Computer Science > EXAM > mid term exam cis426 ALL ANSWERS 100% CORRECT ANSWERS AID GRADE ‘A’ (All)
mid term exam cis426 ALL ANSWERS 100% CORRECT ANSWERS AID GRADE ‘A’
Document Content and Description Below
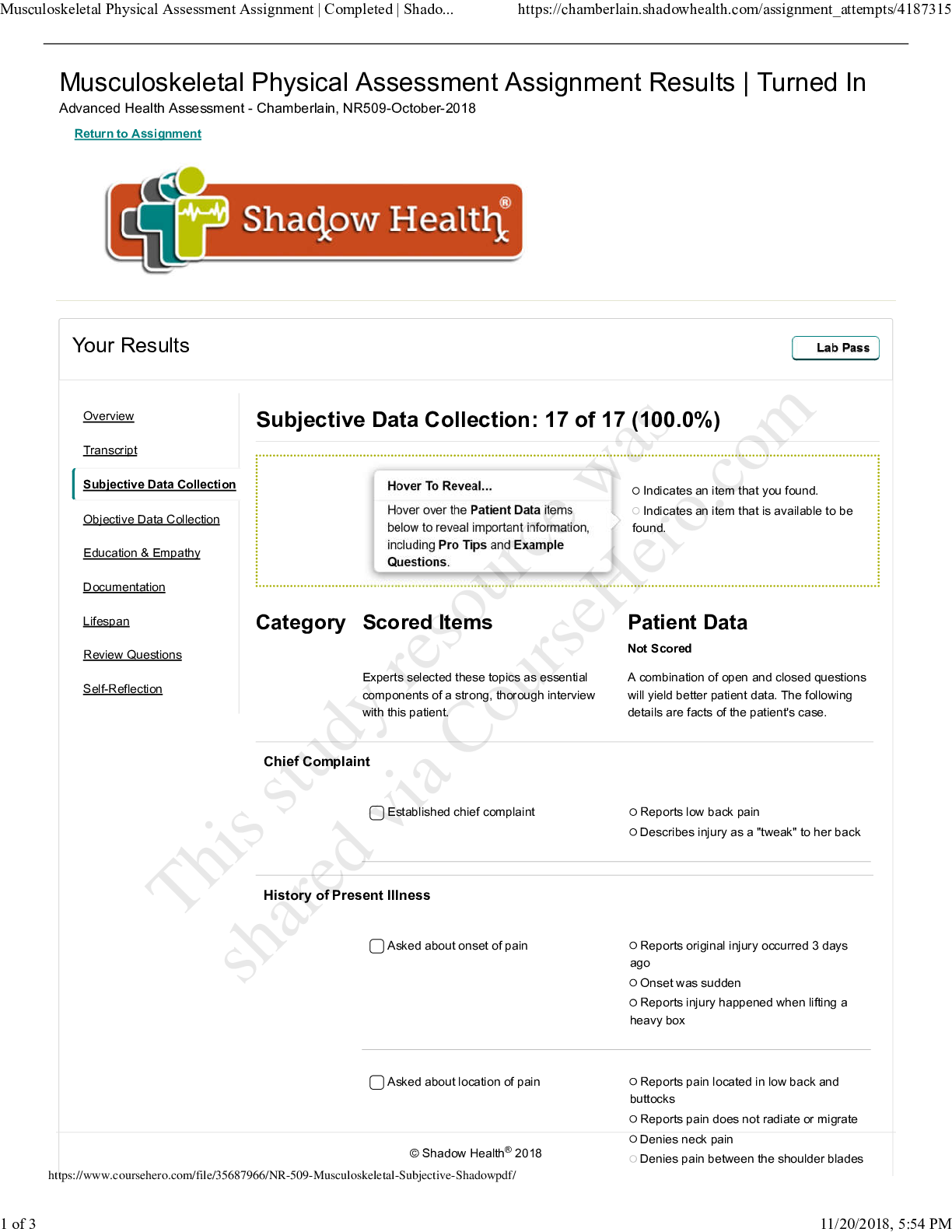
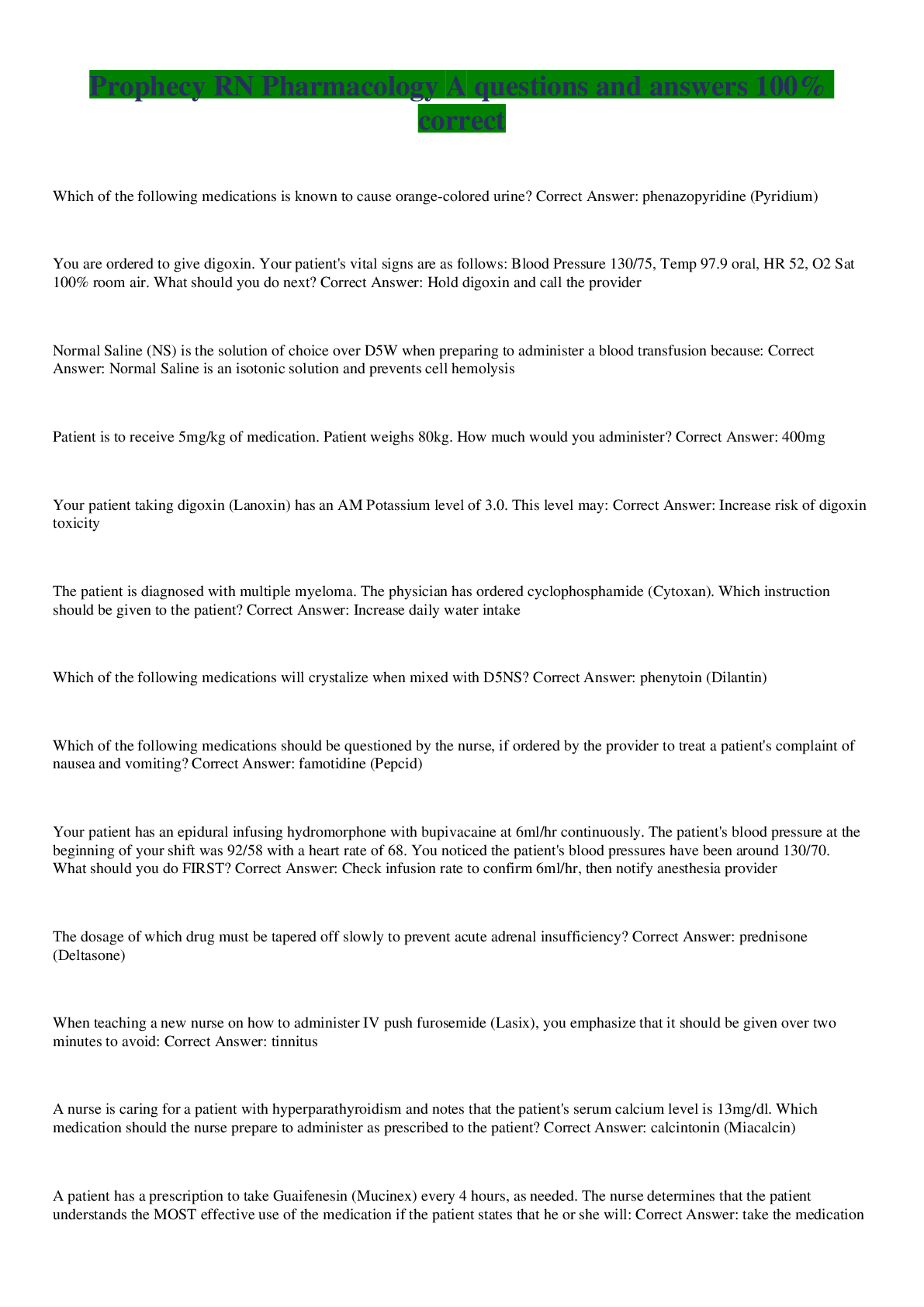
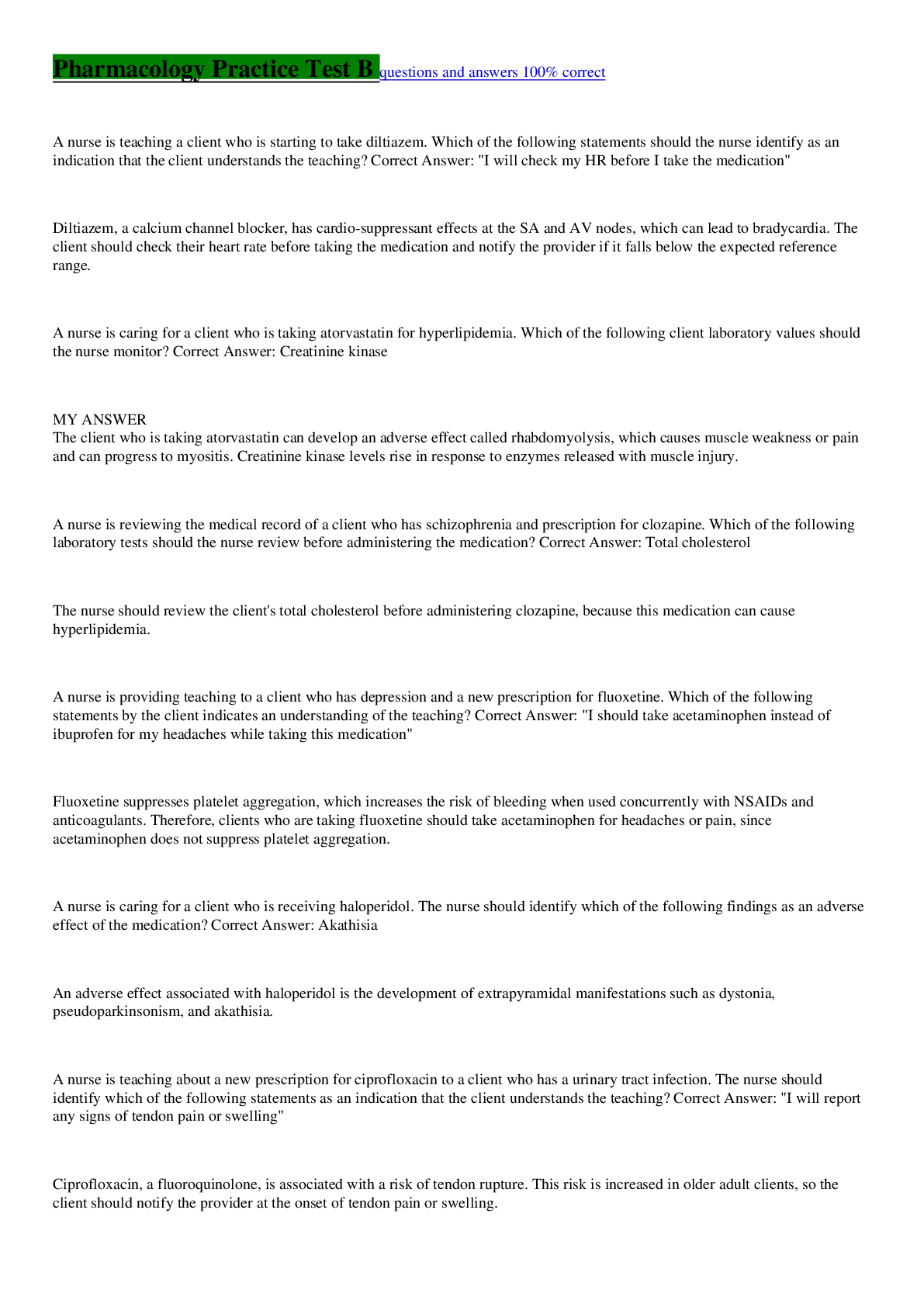
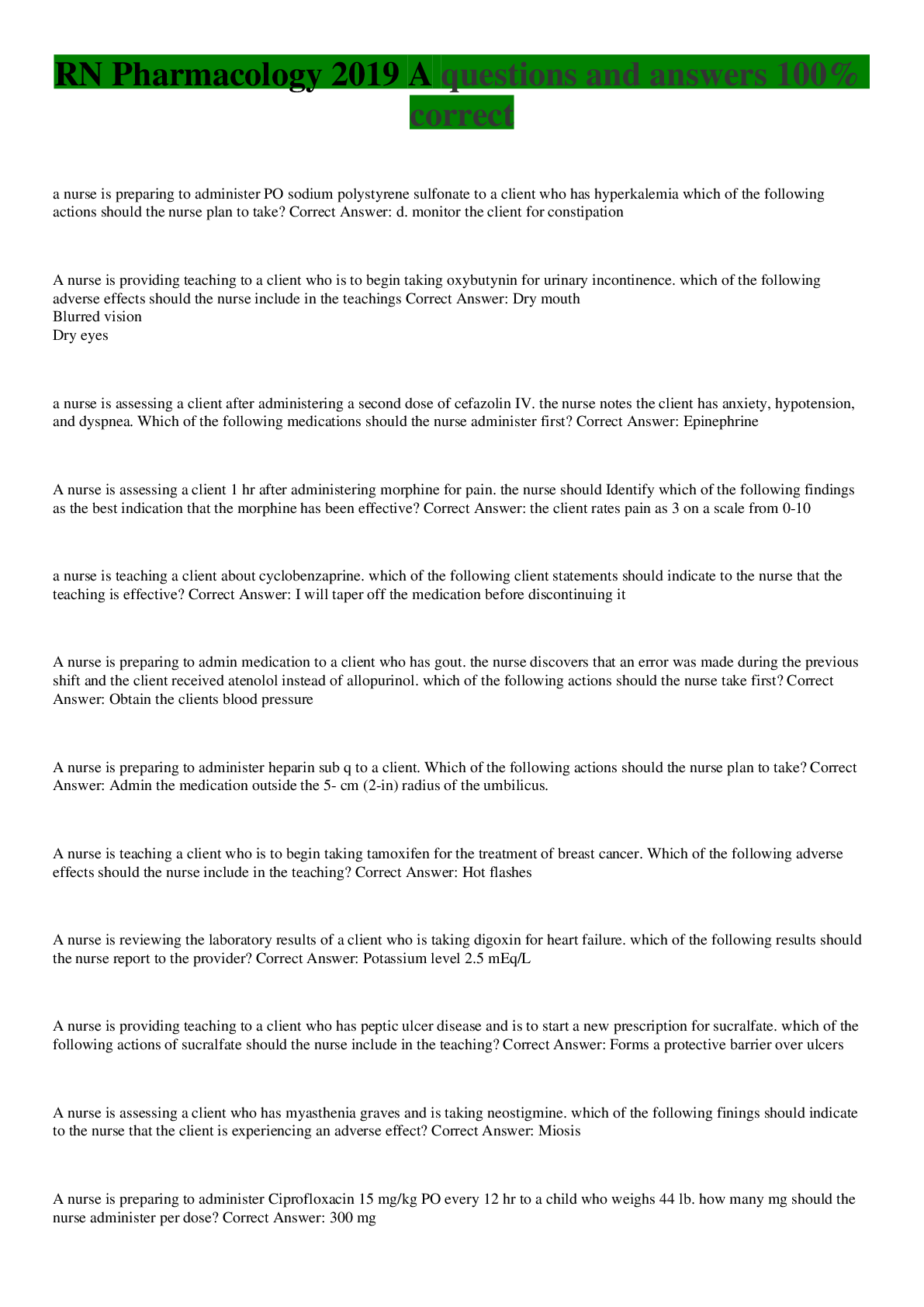
addresses how specific a policy is with respect to resources. Selected Answer: Correct Granularity Correct Answer: Correct Granularity Question 2 0 out of 2 points Which of the following statement... s best captures the role of information security teams in ensuring compliance with laws and regulations? Selected Answer: Incorrect Information security personnel must be trained lawyers, and as such they must work with their organizations’ compliance and legal teams to gain an understanding of legal requirements. Correct Answer: Correct Information security personnel work with their organizations’ compliance and legal teams to determine violations of an organization’s security policy. Question 3 2 out of 2 points In the ISO/IEC 27002 framework, describes the use and controls related to encryption. Selected Answer: Correct cryptography Correct Answer: Correct cryptography Question 4 2 out of 2 points Some organizations create a specific consequence model