Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 3 and 4 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 3 and 4 Exam. 30 Q&A
Document Content and Description Below
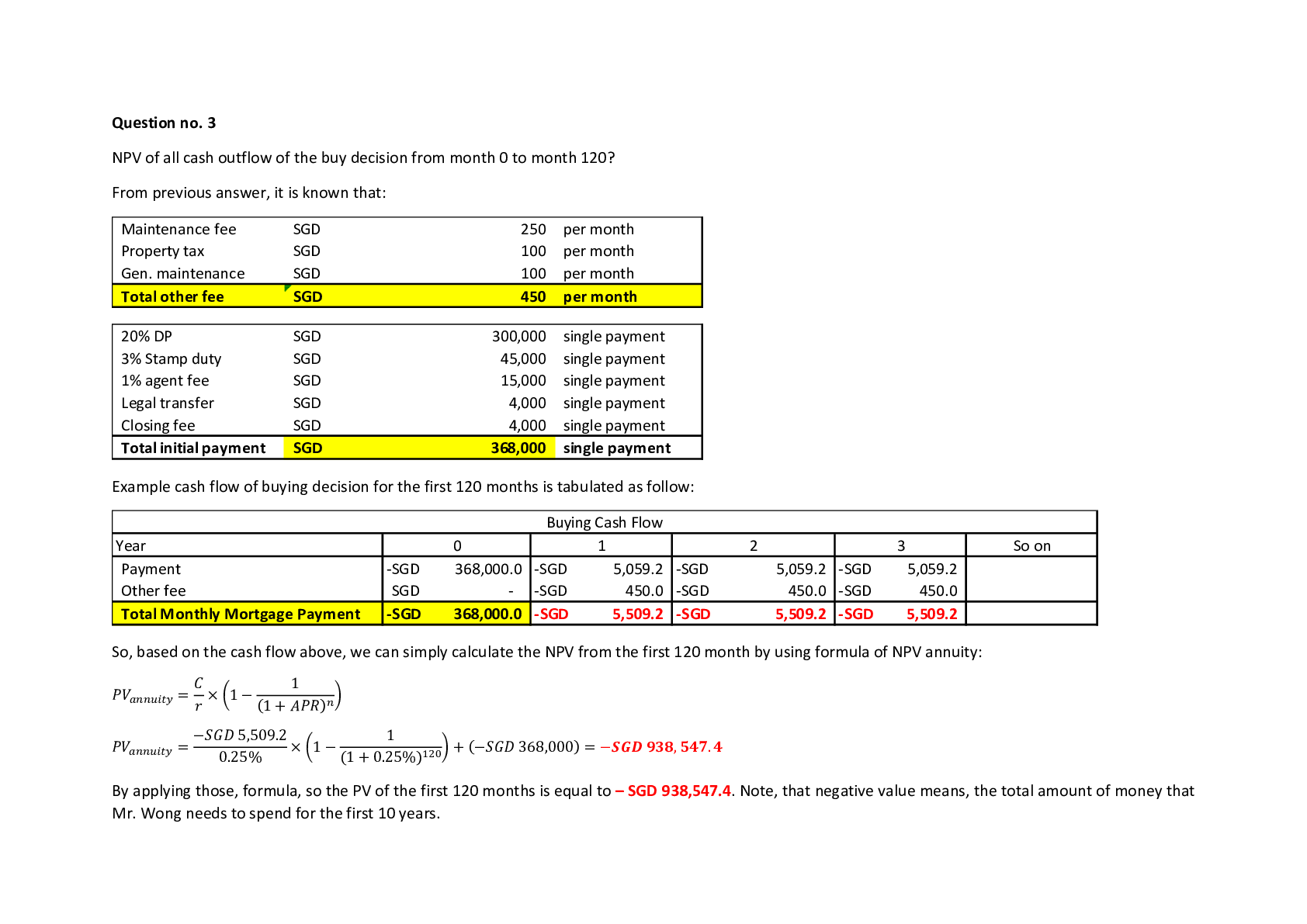
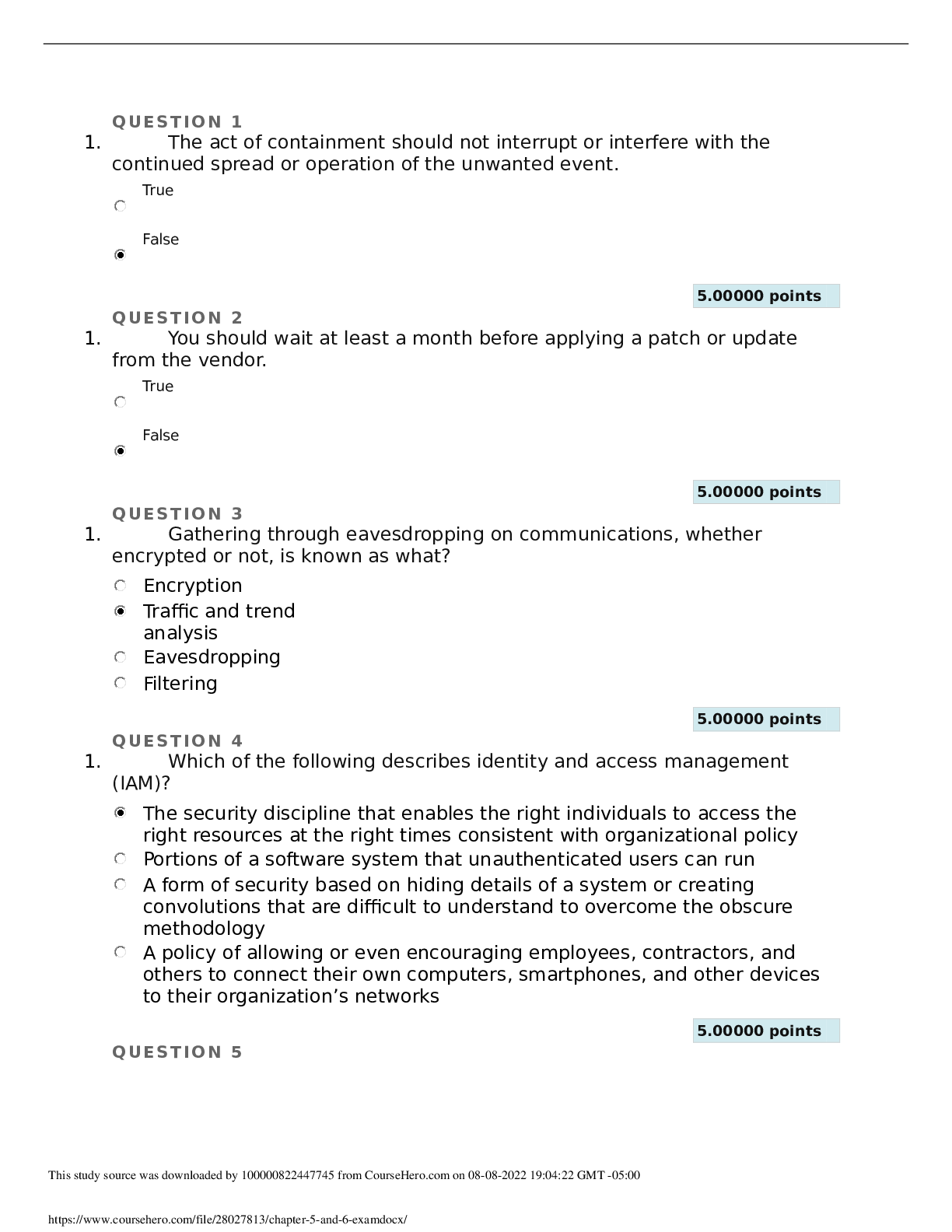
QUESTION 1 1. Which of the following refers to a logical division of data composed of one or more sectors on a hard drive? Boot sector Cluster Buffer Honeypot 5.00000 points QUESTION 2 1. MT... TF is a file format developed by Microsoft commonly used on Windows systems; it offers file security, large volume size, large file size, and alternate data streams (ADS). True False 5.00000 points QUESTION 3 1. Which term describes encryption that protects only the original IP packet's payload? Tunnel mode encryption Transport mode encryption Cryptography IP headers 5.00000 points QUESTION 4 1. Which term describes a form of security defense that focuses on discouraging a perpetrator with physical harm, social disgrace, and legal consequences? Buffer overflow Firewall Deterrent Dumpster diving 5.00000 points QUESTION 5 1. If you have been presented false credentials or you have been lured to an attack site, you might have been a victim of a phishing attack. True False 5.00000 points QUESTION 6 1. Which of the following characteristics describes an edge router? The last device owned and controlled by an organization before an ISP or telco connection A form of VPN establishing a secure VPN over trusted VPN connections A form of cryptography in which each encryption key is used once before being discarded A security service that ensures that a sender cannot deny sending a message 5.00000 points QUESTION 7 1. Scanning refers to the act of probing a network using custom crafted packets to determine the IP addresses in use and whether ports are open or closed. True False 5.00000 points QUESTION 8 1. Which of the following describes covert channel? A criminal whose objective is to compromise IT infrastructures. A method of discovering wireless networks by moving around a geographic area with a detection device. A tactic of pursuing and extracting information for the purpose of making a sale or performing a social engineering attack. An unknown, secret pathway of communication. 5.00000 points QUESTION 9 1. Which of the following characteristics relates to a distributed Denial of Service (DDoS) attack? The information related to the owners and managers of a domain name accessed through the domain registrar’s Web sites and Whois lookups An advancement of keystroke logging to monitor and record many other user activities An attack that uses multiple remotely controlled software agents disseminated across the Internet An attack that occurs on the logical division of a hard drive that can be formatted with a file system 5.00000 points QUESTION 10 1. A script kiddie is an experienced hacker who uses his or her own tools or