Business > EXAM > Qualys Reporting Strategies and Best Practices 39 Questions with Verified Answers,100% CORRECT (All)
Qualys Reporting Strategies and Best Practices 39 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
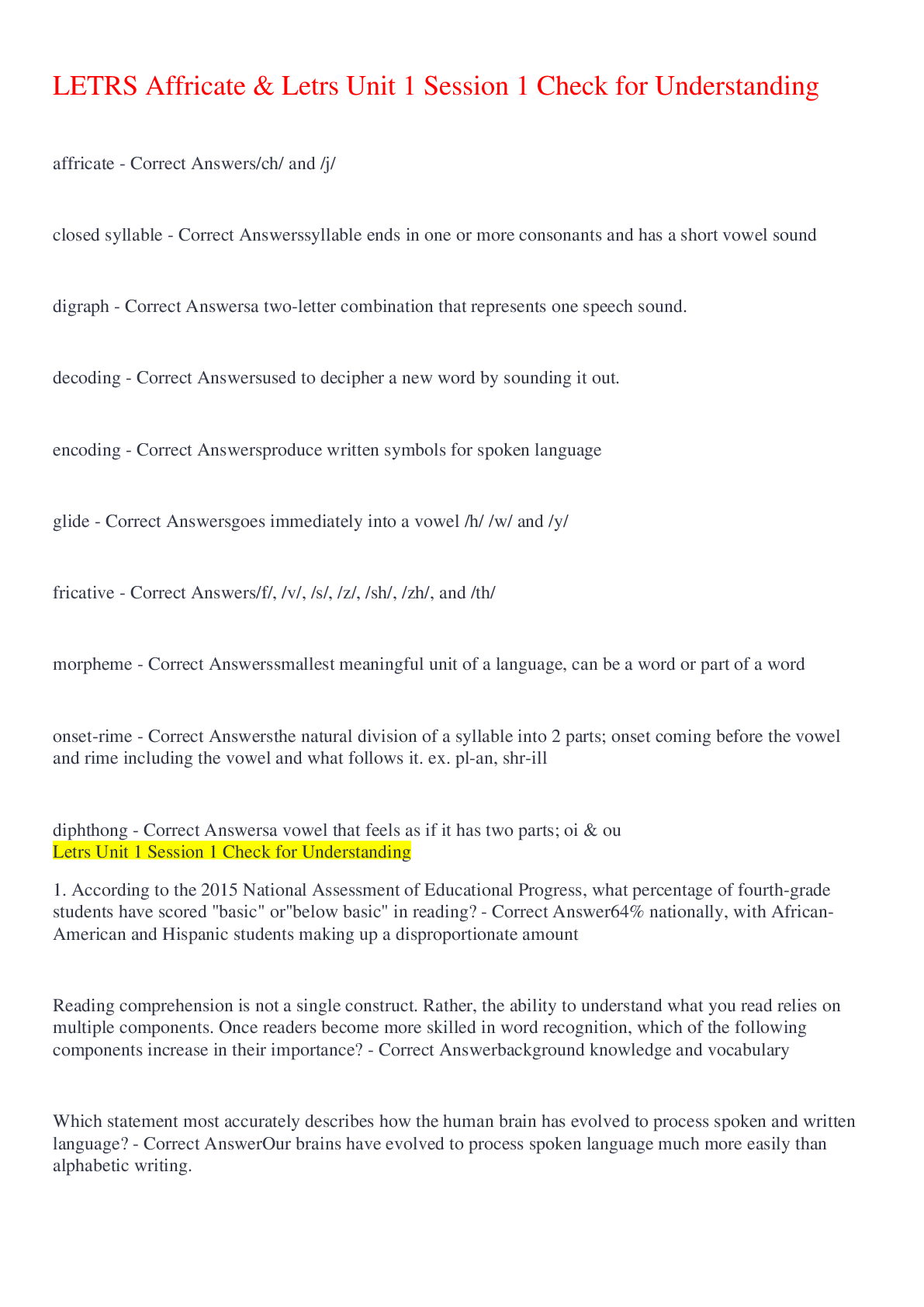
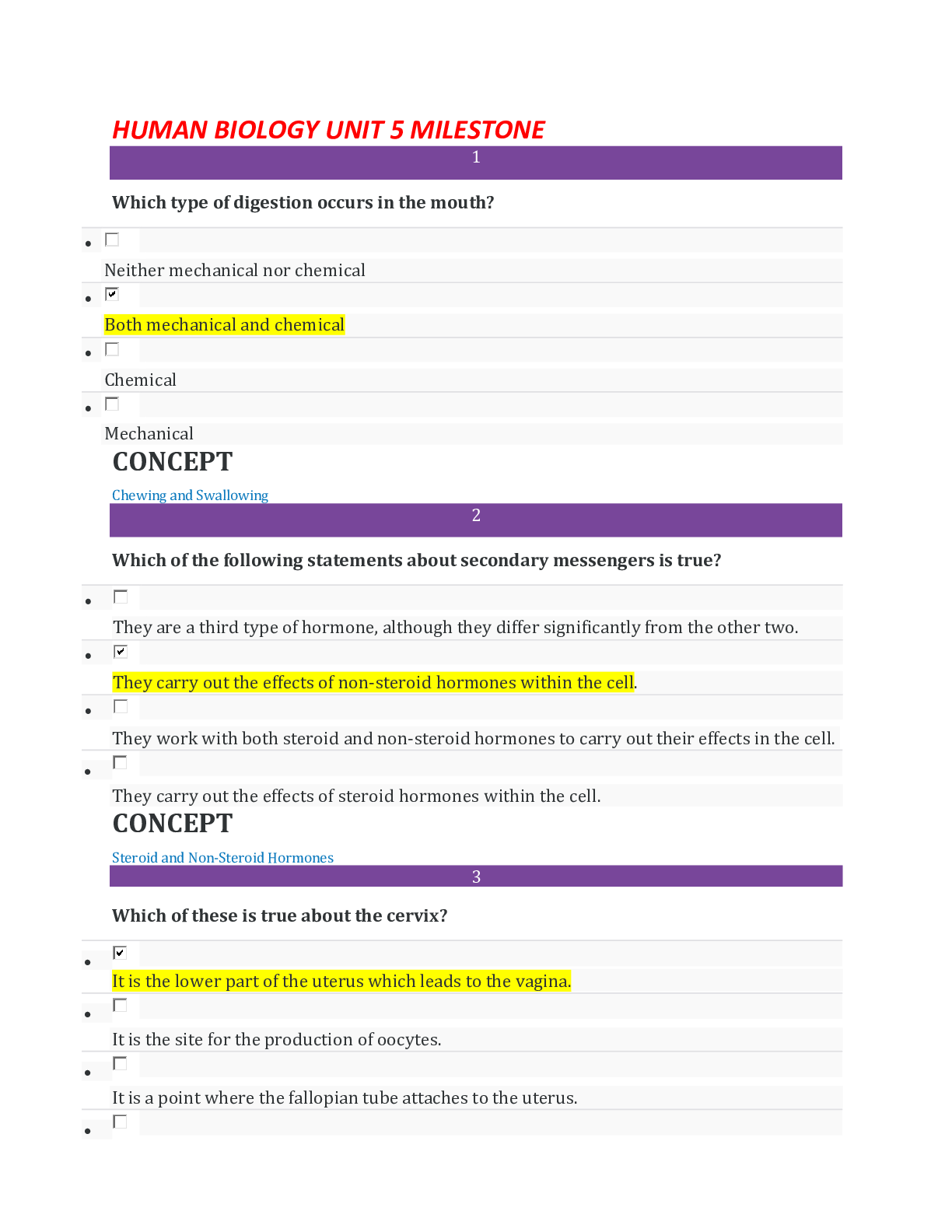
Qualys Reporting Strategies and Best Practices 39 Questions with Verified Answers Identify the different Qualys sensors that collect data from your environment. (Select all that apply)*** (A) ... Scanner (B) Cloud Agents (C) Passive Sensor (D) Container Sensor (E) Cloud Connector - CORRECT ANSWER (A) Scanner (B) Cloud Agents (C) Passive Sensor (D) Container Sensor (E) Cloud Connector _______________ is a lightweight agent that can be installed on clients and servers for real-time visibility.*** (A) Container Sensor (B) Scanner (C) API (D) Cloud Agent - CORRECT ANSWER Cloud Agent Which of the following sensors continuously monitors all network traffic, profiles devices, and flags any asset activity?*** (A) Container Sensor (B) API (C) Passive Sensor (D) Out-of-band - CORRECT ANSWER (C) Passive Sensor Qualys vulnerability severity ranking is solely based on CVSS scores.*** (A) True (B) False - CORRECT ANSWER (B) False Which of the following are recommended best practices for reporting?*** (A) Align reporting routine with scanning (B) Maintain a good purging practice (C) Build reports based on the requirements of the relevant stakeholders (D) Avoid using trend data as it requires more time for report generation (E) Use scan based reports as much as possible - CORRECT ANSWER (A) Align reporting routine with scanning (B) Maintain a good purging practice (C) Build reports based on the requirements of the relevant stakeholders Using _____________ you can select specific types of vulnerabilities based on corporate severity rankings. (Select all that apply)*** (A) APIs (B) Search Queries (C) Dashboard widgets (D) Qualys Search List (E) Qualys application for Splunk, Qradar, etc. - CORRECT ANSWER (B) Search Queries (D) Qualys Search List Reports that use host-based findings are influenced by changes in the number and type of service ports targeted.*** (A) True (B) False - CORRECT ANSWER (A) True Which of the following are the impacts of stale and inconsistent data?*** (A) Inaccurate remediation performance (B) Dashboards and reports produce erroneous results (C) Vulnerability tickets will continue to remain open (D) Inaccurate security risks calculation and SLA metrics (E) Reduce scan performance - CORRECT ANSWER (A) Inaccurate remediation performance (B) Dashboards and reports produce erroneous results (C) Vulnerability tickets will continue to remain open (D) Inaccurate security risks calculation and SLA metrics Which of the following scan configuration changes