for information security policy. Violations can replace and absorb the broader HR polices that deal with disciplining individuals. A consequence model is intended to be punitive for the individual. Selected Answer: Correct False Correct Answer: Correct False Question 5 2 out of 2 points Which of the following policy frameworks is a widely accepted set of documents that is commonly used as the basis for an information security program, and is an initiative from ISACA, formerly known as the Information Systems Audit and Control Association? Selected Answer: Correct Control Objectives for Information and related Technology (COBIT) Correct Answer: Correct Control Objectives for Information and related Technology (COBIT) Question 6 2 out of 2 points Of the roles commonly found in the development, maintenance, and compliance efforts related to a policy and standards library, which of the following has the responsibilities of directing policies and procedures designed to protect information resources, identifying vulnerabilities, and developing a security awareness program? Selected Answer: Correct information resources security officer Correct Answer: Correct information resources security officer Question 7 0 out of 2 points Implementing security policy means continuous communication with and ensuring transparency about what’s working and what’s not working. Selected Answer: Incorrect executives Correct Answer: Correct stakeholders Question 8 2 out of 2 points Research shows that projects dedicated to information security policies fail due to eight common perceived missteps. Which of the following is not one of the missteps? Selected Answer: Correct Lack of complexity: This refers to an oversimplication of policies that sacrifices depth and nuance. Correct Answer: Correct Lack of complexity: This refers to an oversimplication of policies that sacrifices depth and nuance. Question 9 2 out of 2 points In a large organization, the complexity required to keep operations running effectively requires a hierarchy of specialties. Thus, which of following organizational structures is preferred? Selected Answer: Correct hierarchical organizational structure Correct Answer: Correct hierarchical organizational structure Question 10 2 out of 2 points In order to gain a deeper understanding of how employees interact in the workplace, it is useful to learn about the eight classic personality types that have been identified by HR Magazine. One of these is the achievers. Which of the following descriptions best captures this personality type? Selected Answer: Correct These people are very result oriented. They genuinely want the best result and may