Medicine > QUESTIONS & ANSWERS > WGU Master's Course C701 - Ethical Hacking with Complete Solution (All)
WGU Master's Course C701 - Ethical Hacking with Complete Solution
Document Content and Description Below
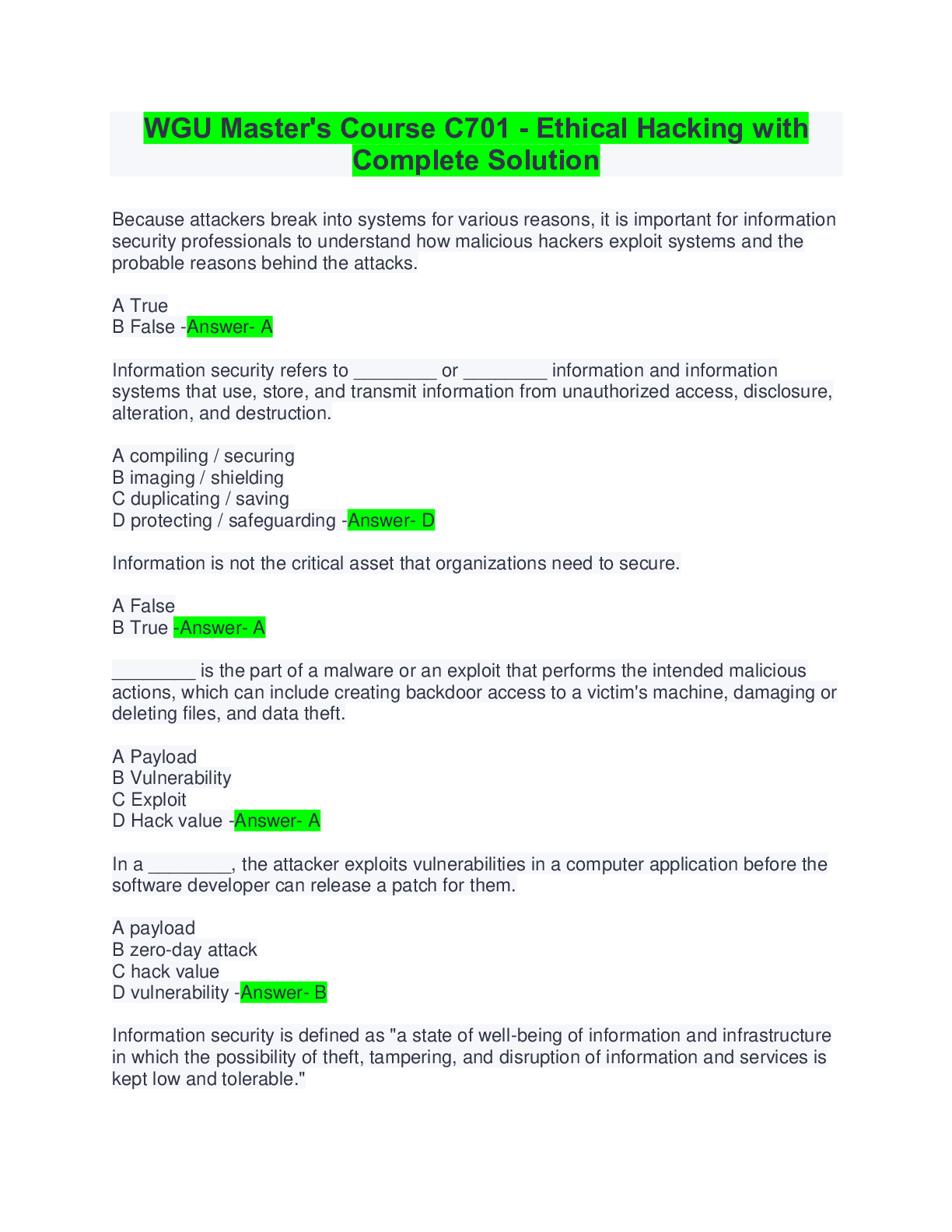
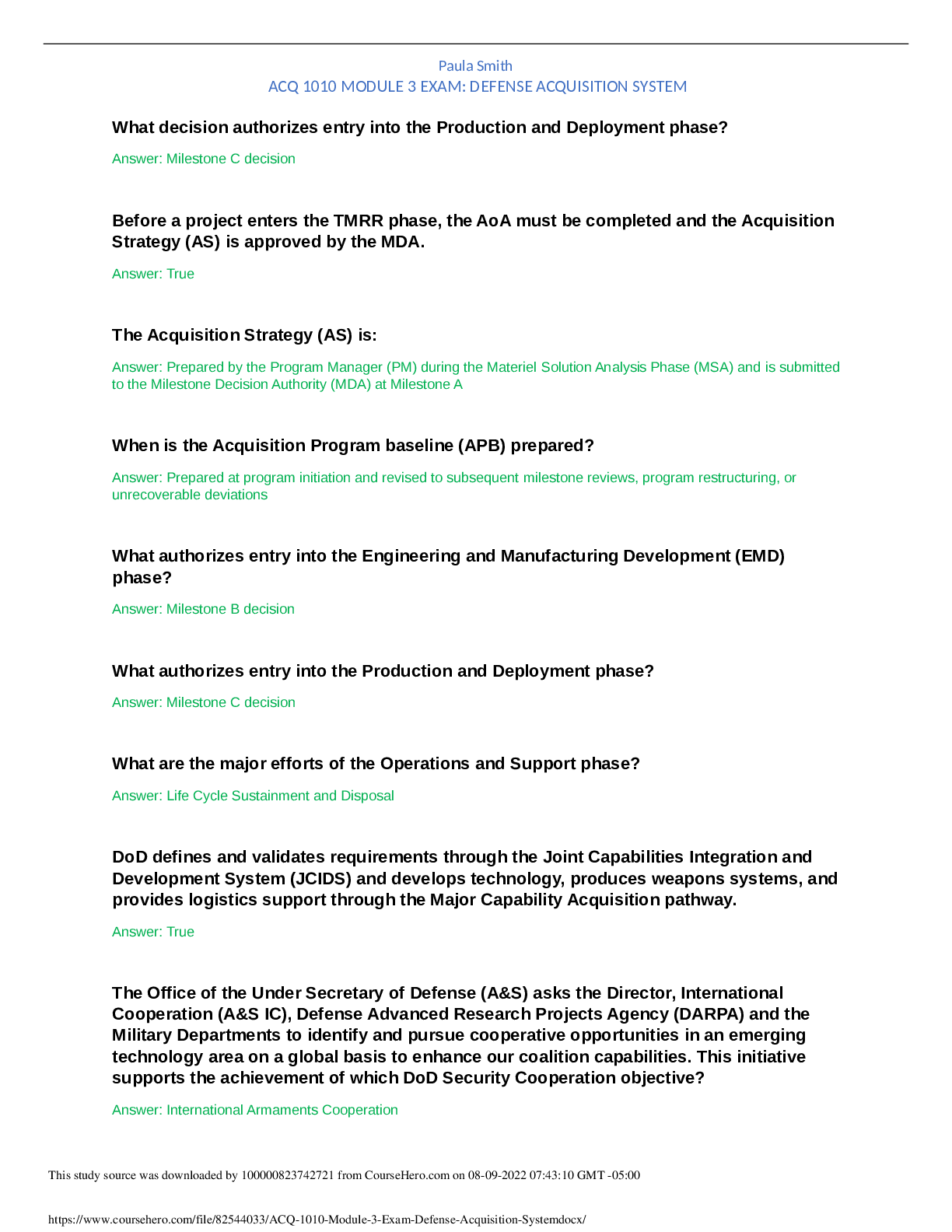
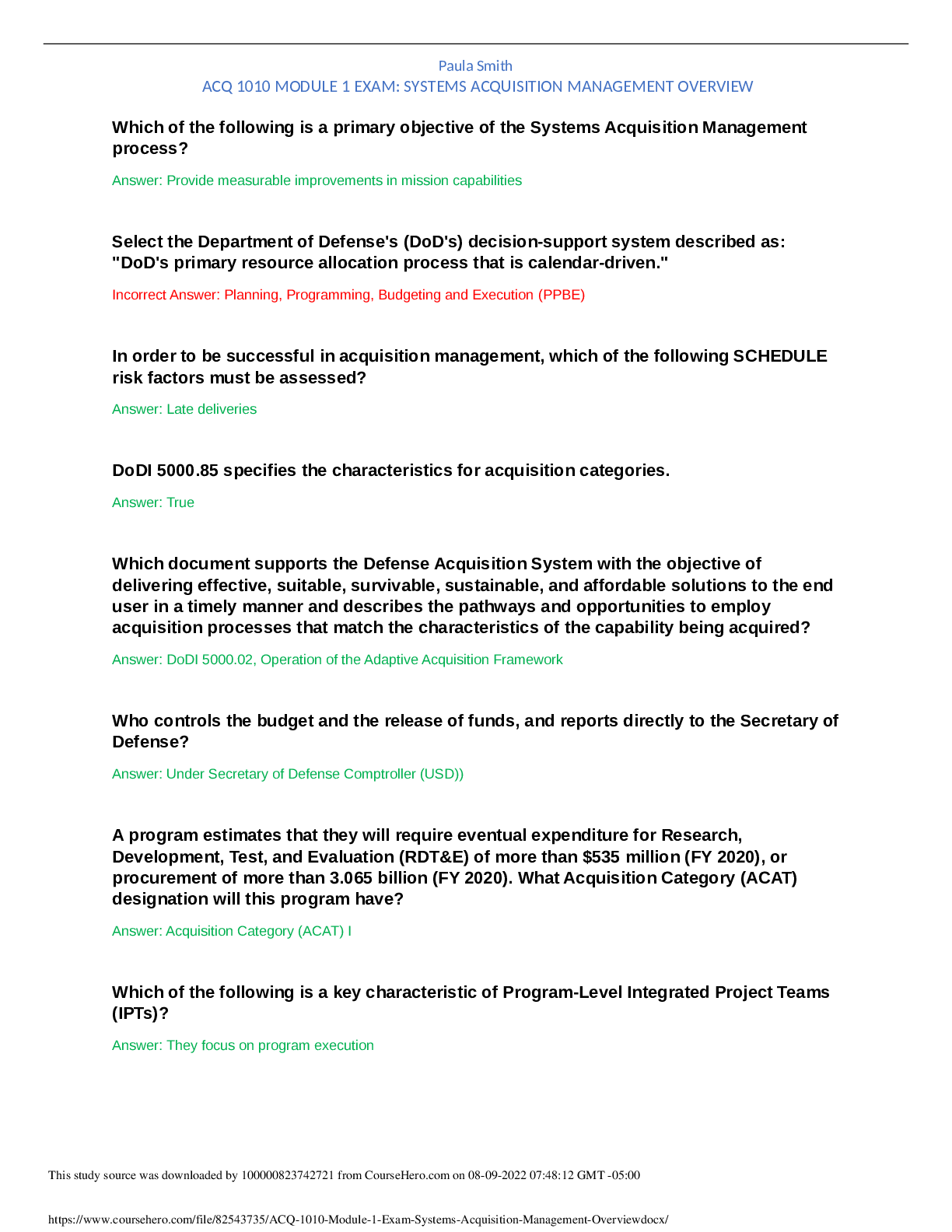
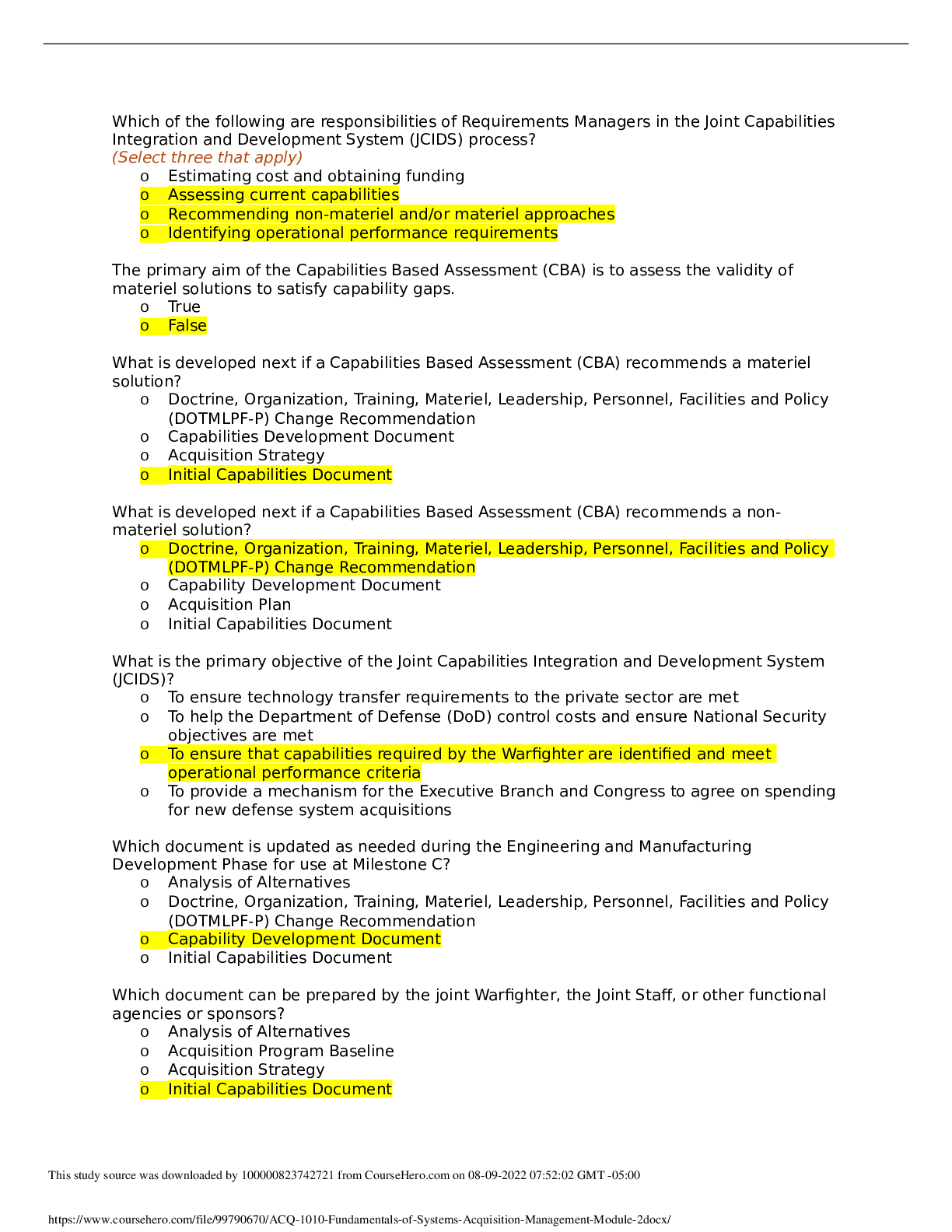
WGU Master's Course C701 - Ethical Hacking with Complete Solution Because attackers break into systems for various reasons, it is important for information security professionals to understand how ... malicious hackers exploit systems and the probable reasons behind the attacks. A True B False -Answer- A Information security refers to ________ or ________ information and information systems that use, store, and transmit information from unauthorized