Computer Science > EXAM > CSIS 330 Final Exam Liberty University answers complete solutions; (Version 3) Latest 2019/2020. (All)
CSIS 330 Final Exam Liberty University answers complete solutions; (Version 3) Latest 2019/2020.
Document Content and Description Below
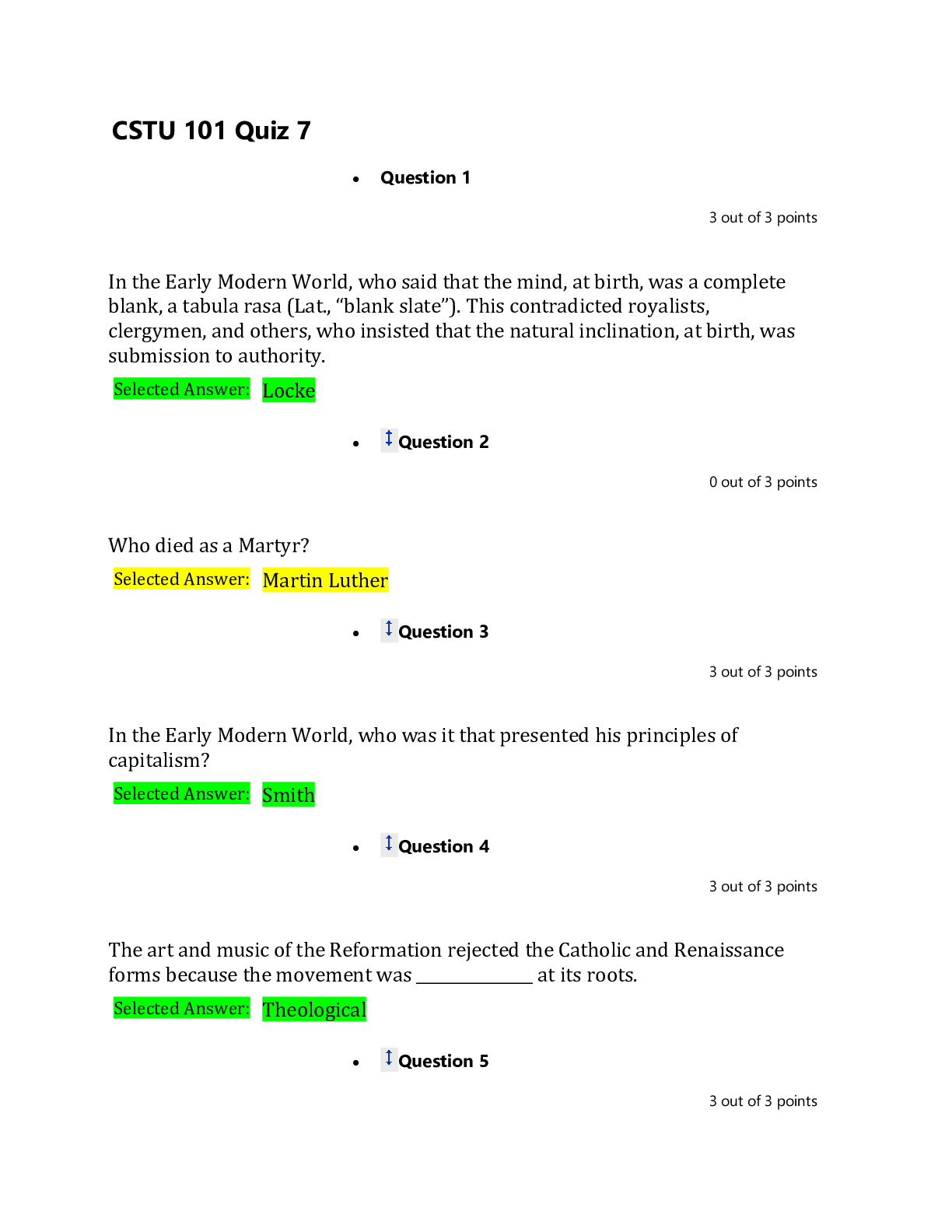
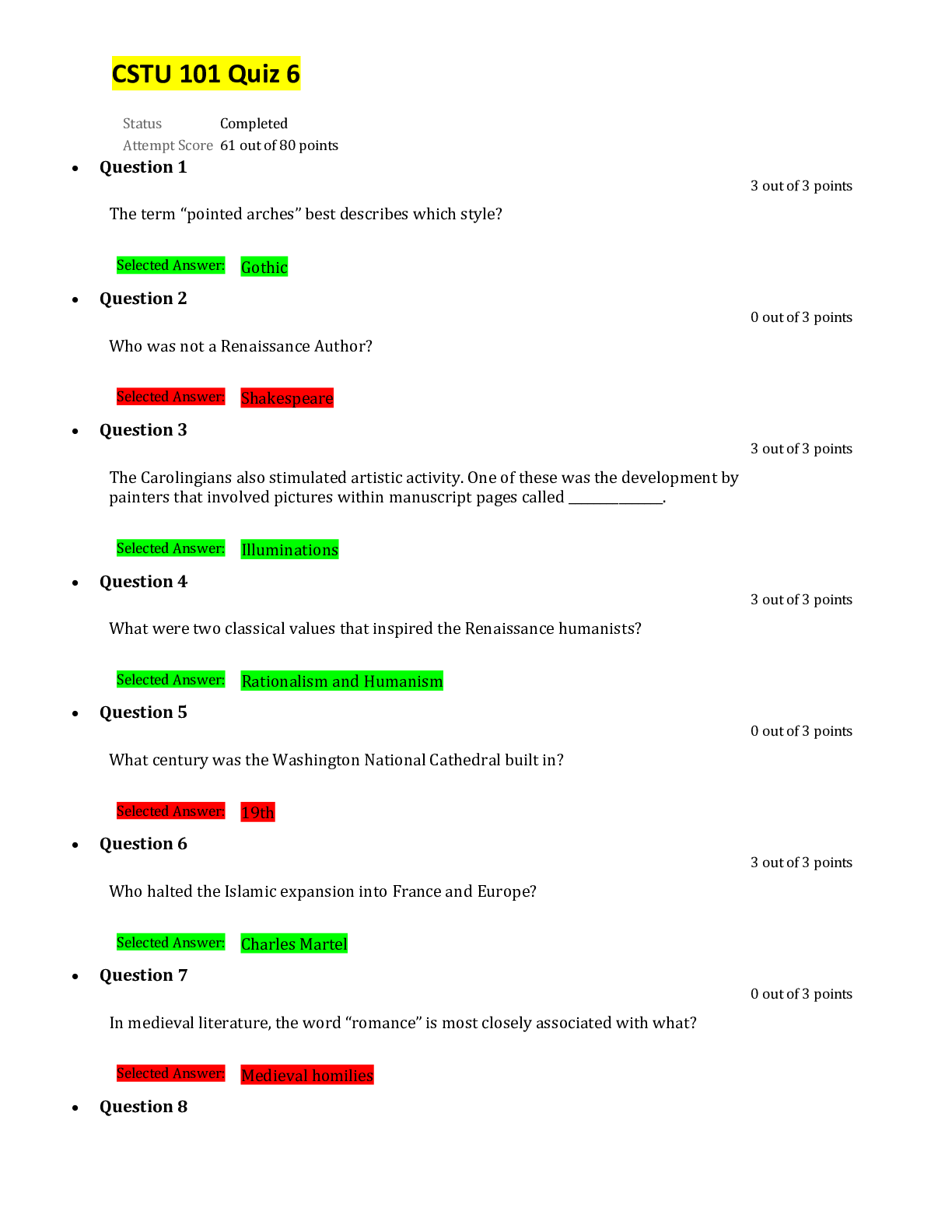
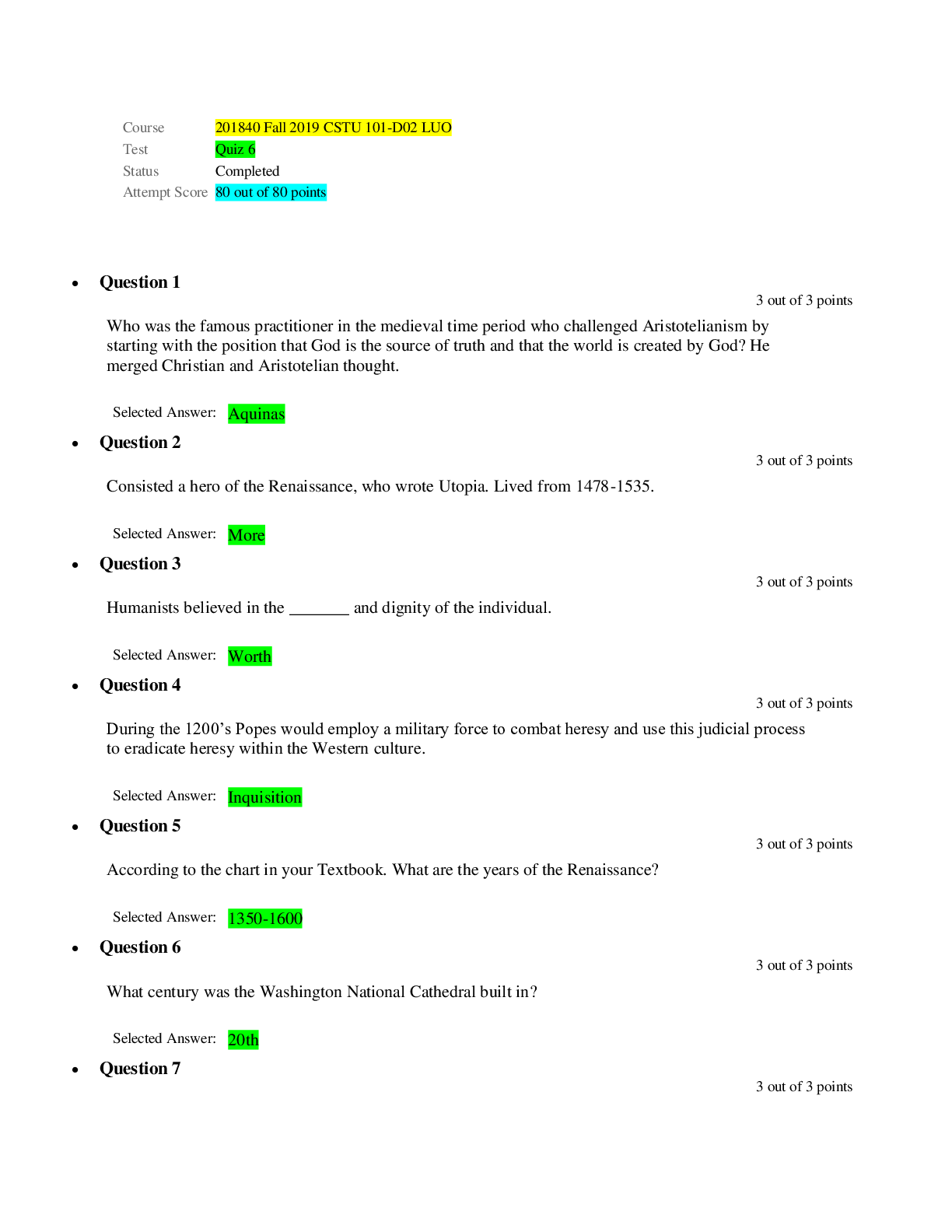
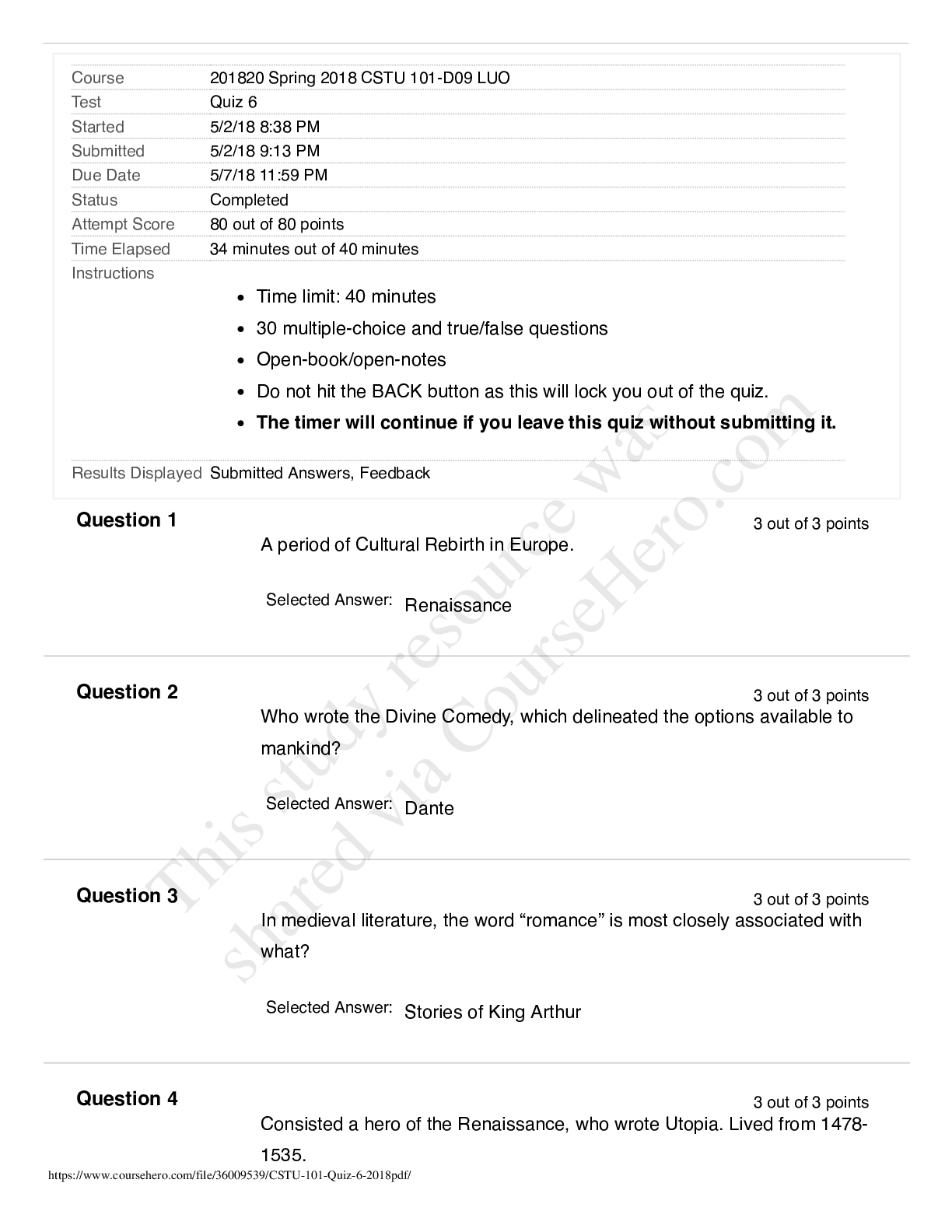
CSIS 330 Final Exam Liberty University answers complete solutions; (Version 3) Latest 2019/2020 CSIS 330 - Final Exam • Question 1 An organization can use a(n) ________________ to provide s... ecure and safe access to individuals who work for a different organization, but require company data. • Question 2 Which of the following is not a benefit of a connection-oriented system, like a circuit-switched telephone system? • Question 3 __________ are computer hosts that have software installed that enable them to request and display the information obtains from a server. • Question 4 Which of the following is not a specific feature of a WAN? • Question 5 _________________________ identify devices, ports, and IP addressing schemes. • Question 6 The Internet is a conglomerate of networks and is owned by the United States. • Question 7 __________________________ involves increased priority for production control or business transaction data. • Question 8 Traditional learning methods provide which two sources of expertise from which the student can obtain information? • Question 9 A(n) ____________ forwards data packets to and receives data packets from the Internet • Question 10 Which mode is used to configure one of the physical or virtual lines? • Question 11 ____________________ is