Information Technology > EXAM > Questions and Answers > University of the Cumberlands ITS 532 ITS 532 Cloud Computing ITS532_Midterm (All)
Questions and Answers > University of the Cumberlands ITS 532 ITS 532 Cloud Computing ITS532_Midterm 50Q&A
Document Content and Description Below
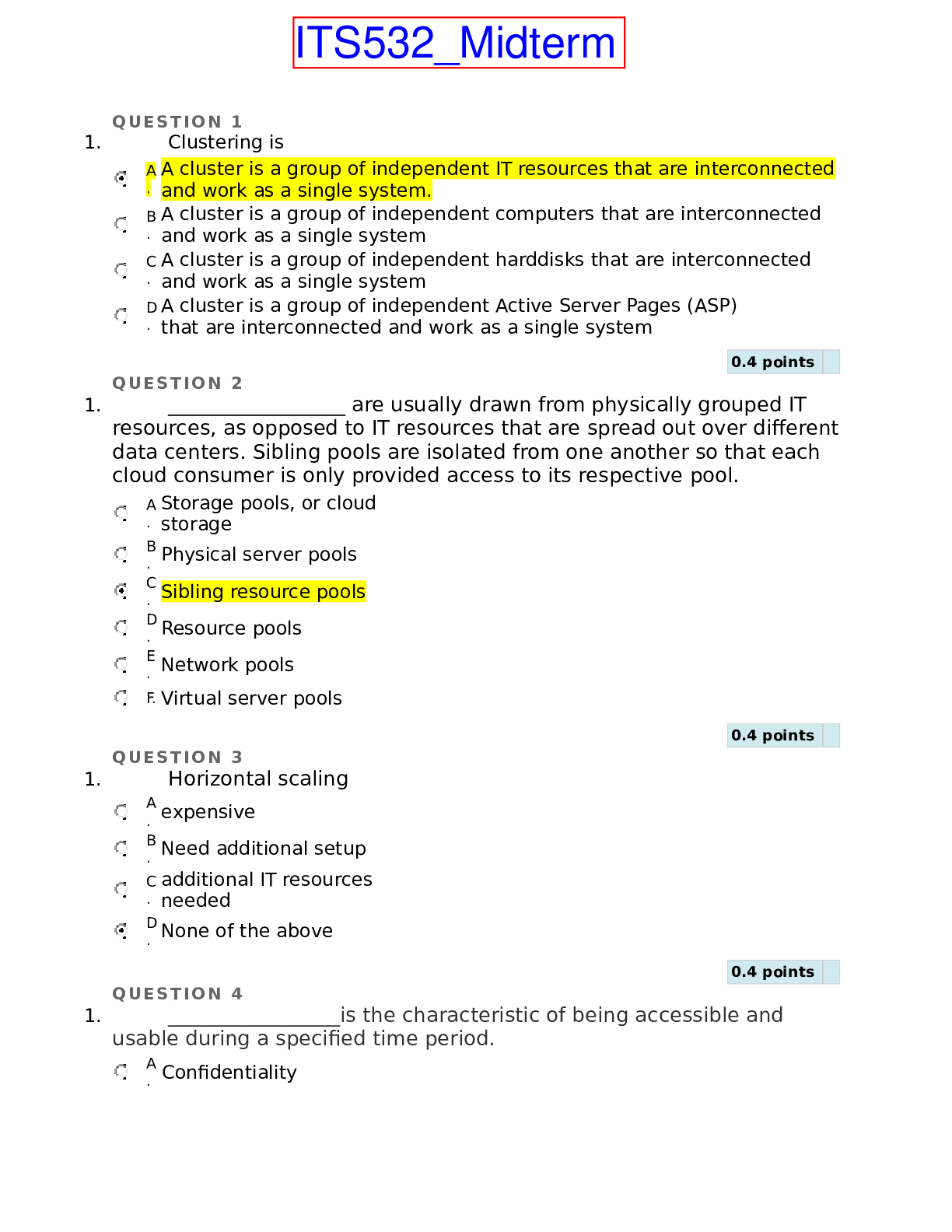
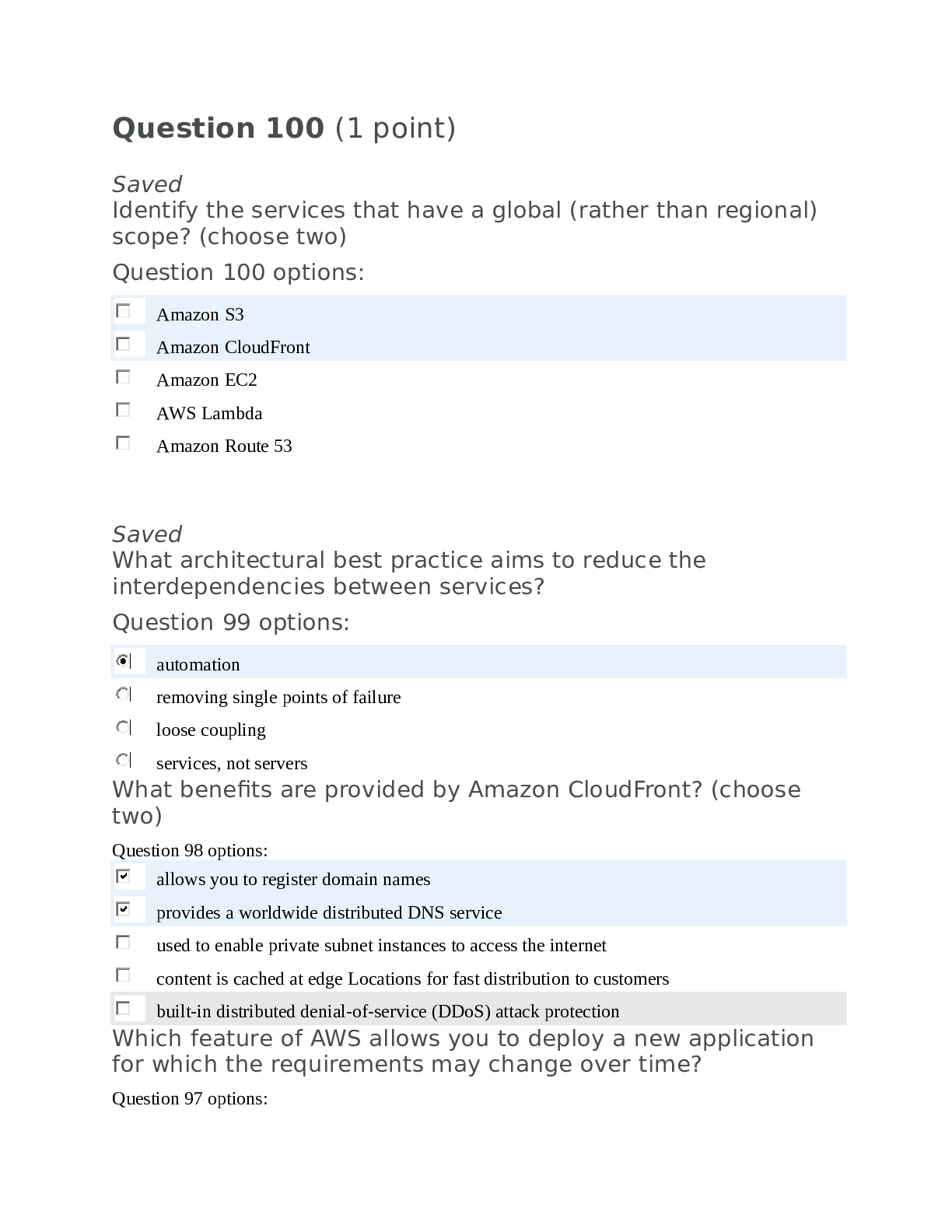
University of the Cumberlands ITS 532 ITS532_Midterm QUESTION 1 1. Clustering is A. A cluster is a group of independent IT resources that are interconnected and work as a single system. B. A c... luster is a group of independent computers that are interconnected and work as a single system C. A cluster is a group of independent harddisks that are interconnected and work as a single system D. A cluster is a group of independent Active Server Pages (ASP) that are interconnected and work as a single system 0.4 pointsQUESTION 2 1. ___________________ are usually drawn from physically grouped IT resources, as opposed to IT resources that are spread out over different data centers. Sibling pools are isolated from one another so that each cloud consumer is only provided access to its respective pool. A. Storage pools, or cloud storage B. Physical server pools C. Sibling resource pools D. Resource pools E. Network pools F. Virtual server pools 0.4 pointsQUESTION 3 1. Horizontal scaling A. expensive B. Need additional setup C. additional IT resources needed D. None of the above 0.4 pointsQUESTION 4 1. _________________is the characteristic of being accessible and usable during a specified time period. A. Confidentiality B. Integrity C. Authenticity D. Availability E. Threat F. Vulnerability G. Risk H. None of the above 0.4 pointsQUESTION 5 1. An -------------------------------represents the physical perimeter that surrounds a set of IT resources that are owned and governed by an organization A. organizational boundary B. None of the above C. Cloud Computing Reference D. Cloud Carrier 0.4 pointsQUEST ION 6 1. Packet networks with “best effort” quality-of-service (QoS) typically transmit packets on a ------------------------------basis A. firstin/ last serve B. first-come/firstserve C. noe of the above D. last in / fiirst serve 0.4 pointsQUEST ION 7 1. Tasks that are typically automated and implemented through the resource management system not include: A. enforcing usage and security policies throughout the lifecycle of cloud service instances B coordinating IT resources in relation to the involvement of other . mechanisms, such as resource replication, load balancer, and failover system C. monitoring cloud service status, usage, and performance D. allocating and releasing virtual IT resources into the available physical infrastructure in response to the starting, pausing, resuming, and termination of virtual IT resource instances E. managing virtual IT resource templates that are used to create pre-built instances, such as virtual server images F. enforcing usage and security policies throughout the lifecycle of cloud service instances 0.4 pointsQUESTION 8 1. _________________is the characteristic of something having been provided by an authorized source. This concept encompasses nonrepudiation, which is the inability of a party to deny or challenge the authentication of an interaction A. Confidentiality B. Integrity C. Authenticity D. Availability E. Threat F. Vulnerability G. Risk H. None of the