scripts. True False 5.00000 points QUESTION 11 1. Which of the following refers to a communication pathway, circuit, or frequency dedicated or reserved for a specific transmission? Hardware VPN Host-to-site VPN Asymmetric cryptography Channel 5.00000 points QUESTION 12 1. Identity proofing is a form of authentication. True False 5.00000 points QUESTION 13 1. A VPN appliance can be placed inside and outside the corporate firewall. True False 5.00000 points QUESTION 14 1. Which of the following characteristics relates to the term algorithm? A hardware VPN device A VPN created between two individual hosts across a local or intermediary network Used to connect a remote or mobile host to a networked office workstation A set of rules and procedures—usually mathematical in nature—that can define how the encryption and decryption processes operate 5.00000 points QUESTION 15 1. A rootkit describes a form of malware that hackers can upload and deploy on a target system; it often replaces multiple components of the host operating system with altered code. True False 5.00000 points QUESTION 16 1. Which of the following describes a banner? A message sent by a service in response to a valid or invalid query. Its function is to confirm communication is functioning properly or to announce an error. A form of unauthorized access to a system. Persistent public messaging forums accessed over the Network News Transfer Protocol (NNTP). A variant of the UNIX operating system that is supported by Windows NT 4.0, but not subsequent version of Windows. 5.00000 points QUESTION 17 1. Redundant array of independent disks (RAID) is a disk set management technology that gains speed and fault tolerance. True False 5.00000 points QUESTION 18 1. A technique for securing a data exchange or verifying identity is through out of band communication, which uses an alternative route, mechanism, or pathway. True False 5.00000 points QUESTION 19 1. The term XSS refers to the largest amount of data that a datagram can hold based on the limitations of the networking devices managing a given segment. True False 5.00000 points QUESTION 20 1. Which term describes the seemingly random and unusable output from a cryptographic function applied to original data? Dedicated leased line Ciphertext Identity proofing Host VPN Which name is given to a VPN created between a client and a server either within the same local network or across a WAN link or intermediary network to support secure client interaction with the services of a resource host? Site-to-site VPN Software VPN Client-to-server VPN Keyspace Which of the following refers to the malicious insertion of scripting code onto a vulnerable Web site? Insertion attack Upstream filtering Keystroke logger Cross-site scripting (XSS) Which name is given to a rogue program that automatically dials a modem to a pre-defined number to auto-download additional malware