Computer Networking > QUESTIONS & ANSWERS > 95 Q&A on Cyber Awareness 2023 Knowledge Check (Answered) (All)
95 Q&A on Cyber Awareness 2023 Knowledge Check (Answered)
Document Content and Description Below
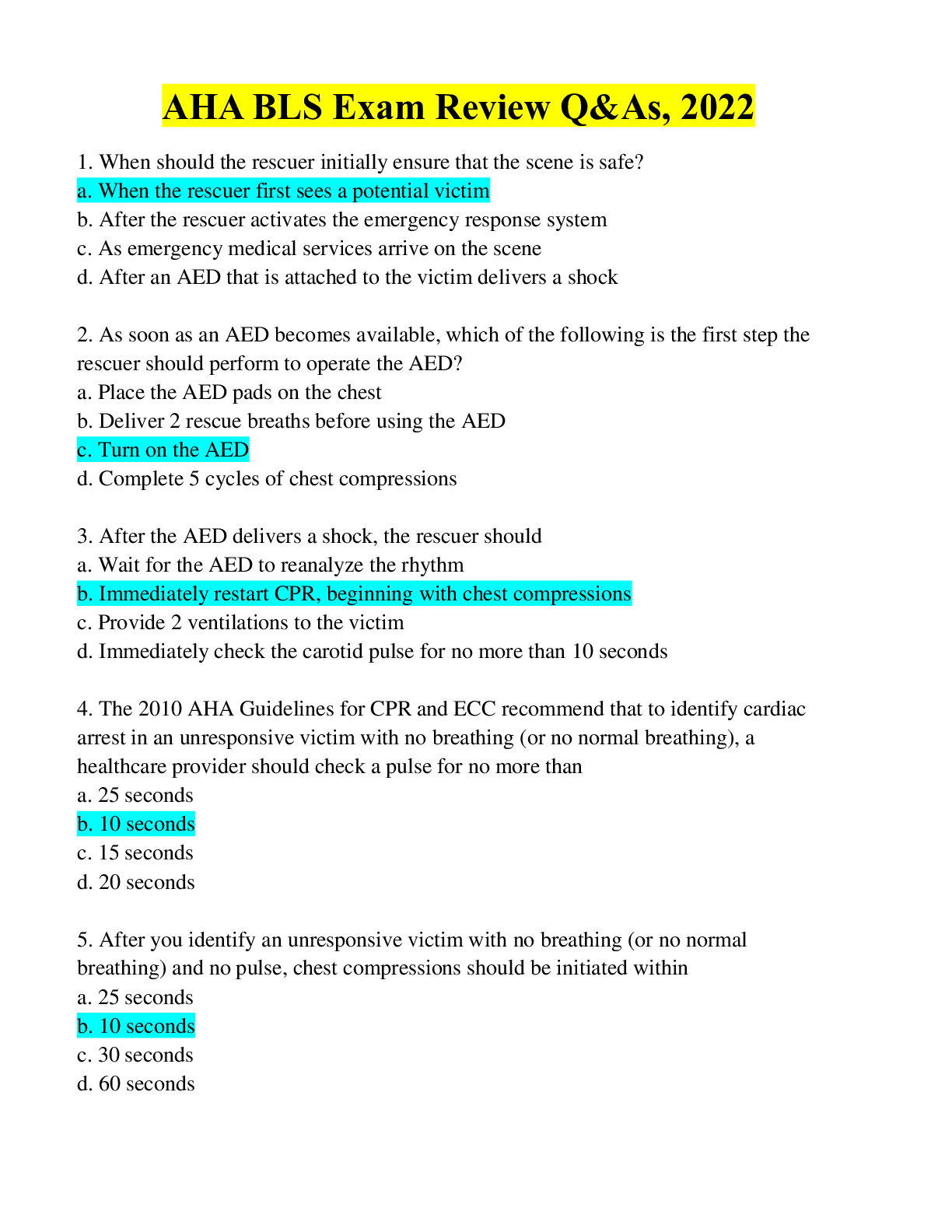
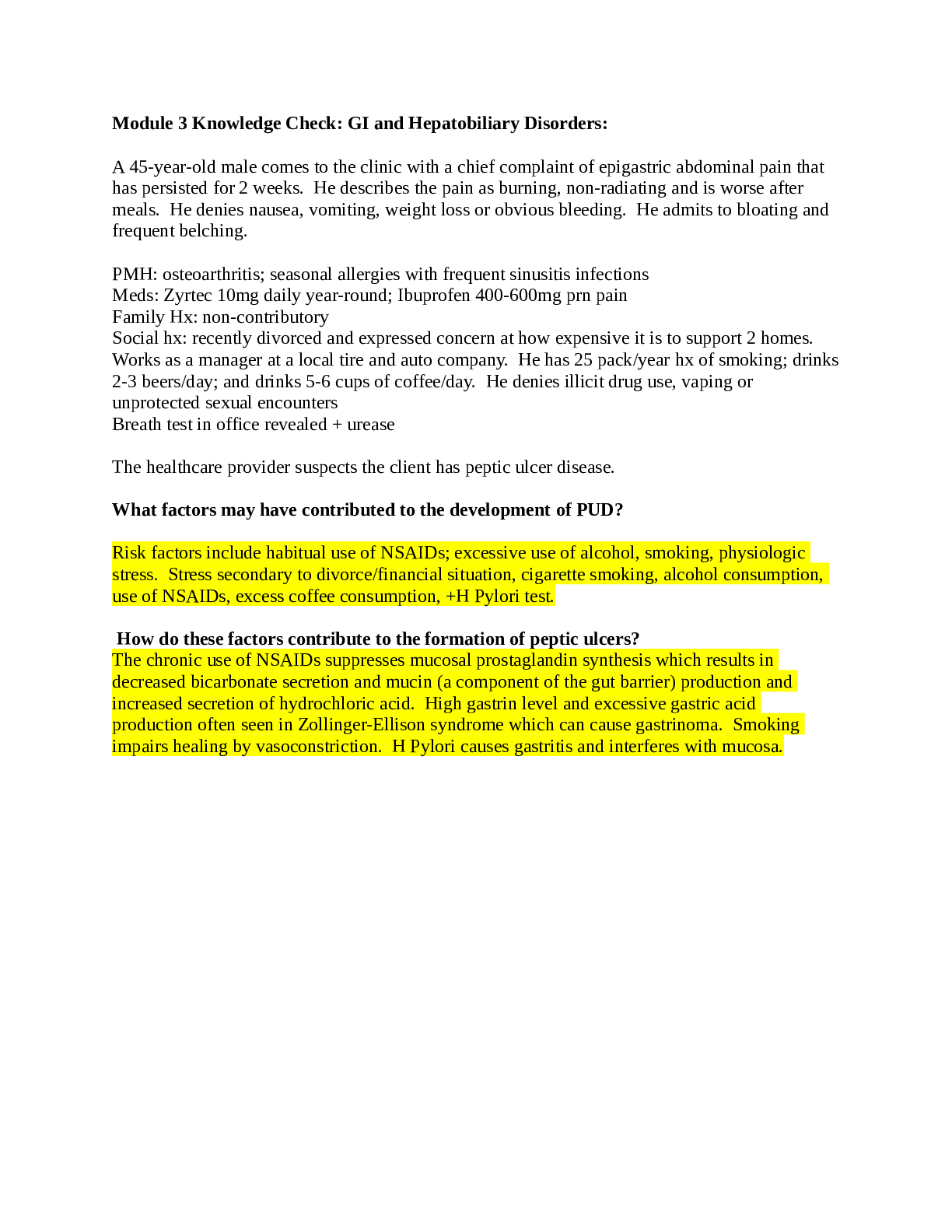
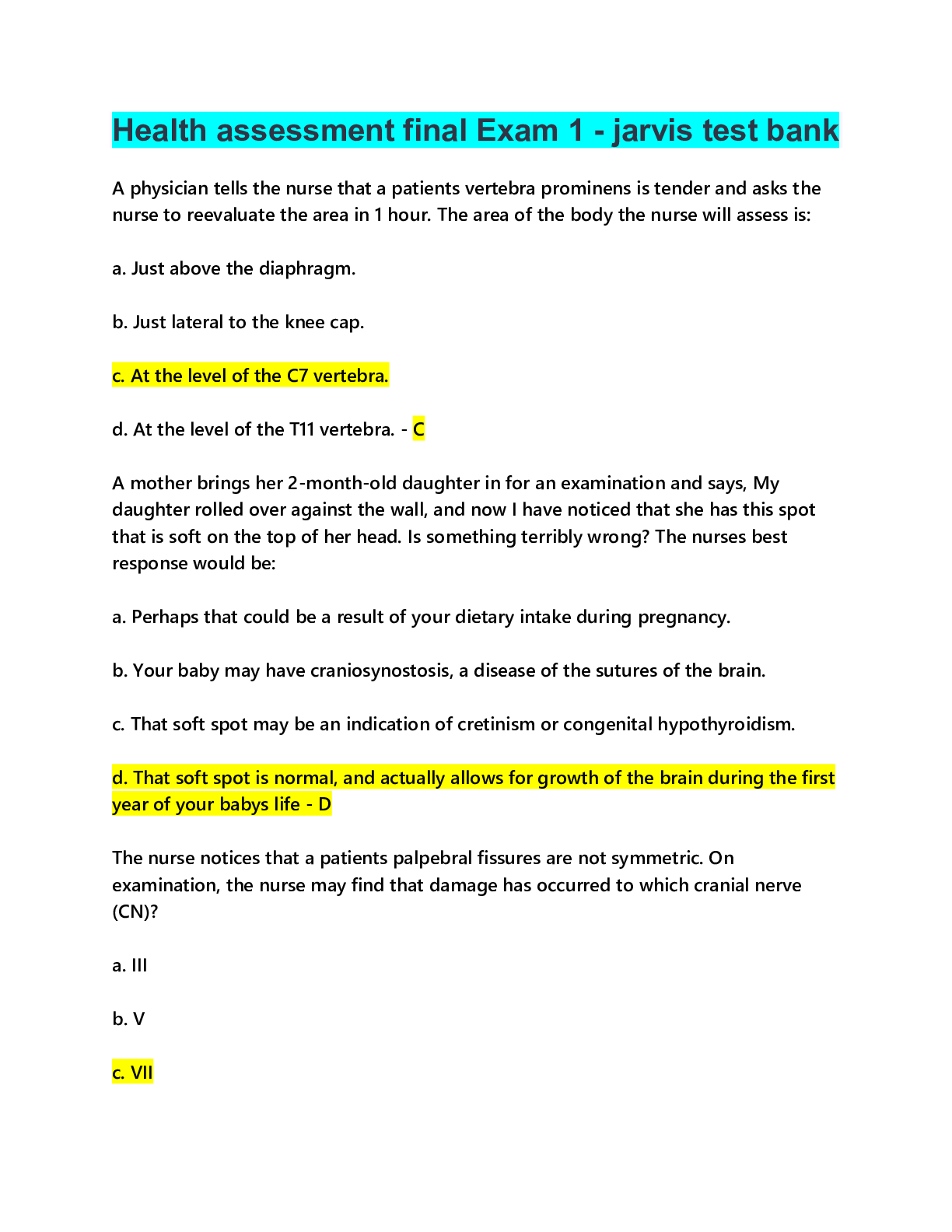
Cyber Awareness 2022-2023 Knowledge Check (Answered) 1. How many potential insider threat indicators does a person who is married with two children, vacations at the beach every year, is pleasant t... o work with, but sometimes has poor work quality display? 2. What is the best response if you find classified government data on the internet? 3. After reading an online story about a new security project being developed on the military installation where you work, your neighbor asks you to comment about the article. You know this project is classified. What should be your response? 4. What is a proper response if spillage occurs? 5. What should you do if a reporter asks you about potentially classified information on the web? 6. A user writes down details from a report stored on a classified system marked as Secret and uses those details to draft an unclassified briefing on an unclassified system without authorization. What is the best choice to describe what has occurred? 7. How many potential insider threat indicators does a coworker who often makes others uneasy by being persistent in trying to obtain information about classified projects to which he has no access, is boisterous about his wife putting them in credit card debt, and often complains about anxiety and exhaustion display? 8. Which of the following can an unauthorized disclosure of information classified as Confidential reasonably be expected to cause? 9. Which classification level is given to information that could reasonably be expected to cause serious damage to national security? 10. When classified data is not in use, how can you protect it? 11. Which is a good practice to protect classified information? 12. Which of the following is a good practice to aid in preventing spillage? 13. What is required for an individual to access classified data? 14. What type of activity or behavior should be reported as a potential insider threat? 15. Which of the following practices reduces the chance of becoming a target by adversaries seeking insider information? 16. Which scenario might indicate a reportable insider threat security incident? 17. Why might "insiders" be able to cause damage to their organizations more easily than others? 18. Which of the following is a best practice to protect information about you and your organization on social networking sites and applications? 