Computer Science > QUESTIONS & ANSWERS > 2022/2023 BEST Security+ SY0-601 EXAM STUDY with Complete Solutions (All)
2022/2023 BEST Security+ SY0-601 EXAM STUDY with Complete Solutions
Document Content and Description Below
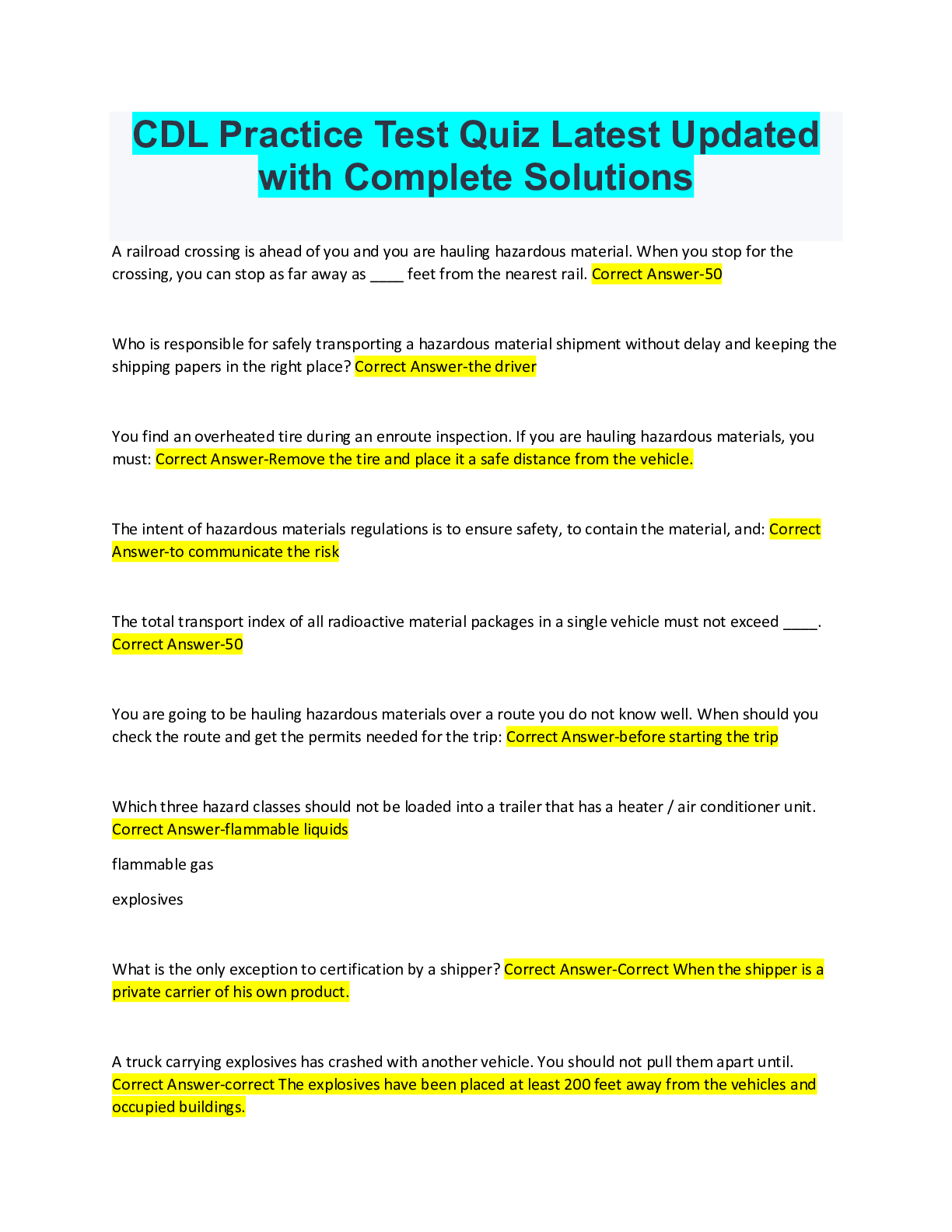
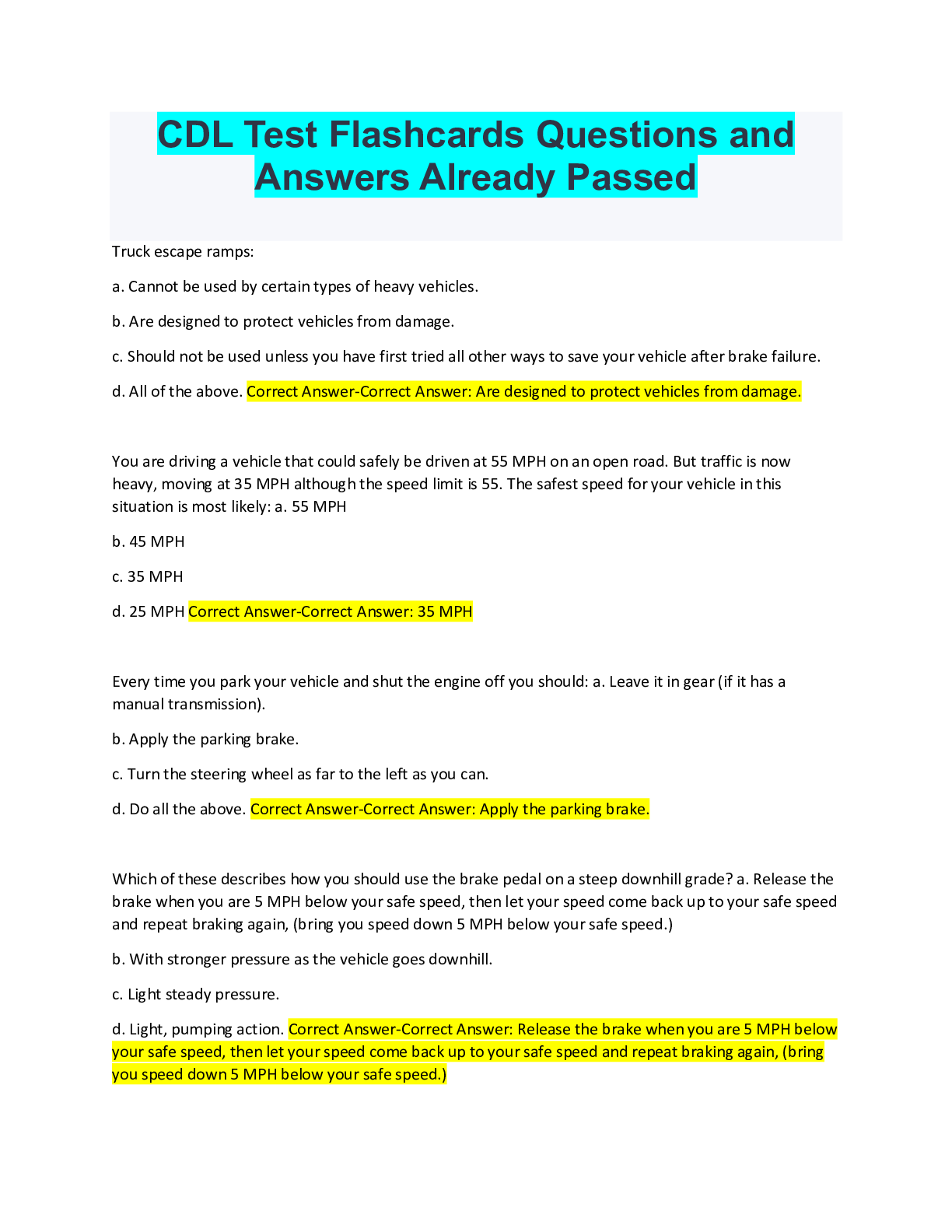
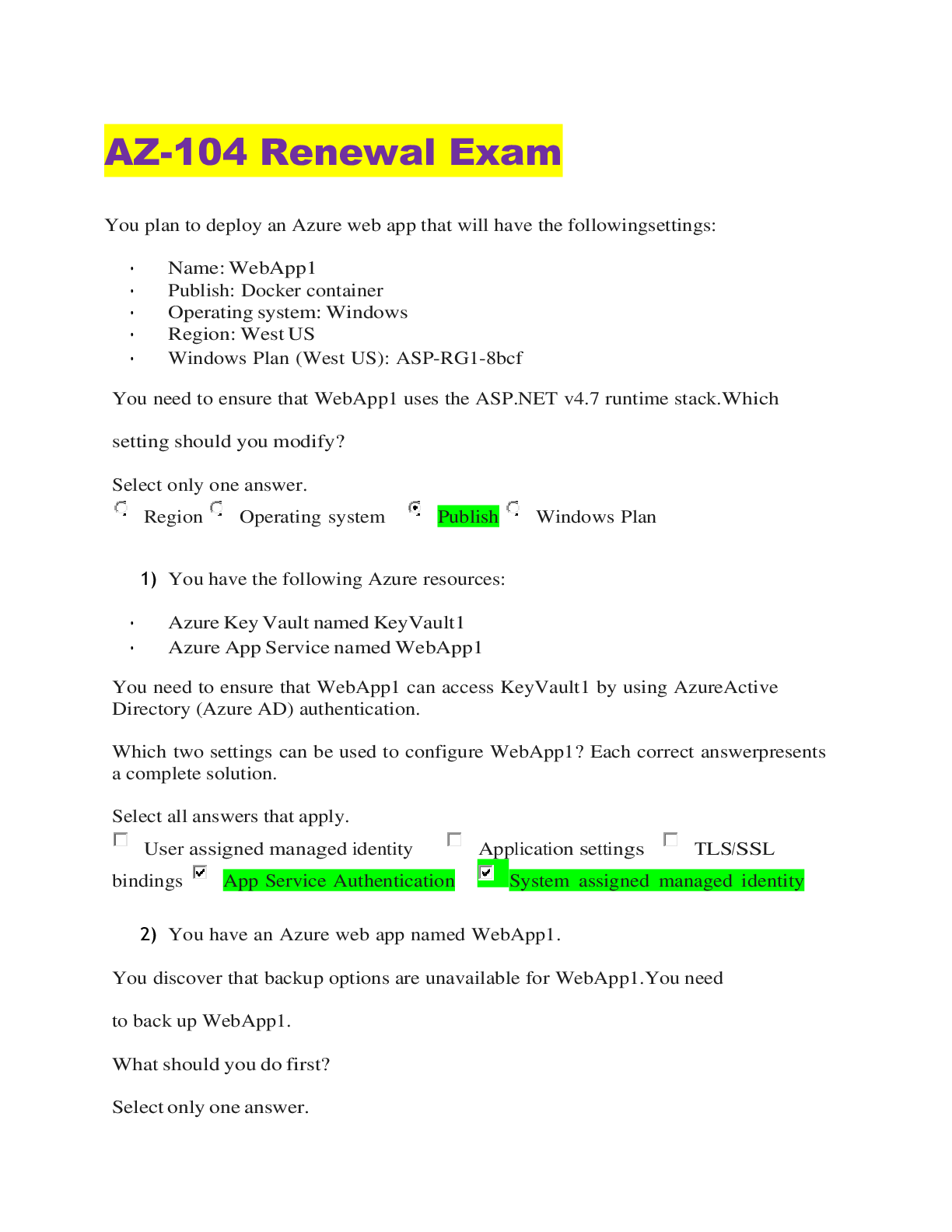
2022/2023 BEST Security+ SY0-601 EXAM STUDY with Complete Solutions C - An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has... only been given the documentation available to the customers of the applications. Which of the following BEST represents the type of testing that will occur? A. Bug bounty B. Black-box C. Gray-box D. Black-box A - An attacker is attempting to exploit users by creating a fake website with the URL www.validwebsite.com. The attacker's intent is to imitate the look and feel of a legitimate website to obtain personal information from unsuspecting users. Which of the following social-engineering attacks does this describe? A. Information elicitation B. Typo squatting C. Impersonation D. Watering-hole attack C - A security analyst is reviewing the output of a web server log and notices a particular account is attempting to transfer large amounts of money: GET http://yourbank.com/transfer.do?acetnum=087646958&amount=500000 HTTP/1.11 GET http://yourbank.com/transfer.do?acctnum=087646958& amount=5000000 HTTP/1.1 GET http://yourbank.com/transfer.do?acctnum=087646958&amount=1000000 HTTP/1.1 GET http://yourbank.com/transfer.do?acgtnum=087646958 & amount=500 HTTP/1.1 Which of the following types of attack is MOST likely being conducted? A. SQLi B. CSRF C. Session replay D. API DF - A company