Management Information Systems (MIS) > Report > MIS-589 Week 4 Project Milestone: Network Requirements – LANs and Backbone Networks | Already GRAD (All)
MIS-589 Week 4 Project Milestone: Network Requirements – LANs and Backbone Networks | Already GRADED A
Document Content and Description Below
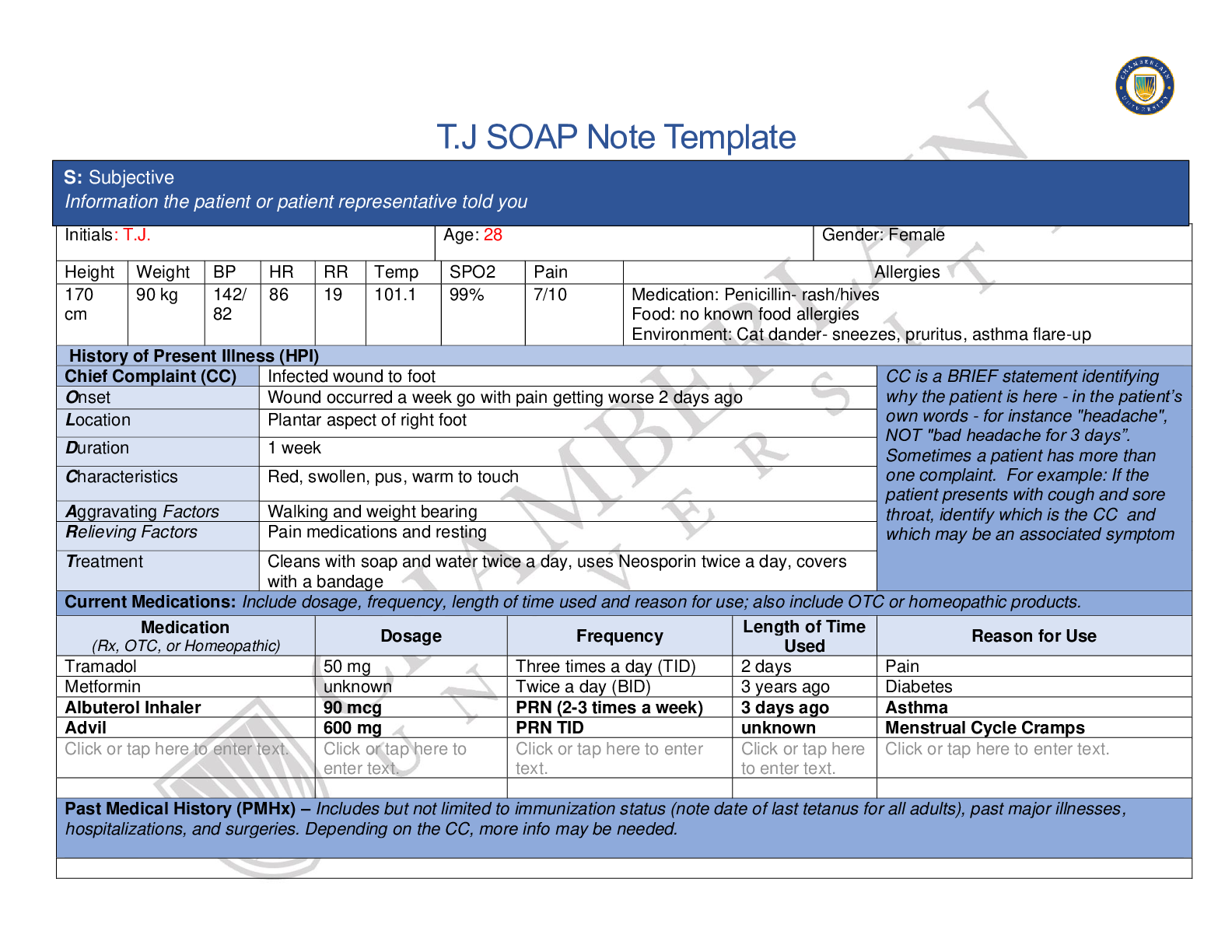
MIS 589 , DeVry University Applied Research Project Milestone 0, Proposal Draft Milestone 1, Proposal Milestone 2, Network Requirements 1 -Physical, Data Link , Network Layers Milestone 3, Netwo... rk Requirements 2 -LAN and Backbone Network Milestone 4, Network Requirements 3 -WAN and Internet Milestone 5, Network Security and Management - Inventory of Assets - Threat Scenario 1 - Network Manager job posting - Project Experience Name MIS589 Project Milestone 0 Proposal Draft VPN (Virtual Private Network) E-commerce Prepared by: Approved by: 1. Description of the service-summary A VPN or Virtual Private Network is a method used to add security and privacy to private and public networks, like WiFi Hotspots and the Internet. VPNs are most often used by corporations to protect sensitive data. 2. Intended clients or customers Any business or company to allow employees to have easy access and connection, even while traveling, to resources that you may not be able to access on another network. If you are using your own VPN, you’ll be able to bypass filters and censorship set by schools and workplaces, and browse anonymously on campus or at work. Even in public places, you can rest assured that your important work is protected from prying eyes and your user data is safe. 3. Business objective statement VPNs allow employee flexibility where network access is needed outside of the business place to perform any business functions including: email, network applications, database access or any other application hosted within the business network. 4. Application architecture description Data storage, data access logic, application logic, presentation logic. The VPN will allow customers to connect securely with sales reps, accouting/billing, or customer service. Clients will be able to access their file accounts, order history, profile and payment methods. Text information will be available and videos will be available for product demonstrations and other marketing related items. Employees will have full access to their accredited software and network locations from any geographic location. Employees will have access to email, instant messaging and video conferencing capabilities. IPSec protocols will be used but will also be paired with tunneling protocols where needed and SSL protocols for more sensitive information. 5. Information provided to the clients The VPN will allow customers to connect securely with sales reps, accouting/billing, or customer service. Clients will be able to access their file accounts, order history, profile and payment methods. Text information will be available and videos will be available for product demonstrations and other marketing related items. 6. Basic requirements Basic requirements of a VPN include data storage, client VPN software, VNP aware routers and firewalls, and a VPN dedicated server Conclusion Clients and employees alike will have secure access to pertinent information through dedicated connections from anywhere in the world. MIS589 Project Milestone 1 Proposal VPN (Virtual Private Network) E-commerce Prepared by: Daniel Wubbena Date: 05/15/2016 Approved by: 1. Description of the service-summary A VPN or Virtual Private Network is a method used to add security and privacy to private and public networks, like WiFi Hotspots and the Internet. VPNs are most often used by corporations to protect sensitive data. 2. Intended clients or customers Any business or company to allow employees to have easy access and connection, even while traveling, to resources that you may not be able to access on another network. If you are using your own VPN, you’ll be able to bypass filters and censorship set by schools and workplaces, and browse anonymously on campus or at work. Even in public places, you can rest assured that your important work is protected from prying eyes and your user data is safe. 3. Business objective statement VPNs allow employee flexibility where network access is needed outside of the business place to perform any business functions including: email, network applications, database access or any other application hosted within the business network. 