Computer Networking > QUESTIONS & ANSWERS > Palo Alto Exam Questions with Complete Solutions (All)
Palo Alto Exam Questions with Complete Solutions
Document Content and Description Below
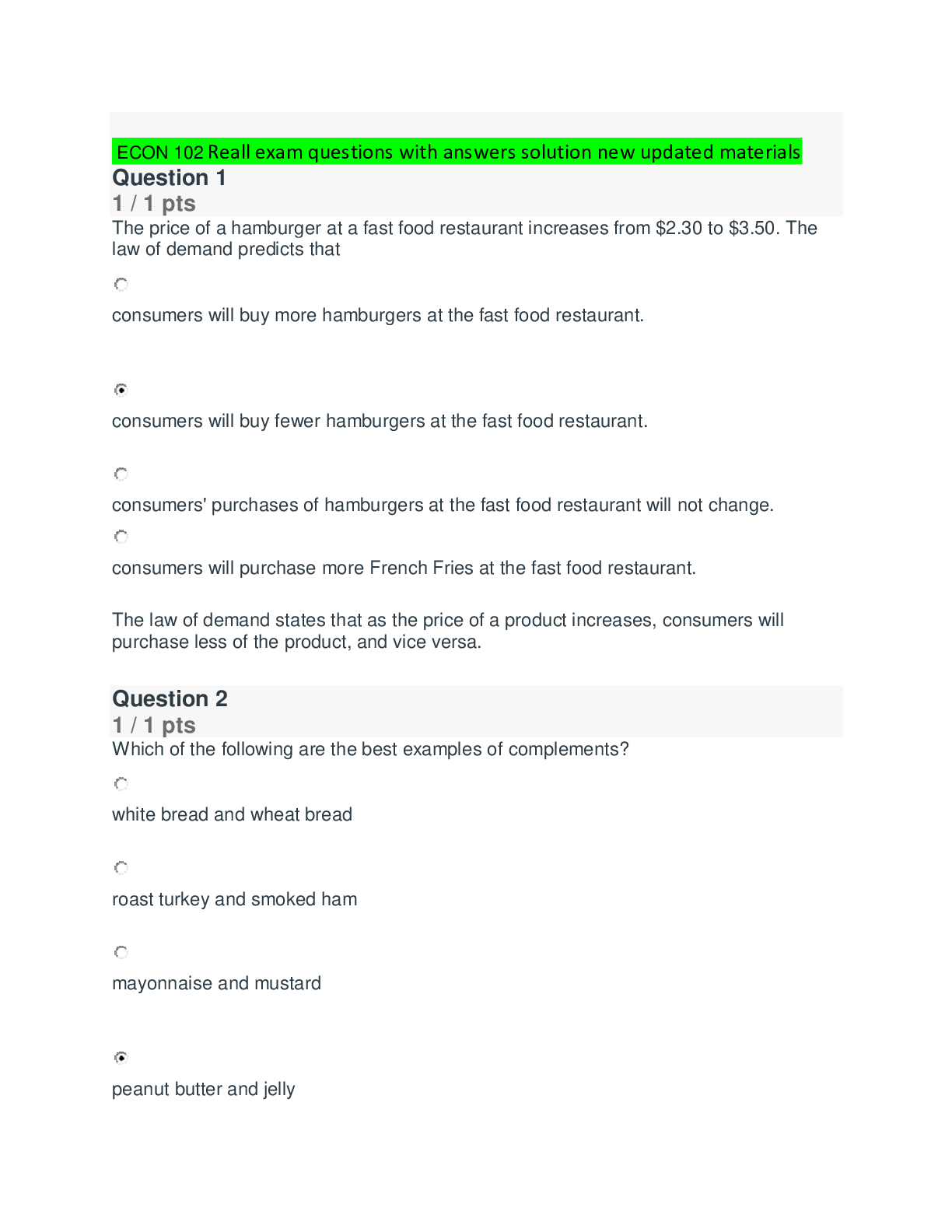
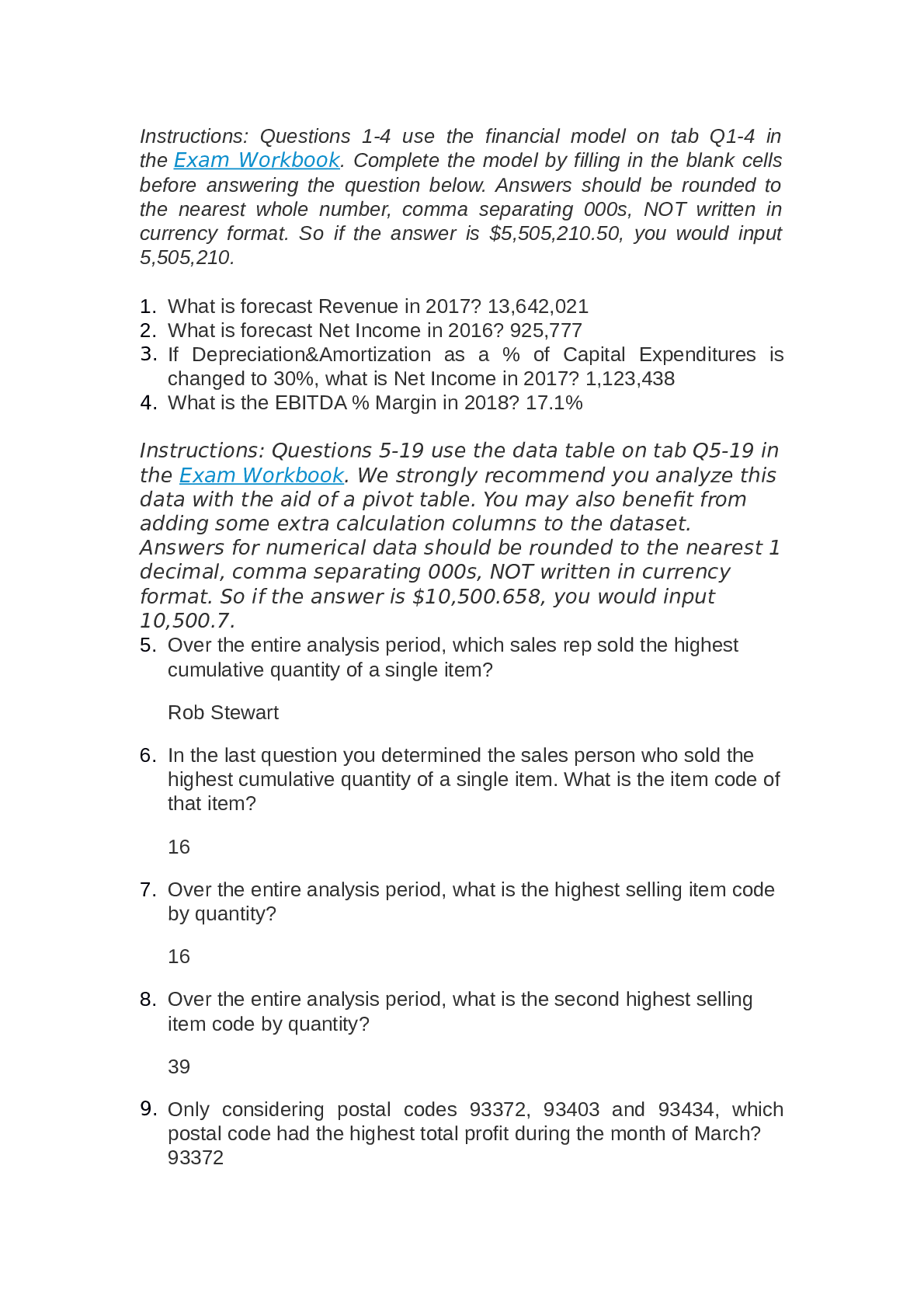
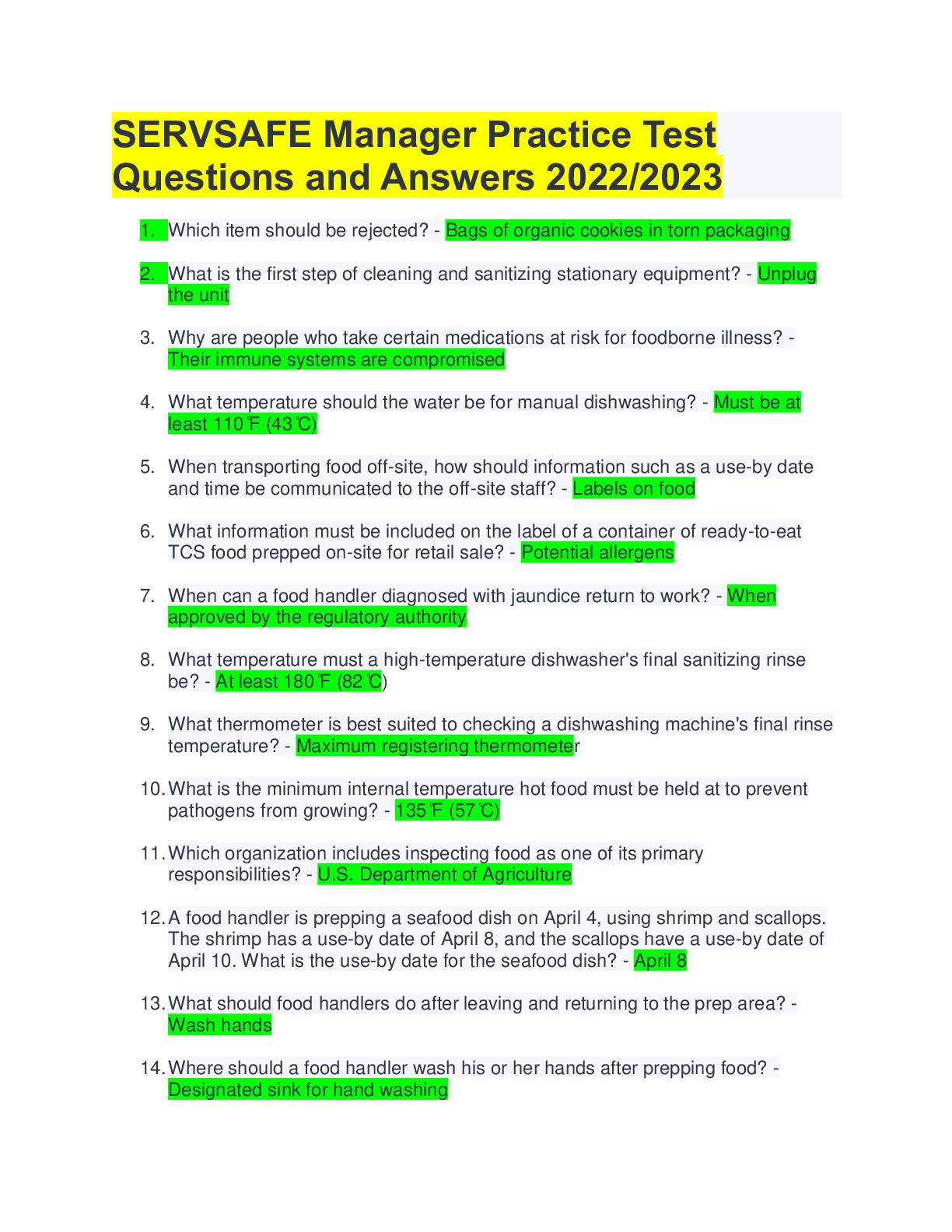
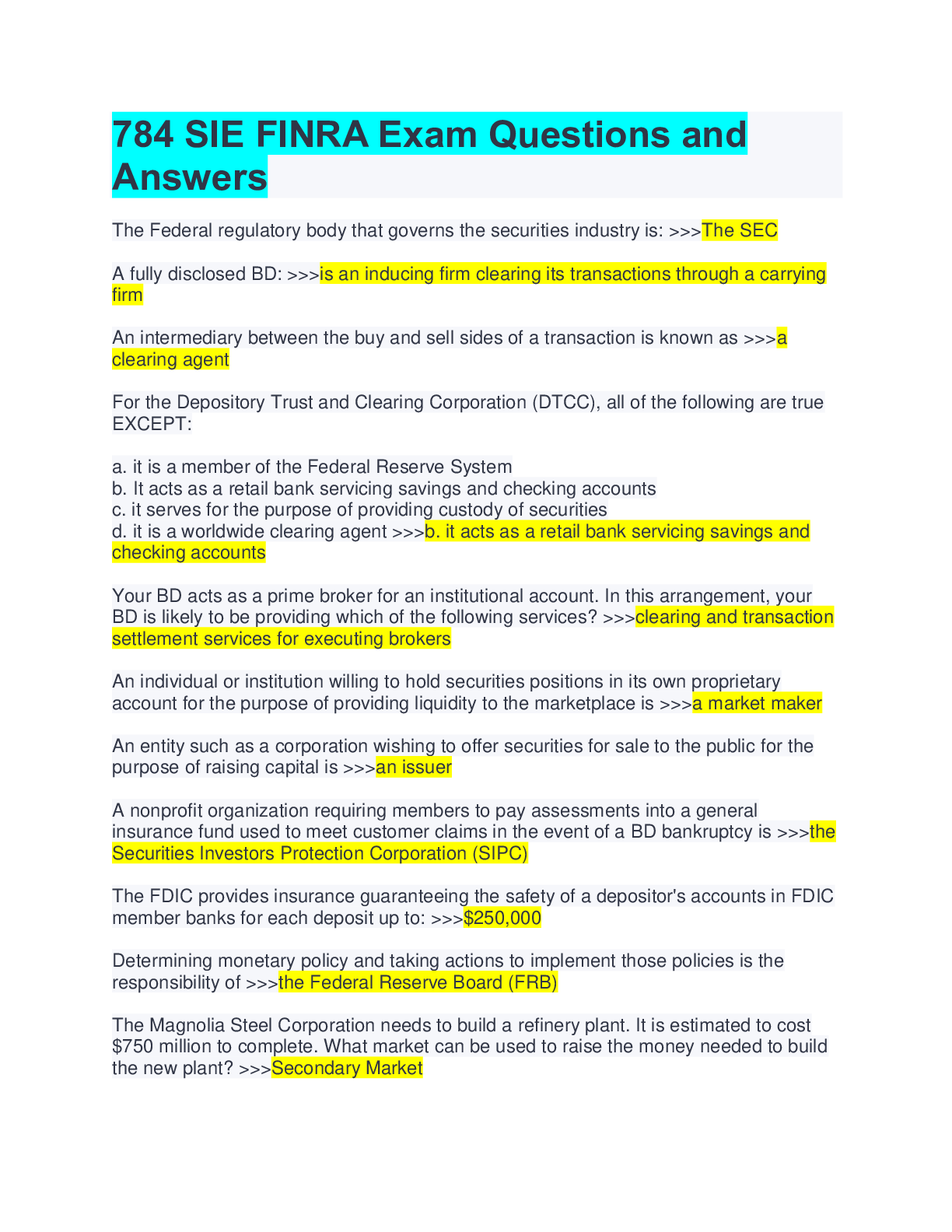
Palo Alto Exam Questions with Complete Solutions An Antivirus Security Profile specifies Actions and WildFire Actions. Wildfire Actions enable you to configure the firewall to perform which operat... ion? A. Delete packet data when a virus is suspected. B. Download new antivirus signatures from WildFire. C. Block traffic when a WildFire virus signature is detected. D. Upload traffic to WildFire when a virus is suspected. -Answer- D. Upload traffic to WildFire when a virus is suspected. An Interface Management Profile can be attached to which two interface types? (Choose two.) A. Tap B. Layer 2 C. Loopback D. Layer 3 E. Virtual Wire -Answer- C. Loopback