HITT 1211 : Health Information Management > EXAM > HIM 370 Week 8 Final Exam – Download For Revision (All)
HIM 370 Week 8 Final Exam – Download For Revision
Document Content and Description Below
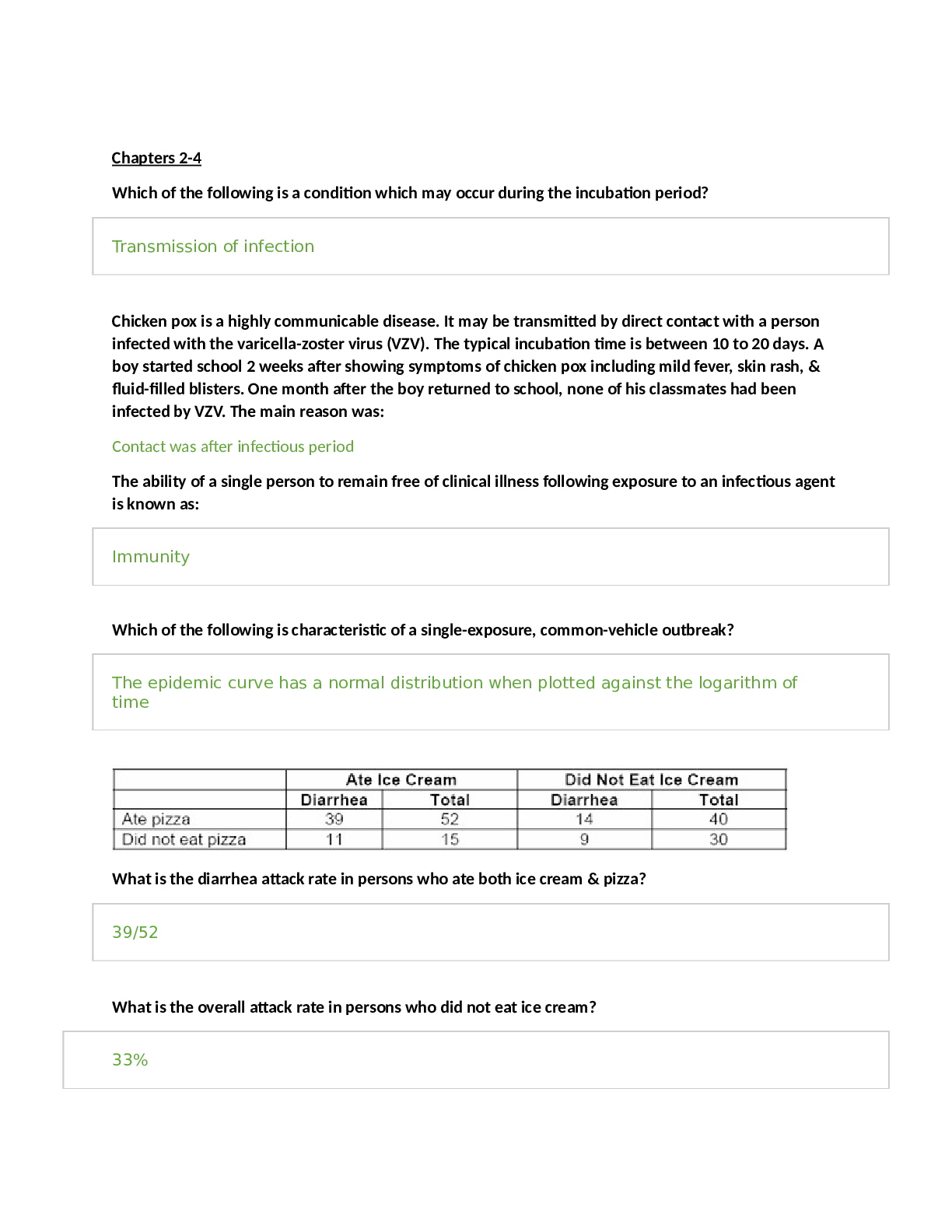
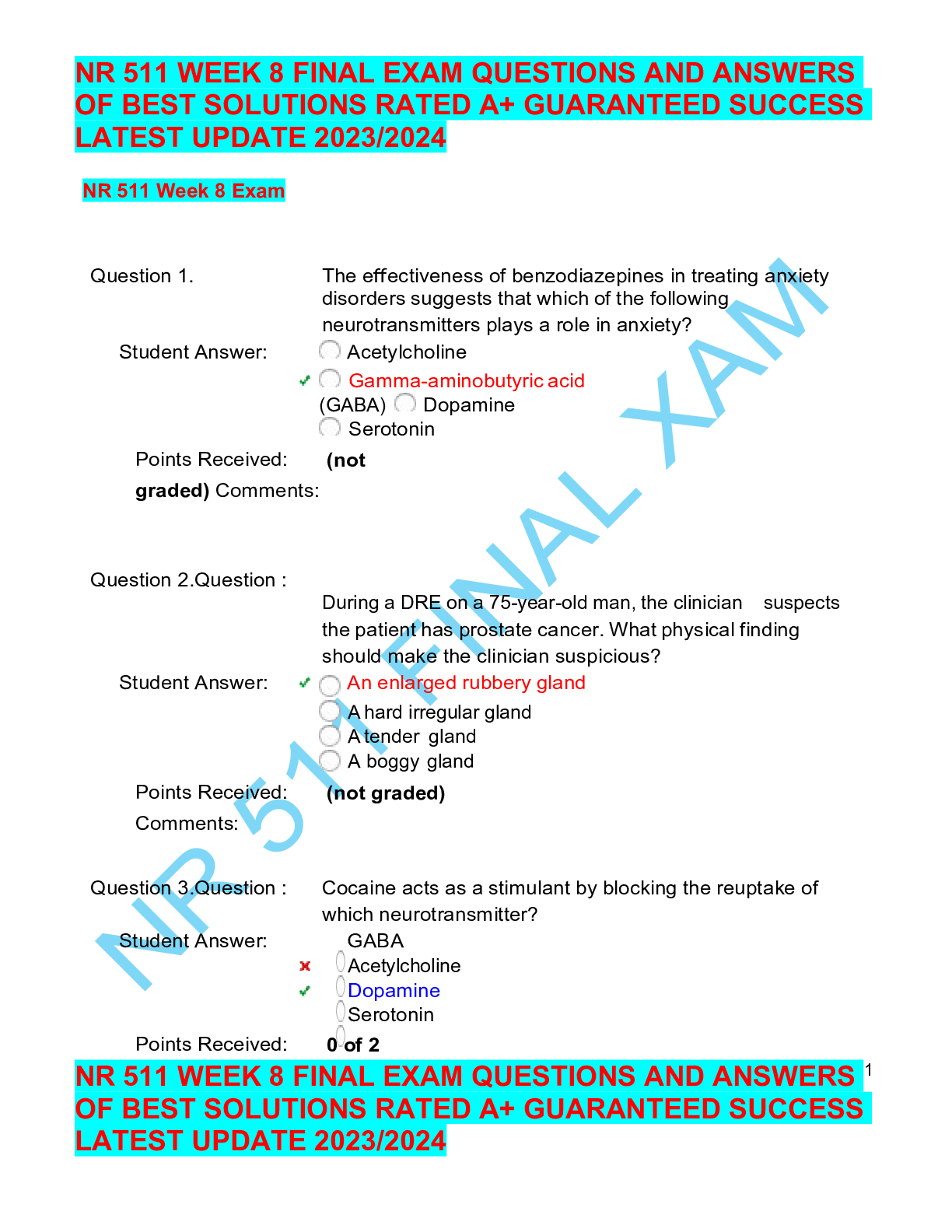
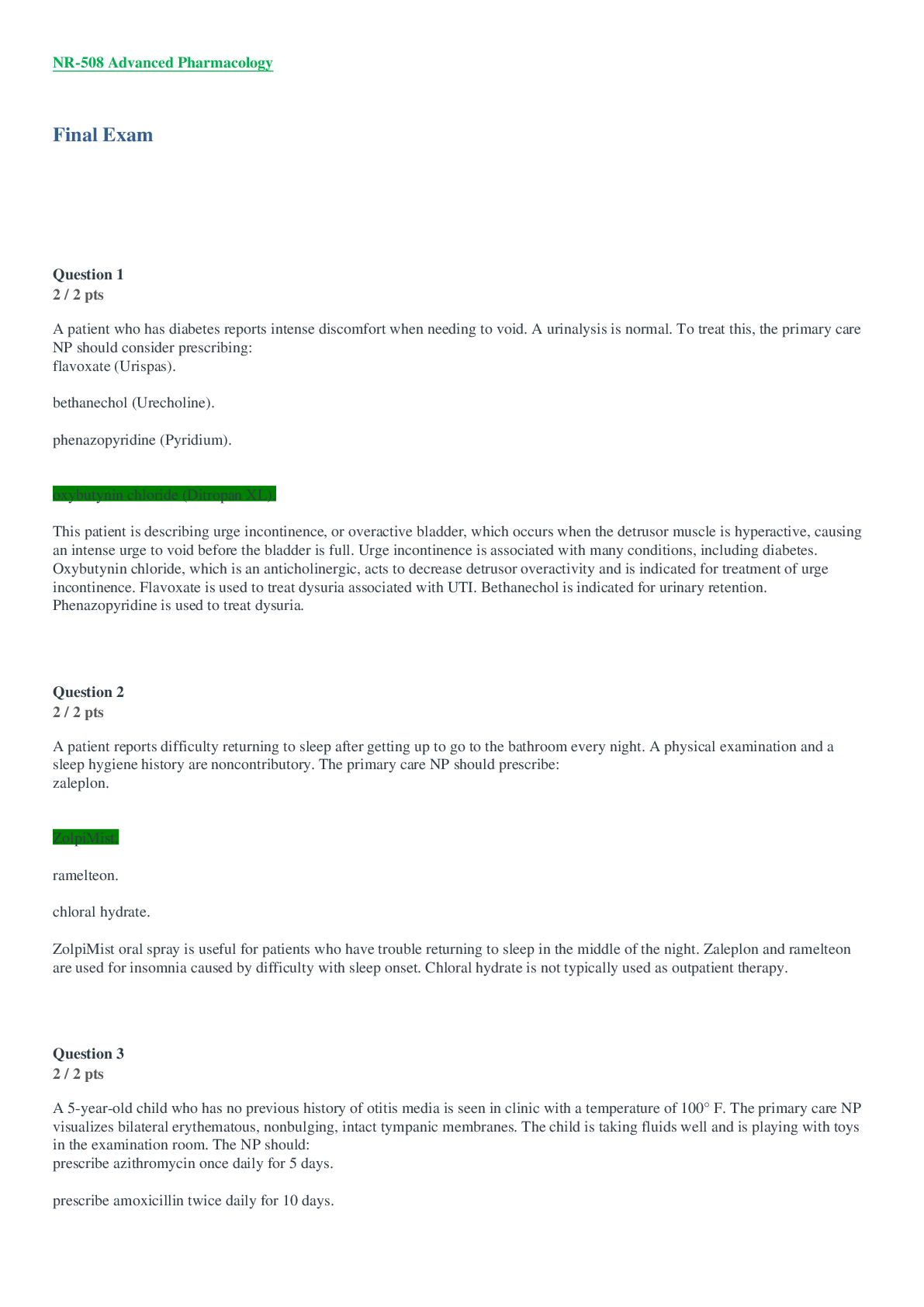
HIM 370 Week 8 Final Exam – Download For Revision (CO 1) Gail Smith oversees all activities associated with the development, implementation, and administration of Health Science Center policies... and procedures covering the privacy of, and access to, patient health information. Based on this information, she is most likely in the position of a(n) . Information Security Officer Privacy Officer HIM Director HR Manager (CO 1) Sarah Williams' responsibilities include leading the incident response team and conducting personnel pertaining to data protection in the Health Information Systems (HIS) Department. Based on her responsibilities, she is most likely in the role of a(n) . Information Security Officer Privacy Officer HIM Director HR Manager (CO 1) Ms. Jones oversees all activities associated with the development, implementation, and administration of Health Science Center policies and procedures, covering patient confidentiality. Based on this information, she is most likely in the position of a(n) . Information Security Officer. Privacy Officer HIM Director HR Manager (CO 9) Which of the following most accurately describes the difference