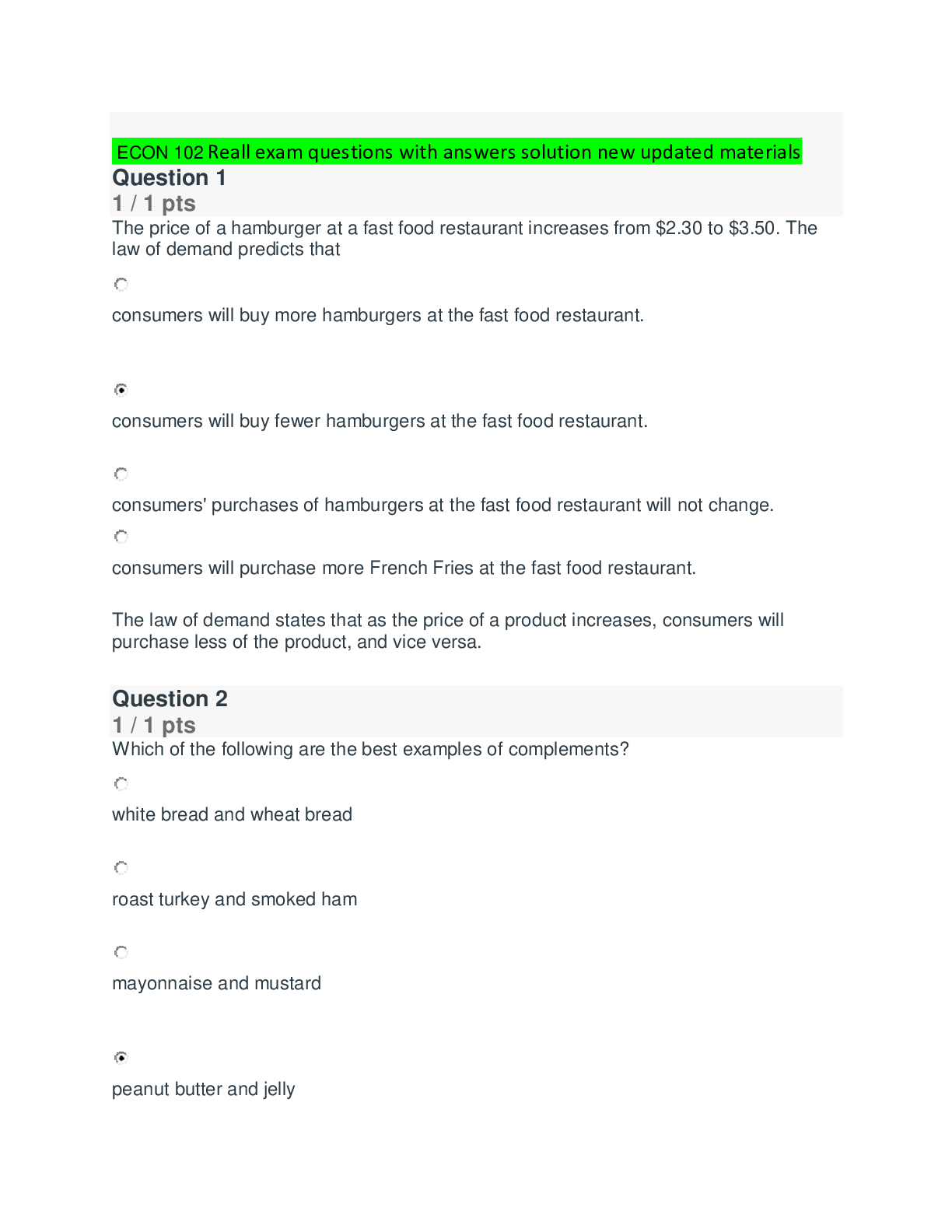
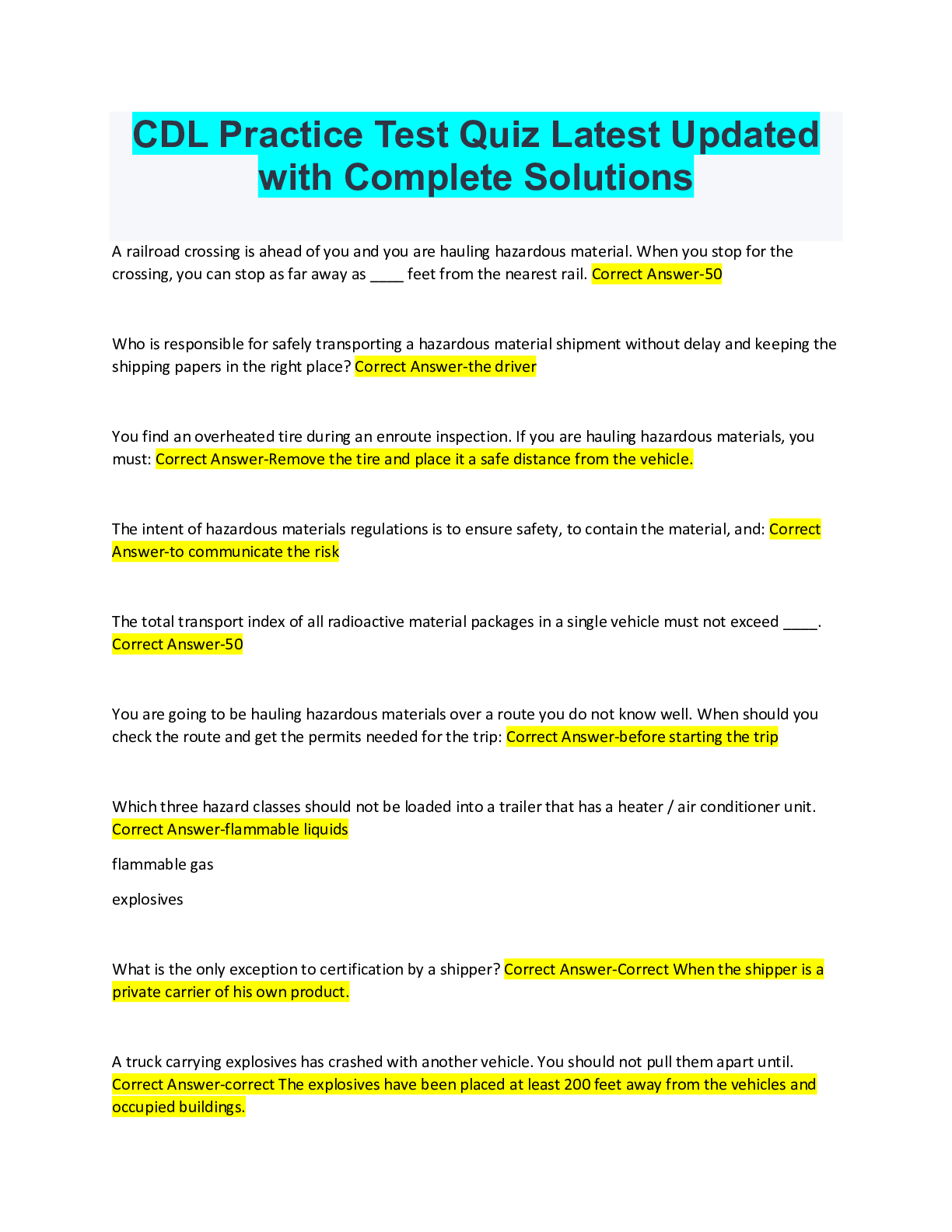
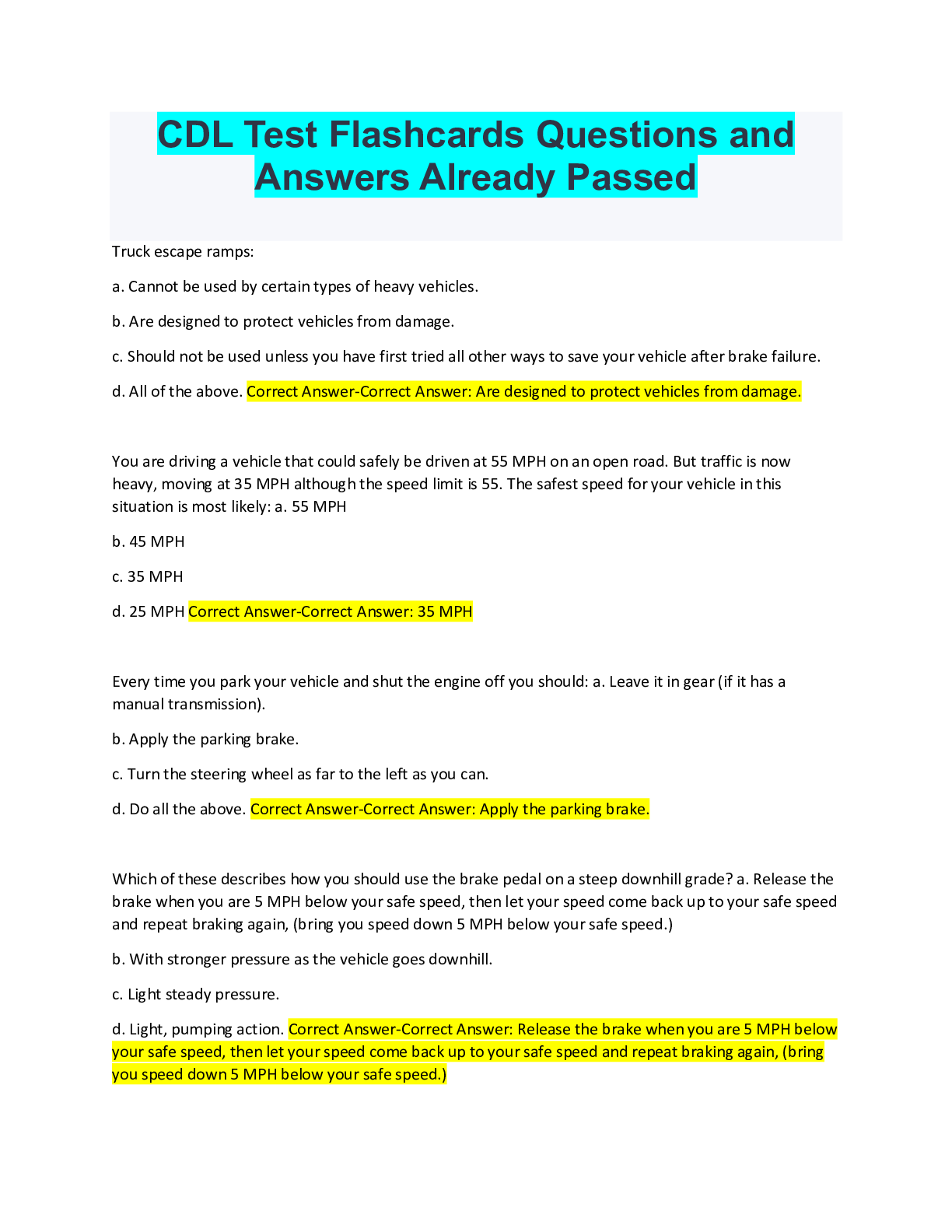
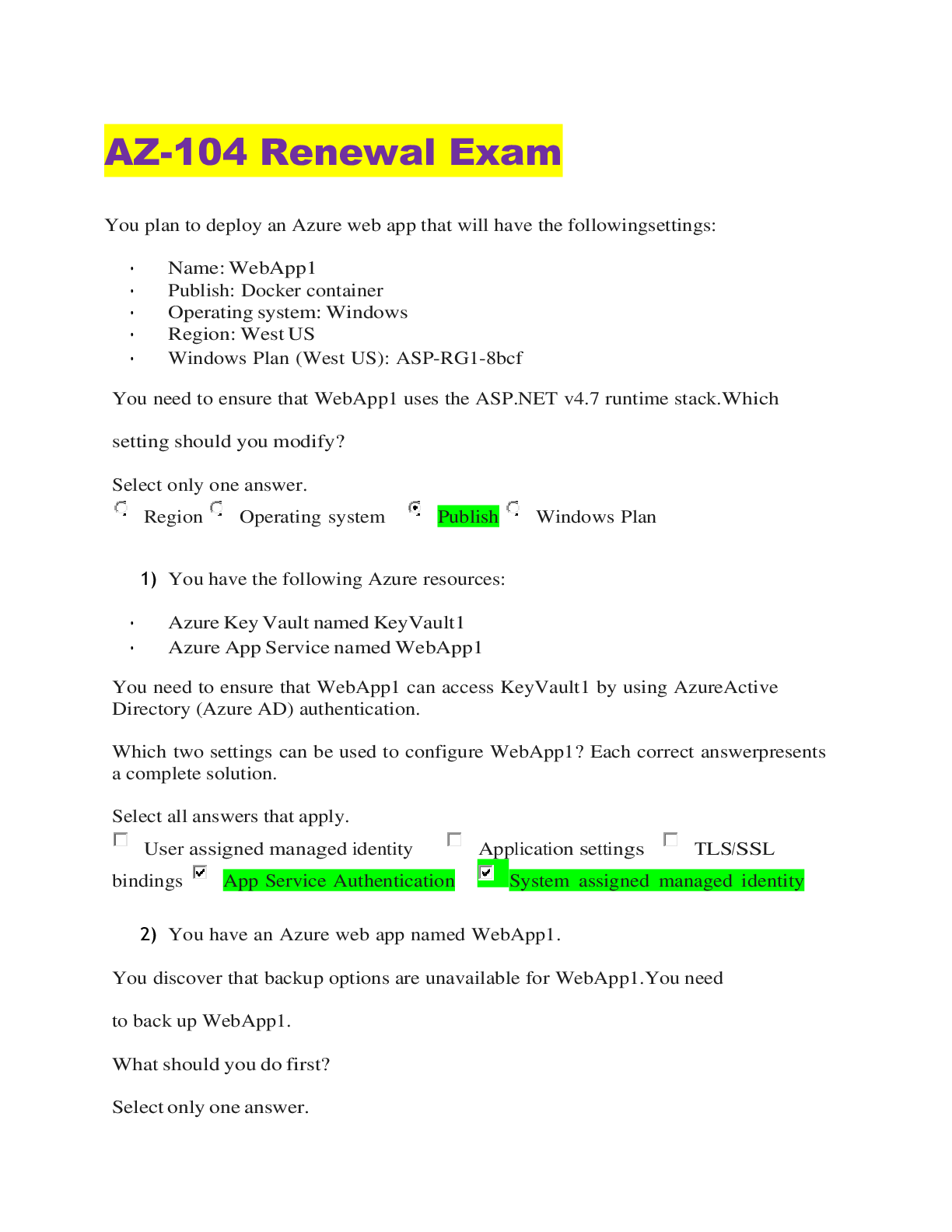
Computer Science > QUESTIONS & ANSWERS > SY0-601 Final Exam Questions with Complete Solutions (All)
SY0-601 Final Exam Questions with Complete Solutions
Document Content and Description Below
SY0-601 Final Exam Questions with Complete Solutions Which of the following will MOST likely adversely impact the operations of unpatched traditional programmable-logic controllers, running a back-... end LAMP server and OT (operational technology) systems with human-management interfaces that are accessible over the Internet via a web interface? (Choose two.) -Answer- A. Cross-site scripting B. Data exfiltration C. Poor system logging D. Weak encryption E. SQL injection F. Server-side request forgery Answer: D,F A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants to ensure it does not happen again. Which of the following should the IT administrator do FIRST after recovery? in order to prevent future ransomware attack against a file