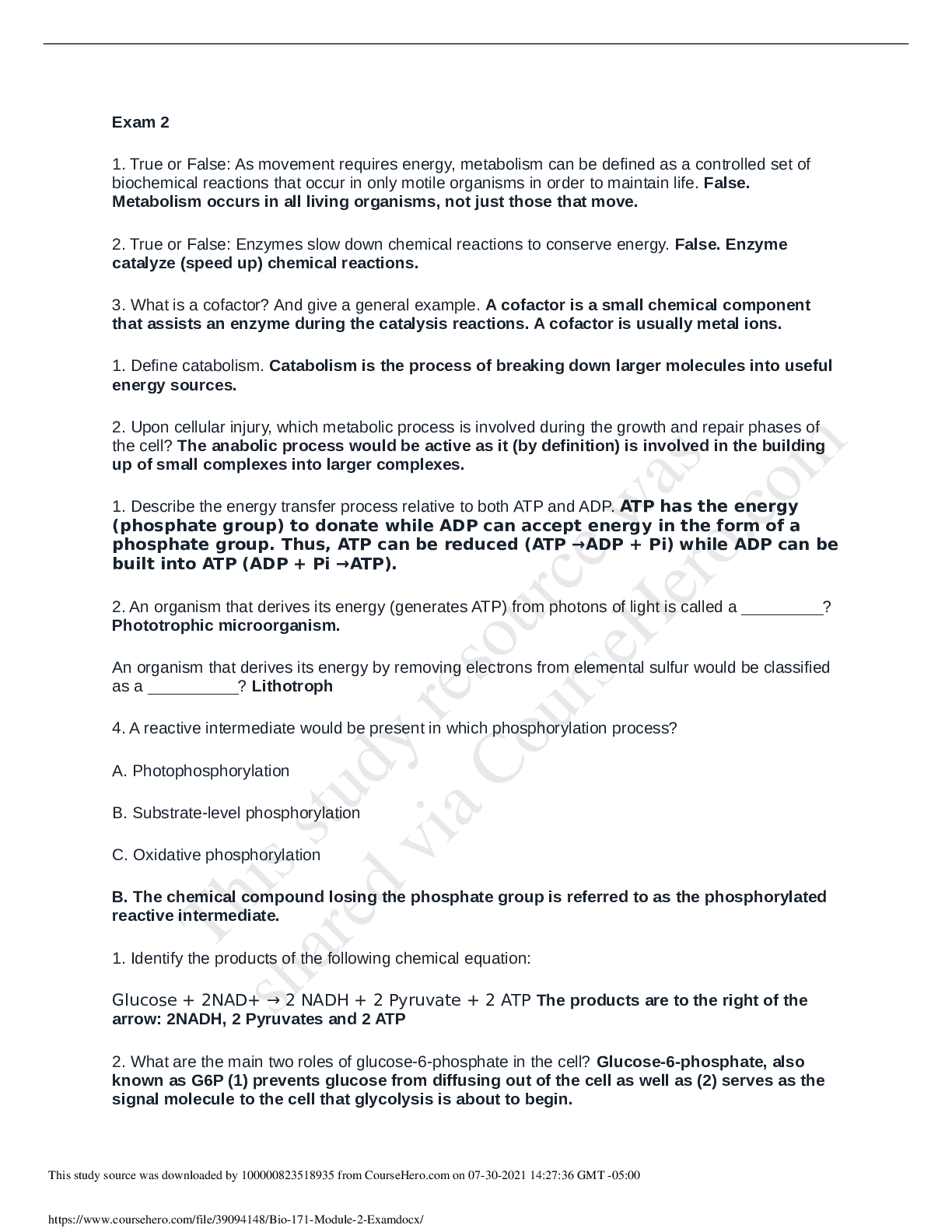
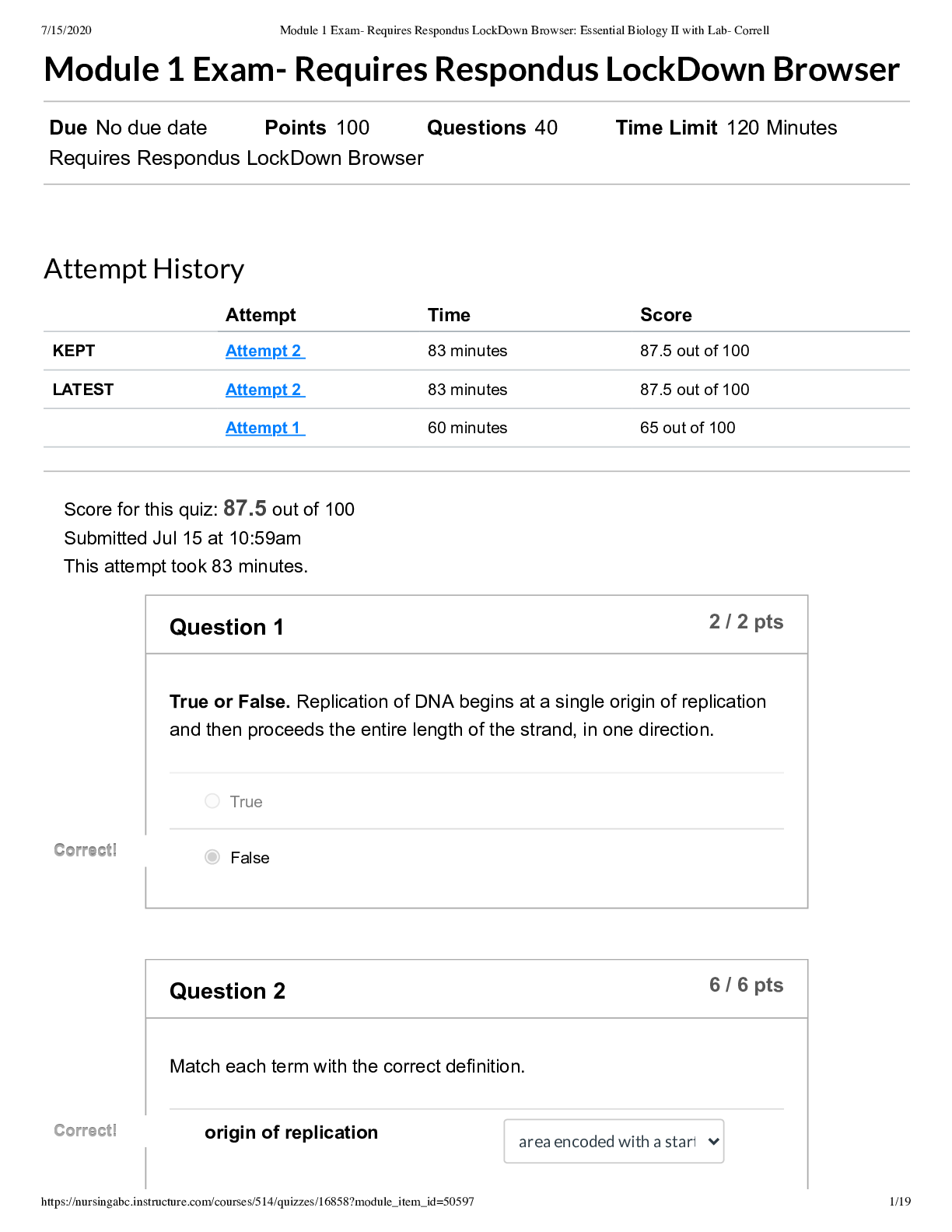
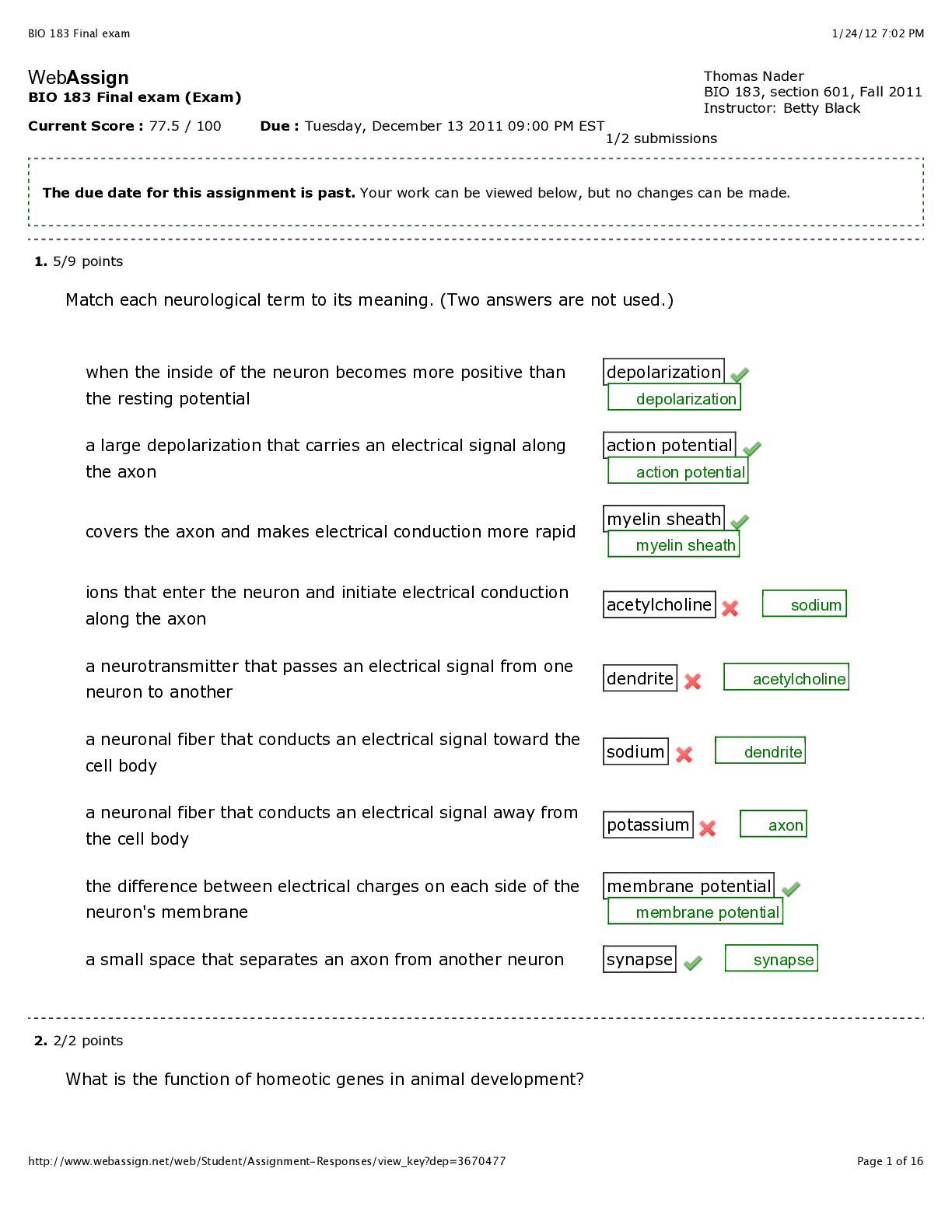
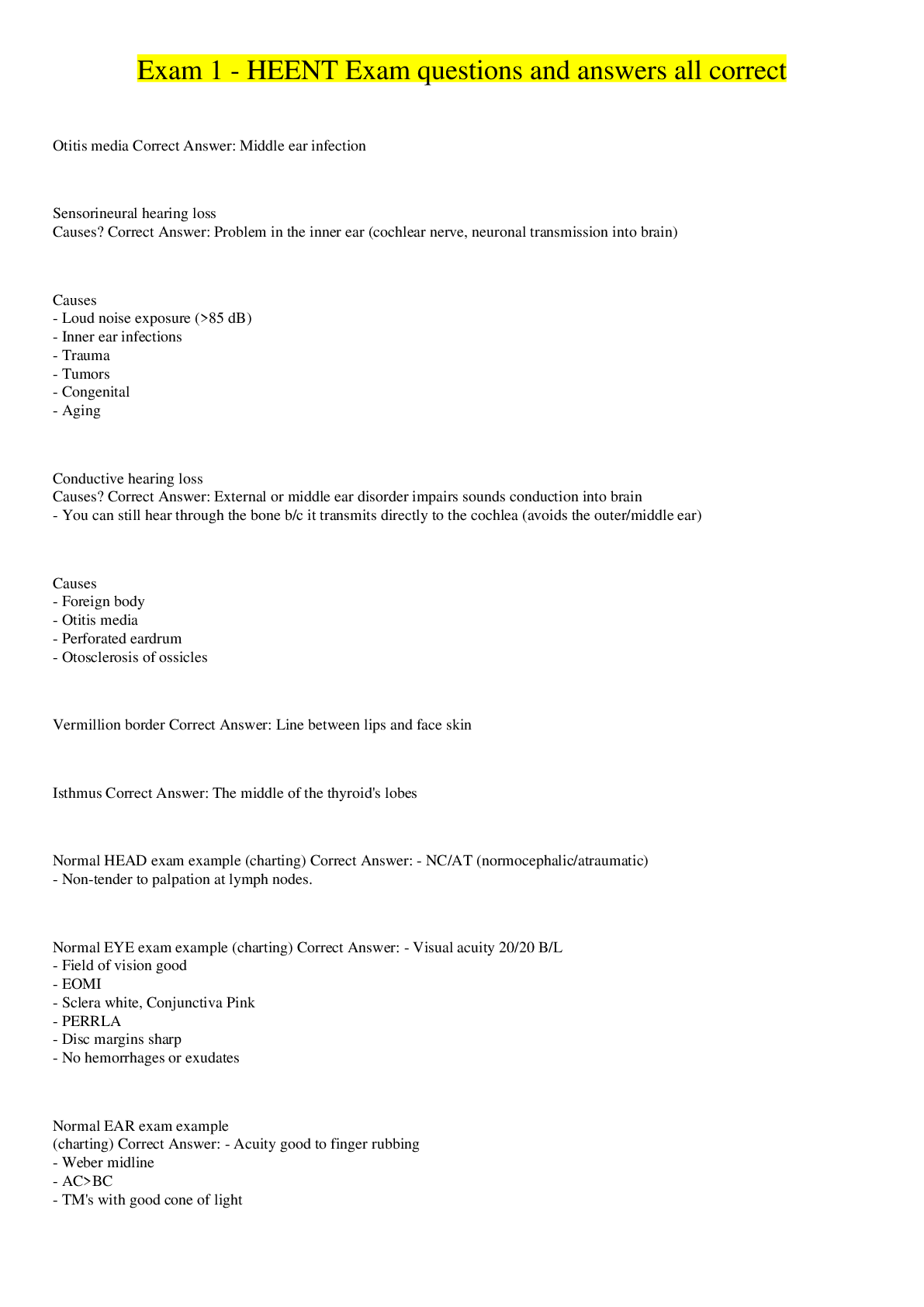
Computer Science > EXAM > WGU- C725 questions with complete solutions (All)
WGU- C725 questions with complete solutions
Document Content and Description Below
SOX (Sarbanes-Oxley Act) Correct Answer: Requires corporate executives to review and modernize their company's financial reporting systems. GLBA (Gramm-Leach-Bliley Act) Correct Answer: Known as ... the Financial Modernization Act of 1999. It is a United States federal law that requires financial institutions to explain how they share and protect their customers' private information. To