above 0.4 pointsQUESTION 9 1. ___________________ are ready to be allocated to virtual servers, and are typically broken down into individual processing cores A. Physical server pools B. Storage pools C. Virtual server pools D. CPU pools E. Resource pooling architecture F. Resource pools 0.4 pointsQUESTION 10 1. A cloud service is any IT resource that is made A. Remotely accessible via a cloud B. Physical accessible via a cloud C. Locally accessible via a cloud D. None of the Above 0.4 pointsQUESTION 11 1. --------------------------------------- his model is based on an architecture comprised of two or more inter-connected clouds. A. Virtual Private Cloud B. Private cloud C. Public cloud D. Inter-Cloud E. Hybrid cloud 0.4 pointsQUESTION 12 1. _________________ _____________________________mechanism enables one cloud service consumer to be authenticated by a security broker, which establishes a security context that is persisted while the cloud service consumer accesses other cloud services or cloud-based IT resources. Otherwise, the cloud service consumer would need to re-authenticate itself with every subsequent request A. Credential Management B. Authorization C. Authentication, authorization, and accounting (AAA) D. Integrity of E. User Management F. Authentication G. Accounting H. The single sign-on (SSO) 0.4 pointsQUESTION 13 1. A cloud delivery model represents a specific, pre-packaged combination of IT resources offered by a cloud provider. Three common cloud delivery models have become widely established and formalized: A. IaaS, PaaS and SaaS B. SaaS, PaaS and AaaS C. SaaS, AaaS and Paas D. AaaS, PaaS and SaaS 0.4 pointsQUESTION 14 1. Tasks that can commonly be performed by cloud consumers via a remote administration console NOT include A. monitoring QoS and SLA fulfillment B. capacity cost planning C. planning and assessing IT resource provisioning D. managing leasing costs and usage fees E. None of the Above F. managing user accounts, security credentials, authorization, and access control G. tracking internal and external access to leased services H. configuring and setting up cloud services 0.4 pointsQUESTION 15 1. _________________is the characteristic of something being made accessible only to authorized parties A. Confidentiality B. Integrity C. Authenticity D. Availability E. Threat F. Vulnerability G. Risk H. None of the above 0.4 pointsQUESTION 16 1. _________________is a potential security violation that can challenge defenses in an attempt to breach privacy and/or cause harm A. Confidentiality B. Integrity C. Authenticity D. Availability E. Threat F. Vulnerability G. Risk H. None of the above 0.4 pointsQUESTION 17 1. ____________________ Clustered IT resources in active/active mode are commonly used to support workload balancing between different cluster nodes. A. Hypervisor B. Audit Monitor C. Cloud Usage Monitor D. Resource Replication E. Resource Cluster F. Logical Network Perimeter 0.4 pointsQUESTION 18 1. _________________ RThe credential management system establishes identities and access control rules for defined user accounts, which mitigates the threat of insufficient authorization. A. The single sign-on (SSO) B. Credential Management C. Authentication, authorization, and accounting (AAA) D. Encrypt E. Authorization F. Integrity of G. User Management H. Authentication 0.4 pointsQUESTION 19 1. ____________________ Workloads