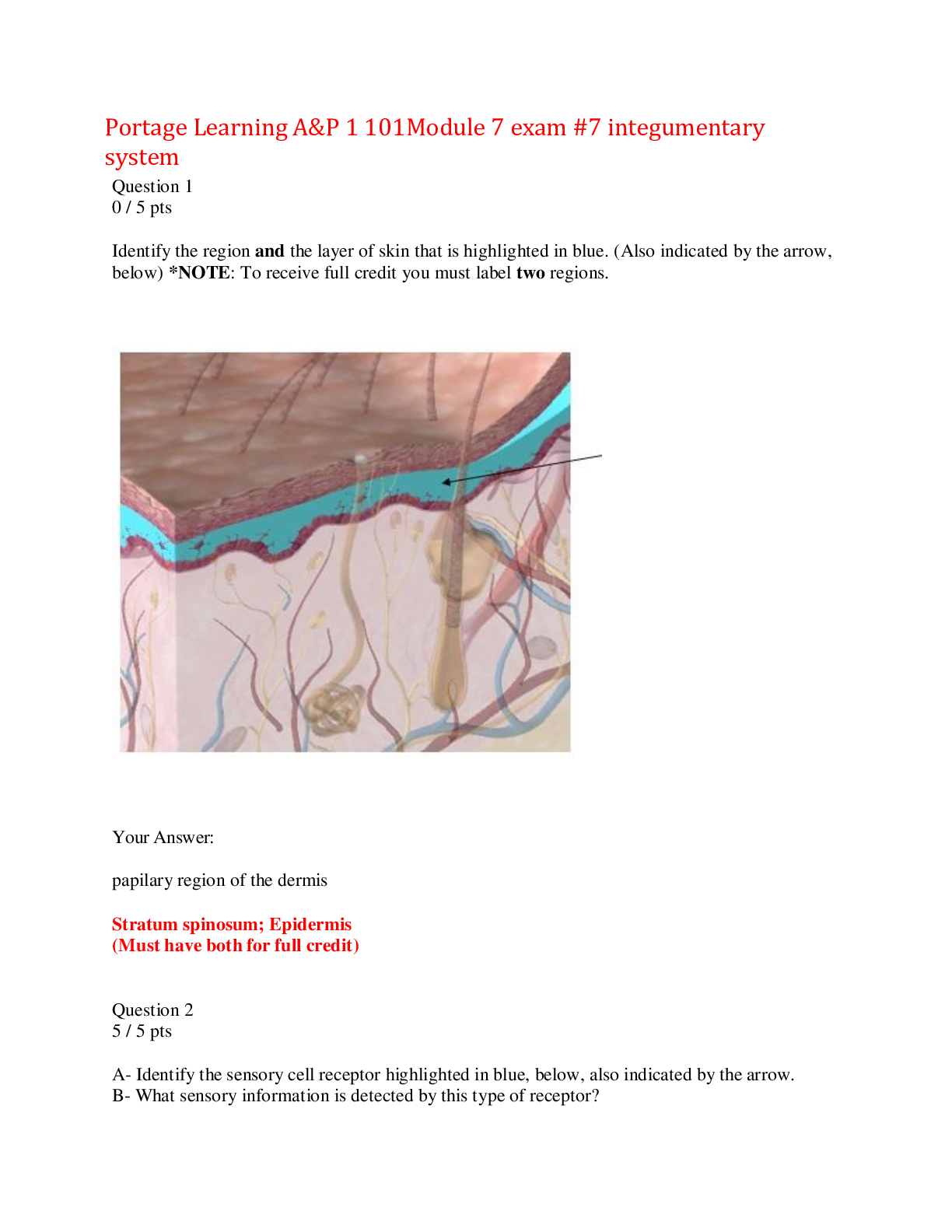
PCNSA Exam 352 Questions with Verified Answers,100% CORRECT
Document Content and Description Below
PCNSA Exam 352 Questions with Verified Answers Palo Alto NGFWs enable you to adopt security best practices to minimize opportunities for attack by using the following *three* policy types... - CORR... ECT ANSWER Application, User, and Content based policies. T/F: Palo Alto NGFWs allow you to automate workflows via integration with administrative tools such as ticketing services, or any system with a RESTful API. - CORRECT ANSWER True What are the *three* families of Palo Alto NGFWs? - CORRECT ANSWER 1) VM Series 2) Prisma Access (Cloud Firewall SaaS) 3) Physical Firewalls Name at least *three* of the physical Palo Alto NGFW models. - CORRECT ANSWER 1) PA-220 2) PA800 3) PA-3200 4) PA-5200 5) PA-7000 Older models include: PA-200, PA-500, PA-3000 and PA-5000. What capabilities does Palo Alto Traps *Advanced Endpoint Protection* provide? - CORRECT ANSWER Advanced Endpoint Protection blocks: exploits, ransomware, malware, and fileless attacks to minimize infected endpoints and servers. What does *AutoFocus* provide? - CORRECT ANSWER AutoFocus provides instant access to community-based threat data, enhanced with deep context and attribution from the Unit 42 threat research team, saving analysts time and effort. How often is the WildFire cloud database updated? - CORRECT ANSWER Approximately every *5* minutes. What is Palo Alto *WildFire*? - CORRECT ANSWER WildFire is a cloud based malware analysis and zero day exploit detection feature. What is Palo Alto *Threat Prevention*? - CORRECT ANSWER Threat Prevention is an IPS feature for detecting network signatures. What is Palo Alto *URL Filtering*? - CORRECT ANSWER URL Filtering is a feature for categorizing web traffic and preventing phishing attempts. What is Palo Alto *MineMeld*? - CORRECT ANSWER MineMeld is a threat intelligence aggregation tool for gathering and applying IOCs at the firewall. What is Palo Alto *Cortex Data Lake*? - CORRECT ANSWER Cortex Data Lake is a tool for collecting and managing vast amounts of security logs. What is Palo Alto *Cortex XDR*? - CORRECT ANSWER Cortex XDR is a machine learning *UBA tool*, for detecting post-intrusion activities, such as risky behavior, data exfiltration, or anomalies. The Palo Alto Networks Security Operating Platform is designed for which *three* purposes? A) consume innovations quickly B) ensure compliance C) focus on what matters D) prevent successful cyberattacks - CORRECT ANSWER *A)* consume innovations quickly *C)* focus on what matters *D)* prevent successful cyberattacks Which item is not one of the six primary components of the Palo Alto Networks Security Operating Platform? A) applications (Palo Alto Networks applications, third-party applications, customer applications) B) Cloud-Delivered Security Services C) WildFire D) Cortex and Cortex Data Lake E) Network Security F) Advanced Endpoint Protection G) Cloud Security - CORRECT ANSWER *C)* WildFire Which cloud-delivered security service provides instant access to community-based threat data? A) Prisma SaaS B) AutoFocus C) Threat 42 D) Cortex XDR - CORRECT ANSWER B) AutoFocus Which cloud-delivered security service provides security for branches and mobile users? A) MineMeld B) Cortex XDR C) AutoFocus D) Prisma Access - CORRECT ANSWER *D)* Prisma Access Which Palo Alto Networks Security Operating Platform component provides *access to applications* from Palo Alto Networks, third parties, and customers? A) Cloud-Delivered Security Services B) WildFire C) Cortex D) Network Security E) Advanced Endpoint Protection - CORRECT ANSWER C) Cortex Which Palo Alto Networks firewall feature provides all the following abilities? • Stops malware, exploits, and ransomware before they can compromise endpoints • Provides protection while endpoints are online and offline, on network and off • Coordinates enforcement with network and cloud security to prevent successful attacks • Detects threats and automates containment to minimize impact • Includes WildFire cloud-based threat analysis service with your Cortex XDR subscription • Integrates with the Palo Alto Networks Security Operating Platform A) Cortex XDR B) Prisma SaaS C) URL Filtering D) WildFire E) GlobalProtect F) AutoFocus - CORRECT ANSWER *A)* Cortex XDR What architecture does Palo Alto use to reduce latency with processing packets? - CORRECT ANSWER Single-Pass Parallel Processing (SP3) architecture. What are the *two* components of Single-Pass Parallel Processing (SP3) architecture? - CORRECT ANSWER 1) Single-Pass Software 2) Parallel Processing Hardware T/F: Management and Data planes have dedicated hardware resources (CPU, RAM, and storage), making them independent of each other. - CORRECT ANSWER True T/F: When administrator is running a very processor-intensive report, he/she may notice the firewall has decreased ability to process packets. - CORRECT ANSWER False The firewall would not be affected by this reporting job, because there is separation of the data and control (management) planes. What are some of the *management features* the control plane provides the firewall with? - CORRECT ANSWER 1) Firewall configuration 2) Logging 3) Reporting What are some of the *data processing* features the data plane provides the firewall with? - CORRECT ANSWER 1) Signature matching 2) Security processing 3) Network processing Which plane is signature matching part of, and what are some of the things signature matching can identify? - CORRECT ANSWER Signature matching is part of the data plane. Signature matching can identify: exploits (IPS), viruses, spyware, CC#s, and SSNs. Which plane is security processing part of, and what are some of the things security processing handles? - CORRECT ANSWER Security processing is part of the data plane. Security processing handles: App-ID, User-ID, URL match, policy match, app decoding, SSL/IPSEC, and decompression. Which plane is network processing part of, and what are some of the things network processing handles? - CORRECT ANSWER Network processing is part of the data plane. Network processing handles: flow control, route lookup, MAC lookup, QoS, and NAT. Which *three* management features does the control plane provide? A) security processing B) logging C) reporting D) firewall configuration E) signature matching F) network processing - CORRECT ANSWER *B)* logging *C)* reporting *D)* firewall configuration Which *three* data processing features does the data plane provide? A) network processing B) security processing C) signature matching D) firewall configuration E) logging F) reporting - CORRECT ANSWER *A)* network processing *B)* security processing *C)* signature matching Which *three* of the following components are part of the Network Processing module? A) QoS B) NAT C) App-ID D) flow control E) url match F) spyware - CORRECT ANSWER *A)* QoS *B)* NAT *D)* flow control Which approach most accurately defines the Palo Alto Networks *SP3 architecture*? A) prioritize first B) sequential processing C) scan it all, scan it once D) zero trust segmentation platform - CORRECT ANSWER *C)* scan it all, scan it once What is the result of using a stream-based design of architecture? A) superior performance B) increased latency C) superior latency D) increased functionality - CORRECT ANSWER *A)* superior performance What is the *zero trust* security model? - CORRECT ANSWER Zero Trust is an alternative security model that addresses the shortcomings of the traditional, perimeter-centric strategies. Where is the blindspot in traditional *perimeter* security models? - CORRECT ANSWER Traditional perimeter security models have a blindspot with monitoring lateral (east-west) traffic within the network. Which security model does Palo Alto Networks recommend that you deploy? A) separation-of-trust B) zero trust C) trust-then-verify D) never trust - CORRECT ANSWER *B)* zero trust The Zero Trust model is implemented to specifically inspect which type of traffic? - CORRECT ANSWER East-West (Lateral) What are the *three* main concepts of Zero Trust? A) All resources are accessed in a secure manner, regardless of location. B) Access control is on a "need-to-know" basis and is strictly enforced. C) Credentials need to be verified. D) All traffic is logged and inspected. E) Internal users are trusted implicitly. F) External users are trusted explicitly. - CORRECT ANSWER *A)* All resources are accessed in a secure manner, regardless of location. *B)* Access control is on a "need-to-know" basis and is strictly enforced. *D)* All traffic is logged and inspected. Which *three* Palo Alto Networks products secure your network? A) MineMerge B) Prisma SaaS C) URL filtering D) Containers E) TrapContent F) WildFire - CORRECT ANSWER *B)* Prisma SaaS *C)* URL filtering *F)* WildFire According to Palo Alto, what