Information Technology > EXAM > WGU C724 Information Systems Management Unit 7 Test with Complete Solution (All)
WGU C724 Information Systems Management Unit 7 Test with Complete Solution
Document Content and Description Below
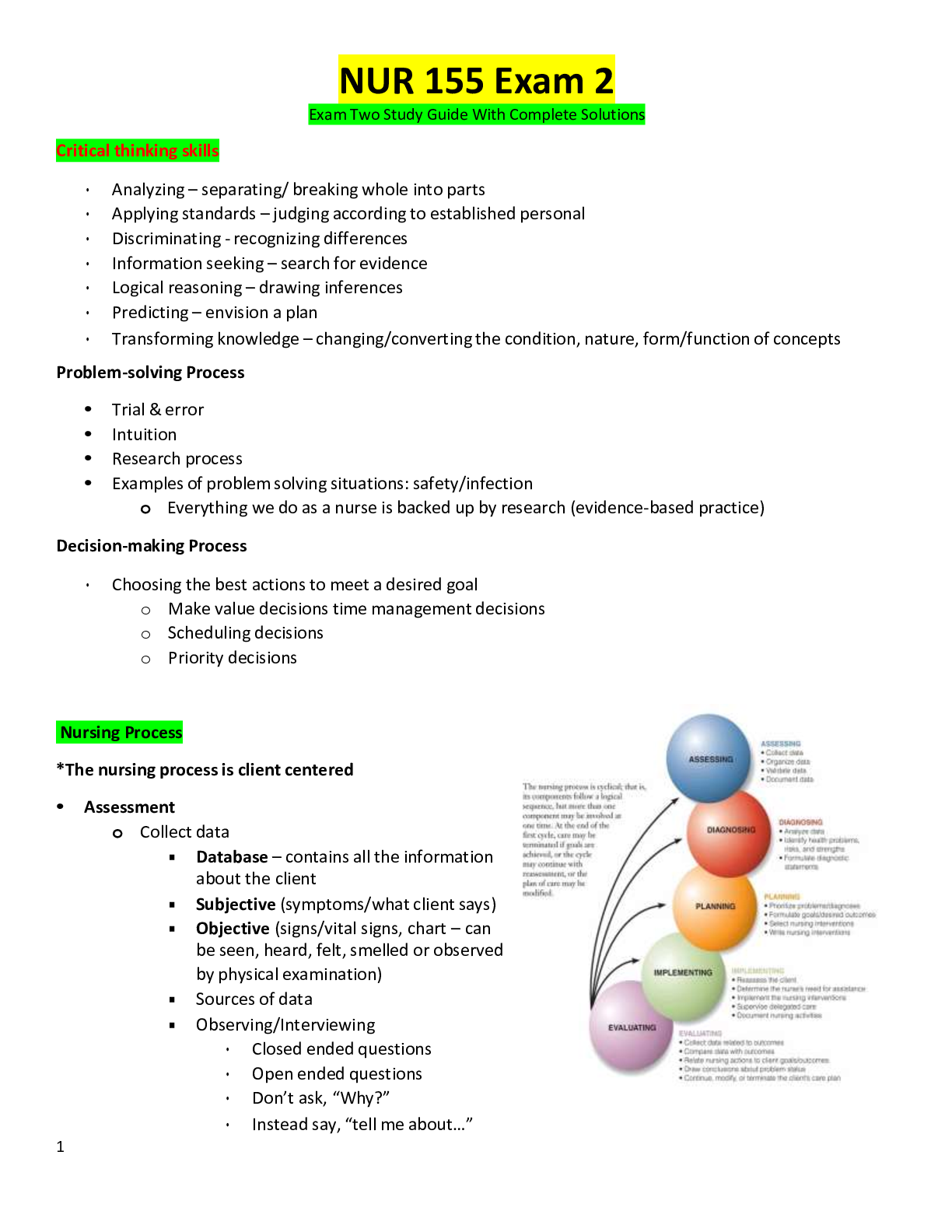
False - ANSWER [True/False] Information is a valuable asset and not everyone in the world can be trusted with it. Therefore, we need to protect our valuable information from those with poor intentions... . The protection of our information assets is a discipline known as data security. a.) True b.) False Black Hat - ANSWER Organizations are constantly encountering cyber-attacks from intruders. For instance, in late 2013, the security system of Target Stores, Inc., was compromised by which of the following type of attacker? a.) Grey Hat b.) Black Hat c.) White Hat Phishing - ANSWER Criminals use which method to send legitimate-looking emails to innocent victims, which direct them to a Website where they are asked to input personal information such as user logon and password? a.) Identity theft b.) Pharming c.) Social engineering d.) Phishing Financial Services Modernization Act (aka Gramm-Leach-Bliley Act) of 1999 - ANSWER Organizations must follow procedures to store or transfer their financial information as outlined in which of the following legislation? a.) Public Company Accounting Reform and Investor Act (aka Sarbanes-Oxley Act) of 2002 b.) Health Insurance Portability and Accountability Act (HIPAA) of 1996 c.) Financial Services Modernization Act (aka Gramm-Leach-Bliley Act) of 1999 Auditing can only be used by the accounting department - ANSWER Security policies are output from an organization's risk assessment process, which cover an organization's need for various levels of security. Auditing is an example of a security policies control. Which of the following is FALSE regarding auditing? a.) Auditing is used by many divisions and departments within an organization b.) Auditing can only be used by the accounting department c.) An IS auditor may penetrate security policies to determine their adequacy or need for training False - ANSWER [True/False] The process of turning information into an unreadable format to prevent unauthorized access is known as decryption. a.) True b.) False Hot sites - ANSWER Organizations need to include redundancy in their business disaster recovery plan by creating duplicate facilities. Which of the following sites offer offsite office space that allow recovery within minutes to hours? a.) Warm sites b.) Shared hot sites c.) Cold sites d.) Hot sites A and B - ANSWER (Select all that apply). What are some of the actions that savvy users do to protect their privacy? a.) Delete cookies from the computer periodically b.) Enable popup blockers c.) Do not use anonymous browsing Consult legal counsel and retain documentation of all stolen information - ANSWER If your identity has been stolen, what should you do? a.) Protect access to your information assets b.) Understand the methods that criminals used to steal the personal information c.) Understand which assets are irreplaceable and how they are vulnerable d.) Consult legal counsel and retain documentation of all stolen information A small business owner installs Microsoft Office suite on all the computers in his office - ANSWER Which of the following action is considered ethical, social, and legally acceptable? a.) An employee searches the corporate data resources for sensitive information about his neighbor or friends b.) A small business owner installs Microsoft Office suite on all the computers in his office c.) A high school student copies, uses, and distributes Taylor Swift music videos to his classmates Utilitarian approach - ANSWER Which of the following category of ethical models for ethical behavior approach assesses the consequences and/or outcomes of an action to determine the greatest good or least harm for the greatest number, regardless of the justice or fairness of or to the individual? a.) Utilitarian approach b.) Rights approach c.) Virtue d.) Fairness approach False - ANSWER [True/False] Digital goods are adequately protected