seek different ways to bring that result into being. Correct Answer: Correct These people are very result oriented. They genuinely want the best result and may seek different ways to bring that result into being. Question 11 2 out of 2 points For leaders, implementing security policies is all about working through others to gain their support and adhere to the policies. Of the widely accepted leadership rules that apply to security policies, which of the following is not among these rules? Selected Answer: Correct productivity Correct Answer: Correct productivity Question 12 2 out of 2 points Implementing security policies is easier if you manage it from a change model perspective. The first step of this model is to create urgency. Who is responsible for conveying urgency to business leaders? Selected Answer: Correct chief information security officer Correct Answer: Correct chief information security officer Question 13 0 out of 2 points A(n) is a term used to indicate any unwanted event that takes places outside the normal daily security operations. This type of event relates to a breakdown in controls as identified by the security policies. Selected Answer: Incorrect operational risk Correct Answer: Correct security event Question 14 2 out of 2 points Of the six specific business risks, the risk results from negative publicity regarding an organization’s practices. Litigation and a decline in revenue are possible outcomes of this type of risk. Selected Answer: Correct reputational Correct Answer: Correct reputational Question 15 0 out of 2 points Which of the following is not one of the similarities shared by an enterprise risk management (ERM) framework and a governance, risk management, and compliance (GRC) framework? Selected Answer: Incorrect proactively enforce policy Correct Answer: Correct the importance of value delivery Question 16 0 out of 2 points An illustration of would be an organization installing malware software on the network and endpoint, monitoring for suspicious traffic, and responding as needed. Selected Answer: Incorrect risk evaluation Correct Answer: Correct disposal of risk Question 17 2 out of 2 points Also known as the Federal Information Processing Standards (FIPS), the framework is a shared set of security standards required by the Federal Information Security Management Act (FISMA). Selected Answer: Correct NIST Correct Answer: Correct NIST [Show More]
Last updated: 1 year ago
Preview 1 out of 16 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jun 29, 2021
Number of pages
16
Written in
Additional information
This document has been written for:
Uploaded
Jun 29, 2021
Downloads
0
Views
34