are the *six* stages of the Cyber Attack Lifecycle? - CORRECT ANSWER 1) Reconnaissance 2) Weaponization & Delivery 3) Exploitation 4) Installation 5) Command & Control 6) Actions on the Objective How do network security zones assist the zero trust model? - CORRECT ANSWER Network security zones segment traffic and allow for inspection between zones. T/F: Blocking just one stage in the Cyber-Attack Lifecycle is all that is needed to protect a company's network from attack. - CORRECT ANSWER True Which of the following are stages of the Cyber-Attack Lifecycle? (Choose two.) A) weaponization and delivery B) manipulation C) extraction D) command and control - CORRECT ANSWER *A)* weaponization and delivery *D)* command and control Command and control be prevented through which *two* methods? A) exploitation B) DNS Sinkholing C) URL filtering D) reconnaissance - CORRECT ANSWER *B)* DNS Sinkholing *C)* URL filtering Exploitation can be mitigated by which actions? (Choose two.) A) keeping systems patched B) using local accounts C) blocking known and unknown vulnerability exploits on the endpoint D) providing admin credentials - CORRECT ANSWER *A)* keeping systems patched *C)* blocking known and unknown vulnerability exploits on the endpoint What are the *four* methods used to manage the Palo Alto Networks next-generation firewalls? - CORRECT ANSWER 1) Web interface 2) CLI 3) Panorama 4) XML API What is required to accomplish tasks like retrieving licenses and updating the threat and application signatures on the firewall? - CORRECT ANSWER The firewall must be able to access the Internet via its management (MGT) port. To gain access to the firewall for the first time, what *four* pieces of information are needed for the MGT port? - CORRECT ANSWER 1) IP address 2) Netmask 3) Default gateway 4) At least one DNS server address Note: If the firewall is set up as a DHCP client, this information will be included automatically via DHCP. What is the default username and password for a Palo Alto Firewall? - CORRECT ANSWER Username: admin Password: admin What benefit does CLI access to the firewall offer admins? - CORRECT ANSWER Debug information. What CLI command allows you to access configuration mode while in operational mode? - CORRECT ANSWER *configure* What are some basic networking commands available from the CLI, while in operational mode? - CORRECT ANSWER Ping, traceroute, etc. Which mode enables you to display and modify the configuration parameters of the firewall, verify candidate configuration, and commit the config? - CORRECT ANSWER Configuration Mode What CLI command would show you both your system up-time and MAC address? - CORRECT ANSWER *show system state* What is the name of the Palo Alto Networks product that provides centralized web-based management, reporting, and logging for multiple firewalls? - CORRECT ANSWER Panorama How does the Palo Alto XML API work? - CORRECT ANSWER The XML API provides a representational state transfer (REST)-based interface to access firewall configurations, operational status, reports, and packet captures from the firewall. What sort of tasks can the PAN-OS XML API be used to automate? - CORRECT ANSWER 1) Create, update, and modify firewall and Panorama configurations. 2) Execute operational mode commands, such as restarting the system or validating configurations. 3) Retrieve reports. 4) Manage users through User-ID. 5) Update dynamic objects without having to modify or commit new configurations. What is the firewall dashboard? - CORRECT ANSWER *It is the home screen for the web management GUI.* The firewall Dashboard provides information in a condensed format, including general information such as device name, MGT IP address, and licensing information. This page can be augmented by adding, removing, or editing widgets. What are the *three* categories of widgets that can be displayed on the firewall dashboard? - CORRECT ANSWER 1) Application Widgets 2) Log Widgets 3) System Widgets What is the *ACC* tab used for? - CORRECT ANSWER *ACC* uses the firewall logs to graphically depict traffic trends on your network. What is the *Monitor* tab used for? - CORRECT ANSWER The *Monitor* tab provides logging visibility, the ability to run packet captures, and report options. What is the *Policies* tab used for? - CORRECT ANSWER *Policies* allows the creation of policies such as security policy and NAT policy. What is the *Objects* tab used for? - CORRECT ANSWER *Objects* allows the creation of objects such as Address objects. What is the *Network* tab used for? - CORRECT ANSWER *Network* allows the configuration of network parameters such as interfaces and zones. What is the *Device* tab used for? - CORRECT ANSWER *Device* allows the configuration of system information such as the hostname or certificates. What does the *task* icon in the bottom right of the GUI do? - CORRECT ANSWER It displays the tasks that you, other administrators, or the PAN-OS software have initiated since the last firewall reboot (for example, manual commits or automatic FQDN refreshes). What is the management interface used for? - CORRECT ANSWER The management interface is used to communicate with servers and systems including: *DNS*, *Email*, *Palo Alto Servers*, *external dynamic lists*, and Panorama. What are service routes? - CORRECT ANSWER Service routes are used so that the communication between the firewall management interface and various servers goes through the data ports on the data plane. These data ports require appropriate security policy rules before external servers can be accessed. What is the navigation path within the Palo Alto GUI, for customizing service routes? - CORRECT ANSWER Device *>* Setup *>* Services *>* Service Route Configuration *>* Customize Which *three* important *network services* do Palo Alto NGFWs integrate with? - CORRECT ANSWER 1) DHCP 2) NTP 3) DNS T/F: Palo Alto NGFWs can operate without a primary DNS server configured. - CORRECT ANSWER False What is the GUI path for configuring a DNS server or NTP server for the Palo Alto to use? - CORRECT ANSWER Device > Setup > Services > Services_gear_icon What is the GUI path for configuring an IP address or default gateway for the Palo Alto management interface? - CORRECT ANSWER Device > Setup > Interfaces What are *two* firewall management methods? A) CLI B) RDP C) VPN D) XML API - CORRECT ANSWER *A)* CLI *D)* XML API Which *two* devices are used to connect a computer to the firewall for management purposes? A) rollover cable B) serial cable C) RJ-45 Ethernet cable D) USB cable - CORRECT ANSWER *B)* serial cable *C)* RJ-45 Ethernet cable What is the default IP address on the *MGT interface* of a Palo Alto Networks firewall? A) 192.168.1.1 B) 192.168.1.254 C) 10.0.0.1 D) 10.0.0.254 - CORRECT ANSWER *A)* 192.168.1.1 What are the *two* default services that are available on the MGT interface? A) HTTPS B) SSH C) HTTP D) Telnet - CORRECT ANSWER *A)* HTTPS *B)* SSH T/F: Service route traffic has Security policy rules applied against it. - CORRECT ANSWER True Service routes may be used to forward which *two* traffic types out a data port? A) External Dynamic Lists B) MineMeld C) Skype D) Palo Alto Networks updates - CORRECT ANSWER *A)* External Dynamic Lists *D)* Palo Alto Networks updates Where do candidate configurations reside? - CORRECT ANSWER Candidate configurations reside in memory on the *control plane*. Where do running configurations reside? - CORRECT ANSWER Running configurations reside in memory on the *data plane*. Which file format is used for importing and exporting candidate configurations? - CORRECT ANSWER *.xml* How do you undo a candidate configuration? - CORRECT ANSWER Using the *revert to last saved configuration* option. What operation is necessary to write the candidate configuration to the running configuration? - CORRECT ANSWER *commit* When firewall commits are queued, which commits does the firewall prioritize? - CORRECT ANSWER Commits that the firewall initiates automatically, such as FQDN refreshes. What is the GUI path for managing firewall configurations? - CORRECT ANSWER *Device > Setup > Operations* What is the name of the file that stores the firewall's running configuration? - CORRECT ANSWER *running-config.xml* What are the *five* configuration management options? - CORRECT ANSWER 1) Revert 2) Save 3) Load 4) Export 5) Import T/F: The firewall creates a timestamped version of the running configuration whenever a commit is made. - CORRECT ANSWER True Which command backs up configuration files to a remote network device? A) import B) load C) copy D) export - CORRECT ANSWER *D)* export The command *load named configuration snapshot* overwrites the current candidate configuration with which *three* items? A) custom-named candidate configuration snapshot (instead of the default snapshot) B) custom-named running configuration that you imported