a method for remotely establishing a CLI session of a device, through a virtual interface, over a network. • Question 12 What command is used on a Windows PC at the command prompt to display the computer’s IP configuration setttings? • Question 13 According to the textbook, when a banner is used on an IOS device, it should always welcome someone to the device as its first statement. • Question 14 What CLI shortcut completes the remainder of a partially typed command or keyword? • Question 15 The Delete key (the key normally used to erase characters to the right of the cursor) is not recognized by terminal emulation programs. • Question 16 What type of connection to a Cisco IOS switch is used to make the initial configuration? • Question 17 Which protocol receives message segments from the transport layer, packages them into packets, and addresses them for end-to-end delivery over an internetwork? • Question 18 The TCP/IP protocol suite does not specify which protocols to use when transmitting over a physical medium. • Question 19 The ___________ model is the most widely known internetwork reference model. • Question 20 _______________________ is the term used to refer to the PDU at the Transport layer of the TCP/IP model. • Question 21 A group of inter-related protocols necessary to perform a communication function is called a(n) ____________. • Question 22 ___________ is the process used by a receiving device to remove one or more of the protocol headers. • Question 23 Is the binary number 10101011 odd or even? • Question 24 What is the binary equivalent of the decimal number 119? • Question 25 What is the binary equivalent of the hexadecimal number AA? • Question 26 What is the decimal equivalent