Information Technology > EXAM > SAPPC Certification Study Guide; Questions & Answers :Latest 2022: 2023: Guaranteed A+ Guide (All)
SAPPC Certification Study Guide; Questions & Answers :Latest 2022: 2023: Guaranteed A+ Guide
Document Content and Description Below
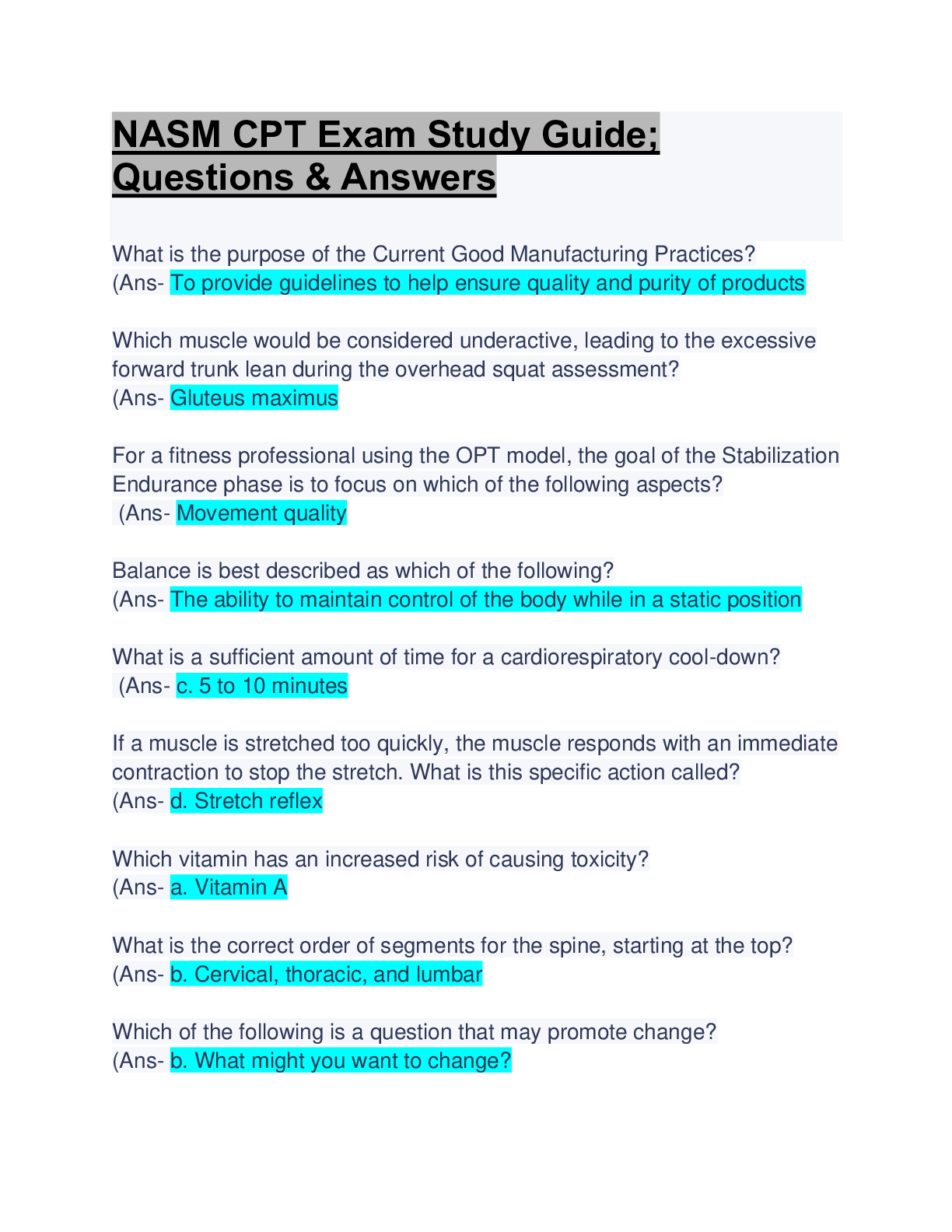
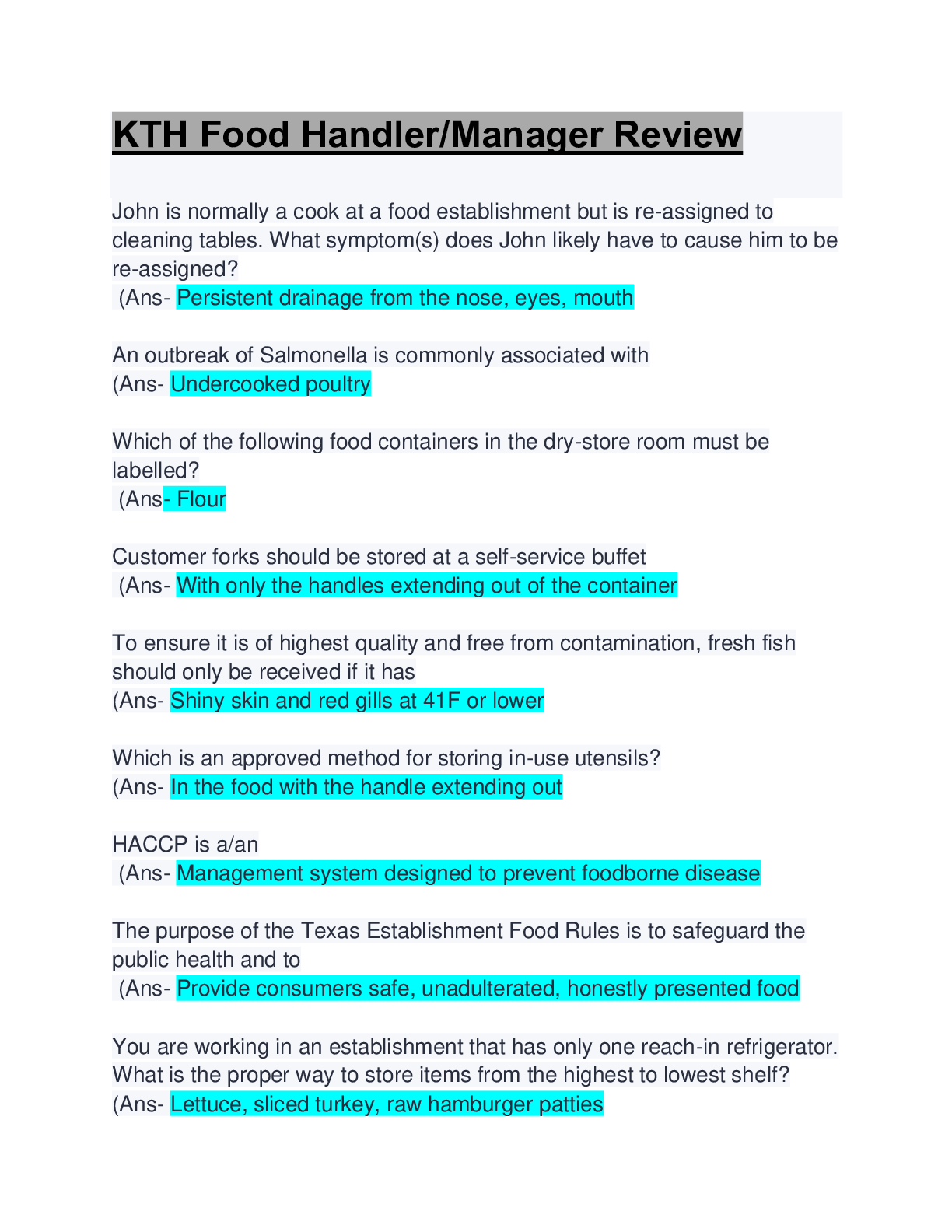
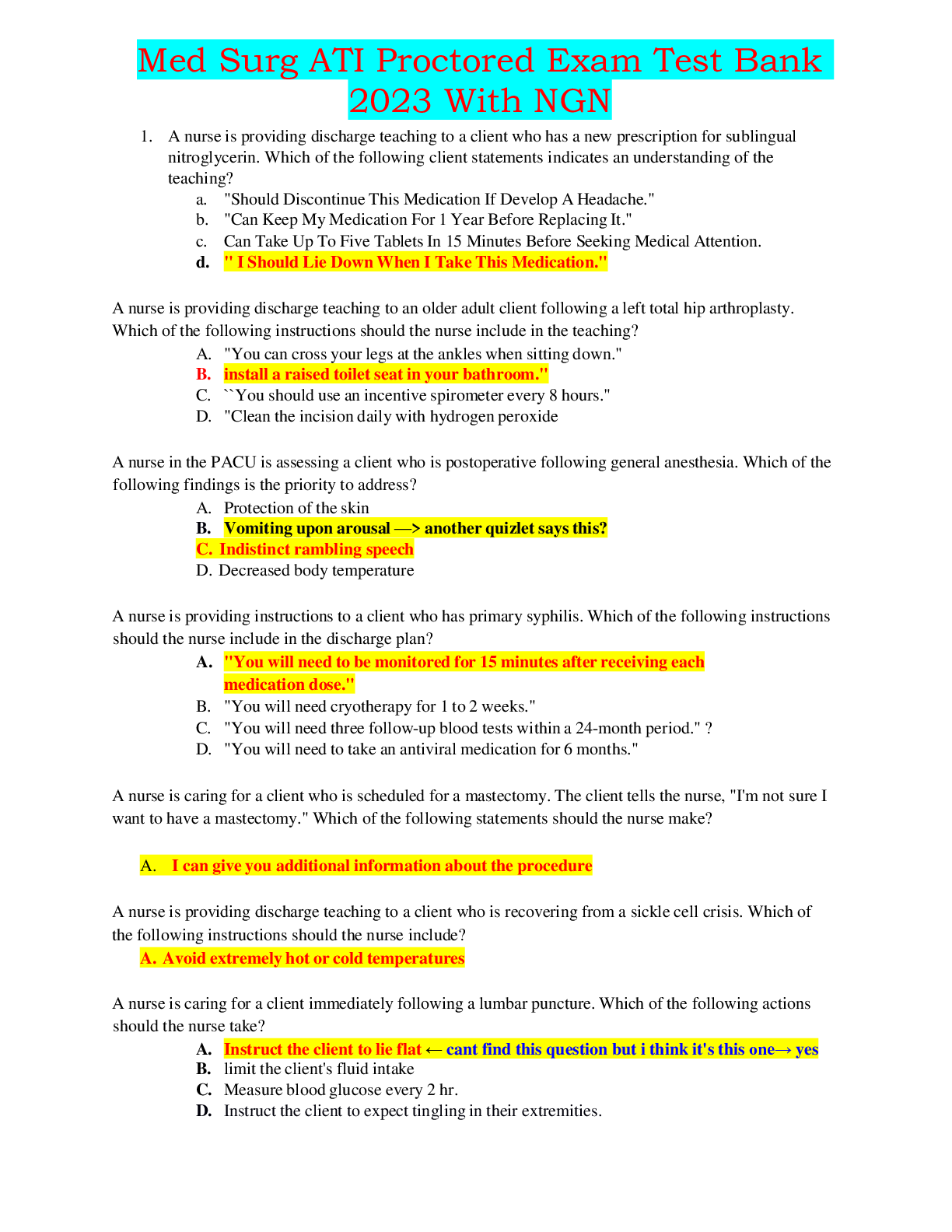
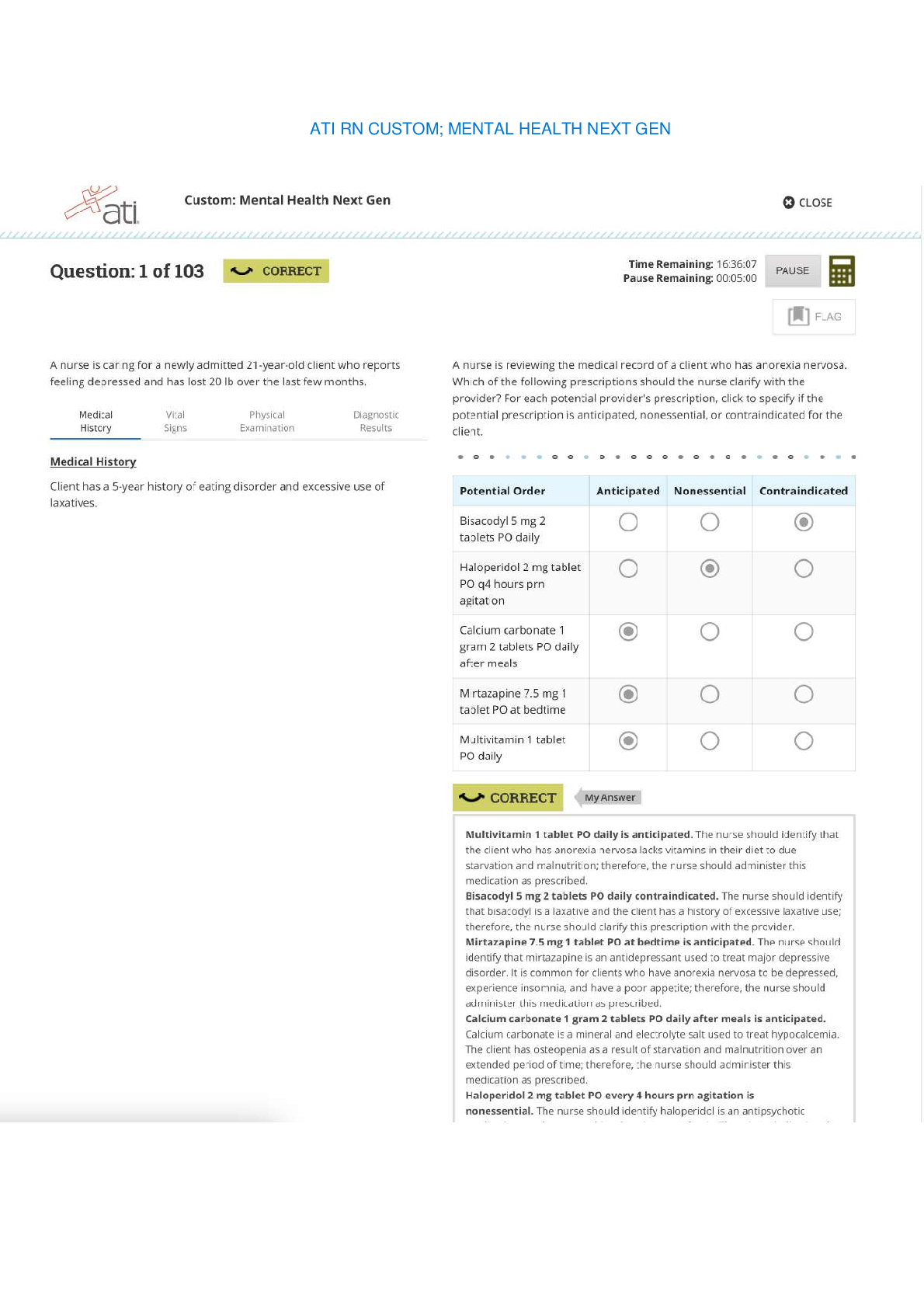
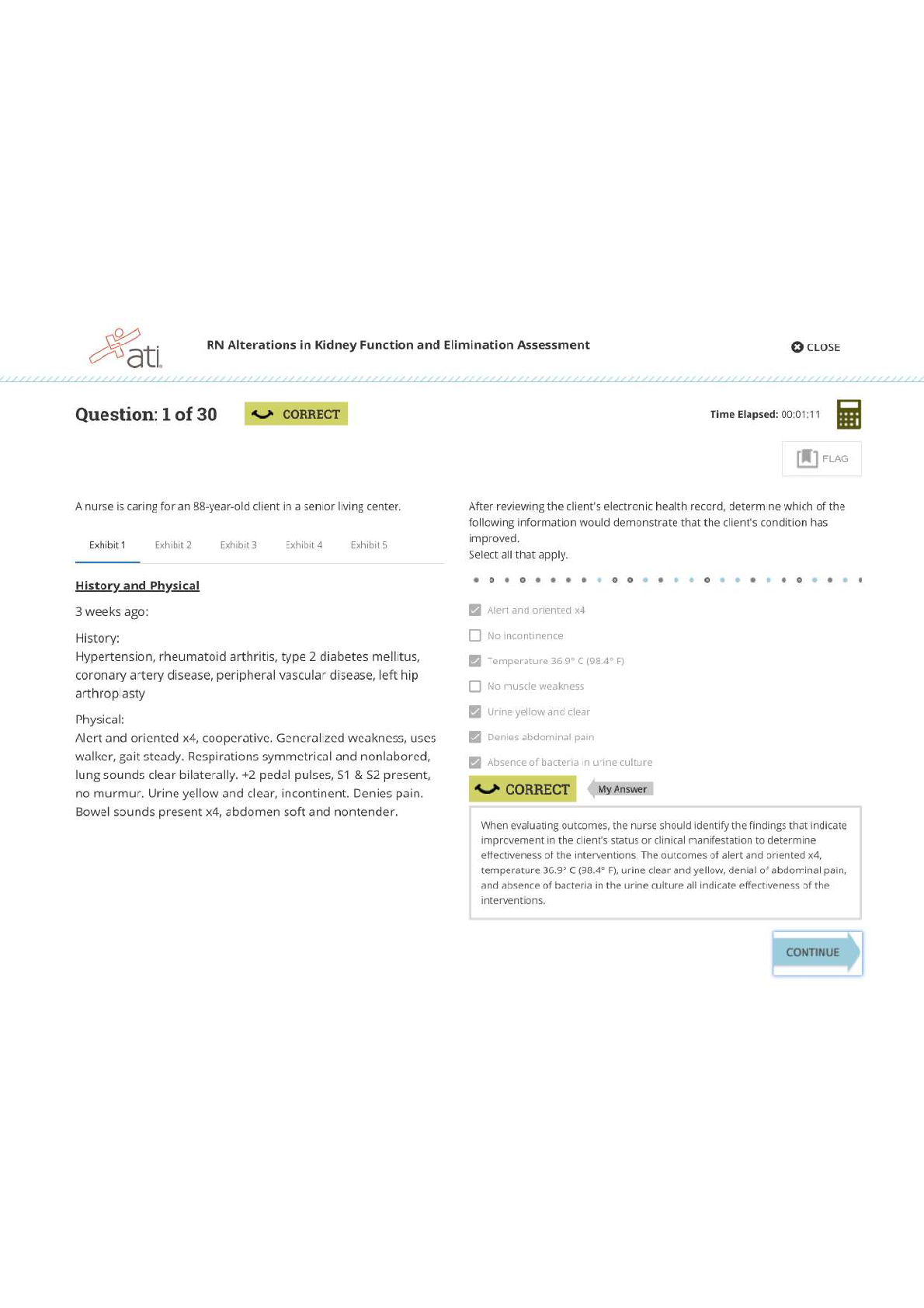
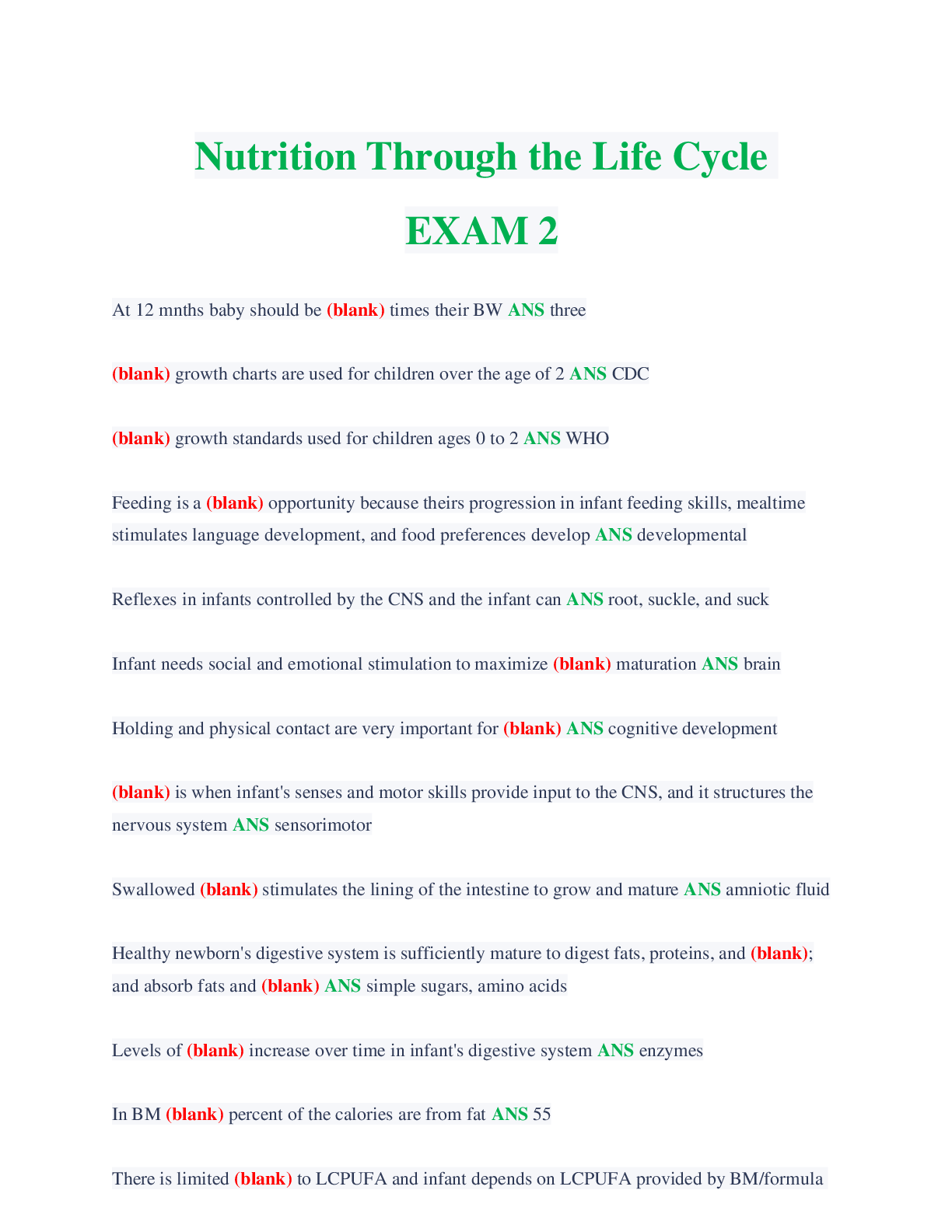
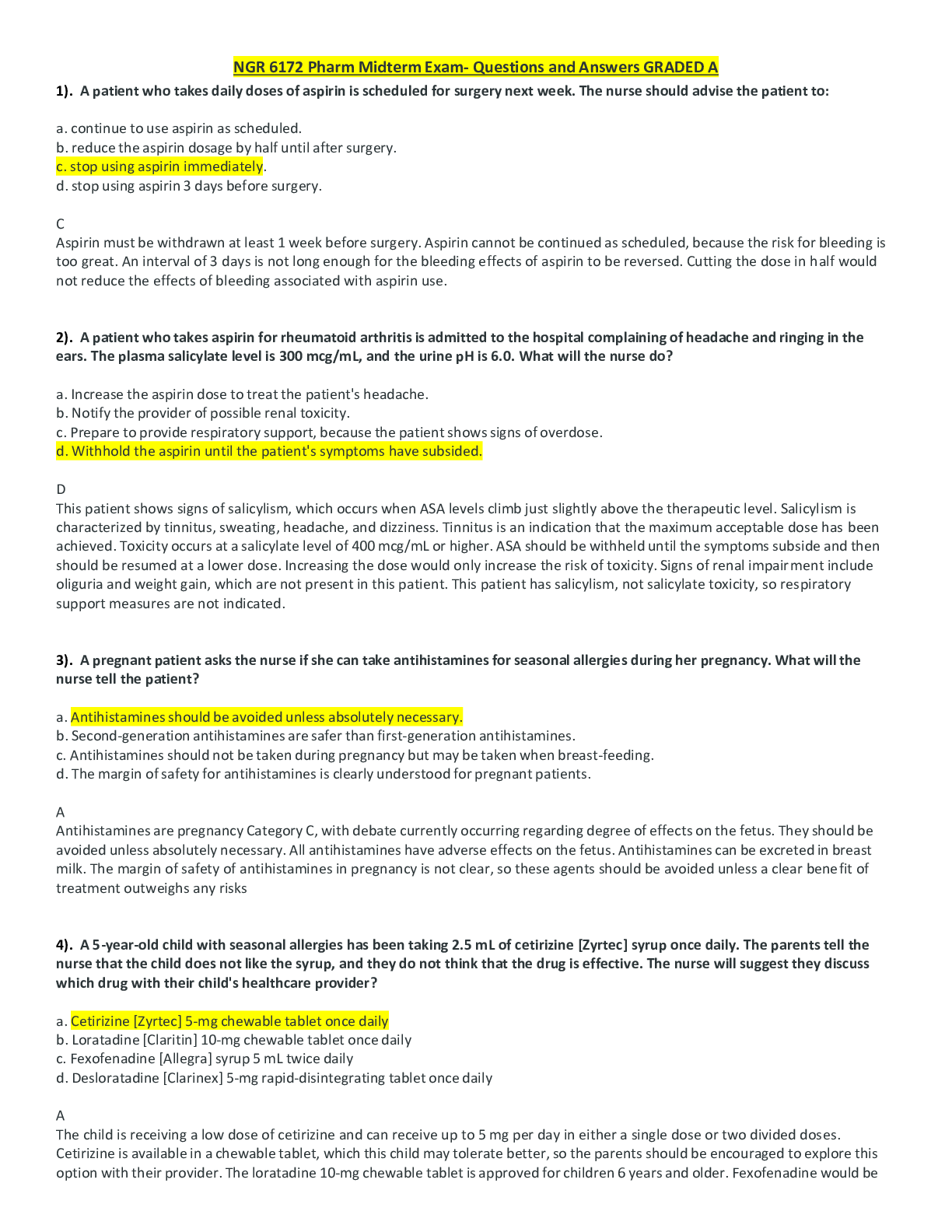
Sharing and reporting information is essential to detecting potential insider threats. True or False? (Ans - True Two security