impact reports? (Select all that apply) *** (A) Change in scan performance settings (B) Change in authentication mode (C) Change to vulnerability detection criteria (D) Change in target ports for host discovery (E) Change in target for ports scanning - CORRECT ANSWER (B) Change in authentication mode (C) Change to vulnerability detection criteria (E) Change in target for ports scanning Purging an asset causes the associated scan findings to be deleted.*** (A) True (B) False - CORRECT ANSWER (B) False What is the recommended action if the asset is decommissioned, and the IP address of the asset will not be used again?*** (A) Subscribe (B) Add (C) Remove (D) Purge - CORRECT ANSWER (C) Remove What is the recommended action if the asset is decommissioned, and the IP address of the asset will be used again?*** (A) Purge (B) Add (C) Subscribe (D) Remove - CORRECT ANSWER (A) Purge Which report option allows a Qualys user to interact with the report data and get a high-level view of data that is required on an ongoing basis?*** (A) APIs (B) Dashboards (C) Search Queries (D) VM Report Templates - CORRECT ANSWER (B) Dashboards Which of the following reporting option allows a non-Qualys user to access report data?*** (A) Widgets (B) Dashboards (C) VM Report Templates (D) Search Queries - CORRECT ANSWER (C) VM Report Templates Which of these is recommended to be used when you need to bulk export data?*** (A) Dashboards (B) VM Reporting (C) Queries (D) APIs - CORRECT ANSWER (D) APIs Which of these Qualys Applications can be used to build widgets that can represent FIXED vulnerabilities?*** (A) Vulnerability Management (B) AssetView (C) Global AI (D) Threat Protection - CORRECT ANSWER (A) Vulnerability Management Which of these applications provides threat indicators that can be correlated with vulnerabilities?*** (A) Vulnerability Management (B) Asset Inventory (C) AssetView (D) Threat Protection - CORRECT ANSWER (D) Threat Protection Which of these is NOT a Qualys Real-time Threat Indicator?*** (A) Phishing (B) High Data Loss (C) Zero-Day (D) Solorigate Suburst - CORRECT ANSWER (A) Phishing Which of these is not a valid vulnerability status?*** (A) Reopened (B) New (C) Active (D) Patched - CORRECT ANSWER (D) Patched Which of the following search query does not represent a correctly formatted query type?*** (A) NOT tags.name:'Cloud Agent' (B) vulnerability.severity:[3..5] (C) LastFullScan>now-90d (D) vulnerability.severity:[1,2,3] - CORRECT ANSWER (B) vulnerability.severity:[3..5] Scan-based findings can only be generated when a host has been scanned using a scanner appliance. (A) True (B) False - CORRECT ANSWER (A) True It is possible to display or exclude vulnerabilities associated with non-running kernels.*** (A) False (B) True - CORRECT ANSWER (B) True Which of the following apply to template-based reporting?