Computer Science > EXAM > C725| 300 questions with complete solutions| WGU (All)
C725| 300 questions with complete solutions| WGU
Document Content and Description Below
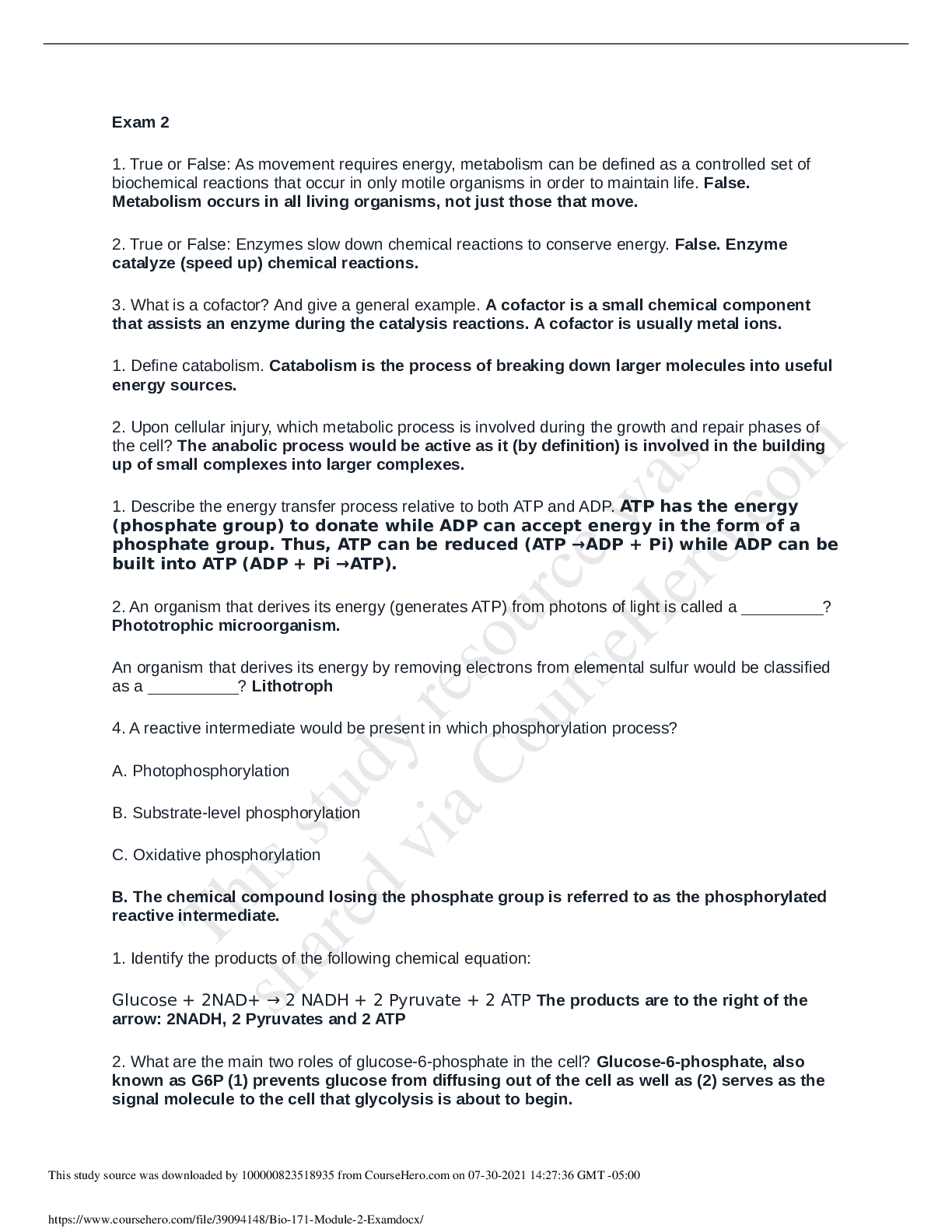
Information security is primarily a discipline to manage the behavior of Correct Answer: People Careers in information security are booming because of which of the following factors? Correct Answe... r: threat of cyber terrorism, gov regs, growth of the internet Which of the following best represents the three objectives of information security? Correct Answer: CIA A program for information security should include which of the following elements? Correct Answer: Security policies and procedures Which of the following topics are part of an information security practice? Correct Answer: Laws and ethical practices, access controls, security architecture Which college curriculum is more appropriate for a career in information security Correct Answer: business admin and comp info sciences The formal study of information security has accelerated primarily for what reason? Correct Answer: (increasingly interconnected global networks) Cybersecurity is like an umbrella. Under the umbrella are the following: Correct Answer: Compliance, policies, standards, admin, auditing, software dev security, permission controls, incident response, physical security, intrusion detection and prevention, ops controls, antivirus, security testing, training and awareness, key management, public key infrastructure, disaster recovery, access controls The growing demand for InfoSec specialists is occurring predominantly in which of the following types of organizations Correct Answer: Gov, corporations, not for profit foundations What is meant by the phrase "the umbrella of information security"? Correct Answer: IS incorporates many different pursuits and disciplines Which of the following roles helps development teams meet security requirements? Correct Answer: Security consultants Secuyrity consultants do this: Correct Answer: perform risk analysis of new systems by balancing the needs of business with the threats that stem from opening up access to data or managing new information that could compromise the business if it fell into the wrong hands. Who is responsible for ensuring that systems are auditable and protected from excessive privileges? Correct Answer: Security admins Security admins do this Correct Answer: help to establish new user accounts, ensure that auditing mechanisms are pr [Show More]
Last updated: 1 year ago
Preview 1 out of 31 pages

Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Nov 12, 2022
Number of pages
31
Written in
Additional information
This document has been written for:
Uploaded
Nov 12, 2022
Downloads
0
Views
66




.png)