professionals - Paul and Ashley - are discussing security program ar... eas. Paul says that Information Security practitioners train and/or advise Original Classification Authorities in the application of the process for making classification determinations. Ashley says that Physical Security practitioners work with a facility's Antiterrorism Officer to deploy defensive measures designed to reduce the facility's vulnerability from terrorist attacks. (Ans - Paul and Ashley are both correct Two security professionals - Paul and Ashley - are discussing security program areas. Paul says that Information Security practitioners work with a facility's Antiterrorism Officer to deploy defensive measures designed to reduce the facility's vulnerability from terrorist attacks. Ashley says that Personnel Security practitioners train and/or advise Original Classification Authorities in the application of the process for making classification determinations. (Ans - Paul and Ashley are both incorrect SPeD is an abbreviation for? (Ans - Security Professional Education Development SPed is a certification program of what agency? (Ans - Department of Defense Security Fundamentals Professional Certification (SFPC) definition? (Ans - The individual understands foundational security concepts, principles, and practices. (Core Certification for SPed). Security Asset Protection Professional Certification (SAPPC) definition? (Ans - The Individual applies foundational security concepts, principles, and practices. (Core Certification for SPed). Security Program Integration Professional Certification (SPIPC) definition? (Ans - The individual understands and applies risk assessment and security program management based on security concepts, principles, and practices. (Core Certification for SPed). Security Enterprise Professional Certification (SEPC) definition? (Ans - The individual understands and applies concepts, principles, and practices for managing enterprise-wide security. What are the three principle incident/events required to be