*** (A) Is intended to generate reports that are easy to read, understand and prioritize (B) Is designed for large scale data exports (C) Is intended for exporting every vulnerability from a subscription (D) Is designed to be interactive - CORRECT ANSWER (A) Is intended to generate reports that are easy to read, understand and prioritize What is the maximum report storage size that can be assigned per user?*** (A) 200MB (B) 100MB (C) 500MB (D) 1GB - CORRECT ANSWER (A) 200MB Which of these reports can be used to identify the latest patches that need to be installed to address open vulnerabilities? (Select all that apply) (A) Compliance report (B) Remediation report (C) Scan report with "Exclude Superseded Patches" option selected (D) Patch report (E) Vulnerability Scorecard report - CORRECT ANSWER (A) Compliance report (B) Remediation report (D) Patch report As a pre-requisite, which of these needs to be enabled in an authentication record for findings from the authenticated scan of a scanner appliance and the Cloud Agent to be merged? (A) IP-based tracking (B) Agentless tracking (C) DNS-based tracking (D) BetBios tracking - CORRECT ANSWER (B) Agentless tracking Which of these report types provides high-level data to assess the overall security status of your assets?*** (A) Patch report (B) Scorecard report (C) Scan report (D) Authentication report - CORRECT ANSWER (B) Scorecard report Which of the following display options are not available for selection when the trending option is not included under Host-based findings in the report template? (Select all that apply) (A) Vulnerabilities by Severity over Timeterm-33 (B) Business Rick by Asses Group over Time (C) 10 Most Prevalent Vulnerabilities (D) Vulnerabilities by Severity (E) Vulnerabilities by Status - CORRECT ANSWER (A) Vulnerabilities by Severity over Time (B) Business Rick by Asses Group over Time Patch supersedence is only applicable to OS level patch QIDs.*** (A) False (B) True - CORRECT ANSWER (B) True To display host details such as identification information for Cloud Agents or cloud related information, the Sort by option in the report template must be set to ________. (A) Asset Group (B) Vulnerability (C) Operating System (D) Host - CORRECT ANSWER (D) Host How do you identify vulnerabilities that are currently ignored on selected hosts? *** (A) By using a static search list (B) By using a dynamic search list (C) by using vulnerability report (D) By using the Ignored Vulnerability report - CORRECT ANSWER (D) By using the Ignored Vulnerability report When you create a Remediation policy to ignore a vulnerability a ______________ is used to identify specific vulnerabilities to ignore.