4. Application architecture description 5. Information provided to the clients 6. Basic requirements Conclusion Network Requirements 1 Physical, Data Link, Network Layers E-commerce Prepared by: Dan Wubbena Date: 05/21/16 Approved by: Summary of physical media and network design for the proposed service (max 200 words) The VPN does not really alter the Physical Layer requirements, as a network is a network. Ideally fiber optics should be used, but CAT5 may have to suffice depending on financial budget constraints. The Data Link layer will be discussed ensuring the most efficient use of bandwidth for customers and employees to access the VPN. Since the VPN will most likely occupy the Layer 3 Network Layer, the specific components of Layer 1 and Layer 2 will be considered somewhat generic. A. Physical media selection: summary Cat 5 or fiber optics, Wifi A.1 Physical media consideration: Types of network and transmission distances Distances will be of very little concern considering the purpose of a VPN is to allow network access from any geographic location that provides internet access. GRE tunneling will be used through the service provider to provice point to point access communication. A.2 Physical media consideration: cost Some significant cvosts may be incurred in future Layers for specific software, but the overall costs of the Physical Layer 1 will be minimal…only CAT 5 of Fiber Optics B. Medium access C. Network design D. Network layer Conclusion MIS589 Project Milestone 3 Network Requirements 2 LAN and Backbone Network VPN E-commerce Prepared by : Daniel Wubbena Date: 05/27/2016 Approved by: Summary of LAN or backbone network for the proposed network (max 200 words) This section will cover the components, technologies, tunneling and VPN security measures needed for this project to be successful. This information will include, but not be limited to, remote access, site-to-site, connectivity, transit times and network topology. A. LAN design summary Basic requirements of a VPN include data storage, client VPN software, VNP aware routers and firewalls, and a VPN dedicated server A.1 Wired or wireless LAN functions The VPN will allow customers to connect securely with sales reps, accouting/billing, or customer service. Clients will be able to access their file accounts, order history, profile and payment methods. Text information will be available and videos will be available for product demonstrations and other marketing related items. Employees will have full access to their accredited software and network locations from any geographic location. Employees will have access to email, instant messaging and video conferencing capabilities A.2 Wired or wireless LAN link and device requirements DSL for voice, data and voice/data. C10 Communications ADSL filter splitter CAT 5 cabling 4 ASUS RT-AC87U Routers (two for ISP, two for VPN) 6 Servers: Data, proxy, communiCISCO VPN 3002cation, application, VPN, backup A.3 Wired or wireless LAN bandwidth and performance requirements 30 concurrent VPN connections desired, so bandwidth requirements will require at least 10Mbps B. Backbone network (if applicable) It may be possible that a MPLS VPN backbone network would be required, however the business would first need a complete evaluation. I would assume at this point, it would NOT be needed, but should be in the short term strategic plan to accommodate for business growth. Conclusion MIS589 Project Milestone 4 Network Requirements 3 WAN and Internet (Name of your service) (Name of your company or business) Prepared by: (Your Name) Date: Approved by: Summary of WAN and Internet requirements for the proposed network (max 200 words) A.1 Need for WAN connectivity A.2 Traffic through the WAN A.3 Possible WAN options A.4 Explain your choice for WAN service B.1 Role of Internet in your network Pro and cons of using Internet in business Conclusion MIS589 Project Milestone 5 Network Security Inventory of Assets Asset Importance Most Important Security Requirement Description Owner(s) MIS589 Project Milestone 5 Network Security Threat Scenario Asset Asset Importance Threat Description Likelihood Impact on Confidentiality Integrity Availability Impact Area Priority Impact Score Financial Productivity Reputation Legal Impact Score Risk Score (likelihood x Impact Score) Risk Control Strategy Accept Mitigate Share Defer Risk Mitigation Controls [Show More]
Last updated: 1 year ago
Preview 1 out of 13 pages
.png)
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Feb 16, 2022
Number of pages
13
Written in
Additional information
This document has been written for:
Uploaded
Feb 16, 2022
Downloads
0
Views
58







.png)