of the binary number 01000000? • Question 27 What is the binary equivalent of the decimal number 65? • Question 28 What is the decimal equivalent of the hexadecimal number A0? • Question 29 Bits are encoded on fiber as ___________________________. • Question 30 What type of connector is used to terminate UTP cables? • Question 31 The _________________ layer controls how data is transmitted onto the physical media by encoding the binary digits that represent data into signals. • Question 32 _________________________ is a transmission technique in which the amplitude of the carrier varies in accordance with the signal. • Question 33 ______________ stipulates the commercial cabling standards for LAN installations and is the standard most commonly used in LAN cabling environments. • Question 34 ____________________________ is popular in long-distance situations spanning hundreds of kilometers such as required in long-haul telephony and cable TV applications. • Question 35 A(n) _______________ transmission of data exists when data signals are sent along with a clock signal that occurs at evenly spaced time durations. • Question 36 What type of connector is usually used to terminate a UTP cable? • Question 37 _________ is a logical interface on a switch associated with a virtual local-area network (VLAN). • Question 38 A _______________________ MAC address is the unique address used when a frame is sent from a single transmitting device to a single destination device. • Question 39 Which of the following is not a function of data encapsulation in Ethernet? • Question 40 In ________________ switching, the switch acts upon the data as soon as it is received, even if the transmission is not complete. • Question 