between training and awareness? Training is less formal and interactive than an awareness program. Training is more formal and interactive than an awareness program. A training program is more expensive than an awareness program. An awareness program is more expensive than a training program. (CO 9) Which of the following should you do if an audit does not return any opportunities for improvement? Hire a consultant to review again. Consider that the audit components are not detailed enough. Perform another one the following year. Conclude that no improvements are needed. (CO 9) Which technical components should be included in developing a checklist for auditing and monitoring compliance? Authorization controls Physical access controls Data encryption mechanisms All of the above (CO 2) All patient information is designated protected health information (PHI) and includes information that is . stored on electronic media written format spoken All of the above (CO 2) Which of the following is the main purpose of HIPAA? HIPPA guarantees insurance coverage for all U.S. citizens. HIPPA improves technology. HIPPA reduces administrative costs and protects patient information. All of the above (CO 2) Which of the following headers must appear in a notice of privacy practices? This notice describes how much medical information about you may be used and disclosed, and how you can get access to this information. Review carefully. This notice details your rights, obligations, and course of actions related to your health information. Review carefully. This notice describes your obligations to ensure the protection of your medical information. Review carefully. This notice advises you of your legal rights with respect to how your medical information may be used. Review carefully. (CO 4) Which of the following is characteristic of an appropriate consent? Customizable Generic Gives insurers permission to use and disclose all information Must contain specific information regarding the information to be disclosed (CO 4) Organizations should perform an initial risk analysis to determine which of the following? Disclosures Unauthorized uses Data integrity All of the above (CO 4) Which of the following is NOT a level or risk to be taken into consideration when analyzing risks to protected health information (PHI)? Residual risk Present risk Inherent risk Past risk (CO 5) To address disposal of media, an organization should . create a retrievable, exact copy of electronic protected health information, when needed, and before movement of equipment develop policies and procedures to address the final disposition of electronic protected health information (PHI) and/or hardware implement procedures for removal of electronic protected health information (PHI) from electronic media before the media are made available for reuse create a special team to address the issue (CO 5) Which is NOT an example of a physical safeguard, as outlined by HIPAA? Access to doors Computer passwords Workstation availability Badge access (CO 6) Access controls consist of . identification authentication authorization All of the above (CO 3) Which term identifies patient information related to medical record numbers and fingerprinting? PII PHI DII HIPAA (CO 3) How often should you consider performing a review of your security policies? Every 5 years Never Right before being audited Annually (CO 8) Which of the following is the most likely group to target for HIPAA privacy and security training? Personnel who received promotions Trash removal contractors Third party insurance companies Call centers and front desk switchboards (CO 7) Which of the following are the appropriate guidelines for dealing with medical information requests? Appropriate guidelines ensure that receiving machines are unsecured. Appropriate guidelines is do not supply information if subpoenaed. Appropriate guidelines is do not supply information if you have patient consent. Appropriate guidelines ensure there is a secured telephone line for telephone requests. (CO 7) Who does not need to be part of a security incident team? CIO Legal counsel HIPAA security officer ER nurse [Show More]
Last updated: 2 months ago
Preview 1 out of pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Mar 08, 2024
Number of pages
Written in
Additional information
This document has been written for:
Uploaded
Mar 08, 2024
Downloads
0
Views
3



















.png)