to the victim or to upload stolen data from the victim? Adwar e Sector Spywar e Dialer When a communication exchange that does not verify the identity of the endpoints of a communication and accepts any properly formed response as valid, a non-authenticating query service is in use. True False A dedicated connection is always off and available for immediate transmission of data only when there is an emergency. True False Rekeying triggers the generation of a new symmetric encryption key and secure exchange of that key. True False When too much data crosses a network segment, throughput and latency are increased. True False Which term is a form of exploitation in which an unauthorized or rogue DNS server responds to DNS queries with false resolutions? DNS poisoning DNS spoofing Banner grabbing Dumpster diving Which of the following us an intentional discharge made to damage or destroy electronic equipment ranging from cell phones to computers and servers? Session hijacking Virus Intentional electromagnetic interference (IEMI) Chip creep Which of the following terms describes hiding information from unauthorized third parties? Virtual Private Network (VPN) Split tunnel Cryptography Authentication, Authorization, and Accounting (AAA) Services Fragmentation occurs when a dataset is too large for maximum supported size of a communication container, such as a segment, packet, or frame. The original dataset divides into multiple sections or fragments for transmission across the size-limited medium, and then reassembles on the receiving end. True False Hackers can be deterred by defense methods that detect and evade. All of the following are defense methods, except which one? Honeypot s Firewalls IDSs Botnet army 1. What is compression? A VPN used to grant outside entities access into a perimeter network; used to host resources designated as accessible to a limited group of external entities, such as business partners or suppliers, but not the general public A subset of asymmetric cryptography based on the use of key pair sets The art and science of hiding information from unauthorized third parties Removal of redundant or superfluous data or space to reduce the size of a data set Which term is used to describe a feature added to the NTFS file system to support files from POSIX, OS/2, and Macintosh? Deterrent Adware Hierarchical file system (HFS) Alternate data stream (ADS) VPNs increase the risk caused by insecure access locations and prevent interaction with LAN resources. Answer s: Fals e [Show More]
Last updated: 1 year ago
Preview 1 out of 8 pages
Instant download
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
8
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
95












 Mod 1, 2, 3 and 4 Quiz, All Correct Answers with Explanations (Latest 2021) All Correct Study Guide, Download to Score A.png)
 All Correct Study Guide, Download to Score A.png)