access, disclosure, alteration, and destruction. A compiling / securing B imaging / shielding C duplicating / saving D protecting / safeguarding -Answer- D Information is not the critical asset that organizations need to secure. A False B True -Answer- A ________ is the part of a malware or an exploit that performs the intended malicious actions, which can include creating backdoor access to a victim's machine, damaging or deleting files, and data theft. A Payload B Vulnerability C Exploit D Hack value -Answer- A In a ________, the attacker exploits vulnerabilities in a computer application before the software developer can release a patch for them. A payload B zero-day attack C hack value D vulnerability -Answer- B Information security is defined as "a state of well-being of information and infrastructure in which the possibility of theft, tampering, and disruption of information and services is kept low and tolerable." A False B True -Answer- B Information security relies on four major elements: confidentiality, integrity, availability, and authenticity. A True B False -Answer- B ________ is the assurance that the information is accessible only to those authorized to have access. A Availability B Confidentiality C Authenticity D Integrity -Answer- B Confidentiality controls include data classification, data encryption, and proper equipment disposal. A False B True -Answer- B ________ is trustworthiness of data or resources in the prevention of improper and unauthorized changes—the assurance that information is sufficiently accurate for its purpose. A Confidentiality B Availability C Authenticity D Integrity -Answer- D Measures to maintain data integrity may include a checksum and access control. A False B True -Answer- B ________ is the assurance that the systems responsible for delivering, storing, and processing information are accessible when required by authorized users. A Integrity B Confidentiality C Availability D Authenticity -Answer- C Measures to maintain data availability do not include redundant systems' disk array and clustered machines, antivirus software to stop worms from destroying networks, and distributed denial-of-service (DDoS) prevention systems. A True B False -Answer- B [Show More]
Last updated: 1 year ago
Preview 1 out of 90 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Sep 22, 2022
Number of pages
90
Written in
Additional information
This document has been written for:
Uploaded
Sep 22, 2022
Downloads
0
Views
85








.png)





.png)