _____________? A) information privacy B) privacy C) confidentiality D) information system security ANSWERS: C) confidentiality ____________ is a combination of hardware and software that forms a barrier between systems, or different parts of a single system to protect those systems from unauthorized access. A) Antivirus software B) Firewall C) Physical security D) Application security ANSWERS: B) Firewall The ability to use a health enterprise's information system from outside locations such as a physician's office is known as ___________. A) remote access B) automatic access C) system connectivity D) auto connectivity ANSWERS: A) remote access What are the driving forces behind the Health Information Exchange (HIE) movement? A) provider demands for cost containmentB) international demands C) healthcare insurance reform D) federal legislation, and demands for safer, more efficient healthcare ANSWERS: D) federal legislation, and demands for safer, more efficient healthcare How do Health Information Exchanges (HIEs) impact healthcare delivery? A) HIEs have the capacity to improve the quality of care delivered by decreasing access to records B) HIEs have limited impact at this time C) HIEs increase the efficiency and potentially the quality of the healthcare delivery system D) HIEs have not been shown to impact the safety of care delivered ANSWERS: C) HIEs increase the efficiency and potentially the quality of the healthcare delivery system Information and data privacy A) provide protection for healthcare information only B) includes the right to choose the conditions and extent to which information is shared C) are best maintained through paper backups D) only applies when a HIPAA release form is signed ANSWERS: B) includes the right to choose the conditions and extent to which information is shared The Health Information Technology for Economic and Clinical Health Act (HITECH) is known for all of the following except: A) Including a privacy rule establishing national standards for protecting health information B) Funded workforce training, and new technology research and development in HIT C) Ensured the collection of aggregate data that could be used to improve policy decisions relative to allocation of services and population health D) Provided funds and incentives to increase the adoption of EHRs by providers ANSWERS: A) Including a privacy rule establishing national standards for protecting health information The SWOT analysis is conducted in what phase of information system life cycle? A) evaluation phase B) monitoring and control phase C) implementation phase D) strategic planning phase ANSWERS: D) strategic planning phase Training documents are developed and user training occurs in which phase of the project management life cycle (PMLC)? A) evaluation phase B) design/plan phase C) implementation phase D) monitoring and control phaseANSWERS: C) implementation phase Maintenance of an information system includes all of the following except ____________. A) problem solving and debugging B) training end users C) performing file-backup procedures D) updating security protections ANSWERS: B) training end users Who determines the project implementation strategy? A) the system analyst [Show More]
Last updated: 1 year ago
Preview 1 out of 51 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jul 05, 2022
Number of pages
51
Written in
Additional information
This document has been written for:
Uploaded
Jul 05, 2022
Downloads
0
Views
67

.png)










.png)


.png)