between hypervisors and the virtual servers that they host may require distribution. A. Audit Monitor B. Cloud Usage Monitor C. Resource Cluster D. Hypervisor E. Resource Replication F. Logical Network Perimeter 0.4 pointsQUESTION 20 1. The most common economic rationale for investing in cloud-based IT resources is in the reduction or outright elimination of A. up-front IT investments B. Software purchases C. Hardware IT investments D. Constraction and buliding costs 0.4 pointsQUESTION 21 1. The following NOT specialized cloud mechanisms A. Resource Cluster B. Automated Scaling Listener C. Multi-Device Broker D. Resource Cluster E. Audit Monitor F. Hypervisor G. State machine Database H. Load Balancer 0.4 pointsQUESTION 22 1. A common approach for managing the issuance of asymmetric keys is based on the _____________________________ mechanism, which exists as a system of protocols, data formats, rules, and practices that enable largescale systems to securely use public key cryptography A. None of the above B. RSA infrastructure (RSI) C. public key infrastructure (PKI) D. private key infrastructure (PKI) 0.4 pointsQUESTION 23 1. The communication path that connects a cloud consumer with its cloud provider may involve ....................... A. Single SaaR B. multiple SaaP C. single ISP netwroks D. multiple ISP networks 0.4 pointsQUESTION 24 1. The ____________________ mechanism is a means of providing data authenticity and integrity through authentication and non-repudiation. A message is assigned a digital signature prior to transmission, which is then rendered invalid if the message experiences any subsequent, unauthorized modifications A. decryption B. hash C. digital signature D. encryption 0.4 pointsQUESTION 25 1. A---------------------is a publicly accessible cloud environment owned by a third-party cloud provider. A. Public cloud B. Hybrid cloud C. Private cloud D. Community cloud 0.4 pointsQUESTION 26 1. A ______________is an entity that poses a threat because it is capable of carrying out an attack A. security control B. Security Policy Disparity C. Authenticity D. threat agent E. Security Mechanisms F. Vulnerability G. Security Policies H. None of the above 0.4 pointsQUESTION 27 1. An______________is a non-trusted cloud service consumer without permissions in the cloud A. Confidentiality B. Security Controls C. Authenticity D. anonymous attacker E. Security Mechanisms F. Vulnerability G. Security Policies H. None of the above 0.4 pointsQUESTION 28 1. _________________is the possibility of loss or harm arising from performing an activity. Risk is typically measured according to its threat level and the number of possible or known vulnerabilities A. Confidentiality B. Integrity C. Authenticity D. Availability E. Threat F. Vulnerability G. Risk H. None of the above 0.4 pointsQUESTION 29 1. The programmatic and management interfaces that establish administration environments for a virtualization program to operate with various virtualization solutions can introduce ---------------- gaps due to incompatibilities A. None of the above B portability .C. software D. hardware E. sub function of operating system 0.4 pointsQUESTION 30 1. The following NOT specialized cloud mechanisms A. Automated Scaling Listener B. Failover System C. Hypervisor D. Resource Cluster E. Load Balancer F. Pay-Per-end Monitor G. SLA Monitor H. Audit Monitor 0.4 pointsQUESTION 