Business > EXAM > Qualys Vulnerability Management Self-Paced Training 50 Questions with Verified Answers,100% CORRECT (All)
Qualys Vulnerability Management Self-Paced Training 50 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
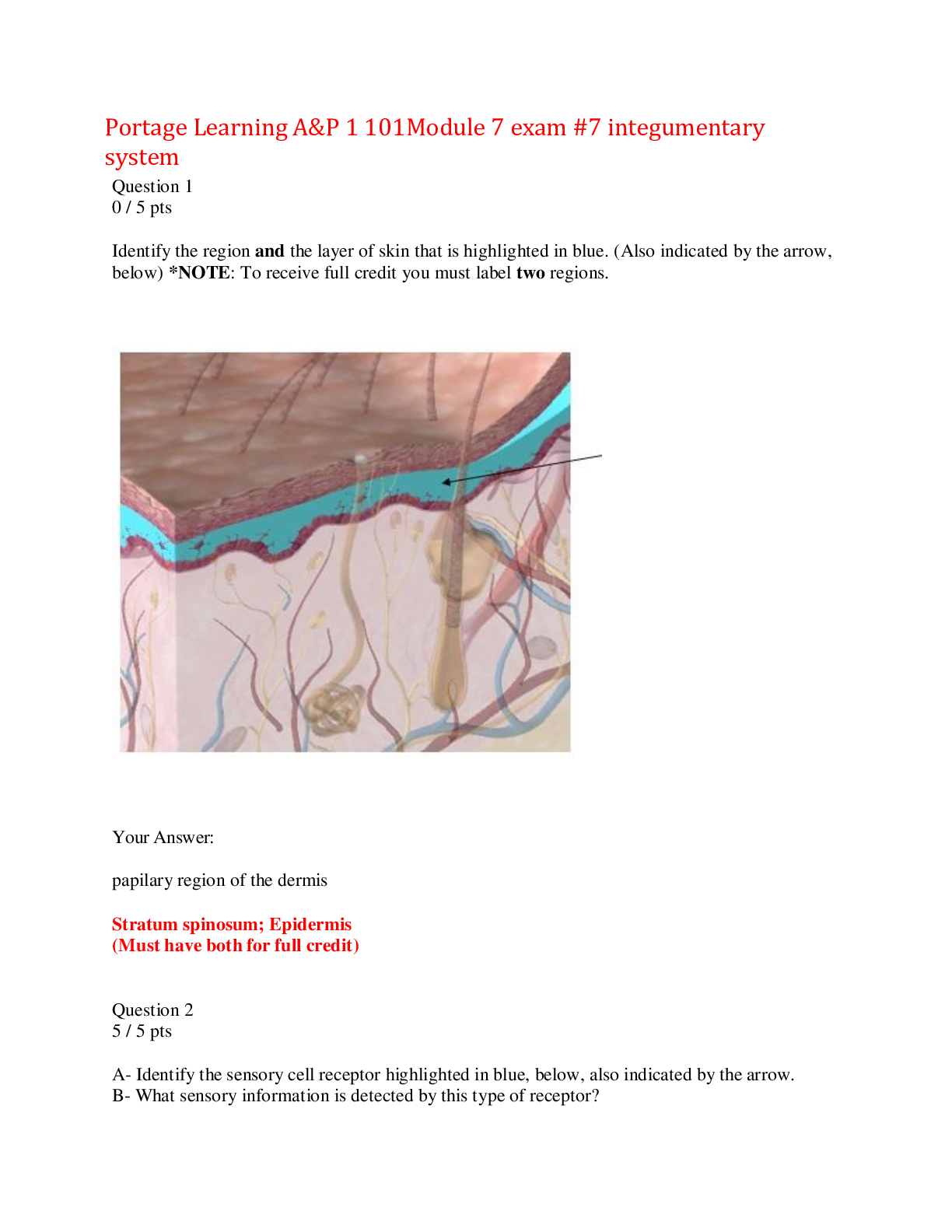
Qualys Vulnerability Management Self-Paced Training 50 Questions with Verified Answers List the default tracking methods available for adding assets to your "scanning" subscription. (Select Thr... ee) (A) DNS Name (B) NetBIOS Name (C) CVE ID (D)Qualys Host ID (E) IP AddressCORRECT ANSWER (A) DNS Name (B) NetBIOS Name (E) IP Address Name the phase or step of the Qualys Vulnerability Management Lifecycle that produces scan results containing vulnerability findings? (A) Report (B) Discover (C) Remediate (D) AssessCORRECT ANSWER (D) Assess Which of the following is the default tracking method used by Qualys Cloud Agents? (A) IP Address (B) Qualys Host ID (C) DNS Name (D) NetBIOS NameCORRECT ANSWER (B) Qualys Host ID Which of the following are phases of the Vulnerability Management Lifecycle? (A) Maintenance (B) Remediate (C) Design (D) Discover (E) ReportCORRECT ANSWER (B) Remediate (D) Discover (E) Report Name the type of scanner appliance (by default) available to all Qualys users with "scanning" privileges? (A) External (Internet-based) Scanner (B) Offline Scanner (C) Virtual Scanner (D) Internal ScannerCORRECT ANSWER (A) External (Internet-based) Scanner Only the _________ user role can edit QIDs in your account KnowledgeBase. (A) Manager (B) Administrator (C) Scanner (D) Unit ManagerCORRECT ANSWER (A) Manager Potential vulnerabilities are automatically verified. (True/ False) (A) True (B) FalseCORRECT ANSWER (B) False A severity ____________ vulnerability is the most urgent. (A) Level 5 (B) Level 1 (C) Level 2 (D) Level 4CORRECT ANSWER (A) Level 5 Which of the following criteria can be used to create a dynamic Search List? (Select Three). (A) Host Name (B) Severity Level (C) IP Address (D) CVE ID (E) CVSS ScoreCORRECT ANSWER (B) Severity Level (D) CVE ID (E) CVSS Score What is the name given to a custom list of QIDs taken from the Qualys KnowledgeBase? (A) Search List (B) Host Assets (C) Asset Group (D) Authentication RecordCORRECT ANSWER (A) Search List You have just created a Search List. Where can you use or apply it? (Select Three) (A) Report Template (B) Remediation Policy (C) Asset Group (D) Business Unit (E) Asset Tag (F) Option ProfileCORRECT ANSWER (A) Report Template (B) Remediation Policy (F) Option Profile A static Search List is created and updated ____________. (A) Manually (B) Explicit (C) By Default (D) AutomaticallyCORRECT ANSWER (A) Manually What are the primary methods available in Qualys VM, for grouping, labeling, and organizing host assets? (Select Two) (A) Severity Levels (B) Search Lists (C) Asset Groups (D) Asset TagsCORRECT ANSWER (C) Asset Groups (D) Asset Tags Which of the following options can be used to add assets to an Asset Group? (Select Three) (A) DNS name (B) MAC address (C) IP address (D) NetBIOS nameCORRECT ANSWER (A) DNS name (C) IP address (D) NetBIOS name Scans must be performed in "________________" mode to produce a list of installed software applications. (A) Authorized (B) Administrative (C) Temporary (D) AuthenticatedCORRECT ANSWER (D) Authenticated Why is it beneficial to configure the Business Impact of an Asset Group? (A) It's used to calculate Business Risk (B) It's used to calculate storage space (C) It's used to calculate Severity Levels (D) It's used to calculate CVSS ScoresCORRECT ANSWER (A) It's used to calculate Business Risk A "static" Asset