server_______ -Answer- A. Scan the NAS (network attached storage) for residual or dormant malware and take new daily backups that are tested on a frequent basis B. Restrict administrative privileges and patch ail systems and applications. C. Rebuild all workstations and install new antivirus software D. Implement application whitelisting and perform user application hardening Answer: A An attacked is attempting to exploit users by creating a fake website with the URL www.validwebsite.com. The attacker's intent is to imitate the look and feel of a legitimate website to obtain personal information from unsuspecting users. Which of the following social-engineering attacks does this describe? Social engineering attack that exploits the user by creating a fake website which resembles the legitimate website is called_____ -Answer- A. Information elicitation B. Typo squatting C. Impersonation D. Watering-hole attack Answer: D Which of the following is a team of people dedicated testing the effectiveness of organizational security programs by emulating the techniques of potential attackers? a team of people dedicated to testing the effectiveness of organizational security programs by emulating the techniques of potential attackers_____ -Answer- A. Red team B. While team C. Blue team D. Purple team Answer: A To reduce costs and overhead, an organization wants to move from an on-premises email solution to a cloud-based email solution. At this time, no other services will be moving. Which of the following cloud models would BEST meet the needs of the organization? movements from on premises email solution to cloud based email solution_____ -Answer- A. MaaS B. laaS C. SaaS D. PaaS {platform as a service/ cloud platform service} Answer: D A security engineer at an offline government facility is concerned about the validity of an SSL (secure socket layer) certificate. The engineer wants to perform the fastest check with the least delay to determine if the certificate has been revoked. Which of the following would BEST these requirement? in order to check the validity of the secure socket layer certificate or any type of certificates ______ -Answer- A. RA B. OCSP C. CRL {certificate revocation list} D. CSR Answer: C A security analyst needs to complete an assessment. The analyst is logged into a server and must use native tools to map services running on it to the server's listening ports. Which of the following tools can BEST accomplish this talk? in order to map the services that are running on the server and the services running from the server to the server's listening port: use_____ -Answer- A. Netcat B. Netstat- Network and statistic {a command that is used to check the operation of local ports and to see if the ports are configured properly and if they are receiving data: incoming and outgoing connections, routing tables, port listening, and usage statistics} C. Nmap D. Nessus Answer: B [Show More]
Last updated: 1 year ago
Preview 1 out of 64 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$11.00
Document information
Connected school, study & course
About the document
Uploaded On
Aug 26, 2022
Number of pages
64
Written in
Additional information
This document has been written for:
Uploaded
Aug 26, 2022
Downloads
0
Views
123











.png)






.png)

 ANSWERS.png)