*** (A) Search List (B) APIs (C) Search Query (D) Widget - CORRECT ANSWER (A) Search List Which of these steps are required to set up exception handling using remediation policies in Vulnerability Management? (Select all that apply)*** (A) Monitoring ignored vulnerabilities (B) Create Remediation Policy to ignore specific vulnerabilities (C) Define criteria for exception handling (D) Create Search List to filter specific vulnerabilities (E) Reorder rules to place Remediation Policy to ignore vulnerabilities at the top - CORRECT ANSWER (A) Monitor ignored vulnerabilities (B) Create Remediation Policy to ignore specific vulnerabilities (C) Define criteria for exception handling (D) Create Search List to filter specific vulnerabilities (E) Reorder rules to place Remediation Policy to ignore vulnerabilities at the top Existing Patch Tuesday dashboard users should consider __________ following a new Patch Tuesday release to retain current historical trend data for vulnerability tracking.*** (A) Creating a custom dashboard (B) Importing the new Patch Tuesday Widget into an existing dashboard (C) Creating a custom widget (D) Importing the new Patch Tuesday dashboard - CORRECT ANSWER (D) Importing the new Patch Tuesday dashboard Which of the following are recommended best practices when configuring a VM scan report template? (Select all that apply) (A) Selecting Asset Group(s) or Asset Tag(s) as report targets (B) Selecting a very large timeframe for trending data (C) Selecting the "All" Asset Group as report target (D) Including all vulnerability findings in the report (E) Including specific vulnerabilities using Search List filter(s) - CORRECT ANSWER (A) Selecting specific Asset Group(s) or Asset Tag(s) as report targets (E) Including specific vulnerabilities using Search List filter(s) Which of the following methods can be used if you need to create a search list with a very large number of CVE IDs (when the count exceeds the maximum number of CVE IDs that can be added in the Search List UI)? (Select all that apply)*** (A) Using QQl search query for CVE IDs in the report (B) There is no way to support this use case (C) By changing an account setting in the Qualys backend to include more CVE IDs (D) Splitting the CVE IDs into two or more search lists (E) Using Dynamic Search List API - CORRECT ANSWER (D) Splitting the CVE IDs into two or more search lists (E) Using Dynamic Search List API (A) (B) (C) (D) - CORRECT ANSWER (A) (B) (C) (D) - CORRECT ANSWER (A) (B) (C) (D) - CORRECT ANSWER [Show More]
Last updated: 10 months ago
Preview 1 out of 11 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$8.50
Document information
Connected school, study & course
About the document
Uploaded On
Aug 30, 2023
Number of pages
11
Written in
Additional information
This document has been written for:
Uploaded
Aug 30, 2023
Downloads
0
Views
42