Tag will adjust dynamically and automatically to changes made to your host assets. (True/False) (A) True (B) FalseCORRECT ANSWER (B) False The service creates some initial asset tags based on the existing objects (configurations) in your account. List those asset tags. (Select Four) (A) Asset Groups (B) Business Units (C) Malware Domaine Assets (D) Web Application Assets (E) Software InstalledCORRECT ANSWER (A) Asset Groups (B) Business Units (C) Malware Domaine Assets (D) Web Application Assets Which of the following is NOT a benefit or characteristic of Asset Tags? (A) Dynamically updated (B) Hierarchical organization (support nesting) (C) Helps to automate scanning and reporting tasks (D) Identifies the "Business Impact" of host assetsCORRECT ANSWER (D) Identifies the "Business Impact" of host assets A filtering device can impact the _______ ability to assess a host for vulnerabilities. (A) Scanner's (B) Agent's (C) Connector's (D) API'sCORRECT ANSWER (A) Scanner's Qualys Cloud Agent is installed as a local system service on each host as ___________ agent/agents per host. (A) Multiple (B) Zero (C) One (D) TwinCORRECT ANSWER (C) One You are building an Options Profile that targets "Zero Day" vulnerabilities. Which "Scan" option will allow you to use a "Zero Day" Search List to achieve this objective? (A) Password Brute Forcing (B) Additional Certificate Detection (C) Vulnerability Detection (D) TCP PortsCORRECT ANSWER (C) Vulnerability Detection Agents and Scanners can be combined to cater to the vulnerability assessment needs. (A) Correct (B) IncorrectCORRECT ANSWER (A) Correct The primary modules that collect the host configuration data are: (Select Four) (A) Porting Scanning (B) Operating System Detection (C) Service Detection (D) Network Scanning (E) Host DiscoveryCORRECT ANSWER (A) Porting Scanning (B) Operating System Detection (C) Service Detection (E) Host Discovery Which of the following sensors are presently used by Qualys VM to collect the data needed to perform host vulnerability assessments? (Select Two) (A) Cloud Connector (B) Scanner Appliance (C) Cloud Agent (D) Passive SensorCORRECT ANSWER (B) Scanner Appliance (C) Cloud Agent One of your "Scanner" users would like to perform a comprehensive scan (occasionally) that targets the maximum number of service ports. Which port scanning option do you recommend? (A) None (B) Standard Scan (C) Light Scan (D) FullCORRECT ANSWER (D) Full Which module does a Qualys Scanner Appliance load to determine the LIVE/DEAD status of targeted hosts? (A) Service Detection (B) OS Detection (C) Host Discovery (D) Port ScanningCORRECT ANSWER (C) Host Discovery Which of the following is NOT a valid target for launching a scan? (A) IP address (B) Search List (C) Asset Tag (D) Asset GroupCORRECT ANSWER (B) Search List To scan the IP addresses in your Qualys subscription you first need to add: (A) Scan Preferences (B) Host IPs (C) Asset Tag (D) Asset GroupCORRECT ANSWER (B) Host IPs It is a "best practice" to perform your assessment scans in "_____________" mode. (A) Authenticated (B) Authorized (C) Administrative (D) ScanningCORRECT ANSWER (A) Authenticated Which of the following are required to launch a vulnerability scan? (Select Three) (A) Target Hosts (B) Scanner Appliance (C) Authentication (D) Option ProfileCORRECT ANSWER (A) Target Hosts (B) Scanner Appliance (D) Option Profile By default, the agent collects data after every: (A) Four Hours (B) Ten Hours (C) Twelve Hours (D) Six HoursCORRECT ANSWER (A) Four Hours Report templates cannot be customized. (A) Incorrect (B) CorrectCORRECT ANSWER (A) Incorrect Which