19. What should you do if an individual asks you to let her follow you into your controlled space, stating that she left her security badge at her desk? 20. Which represents a security best practice when using social networking? 21. Which is NOT a sufficient way to protect your identity? 22. Under which circumstances may you be subject to criminal, disciplinary, and/or administrative action due to online misconduct? 23. As someone who works with classified information, what should you do if you are contacted by a foreign national seeking information on a research project? 24. Which of the following is true about unclassified data? 25. What are some potential insider threat indicators? 26. What information posted publicly on your personal social networking profile represents a security risk? 27. What is an individual's Personally Identifiable Information (PII) or Protected Health Information (PHI) considered? 28. Under what circumstances could unclassified information be considered a threat to national security? 29. What type of unclassified material should always be marked with a special handling caveat? 30. Which is true for protecting classified data? 31. Which of the following is true of protecting classified data? 32. Which of the following should be reported as a potential security incident (in accordance with your Agency's insider threat policy)? 33. How many potential insider threat indicators does a person who is playful and charming, consistently win performance awards, but is occasionally aggressive in trying to access sensitive information? 34. Which of the following terms refers to harm inflicted on national security through authorized access to information or information systems? 35. What is the best example of Personally Identifiable Information (PII)? 36. What is the best example of Protected Health Information (PHI)? 37. When is the best time to post details of your vacation activities on your social networking website? 38. What does Personally Identifiable Information (PII) include? 39. What must you ensure if you work involves the use of different types of smart card security tokens? 40. What must you ensure before transmitting Personally Identifiable Information (PII) or Protected Health Information (PHI) via e-mail? 41. What must you do when e-mailing Personally Identifiable Information (PII) or Protected Health Information (PHI)? 42. What is a good practice for physical security? 43. Is it acceptable to take a short break while a coworker monitors your computer while logged on with your CAC? 44. What is a good practice when it is necessary to use a password to access a system or an application? 