C) snapshot.xml D) current running configuration (running-config.xml) E) Palo Alto Networks updates - CORRECT ANSWER *A)* custom-named candidate configuration snapshot (instead of the default snapshot) *B)* custom-named running configuration that you imported *E)* Palo Alto Networks updates What is the path used to download the latest firewall updates? - CORRECT ANSWER *Device > Dynamic Updates* T/F: System updates do not require a firewall reboot. - CORRECT ANSWER False Which *three* actions should you complete before you upgrade to a newer version of software? A) Review the release notes to determine any impact of upgrading to a newer version of software. B) Ensure the firewall is connected to a reliable power source. C) Export the device state. D) Create and externally store a backup before you upgrade. - CORRECT ANSWER *A)* Review the release notes to determine any impact of upgrading to a newer version of software. *B)* Ensure the firewall is connected to a reliable power source. *D)* Create and externally store a backup before you upgrade. Before you install the maintenance or feature release, which release is required to be installed? - CORRECT ANSWER The x.0 base release. For example, to upgrade from 7.x.y to 8.x.y, download both 8.0 and 8.x.y. 8.0 automatically is installed when you install 8.x.y. What's a quick way to verify that the firewall is passing traffic, after finishing an upgrade? - CORRECT ANSWER Select *Monitor > Session Browser* and verify that you are seeing new sessions. What is the *shortest* time interval that you can configure a Palo Alto Networks firewall to download WildFire updates? A) 1 minute B) 5 minutes C) 15 minutes D) 60 minutes - CORRECT ANSWER *A)* 1 minute What is the publishing interval for WildFire updates, with a valid WildFire license? A) 1 minute B) 5 minutes C) 15 minutes D) 60 minutes - CORRECT ANSWER *B)* 5 minutes T/F: A Palo Alto Networks firewall automatically provides a backup of the configuration during a software upgrade. - CORRECT ANSWER True If you have a Threat Prevention subscription but not a WildFire subscription, how long must you wait for the WildFire signatures to be added into the antivirus update? A) 1 to 2hours B) 2 to 4hours C) 10 to 12 hours D) 12 to 48 hours - CORRECT ANSWER *D)* 12 to 48 hours Which of the following is *not* a way to download software? A) over the MGT interface on the control plane B) over a data interface on the data plane C) upload from a computer D) from the Palo Alto Networks Customer Support Portal E) from the PAN-DB database F) from Panorama - CORRECT ANSWER *E)* from the PAN-DB databaseE) from the PAN-DB database How can you tell whether a user account is local? - CORRECT ANSWER If the account has *no* authentication profile, then it is a local account. What are the *two* admin user role types? - CORRECT ANSWER 1) Role Based 2) Dynamic Where would you find the username, IP, and time for a past change made to the firewall? - CORRECT ANSWER *Configuration logs* display entries for changes to the firewall configuration. Name at least *three* authentication types that PAN-OS software supports. - CORRECT ANSWER 1) None 2) Local Database 3) RADIUS 4) LDAP 5) TACACS+ 6) SAML 7) Kerberos Which *two* statements are true about a Role Based Admin Role profile role? A) It is a built-in role. B) It can be used for CLI commands. C) It can be used for XML API. D) Superuser is an example. - CORRECT ANSWER *B)* It can be used for CLI commands. *C)* It can be used for XML API. Note: Role based profiles are customized, not default; and superuser is not one of them. Which *two* Dynamic Admin Role types are available on the PAN-OS software? A) superuser B) superadmin C) deviceuser D) device administrator (read-only) - CORRECT ANSWER *A)* superuser *D)* device administrator (read-only) Which type of profile does an Authentication Sequence include? A) Security B) Authorization C) Admin D) Authentication - CORRECT ANSWER *D)* Authentication An Authentication Profile includes which other type of profile? A) Server B) Admin C) Customized D) Built-in - CORRECT ANSWER *A)* Server T/F: Dynamic Admin Roles are called "dynamic" because you can customize them. - CORRECT ANSWER False What is used to override global Minimum Password Complexity Requirements? A) Authentication Profile B) Local Profile C) Password Role D) Password Profile - CORRECT ANSWER *D)* Password Profile T/F: Zone names are not case sensitive. - CORRECT ANSWER False What are the *two* requirements for creating zones? - CORRECT ANSWER 1) Zone Name 2) Zone Type What is *intrazone traffic*? - CORRECT ANSWER Intrazone traffic is traffic that flows between interfaces that exist within the same zone. For Example: Traffic flowing from one server in the datacenter zone to another server in the datacenter zone. What is the default action for interzone traffic? - CORRECT ANSWER Deny What are the *five* zone types? - CORRECT ANSWER 1) TAP 2) Layer 2 3) Layer 3 4) Virtual Wire 5) Tunnel Which *two* default zones are included with the PAN-OS software? A) Interzone B) Extrazone C) Intrazone D) Extranet - CORRECT ANSWER *A)* Interzone *C)* Intrazone The *External* zone type is used to pass traffic between which type of objects? A) Layer 2 interfaces B) Layer 3 interfaces C) virtual routers D) virtual systems - CORRECT ANSWER *D)* virtual systems Which *two* statements about interfaces are correct? A) Interfaces must be configured before you can create a zone. B) Interfaces do not have to be configured before you can create a zone. C) An interface can belong to only one zone. D) An interface can belong to multiple zones. - CORRECT ANSWER *B)* Interfaces do not have to be configured before you can create a zone. *C)* An interface can belong to only one zone. Which three interface types can belong in a Layer 3 zone? A) loopback B) Layer 3 C) tunnel D) virtual wire - CORRECT ANSWER *A)* loopback *B)* Layer 3 *C)* tunnel What are used to control traffic through zones? A) access lists B) security policy lists C) security policy rules D) access policy rules - CORRECT ANSWER *C)* security policy rules What are the main *five* interfaces types for PAN-OS software? - CORRECT ANSWER 1) Tap 2) Virtual Wire 3) Layer 2 4) Layer 3 5) HA What does a *decrypt mirror* interface do? - CORRECT ANSWER This feature enables decrypted traffic from a firewall to be copied and sent to a traffic collection tool that can receive raw packet captures, such as NetWitness or Solera, for archiving and analysis. What does a *tap* interface do? - CORRECT ANSWER A Tap interface monitors traffic that is connected to a network switch's MIRROR/SPAN port. This mirrored traffic is forwarded by a switch port to a firewall's Tap interface and is analyzed for App-ID, User-ID, Content-ID, and other traffic, just like any other normal data traffic that would pass through the firewall. T/F: TAP interfaces must be assigned to a Tap zone. - CORRECT ANSWER True What actions can be taken on *tap* traffic? - CORRECT ANSWER None. Tap traffic is not managed, and cannot be blocked, allowed, or shaped. What is the function of a *log card* data port? - CORRECT ANSWER A log card data port performs log forwarding for syslog, email, Simple Network Management Protocol (SNMP), and WildFire file forwarding. Note: One data port on a PA-7000 must be configured as a log card interface because the MGT interface cannot handle all the logged traffic. What does a *virtual wire* interface do when it receives a frame or packet for Layer 2 or Layer 3 addresses for switching or routing purposes? - CORRECT ANSWER Traffic passing over a virtual wire does not receive routing or switching, but the virtual wire applies any *security* or *NAT policy rules* before passing an allowed frame or packet over the virtual wire to the second Virtual Wire interface and on to the network device connected to it. T/F: A virtual wire can bind two physical Ethernet interfaces of the same medium (both either copper or fiber), but cannot bind a copper interface to a fiber interface. - CORRECT ANSWER False A virtual wire can bind any combination of copper or fiber medium over it's two interfaces. What is a virtual wire *subinterface*? - CORRECT ANSWER Virtual Wire subinterfaces are used to separate traffic into different zones. These subinterfaces can do things like route traffic from various VLANs or subnets to various zones. Traffic *A* is moving between two Palo Alto interfaces of the same VLAN and same zone. Traffic *B* is moving between two Palo Alto interfaces of the same VLAN and but different zones. What occurs differently with traffic *B* when it arrives at the Palo Alto? - CORRECT ANSWER Traffic *B* will be inspected by security policy rules, while traffic *A* is intrazone traffic and would be allowed by default. Which firewall *tab* contains options that enable you to configure Layer 3 interface settings? - CORRECT ANSWER The *Advanced* tab. What are some of the configurable *Layer 3* interface settings? - CORRECT ANSWER 1) MTU 2) static ARP 3) LLDP 4) IPv6 NDP 5) link speed 6) duplex settings What are some uses for the Palo Alto *loopback* interfaces? - CORRECT ANSWER 1) DNS sinkholes. 