Computer Science > EXAM > Server 2 final Ch 5-8 QUESTIONS AND ANSWERS ALL CORRECT (All)
Server 2 final Ch 5-8 QUESTIONS AND ANSWERS ALL CORRECT
Document Content and Description Below
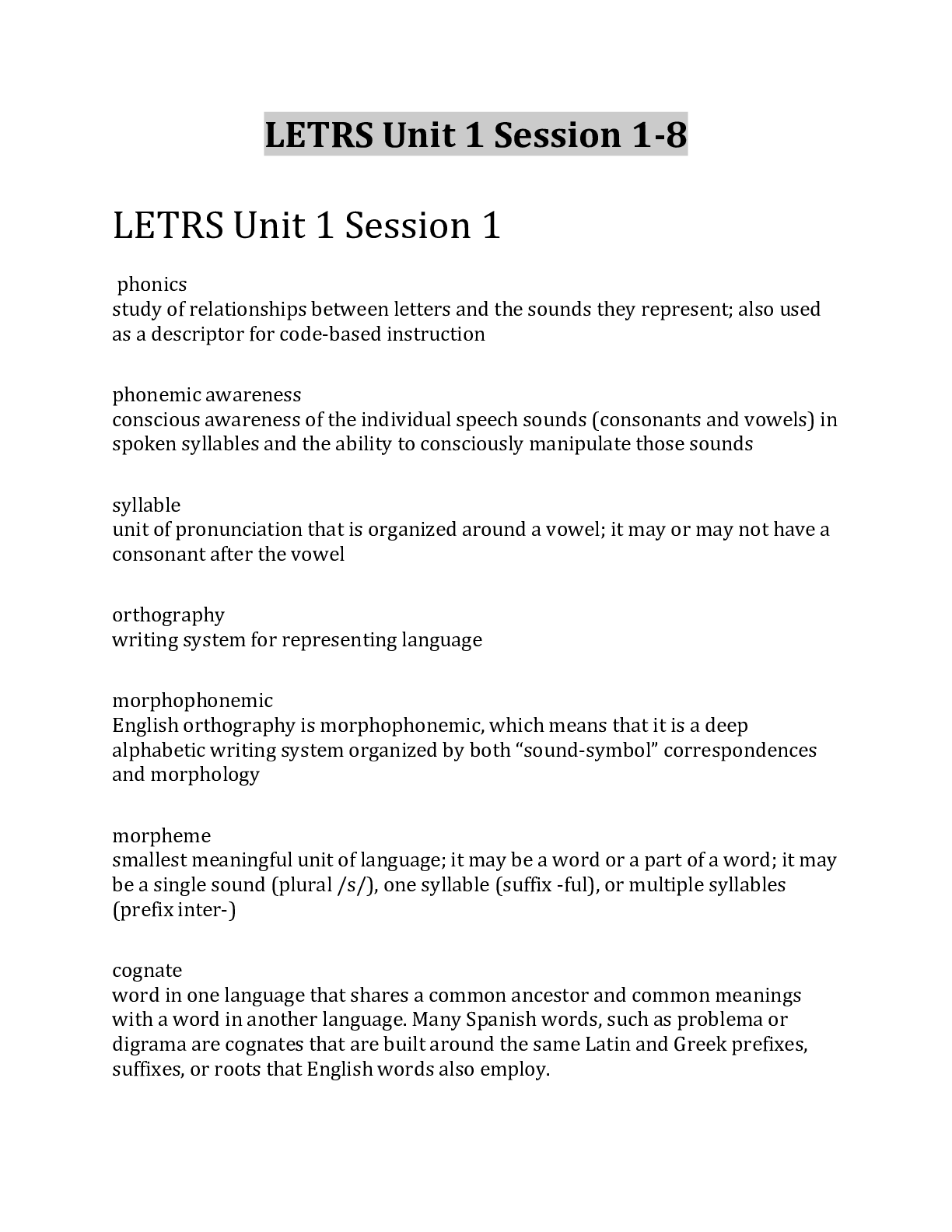
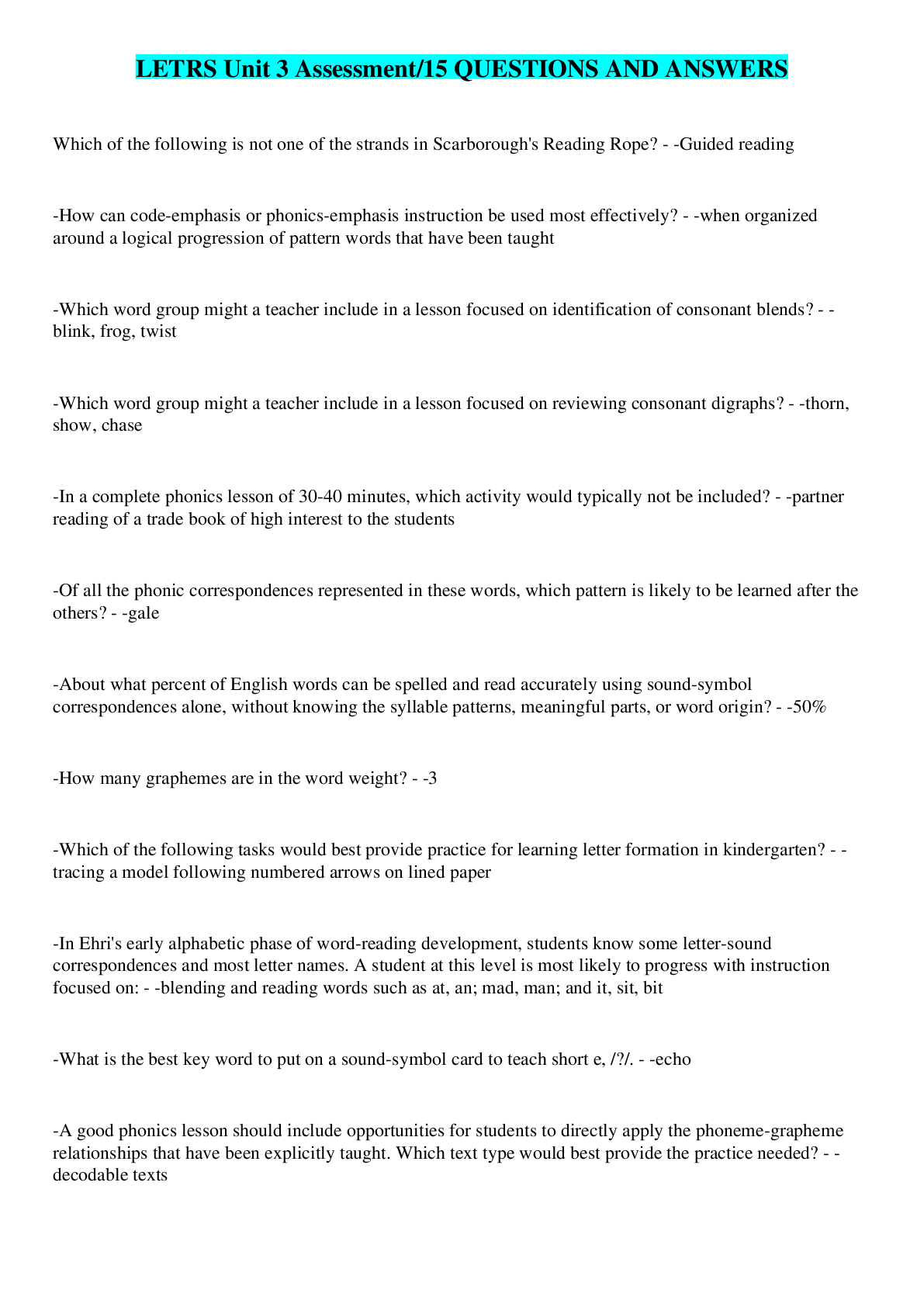
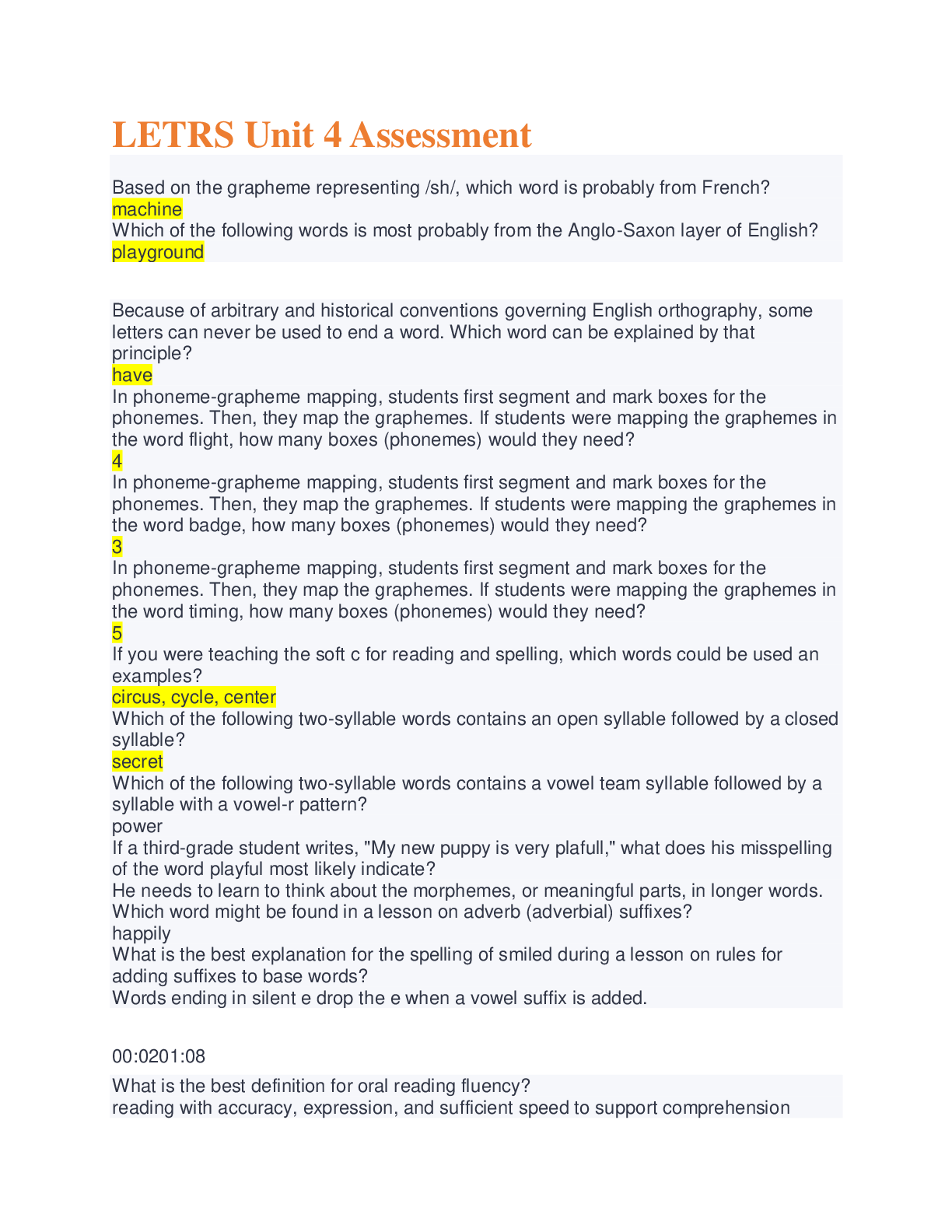
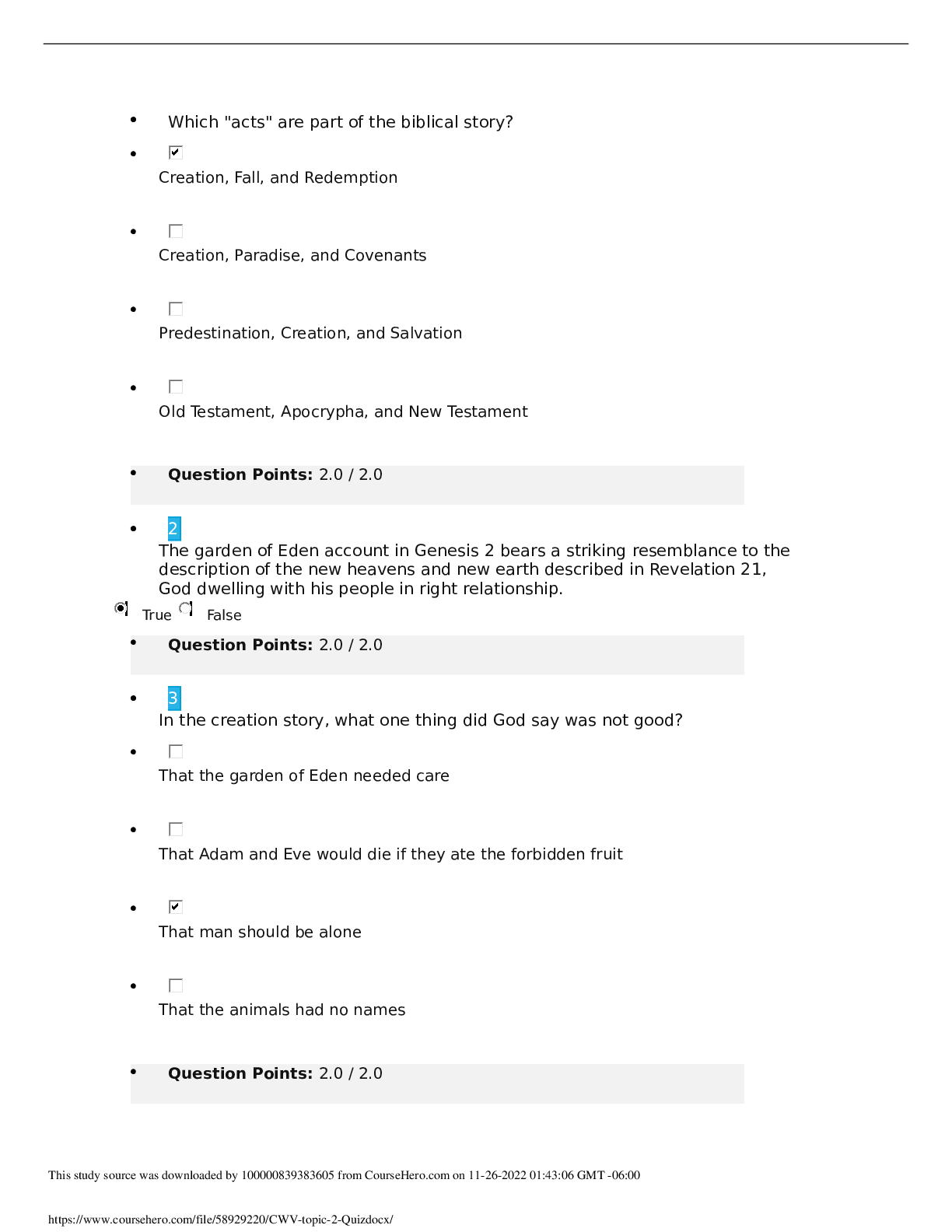
Server 2 final Ch 5-8 A(n) _____ can only contain members from within the same domain. Correct Answer: Global Group You can use the _____ utility to import data from Comma-Separated Values (CSV... ) files. Correct Answer: CSVDE Each user and group object has a(n) _____, which must be unique across an entire Active Directory domain. Correct Answer: SAM account name The Anonymous Logon group is an example of a(n) _____. Correct Answer: Special Identity Group You can use the _____ command-line utility to create and modify Active Directory objects. Correct Answer: LDIFDE When users log on to Active Directory, they receive a(n) _____ consisting of all of their security group memberships. Correct Answer: access token 7. A local user is stored in the _____ database of the computer on which it was created. Correct Answer: Security Account Manager (SAM) Each CSV file needs to begin with a(n) _____ when used with the CSVDE command-line tool. Correct Answer: header record