Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 5 and 6 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 5 and 6 Exam. 20 Q&A
Document Content and Description Below
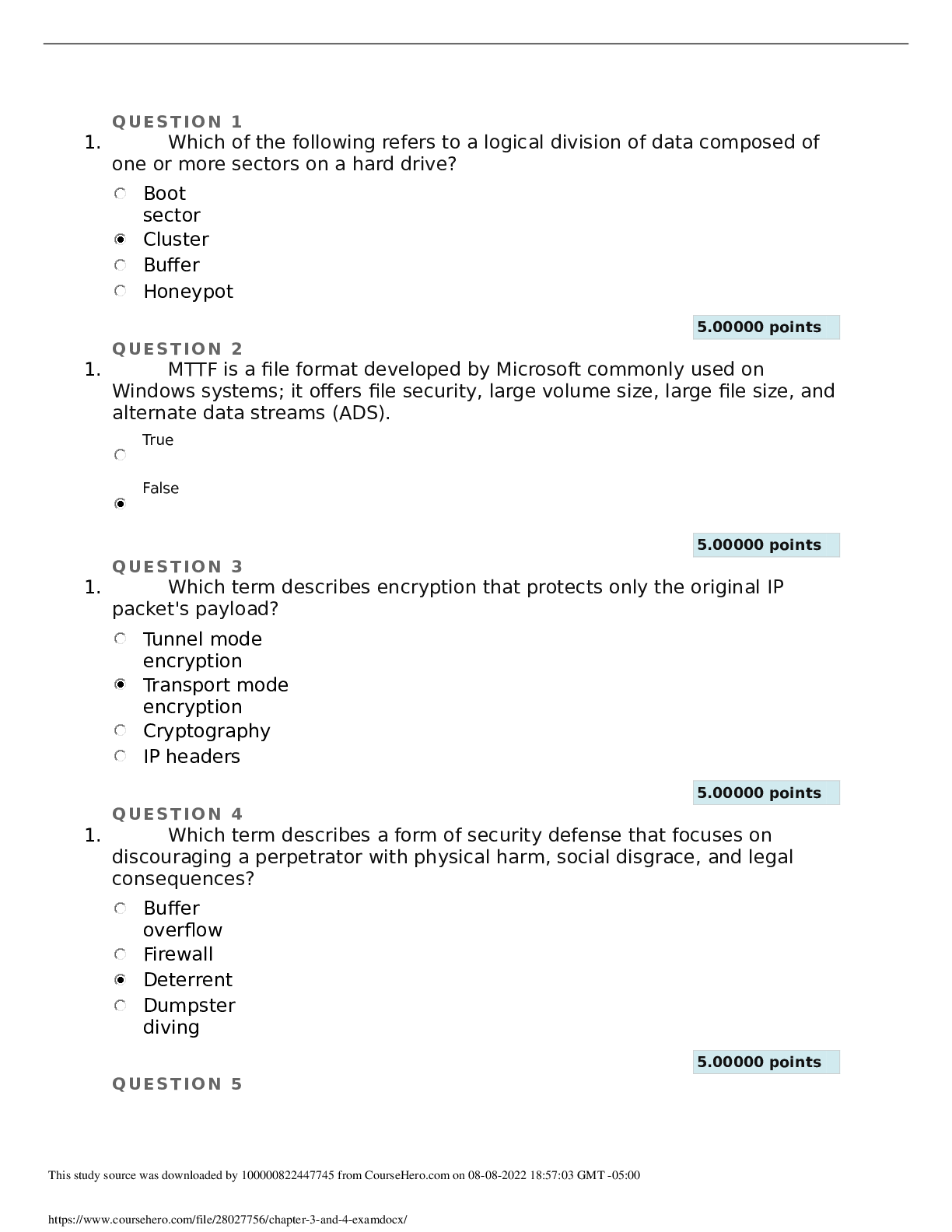
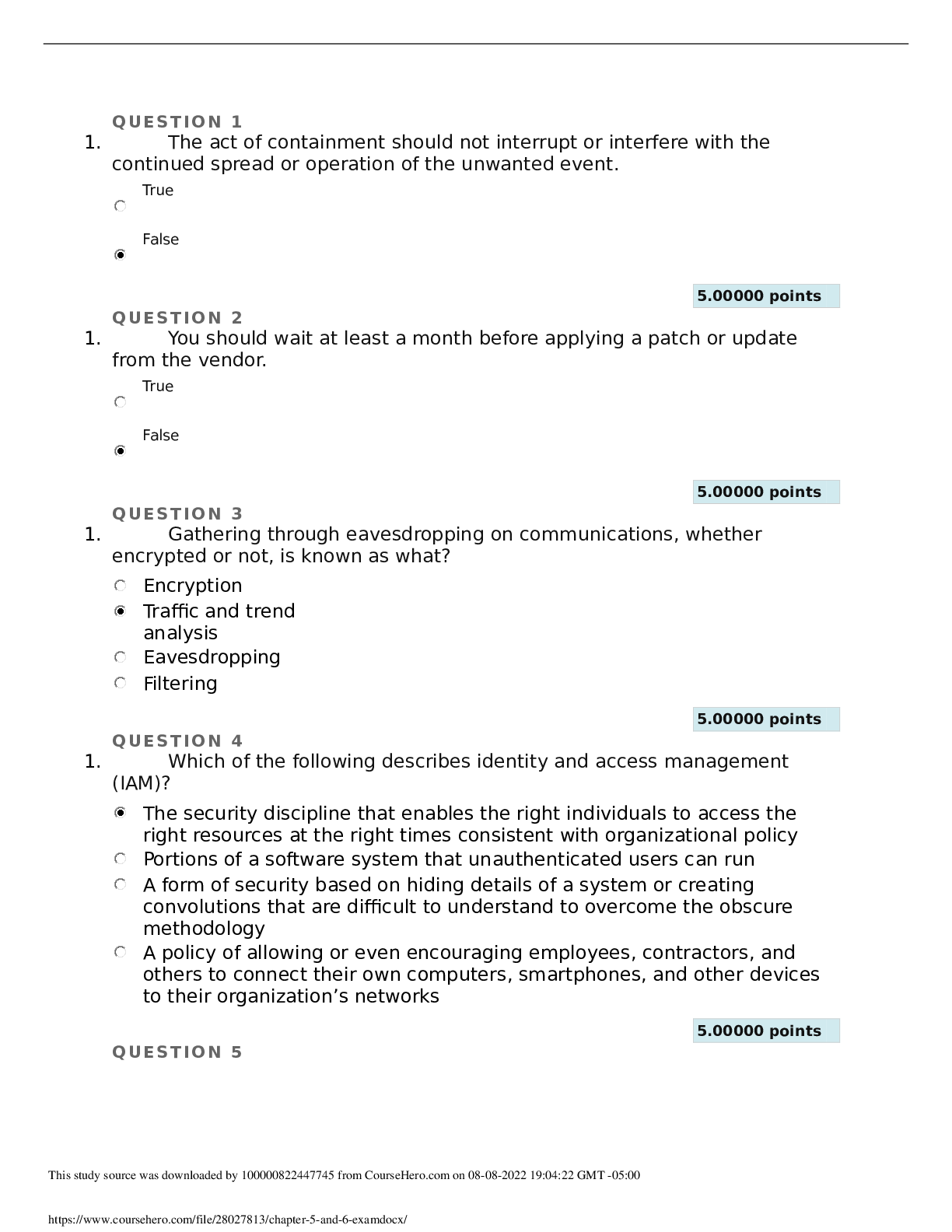
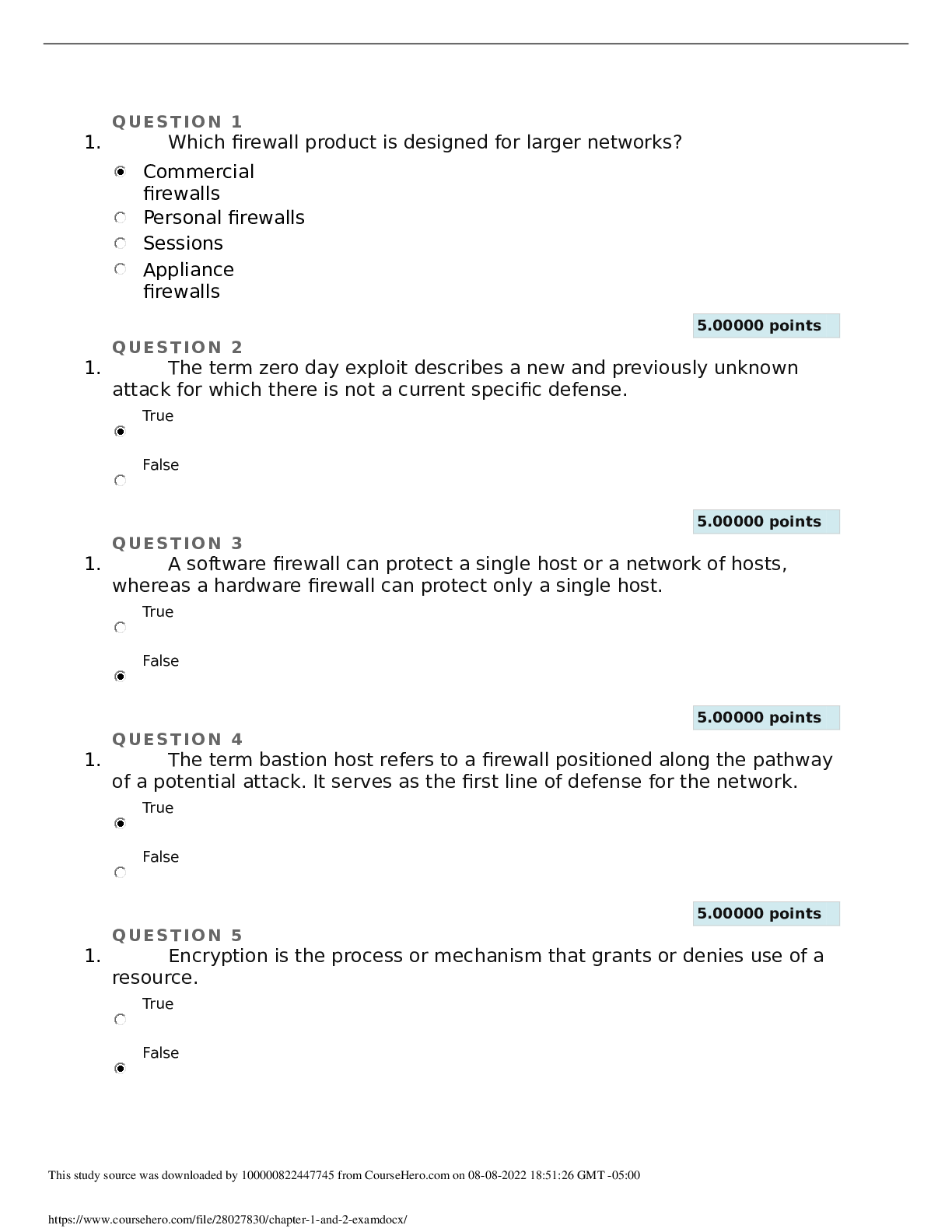
QUESTION 1 1. The act of containment should not interrupt or interfere with the continued spread or operation of the unwanted event. True False 5.00000 points QUESTION 2 1. You should wait at l... east a month before applying a patch or update from the vendor. True False 5.00000 points QUESTION 3 1. Gathering through eavesdropping on communications, whether encrypted or not, is known as what? Encryption Traffic and trend analysis Eavesdropping Filtering 5.00000 points QUESTION 4 1. Which of the following describes identity and access management (IAM)? The security discipline that enables the right individuals to access the right resources at the right times consistent with organizational policy Portions of a software system that unauthenticated users can run A form of security based on hiding details of a system or creating convolutions that are difficult to understand to overcome the obscure methodology A policy of allowing or even encouraging employees, contractors, and others to connect their own computers, smartphones, and