D. Layer 3 App-ID running on a firewall identifies applications using which three methods? (Choose three.) A. PAN-DB lookups B. WildFire lookups C. Application signatures D. Program heuristics E. Known protocol decoders -Answer- C. Application signatures D. Program heuristics E. Known protocol decoders Application block pages can be enabled for which applications? A. any B. web-based C. MGT port-based D. non-TCP/IP -Answer- B. web-based Because a firewall examines every packet in a session, a firewall can detect application ________? A. shifts B. errors C. groups D. filters -Answer- A. shifts Finding URLs matched to the not-resolved URL category in the URL Filtering log file might indicate that you should take which action? A.Reboot the firewall. B. Validate your Security policy rules. C. Validate connectivity to the PAN-DB cloud. D. Re-download the URL seed database. -Answer- C. Validate connectivity to the PAN-DB cloud. For which firewall feature should you create forward trust and forward untrust certificates? A. SSH decryption B. SSL forward proxy decryption C. SSL client-side certificate checking D. SSL Inbound Inspection decryption -Answer- B. SSL forward proxy decryption If a DNS sinkhole is configured, any sinkhole actions indicating a potentially infected host are recorded in which log type? A. Data Filtering B. WildFire Submissions C. Threat D. Traffic -Answer- C. Threat If there is an HA configuration mismatch between firewalls during peer negotiation, which state will the passive firewall enter? A. PASSIVE B. NON-FUNCTIONAL C. ACTIVE D. INITIAL -Answer- B. NON-FUNCTIONAL In a destination NAT configuration, which option accurately completes the following sentence? A Security policy rule should be written to match the _______. A. original pre-NAT source and destination addresses, and the pre-NAT destination zone B. original pre-NAT source and destination addresses, but the post-NAT destination zone C. post-NAT source and destination addresses, and the post-NAT destination zone D. post-NAT