2) GlobalProtect service interfaces (portals and gateways). 3) Routing identification. Which of the following interfaces can be used for managing a firewall? A) Tap B) Virtual Wire C) Layer 2 D) Layer 3 - CORRECT ANSWER *D)* Layer 3 Note: Firewall management through a layer 3 interface requires an interface management profile. What is the purpose of an interface management profile? - CORRECT ANSWER An interface management profile protects the firewall from unauthorized access by defining the protocols, services, and IP addresses that a firewall Layer 3 interface permits for management traffic. T/F: A single Layer 3 interface can be assigned multiple IPv4 addresses. - CORRECT ANSWER True Note: The IPs should not be in the same subnet. What's the path for adding a virtual router? - CORRECT ANSWER *Network > Virtual Routers > Add* What is the main difference between Layer 3 *interfaces* and Layer 3 *subinterfaces*? - CORRECT ANSWER Layer 3 subinterfaces are used for 802.1Q VLANs. Which *two* actions can be done with a Tap interface? A) encrypt traffic B) decrypt traffic C) allow or block traffic D) log traffic - CORRECT ANSWER *B)* decrypt traffic *D)* log traffic Which *two* actions can be done with a Virtual Wire interface? A) NAT B) route C) switch D) log traffic - CORRECT ANSWER *A)* NAT *D)* log traffic Which *two* actions can be done with a Layer 3 interface? A) NAT B) route C) switch D) create a Virtual Wire object - CORRECT ANSWER *A)* NAT *B)* route Layer 3 interfaces support which *two* items? A) NAT B) IPv6 C) switching D) spanning tree - CORRECT ANSWER *A)* NAT *B)* IPv6 Layer 3 interfaces support which *three* advanced settings? A) IPv4 addressing B) IPv6 addressing C) NTP configuration D) NDP configuration E) link speed configuration F) link duplex configuration - CORRECT ANSWER *D)* NDP configuration *E)* link speed configuration *F)* link duplex configuration Layer 2 interfaces support which *three* items? A) spanning tree blocking B) traffic examination C) forwarding of spanning tree BPDUs D) traffic shaping via QoS E) firewall management F) routing - CORRECT ANSWER *B)* traffic examination *C)* forwarding of spanning tree BPDUs *D)* traffic shaping via QoS Which *two* interface types support subinterfaces? A) virtual wire B) Layer 2 C) loopback D) tunnel - CORRECT ANSWER *A)* virtual wire *B)* Layer 2 Note: Subinterfaces are often used for tasks like setting up VLAN tagging. Which *two* statements are true regarding Layer 3 interfaces? A) You can configure a Layer 3 interface with one or more as a DHCP client. B) You can assign only one IPv4 addresses to the same interface. C) You can enable an interface to send IPv4 Router Advertisements by selecting the Enable Router Advertisement check box on the Router Advertisement tab. D) You can apply an interface management profile to the interface. - CORRECT ANSWER *A)* You can configure a Layer 3 interface with one or more as a DHCP client. *D)* You can apply an interface management profile to the interface. Each Layer 3 Ethernet, loopback, VLAN, and tunnel interface defined on the firewall must be associated with what? - CORRECT ANSWER A virtual router. What are the *four* dynamic routing protocols available with Palo Alto firewalls? - CORRECT ANSWER 1) BGP4 2) OSPFv2 3) OSPVv3 4) RIPv2 What are some of the multicast routing protocols available with Palo Alto firewalls? - CORRECT ANSWER 1) IGMPv1 2) IGMPv2 3) IGMPv3 4) PIM-SM 5) PIM-ASM 6) PIM-SSM Where does the firewall populate learned routes to? - CORRECT ANSWER The firewall's IP routing information base (RIB). Where are *best* next-hop routes defined? - CORRECT ANSWER The firewall's forwarding information base (FIB). What is used to set preference for one dynamic routing protocol over another? - CORRECT ANSWER Administrative distances. The lowest values (distances) have the most preference. By default, which routes have the *lowest* (most preferred) administrative distances? - CORRECT ANSWER Static Routes What is *path monitoring*? - CORRECT ANSWER Path monitoring is a Palo Alto feature that continuously pings upstream interfaces to determine the reliability of static routes. Which path monitoring setting determines the max number of unreturned ICMP pings before a route is considered down? - CORRECT ANSWER *ping count* What happens when path monitoring determines a route is down? - CORRECT ANSWER The down route is then *removed* from the routing table, until it's next-hop becomes responsive again. What is the default administrative distance of a static route within the PAN-OS software? A) 1 B) 5 C) 10 D) 100 - CORRECT ANSWER *C)* 10 Which *two* dynamic routing protocols are available in the PAN-OS software? A) RIP1 B) RIPv2 C) OSPFv3 D) EIGRP - CORRECT ANSWER *B)* RIPv2 *C)* OSPFv3 Which value is used to distinguish the best route within the *same* routing protocol? A) metric B) weight C) distance D) cost E) administrative distance - CORRECT ANSWER *A)* metric Which type of security policy should come first in the firewall security policy list, *specific* policies or *general* policies? - CORRECT ANSWER Specific policies should occur first. T/F: The default security policy rules cannot be modified. - CORRECT ANSWER False What are the names of the *two* default security policy rules? - CORRECT ANSWER 1) intrazone-default 2) interzone-default Which statement is true? A) For Intrazone traffic, traffic logging is enabled by default. B) For Interzone traffic, traffic logging is enabled by default. C) For Universal traffic, traffic logging is enabled by default. D) For any rule type, traffic logging is enabled by default. - CORRECT ANSWER *C)* For Universal traffic, traffic logging is enabled by default. Which Palo Alto security policies (rules) are considered *explicit*? - CORRECT ANSWER Any rule created by an administrator is considered explicit. What is a *shadow rule warning*? - CORRECT ANSWER A shadow rule warning indicates that a broader rule matching the criteria is configured *above* the more specific rule. T/F: System reboots, dataplane restarts, and upgrades have no effect on security policy *hit count*. - CORRECT ANSWER True T/F: Renaming a security policy resets the *hit count*. - CORRECT ANSWER True. What is the best practice for security policy logging? - CORRECT ANSWER All security policies should have some form of *logging enabled*. In most cases, *on session end* would be the preferred logging method. Which type of security policy rules most often exist *above* the two predefined security policies? A) intrazone B) interzone C) universal D) global - CORRECT ANSWER *C)* universal What are the two types of *NAT*? - CORRECT ANSWER Source NAT (SNAT) and Destination NAT (DNAT) What are the *three* SNAT types? - CORRECT ANSWER 1) Static IP (1 IP always maps to another) 2) Dynamic IP (1 IP maps to next available IP) 3) Dynamic IP & Port (IP and Port map to next available) For a Palo Alto firewall that handles NAT, which *IP* is used for the *source* of the security policy? A) The Post-NAT IP B) The Pre-NAT IP - CORRECT ANSWER B) The pre-NAT IP is used. For a Palo Alto firewall that handles NAT, which *zone* is used for the source of the security policy? The Post-NAT zone or the Pre-NAT zone? - CORRECT ANSWER The post-NAT zone is used. T/F: The default security policy rules cannot be modified. - CORRECT ANSWER False They can be modified. T/F: The default security policy rules cannot be modified. - CORRECT ANSWER False What are the *three* components of rule usage? - CORRECT ANSWER 1) Hit Count 2) First Hit 3) Last Hit What is the benefit of *bidirectional* NAT? - CORRECT ANSWER Bidirectional NAT enables you to eliminate the need to create an additional NAT policy rule for the incoming traffic. What is the "DIPP NAT Oversubscription Rate?" - CORRECT ANSWER The DIPP NAT Oversubscription Rate is the number of times that the same translated IP address and port pair can be used concurrently. What are the *two* DNAT types? - CORRECT ANSWER 1) Static IP 2) Dynamic IP (with session distribution) A simple way to remember how to configure security policy rules where NAT was implemented is to memorize the following: A) post-NAT zone, post-NAT zone B) post-NAT IP, post-NAT zone C) pre-NAT IP, post-NAT zone D) pre-NAT IP, pre-NAT zone - CORRECT ANSWER *C)* pre-NAT IP, post-NAT zone Which of the following *two* options are types of destination NAT? A) dynamic IP (with session distribution) B) DIPP C) global D) static - CORRECT ANSWER *A)* dynamic IP (with session distribution) *D)* static Which statement is true regarding bidirectional NAT? A) For static translations, bidirectional