45. What is the best description of two-factor authentication?. 46. What certificates are contained on the DoD Public Key Infrastructure (PKI) implemented by the Common Access Card (CAC)/Personal Identity Verification (PIV) card? 47. What are the requirements to be granted access to SCI material? 48. What is a protection against internet hoaxes? 49. What organization issues the directives concerning the dissemination of information regarding intelligence sources, methods, or activities? 50. Which term describes an event where a person who does not have the required clearance or access caveats comes into possession of Sensitive Compartmented Information (SCI) 51. What describes a Sensitive Compartmented Information (SCI) program?. 52. What describes how Sensitive Compartmented Information is marked? - 53. What must users do when using removable media within a Sensitive Compartmented Information Facility (SCIF)? 54. Which is a risk associated with removable media? 55. What is an indication that malicious code is running on your system? corruption 56. What are some actions you can take to try to protect your identity? 57. Which of the following is an appropriate use of Government e-mail? 58. What is a protection against internet hoaxes? 59. What can malicious code do? 60. Which is true of cookies? 61. What is a common method used in social engineering? 62. Which may be a security issue with compressed URLs? 63. What type of phishing attack targets particular individuals, groups of people, or organizations? 64. While on vacation, a coworker calls and asks you to access a site to review and approve a document that is hosted behind a DoD Public Key Infrastructure (PKI) protected webpage. You do not have your government-issued laptop. What action should you take? 65. Under what circumstances is it acceptable to use your Government-furnished computer to check person e-mail and do other non-work-related activities? 66. Which are examples of portable electronic devices (PEDs)? 67. What are some examples of removable media? 68. What is a valid response when identity theft occurs? 69. What is a common indicator of a phishing attempt? 70. What is whaling? 71. Upon connecting your Government-issued laptop to a public wireless connection, what should you immediately do? 72. Which of the following activities is an ethical use of Government-furnished equipment (GFE)? 73. Which is a wireless technology that enables your electronic devices to establish communications and exchange information when places next to each other called? 74. Which of the following helps protect data on your personal mobile devices? 