A(n) _____ can only be used to send and receive email, not to secure network resources. Correct Answer: distribution group _____ is the practice of adding one group as a member of another group. Correct Answer: Group nesting Which special identity group controls anonymous access to resources in Windows Server 2008? Correct Answer: Anonymous Logon What defines the types of objects that can belong to a particular group and the types of resources that group can be used to secure? Correct Answer: Group scope What technique is used to configure one security group as a member of another security group? Correct Answer: Group nesting The Administrator and Guest user accounts are examples of ______________. Correct Answer: Built-in user account Which command-line tool can be used to create various object types within Active Directory? Correct Answer: dsadd Which input file format allows you to create, modify, and delete objects within Active Directory? Correct Answer: Comma Separated Value (CSV) Which group type allows you to assign permissions to resources, as well as receive messages via Active Directory-enabled email applications such as Microsoft Exchange? Correct Answer: Security group Which group scope can contain users and groups from any domain within an Active Directory forest, but can be used only to secure resources located within the same domain as the group itself? Correct Answer: Domain local group Which account type is configured on an Active Directory domain controller and can be used to grant access to resources on any domain-joined computer? Correct Answer: Domain account What can be used to run script files using VBScript or JScript from the Windows desktop or from a command prompt? Correct Answer: Windows Scripting Host (WSH) This service is required to use the runas feature. Correct Answer: Secondary Logon This command-line tool can be used to move an object from one OU to another. Correct Answer: dsmove This tool is used to move objects from one domain to another Correct Answer: Active Directory Migration Tool Hackers will use this attack to identify a user's password by trying numerous words and word combinations until they find a match. Correct Answer: dictionary attack When you create this item do not use words from the dictionary. Correct Answer: strong password This can be used to run a single command using administrative privileges while logging onto a workstation or server using a Domain User account. Correct Answer: runas This can be used for authentication in lieu of a password when used with an ATM or a smart card. Correct Answer: personal identification number (PIN) Use this tool to grant authority to a user or group of users over a portion of the Active Directory tree. Correct Answer: Delegation of Control Wizard This method of moving objects from one OU to another was introduced in Windows Server 2003. Correct Answer: drag-and-drop A dictionary attack is one type of this attack. Correct Answer: password-cracking Which interface allows you to grant limited permissions within Active Directory to individual users or groups to adhere to a principle of least privilege in administering Active Directory? Correct Answer: Delegation of Control Wizard Which program allows you to use the Secondary Logon service to launch individual programs and utilities using administrative privileges? Correct Answer: Runas Which command-line utility can be used to move an Active Directory object from one container to another? Correct Answer: Dsmove What is a numeric or alphanumeric character sequence that you enter with a smart card to access a server or other Active Directory resource? Correct Answer: Personal Identification Nu [Show More]
Last updated: 1 year ago
Preview 1 out of 6 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Jul 11, 2022
Number of pages
6
Written in
Additional information
This document has been written for:
Uploaded
Jul 11, 2022
Downloads
0
Views
99




.png)