NAT enables the firewall to create a corresponding translation in the opposite direction of the translation you configure. B) For static translations, bidirectional NAT enables the firewall to create a corresponding translation in the same direction of the translation you configure. C) For dynamic translations, bidirectional NAT enables the firewall to create a corresponding translation in the opposite direction of the translation you configure. D) For dynamic translations, bidirectional NAT enables the firewall to create a corresponding translation in the same direction of the translation you configure. - CORRECT ANSWER *A)* For static translations, bidirectional NAT enables the firewall to create a corresponding translation in the opposite direction of the translation you configure. What are the *four* default values for DIPP NAT oversubscription? - CORRECT ANSWER 1) 1x: means no oversubscription, where each IP address and port pair can be used only one time. 2) 2x: oversubscribed two times 3) 4x: oversubscribed three times 4) 8x: oversubscribed eight times What is *application shift*? - CORRECT ANSWER Application shift is when an applications changes during the lifetime of a session. For example: A user types www.icloud.com into a web browser to access their iCloud email. This initial request goes out as an HTTP request, and the application is recognized as web-browsing. After the HTTP request is completed, the application is changed to icloud-base. After the icloud-base application is processed, the application changes to icloud-mail. When creating a security policy, why might an application like google-base not require dependent applications like web-browsing and ssl to also be added the security policy? - CORRECT ANSWER In this case (and in other cases) the firewall determines that web-browsing and ssl are dependent applications, and would implicitly allow them for google-base application traffic. What are *two* application dependencies for icloud-mail? A) ssl B) skype C) google-base D) icloud-base - CORRECT ANSWER *A)* ssl *D)* icloud-base What does an application filter enable an administrator to do? A) manually categorize multiple service filters B) dynamically categorize multiple service filters C) dynamically categorize multiple applications D) manually categorize multiple applications - CORRECT ANSWER *C)* dynamically categorize multiple applications Which *two* items can be added to an application group? A) application groups B) application services C) application filters D) admin accounts - CORRECT ANSWER *A)* application groups *C)* application filters What are the *five* properties that define all applications in the App-ID database? - CORRECT ANSWER 1) Category & Sub-Category 2) Risk 3) Tag 4) Characteristic 5)Technology What is the numeric range for application risk scores? - CORRECT ANSWER Applications have a risk score of *1 - 5*, with 5 being the highest risk. What are the *nine* application characteristics? - CORRECT ANSWER 1) Capable of File Transfer 2) Excessive Bandwidth Use 3) Tunnels Other Applications 4) Has Known Vulnerabilities 5) Used by Malware 6) Evasive 7) Pervasive 8) Prone to Misuse 9) Continue Scanning for Other Applications What numeric value should be used to specify the default timeout value for an application? - CORRECT ANSWER *0* (zero) When configuring application settings, what is the *TCP Half Closed timeout setting* used for? - CORRECT ANSWER This value sets the maximum length of time that a session remains in the session table *between* receiving the first FIN and receiving the second FIN or RST. If the timer expires, the session is closed. When configuring application settings, what is the *TCP Time Wait* timeout setting used for? - CORRECT ANSWER This value sets the maximum length of time that a session remains in the session table *after* receiving the first FIN and receiving the second FIN or RST. If the timer expires, the session is closed. What is the main risk involved with App-ID *updates*? - CORRECT ANSWER An application that was previously categorized under a generic App-ID, like web-browsing, may now be categorized under its own unique App-ID. This could break previously created rules or require new rules to be created. Which checkbox feature can be selected to minimize risks involved with APP-ID updates? - CORRECT ANSWER "Disable new apps in content update." T/F: Application and Threat updates can be scheduled for recurrence on specific days at specific times. - CORRECT ANSWER True Which *column* in the Applications and Threats screen includes the options Review Apps and Review Policies? A) Features B) Type C) Version D) Action - CORRECT ANSWER *D)* Action Which link can you select in the web interface to minimize the risk of installing new App-ID updates? A) Enable new apps in content B) Disable new apps in app-id database C) Disable new apps in content D) Enable new apps in App-ID database - CORRECT ANSWER *C)* Disable new apps in content What is a *DUG* and what are it's benefits? - CORRECT ANSWER Dynamic User Groups (DUGs) control access to resources managed by firewall policies. They can be created using dynamic information, such as LDAP groups, which can efficiently reflect changes in an environment. What are the *five* threat level severities? - CORRECT ANSWER 1) Critical 2) High 3) Medium 4) Low 5) Informational Which security profile would block suspected C2 traffic or other outbound post-exploitation threats? - CORRECT ANSWER The anti-spyware security profile. Which security profile would block suspected JavaScript malware? - CORRECT ANSWER The anti-virus security profile. Which security profile would block a suspected buffer overflow or other inbound threats? - CORRECT ANSWER The vulnerability protection security profile. Which security profile would block a suspected hacking websites? - CORRECT ANSWER The URL filtering security profile. When packets traverse a Palo Alto firewall, what are the *two* primary stages of inspection? - CORRECT ANSWER 1) Security Policy Stage 2) Security Profile Stage What are the pros and cons for *deny* vs *drop* actions? - CORRECT ANSWER *Drop*: - Good for defense. Bad for user experience. - Typical action for external (inbound) traffic. *Deny*: - Good for user experience. Bad for defense. - Typical action for internal (outbound) traffic. What is the benefit of the *alert* action? - CORRECT ANSWER While the traffic is allowed, a Threat Log entry is created. If a security profile has an action of reset-client, reset-server, or reset both, what occurs if the traffic is UDP based, rather than TCP based? - CORRECT ANSWER UDP traffic would simply be *dropped* in the case of these actions. Which security profile allows for a *DNS sinkhole* action? - CORRECT ANSWER Anti-Spyware security profiles. Which URL filtering security profile action prompts the user for a password, in order to access a given category? - CORRECT ANSWER The *override* action. Which URL filtering security profile *action* presents the user with a response page indicating that the site has been blocked due to company policy, but offers the user the option to continue to the website? - CORRECT ANSWER The *continue* action. Which *two* actions are available for Antivirus security profiles? A) continue B) allow C) block IP D) alert - CORRECT ANSWER *B)* allow *D)* alert What does *Safe Search Enforcement* do? - CORRECT ANSWER *Safe Search Enforcement* is a firewall feature that blocks adult search results, if the end user is not already using the strictest safe search settings in their browser search query. Which browser search engines are compatible with the *Safe Search Enforcement* feature? - CORRECT ANSWER 1) Google 2) Yahoo 3) Bing 4) Yandex 5) YouTube What are some of the attributes that can be captured with *HTTP Header Logging*? - CORRECT ANSWER 1) User Agent 2) Referrer 3) X-Forwarded For What are the *three* Palo Alto DoS attack mitigation tools? - CORRECT ANSWER 1) Zone Protection profiles 2) DoS Protection profiles and policy rules 3) Packet buffer protection How do *Zone Protection Profiles* work? - CORRECT ANSWER *Zone Protection Profiles* observe new sessions at ingress zones, then limit connections-per-second (CPS) to the firewall. Note: They also have some other minor DoS prevention features, such as port scanning prevention. How do *DoS Protection profiles* and *policy rules* prevent DoS attacks? - CORRECT ANSWER These profiles and policies provide granular control of connections-per-second (CPS) for specific devices. T/F: If a packet matches an existing session, it will bypass the Zone Protection profiles. - CORRECT ANSWER True What does *PPS* and *CPS* stand for? - CORRECT ANSWER Packets per second (PPS) and Connections per second (CPS) What are the *five* types of floods that zone protection profiles protect against? - CORRECT ANSWER 1) SYN (TCP) 