as intellectual property under the historical copyright laws. a.) True b.) False To understand the concept of safe harbor - ANSWER Which of the following is NOT a benefit for individuals to take information security training? a.) Guard against loss from low-tech methods b.) Guard against loss from high-tech methods c.) To understand the value of their information assets d.) To understand the concept of safe harbor Authentication and authorization - ANSWER Which of the following must be enforced to protect the organization's corporate data resources and to control access to the information assets? a.) Authentication and authorization b.) Authentication and prevention c.) Authorization and prevention False - ANSWER [True/False] Every time we use a computer, we are exposed to the risk of getting a computer virus, even when we scan a photo onto a jump drive using a scanner or a printer. a.) True b.) False Public Company Accounting Reform and Investor Act (aka Sarbanes-Oxley Act) of 2002 - ANSWER Organizations must follow procedures to ensure the accuracy, integrity, and security of their financial information as outlined in which of the following legislation? a.) Public Company Accounting Reform and Investor Act (aka Sarbanes-Oxley Act) of 2002 b.) Health Insurance Portability and Accountability Act (HIPAA) of 1996 c.) Financial Services Modernization Act (aka Gramm-Leach-Bliley Act) of 1999 The AUP specifies acceptable and tolerable uses of an organization's computer systems, equipment, and information assets - ANSWER Security policies are output from an organization's risk assessment process, which cover an organization's need for various levels of security. Acceptable use policy (AUP) is an example of a security policies control. Which of the following is TRUE regarding AUP? a.) The AUP specifies acceptable and tolerable uses of an organization's computer systems, equipment, and information assets b.) The AUP determines if the user follows the policies and procedures stipulated by the organization c.) The AUP defines the authorization and authentication of users Unique identity - ANSWER Biometrics is the study and measuring of individual body characteristics, and is often used in computer security. Biometrics falls under which of the following methods? a.) Possession b.) Unique identity c.) Knowledge Data at rest - ANSWER At any point in time, all data must be categorized as being in one of the three states. Data that are not being accessed by the CPU are considered to be in which of the following three states? a.) Data in use b.) Data at rest c.) Data in motion Recover and protect business operations - ANSWER A disaster recovery plan (DRP) is a document of procedures to do what? a.) Reimburse company for infrastructure damages b.) Keep employees safe during natural disasters c.) Recover and protect business operations Install the latest anti-malware and antivirus programs - ANSWER What is the best way for individuals to safeguard their computers against malware? a.) Install only the latest antivirus programs b.) Install the latest anti-malware and antivirus programs c.) Install only the latest anti-malware programs d.) Install any version of anti-malware and antivirus programs Create automatic backups on cloud storage - ANSWER Which of the following actions will help us protect our computer against failure? a.) Do not store data on the cloud b.) Create automatic backups on cloud storage c.) Only store data on a hard drive d.) Store all data on a jump drive B and C - ANSWER (Select all that apply). If we intentionally harden our individual security, we can make it more difficult for criminals to steal our information assets. Which of the following recommendations will harden our individual security? a.) Make account access or changes easier b.) Manage the retention and disposal of potentially sensitive information c.) Randomize behavior [Show More]
Last updated: 1 year ago
Preview 1 out of 14 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Oct 27, 2022
Number of pages
14
Written in
Additional information
This document has been written for:
Uploaded
Oct 27, 2022
Downloads
0
Views
31