is upgrading its wireless infrastructure to WPA2-Enterprise using EAP-TLS. Which of the following must be part of the security architecture to achieve AAA? (Select TWO) A. DNSSEC B. Reverse proxy C. VPN concentrator D. PKI E. Active Directory F. RADIUS C - An organization is concerned that its hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities? A. hping3 -S corsptia.org -p 80 B. nc -1 -v comptia.org -p 80 C. nmap comptia.org -p 80 -sV D. nslookup -port=80 comptia.org AC - A security analyst is performing a packet capture on a series of SOAP HTTP requests for a security assessment. The analyst redirects the output to a file After the capture is complete, the analyst needs to review the first transactions quickly and then search the entire series of requests for a particular string. Which of the following would be BEST to use to accomplish the task? (Select TWO). A. head B. Tcpdump C. grep D. rail E. curl F. openssl G. dd CD - Which of the following are requirements that must be configured for PCI DSS compliance? (Select TWO) A. Testing security systems and processes regularly B. Installing and maintaining a web proxy to protect cardholder data C. Assigning a unique ID to each person with computer access D. Encrypting transmission of cardholder data across networks E. Benchmarking security awareness training for contractors F. Using vendor-supplied default passwords for system passwords AB - A security analyst Is hardening a Linux workstation and must ensure It has public keys forwarded to remote systems for secure login. Which of the following steps should the analyst perform to meet these requirements? (SelectTWO). A. Forward the keys using