41 In ________________ switching, the switch stores the first 64 bytes of the frame before forwarding. • Question 42 In ________________ switching, when the switch receives the frame, it stores the data in buffers until the complete frame has been received. • Question 43 The maximum size of a PDU that a medium can transport is known as the _______________________. • Question 44 Which of the following is not displayed by the IOS show version command on a router? • Question 45 Which of the following statements is false with respect to IP? • Question 46 Which of the following is not a column in an IPv6 Route Table? • Question 47 Which field in a router’s routing table identifies the IP address of the next router to forward a packet? • Question 48 The local routing table of a host typically contains a route to the loopback interface (127.0.0.1). This address is known as a ______________________. • Question 49 Which of the following is not an advantage of the IPv6 simplified header over the IPv4 header? • Question 50 In what part of a router is the current configuration being used located? • Question 51 TCP breaks up a message into small pieces known as ______. • Question 52 Which of the following is not a characteristic of TCP? • Question 53 Which port is assigned to HTTP? • Question 54 Which of the following is not a common transport layer protocol? • Question 55 What range of ports can either be used by TCP to identify the requested service on the destination device or as a client source port? • Question 56 If a client sends an ISN of 2 to a server, and a server responds with an ISN of 1 to the client, what is the final stage of the TCP three-way handshake? • Question 57 Which of the following