General Questions > EXAM > DeVry University_SOCS 360 Week 8 Final Exam/SOCS 360 Week 8 Final Exam Question And Answers_Rated A+ (All)
DeVry University_SOCS 360 Week 8 Final Exam/SOCS 360 Week 8 Final Exam Question And Answers_Rated A+
Document Content and Description Below
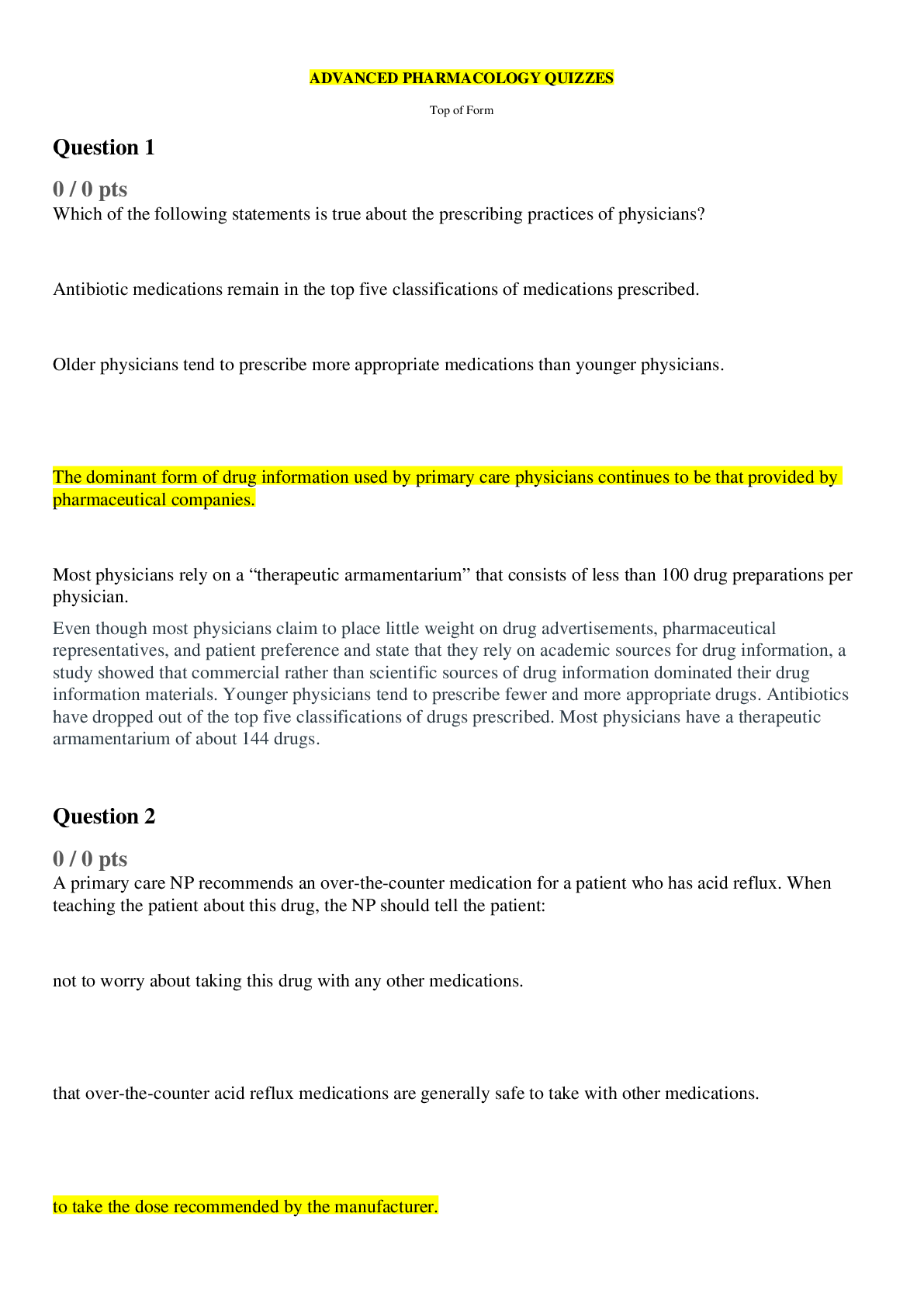
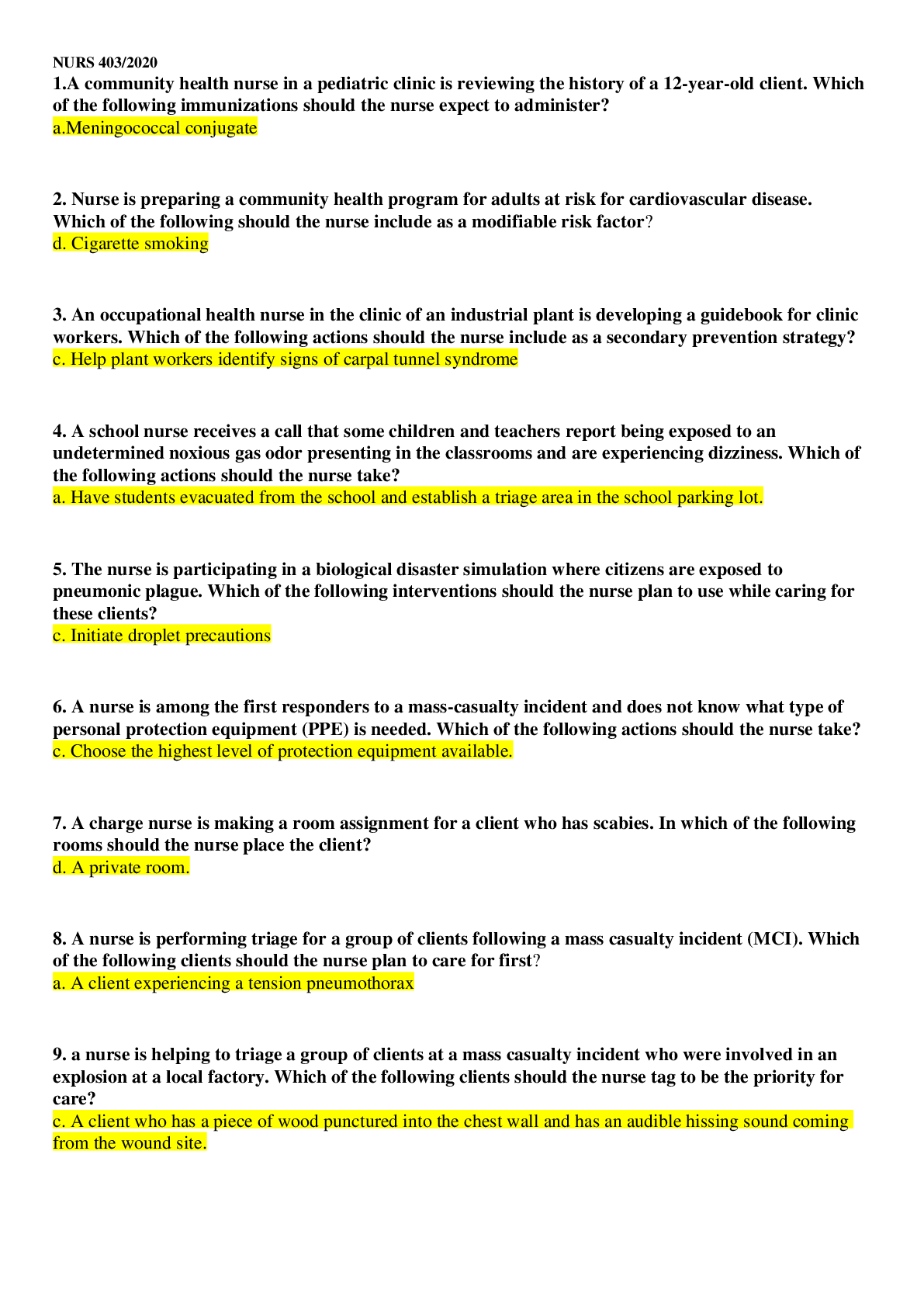
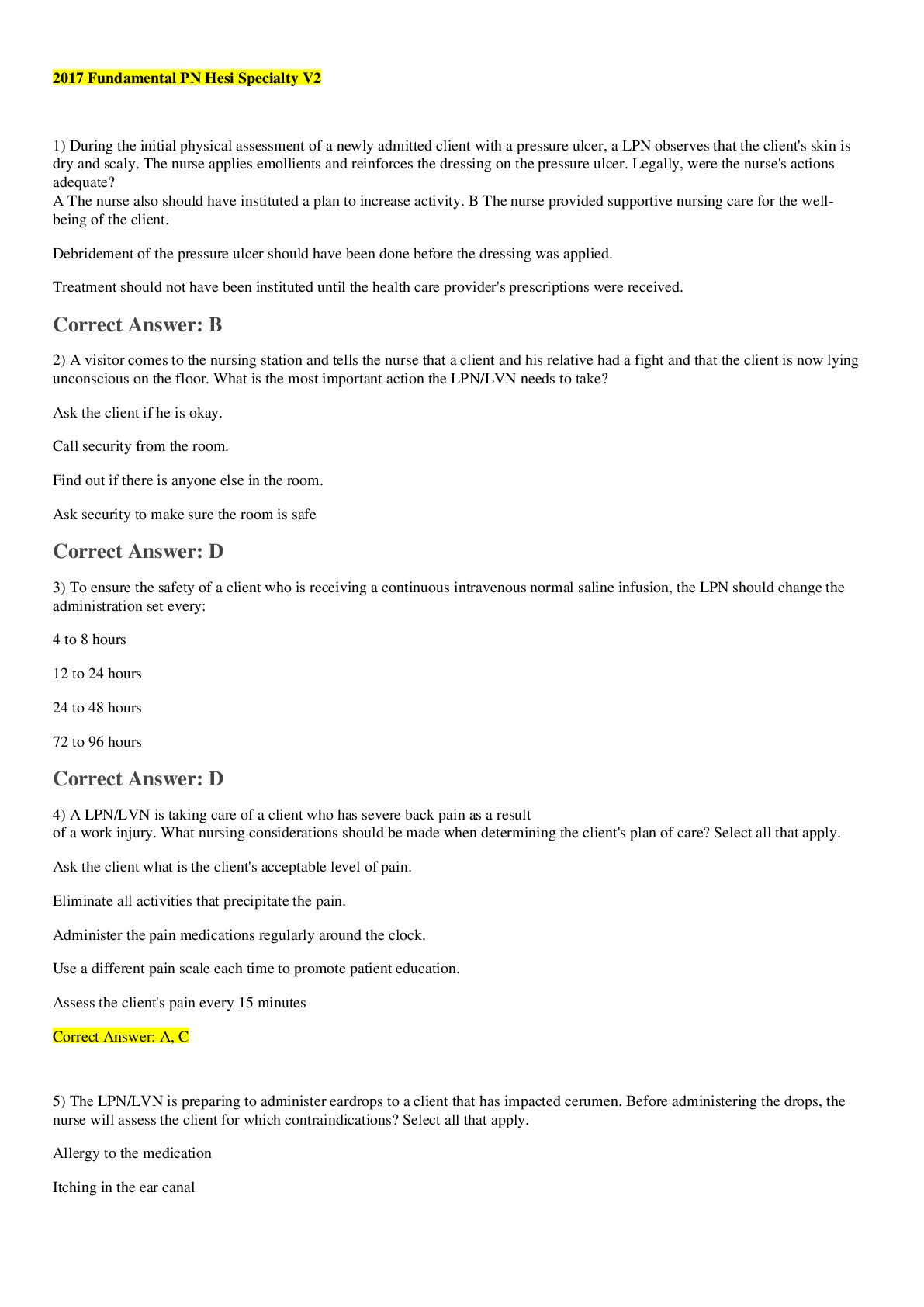
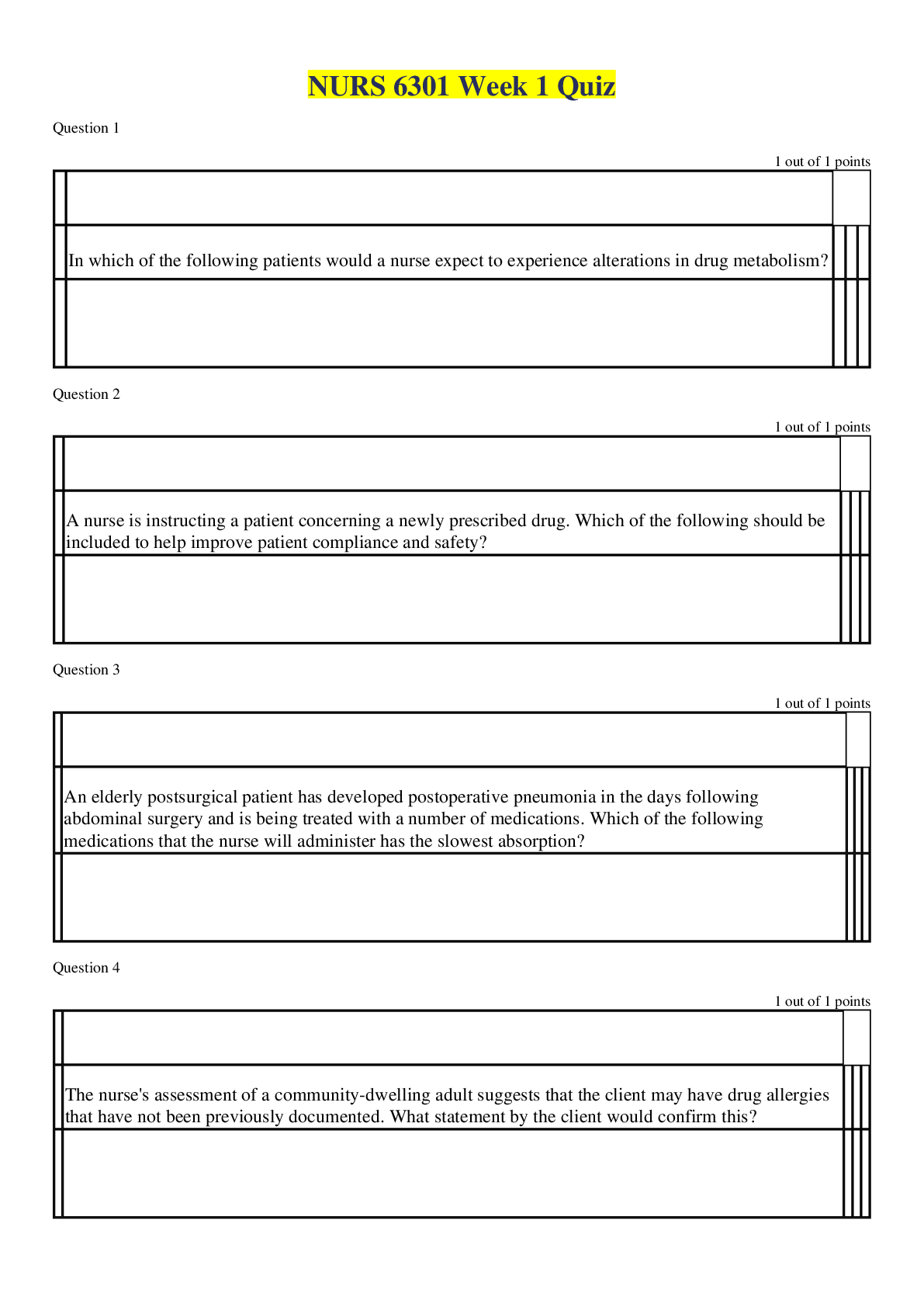
SEC 360 Week 8 Final Exam Multiple Choice Questions Question. (TCO 1) Information security is a process that protects all of the following except _____. Question. (TCO 2) The _____ of the 17 NI... ST control _____ can be placed into the 10 IISSCC _____ comprising the common body of knowledge for information security. Question. (TCO 2) What are the classes of security controls? Question. (TCO 3) Security policies, regardless of level, should ensure that _____ of assets is distinguished, ___ of people is maintained, and that ___ is managed because that is the enemy of security. Question. (TCO 4) Privacy legislation is written to protect _____. Question. (TCO 5) Ideas can be evaluated using ____, which are ____ that are not meant to be _____. Question. (TCO 6) Many believe that the most important physical security control is _____. Question. (TCO 7) The security principle that says that each user should have access to exactly the information resources needed to do his/her job–no more and no less–is called _____. Question. (TCO 8) Security recovery strategies should always seek to restore _____. Question. (TCO 9) Access controls manage the use of _____ by _____ in an information system. Question. (TCO 10) As a generalization, symmetric cryptography is used to encrypt _____, and asymmetric cryptography is used to encrypt _____. Question. (TCO 10) In a given city, there are a group of people who wish to communicate through the use of asymmetric cryptography. They do not wish to work with any type of certificate authority. Given this information, how would this be accomplished? Question. (TCO 11) A firewall that disconnects an internal network from an external network is called__. Question. (TCO 12) In addition to normal functional and assurance bugs, intrusion detection is subject to two kinds of errors called _____ and _____. Question. (TCO 13) Identify the SDLC phase in which business stakeholders and project team members should refer to company information security policies? Explanatory Questions Question. (TCO 1) Explain what is wrong with this policy clause, and show how you could fix it. People shall obey corporate policies. Question. (TCO 2) The three effects of security controls are prevention, detection, and recovery. Briefly explain how these effects are related to the known good state. Question. (TCO 3) Briefly explain the “principle” that states that security = risk management. Question. (TCO 4) Briefly explain what needs to be accomplished before your company monitors the activities of authorized users of your company systems, and then explain what should be accomplished to legally monitor the activities of a hacker (unauthorized user) of your system. Question. (TCO 5) Explain why the Bell-LaPadula model and the Biba model are called dual models. Question. (TCO 6) Briefly explain why good physical security is critical to good information security. Question. (TCO 7) Explain what media disposition means. Question. (TCO 8) Explain the term cold site. Explanatory Questions Question. (TCO 9) Explain the advantage of role-based access controls. Question. (TCO 10) Name the two uses of a private key in asymmetric cryptography. Question. (TCO 11) Explain how a demilitarized zone might be used to protect critical resources that are not to be shared outside of an organization. Question. (TCO 11) What is often another term for a bastion host? Question. (TCO 12) Explain why intrusion detection is necessary in terms of the known good state. Question. (TCO 12) Summarize the benefits of application-level gateways. Question. (TCO 13) Explain what a virus is, pointing out how it is different from a worm. [Show More]
Last updated: 1 year ago
Preview 1 out of 7 pages
 (3).png)
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 22, 2020
Number of pages
7
Written in
Additional information
This document has been written for:
Uploaded
Aug 22, 2020
Downloads
0
Views
48