other devices to their organization’s networks 5.00000 points QUESTION 5 1. Checking authentication, checking authorization and access control, auditing systems, and verifying firewalls and other filters should all be included on which of the following? A physical security checklist A whitelist A response plan A logical security checklist 5.00000 points QUESTION 6 1. Trusted Platform Module (TPM) is a dedicated microchip found on some motherboards; it hosts and protects the encryption key for whole hard drive encryption. True False 5.00000 points QUESTION 7 1. Which of the following describes AppleTalk? A legacy protocol used in networks hosting mainly Macintosh computers A policy that allows employees, contractors, and others to connect their own computers, smartphones, and other devices to their organizations’ networks An application-programming interface (API) developed by IBM in 1985 to emulate NetBIOS on a token ring network An Application Layer protocol used by e-mail clients to receive messages from an e-mail server 5.00000 points QUESTION 8 1. Which of the following determines the available vendor patches that are installed or missing? Vulnerability scan Configuration scan Penetration test Post-mortem assessment 5.00000 points QUESTION 9 1. Single-factor authentication uses a single element of validation or verification to prove the identity of a subject, and it is considered much stronger than multi-factor authentication. True False 5.00000 points QUESTION 10 1. Telnet is a protocol and a service used to remotely control or administer a host through a plaintext command-line interface. True False 5.00000 points QUESTION 11 1. What prevents a hard drive from being read by another system if it is stolen? Whole hard drive encryption Host firewall Antivirus scanner Intrusion detection system (IDS) 5.00000 points QUESTION 12 1. Penetration testing involves the application of hacking techniques, methodology, and tools; ethical security experts conduct penetration testing. True False 5.00000 points QUESTION 13 1. Patch management watches for the release of new updates from vendors, tests the patches, obtains approval, and then oversees the deployment and implementation of updates across the production environment. True False 5.00000 points QUESTION 14 1. Time, money, and effort already spent on a project, event, or device make up its sunk cost. True False 5.00000 points QUESTION 15 1. It is a mistake to use remote system and device management mechanisms that are convenient but not secure, such as telnet, HTTP, and FTP. True False 5.00000 points QUESTION 16 1. Which protocol and a data exchange system commonly used over TCP/IP networks, including the Internet, is unencrypted and performs authentication and data transfer in plaintext? Post Office Protocol (POP) AppleTalk File Transfer Protocol (FTP) Hyper Text Transfer Protocol (HTTP) 5.00000 points QUESTION 17 1. Organizations are usually not aware of when compliance auditing is a mandated periodic occurrence, so preparation is challenging and often not possible. True False 5.00000 points QUESTION 18 1. Which form of investigation aims at checking whether or not a target system is subject to attack based on a database of tests, scripts, and simulated exploits? Incident response plan Fail-open Vulnerability scanning Separation of duties 5.00000 points QUESTION 19 1. SMTP is an Application Layer protocol used by e-mail clients to send messages to an e-mail server and is also used to relay messages between email servers. True False 5.00000 points QUESTION 20 1. Which term describes a form of security based on hiding details of a system, or creating convolutions that are difficult to understand? Firewall Bring Your Own Device (BYOD) Modeling Security through obscurity [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages
Instant download
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
60











.png)
 All Correct Study Guide, Download to Score A.png)