report type is NOT created from a Report Template? (A) Patch Report (B) Authentication Report (C) Map Report (D) Remediation ReportCORRECT ANSWER (B) Authentication Report One of your colleagues would like to build a report to display vulnerability findings over the last three months (including trending information)? What do you recommend? (A) Build a scan template that uses Scan Based findings (B) Build a scan template that sorts findings by Asset Group (C) Build a scan template with the "All" Asset Group as its target (D) Build a scan template that uses Host-Based FindingsCORRECT ANSWER (D) Build a scan template that uses Host-Based Findings Name the types of reports: (Select Four) (A) Scan Report (B) Map Report (C) Patch Report (D) Application Report (E) Remediation ReportCORRECT ANSWER (A) Scan Report (B) Map Report (C) Patch Report (E) Remediation Report The ________ report allows you to track the status of any vulnerability on any host. (A) Technical (B) Executive (C) Scan (D) TrendCORRECT ANSWER (D) Trend Identify the report types that can be scheduled: (Select Three) (A) Asset reports (B) Scan reports using Host-based Findings (C) Patch reports (D) Application reports (E) Remediation reportsCORRECT ANSWER (B) Scan reports using Host-based Findings (C) Patch reports (E) Remediation reports Identify the most privileged user role. (A) Administrator (B) Manager (C) Scanner (D) Auditor userCORRECT ANSWER (B) Manager What are the two components of every Business Unit? (A) Vendors (B) Assets (C) Users (D) SuppliersCORRECT ANSWER (B) Assets (C) Users A business unit can have more than one Unit Manager. (A) Incorrect (B) CorrectCORRECT ANSWER (B) Correct Only ______________ users can edit the default security options for your Qualys account. (A) Administrators (B) Manager (C) Auditor user (D) KnowledgeBaseCORRECT ANSWER (B) Manager Which user role cannot scan assets but can view reports? (A) Manager (B) Reader (C) Scanner (D) Unit ManagerCORRECT ANSWER (B) Reader Remediation policies for the teams dedicated to specific groups of host assets can be constructed using _____________ Groups. (A) Asset (B) Application (C) Scanning (D) VulnerabilityCORRECT ANSWER (A) Asset ___________ can be set on your remediation policy to ensure you are tracking the remediation of vulnerabilities on host systems is occurring in a timely manner. (A) Filtering (B) Processing (C) Deadlines (D) OrderingCORRECT ANSWER (C) Deadlines What are the two components of every Remediation Policy? (A) Results (B) Actions (C) Conditions (D) GraphicsCORRECT ANSWER (B) Actions (C) Conditions In which order are the Multiple Remediation Policies evaluated? (A) From bottom to top (B) In no specific order (C) Based on the rule creation date (D) From top to bottomCORRECT ANSWER (D) From top to bottom Which of the following does not accurately describe a behavior or characteristic of a Remediation Policy? (A) A Remediation policy can be configured to ignore certain vulnerability QIDs (B) Remediation policies contain conditions and actions (C) A remediation policy can be configured to assign detected vulnerabilities to Qualys users (D) A remediation policy at the bottom of the list has precedence over the policies above itCORRECT ANSWER (D) A remediation policy at the bottom of the list has precedence over the policies above it (A) (B) (C) (D)CORRECT ANSWER (A) (B) (C) (D)CORRECT ANSWER [Show More]
Last updated: 8 months ago
Preview 1 out of 14 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
14
Written in
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
23












 (1).png)
.png)

.png)