31 1. ------------------------ is a cloud delivery model for shared cloud services that can be positioned as commercialized products hosted by clouds A. Iaa S B. Aaa S C. Paa S D. Saa S 0.4 pointsQUESTION 32 1. The______________ mechanism encompasses the components and policies necessary to control and track user identities and access privileges for IT resources, environments, and systems. A. HAS h B. RSA C. PKI D. IAM 0.4 pointsQUESTION 33 1. This standard regulates service registries in which WSDL definitions can be published as part of a service catalog for discovery purposes. A. SOA P B. XML C. UDD I D. SOP P E. SOA S 0.4 pointsQUESTION 34 1. _________________________is used to logically organize and isolate resource pools. A. Resource Replication B. Remote Administration System C. Cloud Usage Monitor D. Pay-Per-Use Monitor E. Logical Network Perimeter F. Resource Management System G. Audit Monitor H. Hypervisor 0.4 pointsQUESTION 35 1. Data centers are built upon ------------------ commodity hardware and designed with ------------------ architectures A. standardized , modular B standardized, non . standard C. techncal , modular D. standardized , technical 0.4 pointsQUESTION 36 1. _________________ Username and password combinations remain the most common forms of user authentication credentials managed by the IAM system, which also can support digital signatures, digital certificates, biometric hardware (fingerprint readers), specialized software (such as voice analysis programs), and locking user accounts to registered IP or MAC addresses. A. User Management B. Encrypt C. Credential Management D. Authorization E. Accounting F. Integrity of G. Authentication, authorization, and accounting (AAA) H. Authentication 0.4 pointsQUESTION 37 1. ______________________This mechanism monitors resource pool usage to ensure compliance with privacy and regulation requirements, especially when pools contain cloud storage devices or data loaded into memory. A. Remote Administration System B. Hypervisor C. Logical Network Perimeter D. Cloud Usage Monitor E. Audit Monitor F. Resource Replication G. Resource Management System H. Pay-Per-Use Monitor 0.4 pointsQUESTION 38 1. --------------------------------------- Also known as a “dedicated cloud” or “hosted cloud,” this model results in a self-contained cloud environment hosted and managed by a public cloud provider, and made available to a cloud consumer. A. Private cloud B. Inter-Cloud C. Virtual Private Cloud D. Public cloud E. Hybrid cloud 0.4 pointsQUESTION 39 1. A _______________________ exploits vulnerabilities in the virtualization platform to jeopardize its confidentiality, integrity, and/or availability A. virtualization attack B. weak authentication C. malicious intermediary D. Malicious insiders E. DoS F. Traffic eavesdropping G. Security Policy Disparity H. None of the above 0.4 pointsQUESTION 40 1. A standard syntax used for creating identifiers that point to Web-based resources, the URL is often structured using a logical network location A. Uniform Resource Locator (URL) B. hypermedia C. Hypertext Transfer Protocol (HTTP) D. Markup Languages (HTML, XML) 0.4 pointsQUESTION 41 1. -------------------------------------- Physical data storage media are connected through a dedicated network and provide block-level data storage access using industry standard protocols, such as the Small Computer