ssh-copy-id. B. Forward the keys using scp. C. Forward the keys using ssh -i. D. Forward the keys using openssl -s. E. Forward the keys using ssh-keygen B - An attacker is trying to gain access by installing malware on a website that is known to be visited by the target victims. Which of the following is the attacker MOST likely attempting? A. A spear-phishing attack B. A watering-hole attack C. Typo squatting D. A phishing attack B - A security engineer at an offline government facility is concerned about the validity of an SSL certificate. The engineer wants to perform the fastest check with the least delay to determine if the Which of the following would BEST these requirement? A.RA B. OCSP C. CRL D. CSR B - [DATA] attacking service Etpon port 21 [ATTEMPT] target 192.168.50.1 - login "admin" - pass "password" [ATTEMPT] target 192.168.50.1 - login "adma.." - pass "access" [ATTEMPT] target 192.168.50.1 - login "admin" - pass "allow" [ATTEMPT] target 192.168.50.1 - login "admin" - pass "please" [ATTEMPT] target 192.168.50.1 - login "admin" - pass "cp" [ATTEMPT] target 192.168.50.1 - login "admin" - pase "letmein" [21j[ftp) host: 192.168.50.1 login: admin password: lethein 1 of 1 target successfully completed, 1 valid password found Which of the following BEST describes the type of attack that is occurring? A. Rainbow table B. Dictionary C. Password spraying D. Pass-the-hash C - The website http://companywebsite.com requires users to provide personal Information, Including security question responses, for registration. Which of the following would MOST likely cause a data breach? A. Lack of input validation B. Openpermissions C. Unsecure protocol