source and destination addresses, but the pre-NAT destination zone -Answer- B. original pre-NAT source and destination addresses, but the post-NAT destination zone In a Security Profile, which action does a firewall take when the profiles action is configured as Reset Server? (Choose two.) A. For UDP sessions, the connection is reset. B. For UDP sessions, the connection is dropped. C. The client is reset. D. The traffic responder is reset. -Answer- B. For UDP sessions, the connection is dropped. D. The traffic responder is reset. In an HA configuration, which three components are synchronized between the pair of firewalls? (Choose three.) A. policies B. networks C. objects D. logs -Answer- A. policies B. networks C. objects In an HA configuration, which three functions are associated with the HA1 Control Link? (Choose three.) A. synchronizing sessions B. synchronizing configuration C. exchanging heartbeats D. exchanging hellos -Answer- B. synchronizing configuration C. exchanging heartbeats D. exchanging hellos SSL Inbound Inspection requires that the firewall be configured with which two components? (Choose two.) A. client's digital certificate B. server's digital certificate C. server's private key D. client's public key -Answer- B. server's digital certificate C. server's private key The firewall acts as a proxy for which two types of traffic? (Choose two.) A. SSL Inbound Inspection B. SSL outbound C. SSH D. Non-SSL -Answer- B. SSL outbound C. SSH The Threat log records events from which three Security Profiles? (Choose three.) A. Anti-Spyware B. File Blocking C. Antivirus D. URL Filtering E. WildFire Analysis F. Vulnerability Protection -Answer- A. Anti-Spyware C. Antivirus F. Vulnerability Protection [Show More]
Last updated: 1 year ago
Preview 1 out of 28 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Sep 05, 2022
Number of pages
28
Written in
Additional information
This document has been written for:
Uploaded
Sep 05, 2022
Downloads
0
Views
79









.png)






.png)

 ANSWERS.png)