be GLBA compliant, financial institutions must communicate to their customers how they share the customers' sensitive data, inform customers of their right to opt-out if they prefer that their personal data not be shared with third parties. What are the three methods of sanitization? Correct Answer: Overwriting Deguassing Destruction Mandatory Access Control (MAC) Correct Answer: Uses security labels for access control. Highly restrictive, usually used within government agencies. E.g. TS, SCI, etc. Discretionary Access Control (DAC) Correct Answer: A means of restricting access to objects based on the identity of subjects and/or groups to which they belong. What are the problems with passwords? Correct Answer: Passwords can be insecure, and easily broken. Dictionary words are not advised. Passwords are inconvenient, and repudiable. RADIUS Correct Answer: Remote Access Dial-In User Service; client/server protocol and software that enables remote access users to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service. Cryptosystem Correct Answer: is the hardware or software implementation that transforms plaintext into ciphertext (encrypting it) and back into plaintext (decrypting it). Cryptography Correct Answer: the art of protecting information by transforming it into an unreadable format, called cipher text Cryptanalysis Correct Answer: The science or art of breaking a cryosystem Cryptology Correct Answer: The umbrella study of cryptography and cryptanalysis Cryptographers rely on two basic methods of disguising messages Correct Answer: Transposition, in which letters are rearranged into a different order Substitution, in which letters are replaced by other letters and/or symbols. Symmetric Key Encryption Correct Answer: Encryption system in which a single key is used for both encryption and decryption. DES. 3DES. AES. [Show More]
Last updated: 1 year ago
Preview 1 out of 3 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 12, 2022
Number of pages
3
Written in
Additional information
This document has been written for:
Uploaded
Nov 12, 2022
Downloads
0
Views
37




.png)