D. Missing patches A - Which of the following disaster recovery tests is the LEAST time-consuming for the disaster recovery team? A. Tabletop B. Parallel C. Full interruption D. Simulation C - 259. An organization blocks user access to command-line interpreters but hackers still managed to invoke the interpreters using native administrative tools. Which of the following should the security team do to prevent this from happening in the future? A. Implement HIPS to block Inbound and outbound SMB ports 139 and 445. B. Trigger a SIEM alert whenever the native OS tools are executed by the user C. Disable the built-in OS utilities as long as they are not needed for functionality. D. Configure the AV to quarantine the native OS tools whenever they are executed. C - The manager who is responsible for a data set has asked a security engineer to apply encryption to the data on a hard disk. The security engineer is an example of a: A. data controller B. data owner C. data custodian D. data processor A - A company is launching a new internet platform for its clients. The company does not want to implement its own authorization solution but instead wants to rely on the authorization provided by another platform. Which of the following is the BEST approach to implement the desired solution? A. OAuth B. TACACS+ C. SAML D. RADIUS [Show More]
Last updated: 1 year ago
Preview 1 out of 71 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$11.00
Document information
Connected school, study & course
About the document
Uploaded On
Aug 26, 2022
Number of pages
71
Written in
Additional information
This document has been written for:
Uploaded
Aug 26, 2022
Downloads
0
Views
87