2) UDP 3) ICMP 4) ICMPv6 5) Other IP How does the *SYN Random Early Drop* feature mitigate SYN flood DoS attacks? - CORRECT ANSWER When the flow exceeds the configured *activate rate threshold*, the firewall drops individual SYN packets randomly to restrict the flow. How do SYN cookies work? - CORRECT ANSWER This feature causes the firewall to act like a proxy, intercept the TCP SYN, generate a cookie on behalf of the server to which the SYN was directed, send a SYN-ACK with the cookie to the original source, and clear the SYN queue. Only when the source returns an ACK with the cookie to the firewall does the firewall consider the source valid and forward the SYN to the server. This is the preferred configuration option. What are the *three* types of scans prevented by reconnaissance protection? - CORRECT ANSWER 1) TCP Port Scans 2) Host Sweeps 3) UDP Scans What are the *five* major categories of drops for packet-based attack protection? - CORRECT ANSWER 1) IP Drop 2) TCP Drop 3) ICMP Drop 4) IPv6 Drop 5) ICMPv6 Drop What are the *two* actions taken by zone protection profiles? - CORRECT ANSWER 1) Drop Packets 2) Strip Packet Options T/F: Palo Alto firewalls can only block IP-based protocols. - CORRECT ANSWER False. Palo Altos can use *protocol protection* within a *zone protection profile* to block or allow non-IP protocols such as: LLDP, NetBEUI, Spanning Tree, and Supervisory Control and Data Acquisition (SCADA) systems such as Generic Object Oriented Substation Event (GOOSE), among many others. What are the *two* components of Denial-of-Service Protection? A) Zone Protection profile B) DoS Protection profile and policy rules C) flood protection D) reconnaissance protection - CORRECT ANSWER *A)* Zone Protection profile *B)* DoS Protection profile and policy rules Which cache contains the most frequently accessed sites, which enables quicker URL lookups? - CORRECT ANSWER The *data-place* cache. Which *two* types of attacks does the PAN-DB prevent? A) phishing sites B) HTTP based command-and-control C) infected JavaScript D) flood attacks - CORRECT ANSWER *A)* phishing sites *B)* HTTP based command-and-control Bob is sending traffic from the inside zone to the outside zone. From the *outside zone perspective*, is his traffic *ingress* or *egress*? - CORRECT ANSWER Ingress Bob is sending traffic from the inside zone to the outside zone. From the *inside zone perspective*, is his traffic *ingress* or *egress*? - CORRECT ANSWER Egress Which *two* valid URLs can be used in a custom URL category? A) ww.youtube.** B) www.**.com C) www.youtube.com D) *.youtube.com - CORRECT ANSWER *C)* www.youtube.com *D)* *.youtube.com What Palo Alto feature can be used to force users to authenticate at the firewall to use the internet, allowing the firewall to log the user's name and IP address? - CORRECT ANSWER Captive Portal What are some of the different methods of user mapping? - CORRECT ANSWER 1) Server Monitoring (Windows Event Monitoring) 2) Port mapping (Map Sessions to Source Port) 3) Syslog (Events Forwarded From Authentication Systems) 4) X-Forwarded-For (XFF Headers Forwarded from Proxy to Firewall) 5) Authentication Policy or Captive Portal (Various methods of forcing an authentication event) 6) GlobalProtect (Mobile App) 7) XML API (PAN-OS API for non-standard 3rd party appliances...) 8) Client Probing (WMI or NetBIOS host agent) What are the *three* Captive Portal authentication methods? - CORRECT ANSWER 1) Browser Challenge: Uses Kerberos or NTLAN Manager (NTLM). 2) Web Form: Uses multi-factor authentication, SAML single sign-on, Kerberos, TACACS+, RADIUS, LDAP, or local authentications. 3) Client certificate authentication. Where is zone protection applied? - CORRECT ANSWER The *ingress* interface. Note: In zero-trust environments, zone protection is applied to ingress and egress. Regardless of the organization, what is the recommended *action* for "unknown" and "malformed" packets? - CORRECT ANSWER Drop When would the *UserID integrated agent* be used? - CORRECT ANSWER 1) Environment has *less* than 100 domain controllers. 2) Environment has *less* then 50 syslog servers. 3) To save *bandwidth*. In which *three* situations would the UserID Windows agent be used? - CORRECT ANSWER 1) Environment has *more* than 100 domain controllers. 2) Environment has *more* then 50 syslog servers. 3) To save *processing cycles* on the firewall's management plane. Which of the following *three* methods can be used for mapping usernames to IP addresses? A) Server Monitoring B) Traps C) MineMeld D) Syslog E) AutoFocus F) Port mapping - CORRECT ANSWER *A)* Server Monitoring *D)* Syslog *F)* Port mapping Which type of Server Profile is used to create group mappings? A) RADIUS B) TACACS+ C) Kerberos D) LDAP - CORRECT ANSWER *D)* LDAP The Server Monitoring user mapping method can monitor which *three* types of servers? A) RADIUS B) Microsoft Domain Controllers C) Exchange Servers D) Novell eDirectory Servers - CORRECT ANSWER *B)* Microsoft Domain Controllers *C)* Exchange Servers *D)* Novell eDirectory Servers The Port Mapping user mapping method can monitor which *two* types of environments? A) Citrix B) Microsoft terminal servers C) Exchange Servers D) Linux servers - CORRECT ANSWER *A)* Citrix *B)* Microsoft terminal servers The Windows User-ID Agent can be installed on which *two* operating systems? A) Linux B) Server 2016 C) XP D) Server 2008 - CORRECT ANSWER *B)* Server 2016 *D)* Server 2008 What is *client probing*? - CORRECT ANSWER Client probing is a firewall feature that probes legacy client systems at set intervals, in order to verify a given IP still maps to a specific UserID. Note: Client probing is done using WMI or NetBIOS. Is *client probing* recommended for most networks? - CORRECT ANSWER *No*. Client probing is for legacy Windows networks, has the potential to generate a lot of network traffic, and trusts/relies on data sent from client systems. What is a Palo Alto *BPA*? - CORRECT ANSWER Best Practice Assessment (BPA) is a free tool that assesses firewall configurations and provides feedback on over 200 pass/fail criteria, with the goal of reducing the client's attack surface. What is a BPA *heatmap*? - CORRECT ANSWER The heatmap is part of a BPA, and analyzes a Palo Alto Networks deployment, measuring the adoption rate of features and capabilities across a targeted network infrastructure. What are some of the categories of the Best Practice Assessment (BPA) tool? - CORRECT ANSWER 1) Security 2) Policy Based Forwarding 3) Decryption Rulebase 4) Decryption 5) Application Override 6) Captive Portal 7) DoS Protection What is *application override*? - CORRECT ANSWER Application override is the process of creating unique service objects for custom applications used in an environment, which would otherwise appear as "unknown" to the firewall. What does *PBF* stand for, and what is it? - CORRECT ANSWER Policy-Based Forwarding (PBF) allows you to override the routing table within a firewalls virtual router, and specify the egress (outgoing) interface, rather than route the traffic based on the packet destination IP information. Identify *three* Best Practice Assessment tool primary categories from the following: A) User-ID B) Logging C) Vulnerability Protection D) Security E) Decryption F) DoS Protection - CORRECT ANSWER *D)* Security *E)* Decryption *F)* DoS Protection Which *two* security features normally do not achieve an adoption rate of 100%? A) URL Filtering B) App-ID C) Logging D) DNS Sinkhole - CORRECT ANSWER *A)* URL Filtering *D)* DNS Sinkhole Which type of file is used to generate the Heatmap report and the BPA report? A) Technical Support B) Configuration C) Statistics D) XML - CORRECT ANSWER *A)* Technical Support Which Palo Alto feature focuses on *DLP*, protecting both *PII* and *PCI*? - CORRECT ANSWER Prisma SAAS What are the *three* types of data plane processing? - CORRECT ANSWER 1) Signature Match Processing 2) Security Processing 3) Network Processing T/F: The Control Plane has its own CPU, RAM, and SSD. - CORRECT ANSWER True What are the main *two* Panorama firewall models? - CORRECT ANSWER 1) M-200 2) M-500 What is a *virtual system*? - CORRECT ANSWER A virtual system is a separate logical firewall instance within a single physical Palo Alto firewall. Which firewall *series* supports virtual systems? - CORRECT ANSWER 1) 3000 series 2) 5000 series 3) 7000 series How does the *single pass software* used by Palo Alto firewalls *reduce latency*? - CORRECT ANSWER 1) Scan content *once* (decreasing delay). 2) Use stream-based scanning (increasing throughput). How does *Parallel Processing Hardware* used by Palo Alto firewalls *improve firewall efficiency*? - CORRECT ANSWER 1) Separation of planes. 