reported to DoD Counterintelligence (CI) organizations? (Ans - Espionage, Sabotage, Terrorism & Cyber Policy PMO is an abbreviation for? (Ans - Program Management Office Provides the legal requirements to use lawful means to ensure U. S. receives the best intelligence available? (Ans - E.O. 12333 The manual that includes CI-related requirements for Industry? (Ans - DoD 5220.22-M (NISPOM) Regulation mandating CI-specific training, briefing, and reporting? (Ans - DoDI5240.6: CI Awareness, Briefing, and Reporting Programs Regulation providing procedures to follow when classified information is compromised? (Ans - DoD 5200.1-R: information Security Program What are three principle incidents/events required to report to DoD counterintelligence (CI) organizations? (Ans - Espionage, Sabotage, Terrorism & Cyber Policy List three different types of threats to classified information? (Ans - Insider Threat, Foreign Intelligence Entities (FIE), Cybersecurity Threat List three indicators of insider threats? (Ans – Failure to report overseas travel or contact with foreign nationals. Seeking to gain higher clearance or expand access outside the job scope. Engaging in classified conversations without a need to know. Working hours inconsistent with job assignment or insistence on working in private. Exploitable behavior traits. Repeated security violations. Attempting to enter areas not granted access to. List three elements that should be considered in identifying Critical Program Information? (Ans – - Cause significant degradation in mission effectiveness - Shorten the expected combat-effective life of the system - Reduce technological advantage - Significantly alter program direction - Enable an adversary to defeat, counter, copy, or reverse-engineer the technology or capability. [Show More]
Last updated: 1 year ago
Preview 1 out of 19 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 18, 2022
Number of pages
19
Written in
Additional information
This document has been written for:
Uploaded
Nov 18, 2022
Downloads
0
Views
86