System Interface (SCSI). A. Storage Area Network (SAN) B. RAID C. Hot-Swappable Hard Disks D. Hard Disk Arrays E. Network-Attached Storage (NAS) 0.4 pointsQUESTION 42 1. Cloud service usage conditions are typically expressed in A. Quality of Service agreements (QoSA) B. Service-Level Agreement (SLA) C. Service-Level Quality Agreements (SLQA) D. Service Quality Agreement (SQA) 0.4 pointsQUESTION 43 1. _________________ component defines the correct granularity for access controls and oversees the relationships between identities, access control rights, and IT resource availability. A. Encrypt B. Authorization C. Authentication, authorization, and accounting (AAA) D Authentication .E. The single sign-on (SSO) F. User Management G. Credential Management H. Accounting 0.4 pointsQUESTION 44 1. ------------------------------------- These can be safely removed from arrays without requiring prior powering down. A. Network-Attached Storage (NAS) B. Hot-Swappable Hard Disks C. Storage Area Network (SAN) D. Hard Disk Arrays 0.4 pointsQUESTION 45 1. ------------------------------------- These include snapshotting, which is saving a virtual machine’s memory into a hypervisor-readable file for future reloading, and volume cloning, which is copying virtual or physical hard disk volumes and partitions. A. Storage Area Network (SAN) B. Fast Data Replication Mechanisms C. Network-Attached Storage (NAS) D. Hot-Swappable Hard Disks 0.4 pointsQUESTION 46 1. ____________________ This mechanism can generate new instances of virtualized IT resources in response to runtime workload distribution demands. A. Logical Network Perimeter B. Audit Monitor C. Resource Cluster D. Hypervisor E. Cloud Usage Monitor F. Resource Replication 0.4 pointsQUESTION 47 1. ___________________ are usually configured using one of several available templates chosen by the cloud consumer during provisioning. For example, a cloud consumer can set up a pool of mid-tier Windows servers with 4 GB of RAM or a pool of low-tier Ubuntu servers with 2 GB of RAM. A. Physical server pools B. Resource Replication C. Resource pools D. Virtual server pools E. CPU pools F. Resource pooling architecture 0.4 pointsQUESTION 48 1. ------------------------------------- This subsystem comprises Web acceleration devices, such as XML pre-processors, encryption/decryption appliances, and layer 7 switching devices that perform content-aware routing A. Hot-Swappable Hard Disks B. LAN Fabric C. Storage Area Network (SAN) D. Fast Data Replication Mechanisms E. Web-Tier Load Balancing and Acceleration 0.4 pointsQUESTION 49 1. The ----------------------delivery model represents a self-contained IT environment comprised of infrastructure-centric IT resources that can be accessed and managed via cloud service-based interfaces and tools 0.4 pointsQUESTION 50 1. The ----------------------delivery model represents a pre-defined “ready-touse” environment typically comprised of already deployed and configured IT resources 0.4 pointsClick Save and Submit to save and submit. Click Save All Answers to save all answers. [Show More]
Last updated: 1 year ago
Preview 1 out of 18 pages
Instant download
Instant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 06, 2022
Number of pages
18
Written in
Additional information
This document has been written for:
Uploaded
Aug 06, 2022
Downloads
0
Views
52













.png)



.png)
.png)
.png)
.png)