2) Specialized processing groups (many instances of dedicated hardware for specific tasks). What is the benefit of separating the *data* and *control* planes? - CORRECT ANSWER This separation means that heavy utilization of one won't negatively impact the other - for example, an administrator could be running a very processor-intensive report, and yet the ability to process packets would be completely unhindered, due to the separation of data and control planes. What makes the *Help* button efficient? - CORRECT ANSWER The *Help* button has context awareness. For example: If you are in the home dashboard area when you click the Help button, it will return a page related to the dashboard area. What CLI *command* enters the firewall into *maintenance* mode? - CORRECT ANSWER *maint* What is *admin-level commit*? - CORRECT ANSWER Admin-level commit is a feature that allows each admin to commit only their own changes to the running configuration (rather than everyone's changes). Note: This feature was first released in PAN-OS 8.0 What does the *validate-commit* button do? - CORRECT ANSWER The validate-commit button highlights any potential errors that a commit may create. What action must be taken before Palo Alto licenses can be activated for a firewall? - CORRECT ANSWER The firewall must first be *registered* through the Palo Alto customer support portal, using the firewall's *serial number*. What is represented by the *1* and the *3* when the Palo Alto dashboard states *Ethernet 1/3* is in use? - CORRECT ANSWER *1* is the Ethernet port *column number* of the physical connection. *3* is the Ethernet port *row number* of the physical connection. Which interface type is considered "a bump in the wire," and why? - CORRECT ANSWER *Virtual Wire* interfaces are considered "a bump in the wire," because traffic passes through the Palo Alto without being seen as a hop for the traffic. The virtual wire interfaces do not need IP addresses or MAC addresses assigned to them to function. Virtual routers provide support for static routing and dynamic routing using which *three* protocols? A) OSPF B) RIPv2 C) EGP D) BGP - CORRECT ANSWER *A)* OSPF *B)* RIPv2 *D)* BGP Which *three* attributes are true, regarding virtual wire interfaces? A) Sometimes called a "bump in the wire" or "transparent in-line." B) No support for routing or device management. C) Supports NAT, Content-ID, and User-ID. D) Supports SSL decryption for inbound traffic only. - CORRECT ANSWER *A)* Sometimes called a "bump in the wire" or "transparent in-line." *B)* No support for routing or device management. *C)* Supports NAT, Content-ID, and User-ID. T/F: A Layer 3 interface can be configured as dual stack with both IPv4 and IPv6. - CORRECT ANSWER True What does the *HTTP Header Insertion* feature do? - CORRECT ANSWER HTTP Header Insertion *inserts* or *overwrites* HTTP headers when an organization wants to limit application access to only enterprise versions of an application. Which *CLI command* would determine connectivity state to the PAN-DB cloud service? - CORRECT ANSWER *show url-cloud status* Which *four* actions result in a URL Filtering log entry? A) alert B) allow C) block D) continue E) override - CORRECT ANSWER *A)* alert *C)* block *D)* continue *E)* override T/F: URLs are always matched to a PAN-DB URL category before they match a custom URL category. - CORRECT ANSWER False. T/F: A URL Filtering license is not required to define and use custom URL categories. - CORRECT ANSWER True What is opposite the *traffic initiator*? - CORRECT ANSWER The *traffic responder*. How does Palo Alto describe the *client* vs the *server*? - CORRECT ANSWER The client *initiates* the traffic, whereas the server is the system *responding* to the traffic. The firewall implicitly allows *__________* traffic, and implicitly denies *__________* traffic. - CORRECT ANSWER *intrazone* *interzone* Which *word* should be used *minimally* when creating security policy rules, and why? - CORRECT ANSWER *Any* The less instances of *Any* the firewall has, the less unnecessary lookups the firewall has to do. What does *UUID* stand for, and what is it? - CORRECT ANSWER Universally unique identifiers (UUIDs) are codes applied to logs, which provide an audit trail. What does the *highlight unused rules* feature do? - CORRECT ANSWER The *highlight unused rules* feature will highlight any rules that haven't received hits since the last data plane restart. What does *global find* return, and what does it not return? - CORRECT ANSWER Global find returns results that are part of the firewall configuration, such as IP addresses. It does not return dynamic information, such as logs. How would you determine if a particular instance of logged traffic was decrypted? - CORRECT ANSWER To determine whether the traffic was decrypted, you would need to click the log magnifying glass, and then review the *Flags* table. If the firewall is conducting NAT, what *type* of NAT should an *outbound* rule use? - CORRECT ANSWER *Source NAT* i.e. source IP is changed. If the firewall is conducting NAT, what *type* of NAT should an *inbound* rule use? - CORRECT ANSWER *Destination NAT* i.e. destination IP is changed. How does *DIPP NAT Oversubscription* work? - CORRECT ANSWER *DIPP NAT Oversubscription* uses the *destination IP*, in addition to the source IP and source port, to identify subscriptions. Which *three* choices are valid Source NAT types? A) Dynamic IP B) Dynamic IP / Port C) Port Forwarding D) Static - CORRECT ANSWER *A)* Dynamic IP *B)* Dynamic IP / Port *D)* Static T/F: Logging is enabled by default for *intrazone-default* and *interzone-default* security policy rules. - CORRECT ANSWER False What are the *three* main ways that applications can bypass port based firewall rules? - CORRECT ANSWER 1) Traffic Encryption (SSH, SSL, etc.). 2) Using non-standard ports. 3) Sneaking across port 80. When using *App-ID*, how quickly are *UDP* based applications identified? - CORRECT ANSWER Usually the *first UDP packet* will contain application data. When using *App-ID*, how quickly are *TCP* based applications identified? - CORRECT ANSWER Usually the *fourth or fifth TCP packet* will contain application data (after the TCP handshake). What *four* technologies do Palo Alto firewalls use to identify applications? - CORRECT ANSWER 1) Application Signatures 2) Unknown Protocol Decoder 3) Known Protocol Decoder 4) Protocol Decryption Which key is used for encrypting messages in an SSL/TLS connection? - CORRECT ANSWER The *session* key. What is the *path* used to check the latest available updates for WildFire, App-ID, etc.? - CORRECT ANSWER Device > Dynamic Updates Which of the following is the *name* of the object that dynamically groups applications based on application *attributes* that you can define, such as: Category, Subcategory, Technology, Risk, and Characteristic? A) Application B) Application Filter C) Application Group D) Application Profile - CORRECT ANSWER *B)* Application Filter T/F: Application Groups can contain applications, application filters, or other application groups. - CORRECT ANSWER True. How *many* levels of multi-level decoding can Palo Alto firewalls do? - CORRECT ANSWER *Four* How would an administrator block files that exceed the firewall's decoding limit? - CORRECT ANSWER The administrator would need to create a file blocking policy that blocks *multi-level encoded files*. When creating a data filtering profile, what are the *three* data pattern types that can used to find string matches? - CORRECT ANSWER 1) Predefined Patterns 2) Regular Expressions 3) File Properties What is the Palo Alto *telemetry* feature? - CORRECT ANSWER *Telemetry* is an opt-in feature that allows Palo Alto to anonymously collect system and traffic information to improve threat detection for all customers. T/F: A Security Profile attached to Security policy rule is evaluated only if the Security policy rule matches traffic and the rule action is set to allow. - CORRECT ANSWER True Zone Protection profiles are applied to which of the following: A) Ingress Ports B) Security Policy Rules C) Egress Ports D) Address Groups - CORRECT ANSWER *A)* Ingress Ports T/F: The antivirus security profile defines actions to be taken if an infected file is detected as part of an application. - CORRECT ANSWER True How do Palo Alto firewalls protect against potentially *compromised* private keys? - CORRECT ANSWER Palo Alto firewalls use perfect forward secrecy (PFS) for firewall sessions, causing each session to require new private keys. How does the client verify a server's certificate, when establishing an SSL/TLS connection? - CORRECT ANSWER The client uses PKI to verify the server's certificate. What are the main *three* Palo Alto decryption types? - CORRECT ANSWER 1) SSL Forward Proxy (Outbound) 2) SSL Inbound Inspection 3) SSH Decryption What *two* aspects of a certificate must be checked when verifying a system? - CORRECT ANSWER 1) The issuing CA is trusted. 