75. What is a possible indication of a malicious code attack in progress? 76. What should you do if a commercial entity, such as a hotel reception desk, asks for Government identification so that they can make a photocopy? 77. When is conducting a private money-making venture using your Government-furnished computer permitted? 78. What is a good practice to protect data on your home wireless systems? 79. Which must be approved and signed by a cognizant Original Classification Authority (OCA)? 80. What portable electronic devices (PEDs) are allowed in a Secure Compartmented Information Facility (SCIF)? 81. What is a way to prevent the download of viruses and other malicious code when checking your e-mail? 82. What is a best practice to protect data on your mobile computing device? 83. Which of the following is NOT considered a potential insider threat indicator? - 84. What advantages do "insider threats" have over others that allows them to cause damage to their organizations more easily? 85. Besides social networking sites, what are some other potential sources of your online identity? 86. What action should you take if you receive a friend request on your social networking website from someone in Germany you met casually at a conference last year? 87. A colleague asks to leave a report containing Protected Health Information (PHI) on his desk overnight so he can continue working on it the next day. How do you respond? 88. Which of the following is the best example of Personally Identifiable Information (PII)? 89. What certificates are contained on the Common Access Card (CAC)? 90. When should documents be marked within a Sensitive Compartmented Information Facility (SCIF)? 91. Which organization issues the directives concerning the dissemination of information regarding intelligence sources, methods, or activities? 92. You receive an email from the Internal Revenue Service (IRS) demanding immediate payment of back taxes of which you were not aware. The email provides a website and a toll-free number where you can make payment. What action should you take? 93. When using your Government-issued laptop in public environments, with which of the following should you be concerned? 94. Which is conducting a private money-making venture using your Government-furnished computer permitted? 95. Which of the following is a best practice for securing your home computer? [Show More]
Last updated: 1 year ago
Preview 1 out of 8 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Oct 17, 2022
Number of pages
8
Written in
Additional information
This document has been written for:
Uploaded
Oct 17, 2022
Downloads
1
Views
248

.png)
.png)






















.png)