2) The certificate information is valid, i.e. signature hash, date, etc. T/F: SSH does not use certificates. - CORRECT ANSWER True What does *CSR* stand for, and what is it? - CORRECT ANSWER A certificate signing request (CSR) is request made by a device to a CA, in order to have it's certificate signed by the CA. What is the path for viewing certificates? - CORRECT ANSWER Device > Certificate Management > Certificates What CLI command would display the *decryption exclusion cache*? - CORRECT ANSWER *show system setting ssl-decrypt exclude cache* Which *three* statements are true regarding Public Key Infrastructure? A) Solves the problem of secure identification of public keys. B) Uses digital certificates to verify key owners. C) Relies on manual distribution of shared keys. D) Has root and intermediate certificate authorities. - CORRECT ANSWER *A)* Solves the problem of secure identification of public keys. *B)* Uses digital certificates to verify key owners. *D)* Has root and intermediate certificate authorities. T/F: When the firewall is configured to inspect SSL traffic going to an internal server for which the firewall has the private key, it functions as a forward proxy. - CORRECT ANSWER False. The question describes SSL decryption. A forward proxy would be an intermediary for outbound traffic. What are *two* methods for certificate revocation? A) CRL B) OCSP C) IKE D) SSH - CORRECT ANSWER *A)* CRL *B)* OCSP When the firewall detects that a sessions has been broken as a result of the decryption process, it will cache the session information and will not attempt to decrypt the next session to the same server. How many hours does this cache entry persist? A) 2 B) 6 C) 12 D) 24 - CORRECT ANSWER *C)* 12 What are some reasons for enabling GlobalProtect on the firewall? - CORRECT ANSWER 1) Map IP to UserID. 2) Require user authentication. 3) Protect a sensitive network. T/F: A Windows-based UserID agent should be installed on a domain controller. - CORRECT ANSWER False. It should be installed on endpoints, rather than servers. Which *two* statements are true regarding User-ID and firewall configuration? A) Communication between the firewall and the User-ID agent are sent over an encrypted SSL connection. B) The firewall needs to have information for every User-ID agent to which it will connect. C) NetBIOS is the only client probing method supported by User-ID agent. D) The User-ID agent must be installed on the domain controller. - CORRECT ANSWER *A)* Communication between the firewall and the User-ID agent are sent over an encrypted SSL connection. *B)* The firewall needs to have information for every User-ID agent to which it will connect. Which *three* items are valid choices when configuring the *source user* field in a security policy? A) All B) Known-User C) Any D) Unknown E) None - CORRECT ANSWER *B)* Known-User *C)* Any *D)* Unknown Which *three* file types can be submitted to WildFire without a WildFire license? A) dll B) exe C) pdf D) src E) xml - CORRECT ANSWER *A)* dll *B)* exe *D)* src What are the *three* components of GlobalProtect? - CORRECT ANSWER 1) Portal 2) Gateway 3) Client Software The GlobalProtect client will connect to either an internal gateway or an external gateway based on its location (inside or outside of the corporate network). This location determination is based on the result of which option? A) Reverse DNS Lookup B) User selection during agent startup. C) IP address of the client system. D) It depends on whether the user starts the client in online or offline mode. - CORRECT ANSWER *A)* Reverse DNS Lookup In which *two* formats is the GlobalProtect client available? A) .dmg B) .exe C) .msi D) .pkg - CORRECT ANSWER *C)* .msi *D)* .pkg T/F: If a GlobalProtect agent fails to establish an IPsec connection, the connection type fails back to SSL-VPN. - CORRECT ANSWER True Which *three* statements are true about a GlobalProtect gateway? A) It provides security enforcement for traffic from GlobalProtect clients. B) It requires a tunnel interface for external clients. C) Tunnel interfaces are optional for internal gateways. D) It authenticates against a Server Profile. - CORRECT ANSWER *A)* It provides security enforcement for traffic from GlobalProtect clients. *B)* It requires a tunnel interface for external clients. *C)* Tunnel interfaces are optional for internal gateways. Which *five* pieces of information are passed during IKE phase 1? - CORRECT ANSWER 1) Authentication Method 2) Diffie-Hellman Key Exchange 3) Symmetric Key Algorithm - Bulk Data Encryption 4) Hashing Algorithm 5) Lifetime What happens during phase 1 and phase 2 of IKE? - CORRECT ANSWER Phase 1: Authentication Phase 2: Data Encapsulation What does *IKE* stand for, and what is it? - CORRECT ANSWER Internet Key Exchange (IKE) is the protocol used to set up a security association (SA) in the IPsec protocol suite. T/F: When you create a VPN static route, a next-hop IP address is *not* required. - CORRECT ANSWER True Which *two* options are true, regarding a VPN tunnel interface? A) The tunnel interface always requires an IP address. B) The tunnel interface is a logical layer 3 interface. C) The tunnel interface must be added to a layer three security zone. D) The interface name "tunnel" can be renamed to anything you want, up to 20 characters in length. - CORRECT ANSWER *B)* The tunnel interface is a logical layer 3 interface. *C)* The tunnel interface must be added to a layer three security zone. What are the *three* ways to apply a global filter? - CORRECT ANSWER 1) Define a global filter. 2) Promote a local filter to a global filter. 3) Set a global filter from a table. T/F: A report group must be sent as a scheduled email. It cannot be downloaded directly. - CORRECT ANSWER True What is the name Palo Alto uses for SaaS applications that have been formally approved for use on your network? - CORRECT ANSWER Sanctioned. What is a *split-brain* scenario? - CORRECT ANSWER A *split-brain* scenario occurs when a non-redundant control link (for an HA pair) goes down. This results in the passive firewall concluding that the active firewall is down, and attempts to start services that are already running on the active firewall. T/F: HA backup links must be on a *different* subnet from the primary HA links. - CORRECT ANSWER True T/F: In an active-passive HA pair, the device with the *higher* device priority number is set as the *active* device. - CORRECT ANSWER False. The device with the lower device priority number is set as the ACTIVE device in the HA pair. What is the difference between the *heartbeat* and *hello messages* sent between two firewalls in an HA pair? - CORRECT ANSWER The heartbeat is an *ICMP* health check, while the hello message is a *TCP* health check. Which *three* types of traffic flow across the HA control link? A) Configuration Synchronization B) Session Synchronization C) Heartbeats D) Hellos - CORRECT ANSWER *A)* Configuration Synchronization *C)* Heartbeats *D)* Hellos On a firewall with dedicated HA ports, which option describes the function of the HA2 port? A) Control Link B) Data Link C) Management Link D) Heartbeat Link - CORRECT ANSWER *B)* Data Link T/F: A Backup Control link helps prevent split-brain operation in a firewall HA cluster. - CORRECT ANSWER True What are the *four* failure-detection methods in a firewall HA cluster? A) Heartbeats and Hellos B) Internal Health Checks C) Link Groups D) Path Groups E) Polling - CORRECT ANSWER *A)* Heartbeats and Hellos *B)* Internal Health Checks *C)* Link Groups *D)* Path Groups What aspect of a firewall rule determines whether it is *port-based* or not? - CORRECT ANSWER The *application* field. If the *application* field is set to ANY, then the rule is considered a port-based rule. What are some of the URL categories Palo Alto recommends to *block*? - CORRECT ANSWER 1) copyright-infringment 2) dynamic DNS 3) extremism 4) malware 5) parked 6) phishing 7) proxy-avoidance-and-anonymizers 8) questionable 9) unknown Which phase is *not* one of the *three* phases used in a migration from port-based firewall policies to application-based firewall policies? A) Application Visibility B) Baseline Visibility C) Consolidate, Customize, and Reduce Risk D) Next-Generation Policies - CORRECT ANSWER *B)* Baseline Visibility Which tab in the ACC provides an overview of traffic and user activity on your network? A) Tunnel Activity B) Blocked Activity C) Network Activity D) Threat Activity - CORRECT ANSWER *C)* Network Activity You should set all category actions to which level when you create a new URL filtering profile? A) Alert B) Block C) Continue D) Allow - CORRECT ANSWER *A)* Alert [Show More]
Last updated: 8 months ago
Preview 1 out of 64 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Oct 09, 2023
Number of pages
64
Written in
Additional information
This document has been written for:
Uploaded
Oct 09, 2023
Downloads
0
Views
96