is not a protocol that uses TCP to ensure data delivery? • Question 58 Regulating the amount of data a source transmits is a function of _____________. • Question 59 A _______________ is 32-bits long, and it signifies which part of an IP address is network and which part is host. • Question 60 Both IPv4 and IPv6 use an ICMP protocol as the principal means to verify connectivity. • Question 61 The default subnet mask for a Class B address is _____________. • Question 62 What is the process in generating an IPv6 interface ID that uses a client’s 48-bit Ethernet MAC address and inserts another 16 bits in the middle of the 48-bit MAC address to create a 64-bit interface ID? • Question 63 ____________________ is a representation of information using only 1s and 0s. • Question 64 On a host device, which Windows command can be used to view the IP address information assigned by a DHCP server? • Question 65 Which of the following IPv4 addresses would be used in a private network? • Question 66 A(n) ________________ IPv6 address is an all-0s address represented as ::/128, or just :: in the compressed format. • Question 67 With VLSM, the subnet mask will vary depending on how many bits have been borrowed for a particular subnet. • Question 68 You have been assigned an IP address for your network of 192.168.1.0 / 24. Each subnet needs to accommodate 12 hosts. What is the subnet mask? • Question 69 What is the network address for the host assigned to 172.16.4.35/24 ? • Question 70 What is the first step in planning network subnets? • Question 71 How many hosts per network can you have with a subnet mask of 255.255.192.0? • Question 72 IPv4 subnets are created by using one or more of the ____________ bits as ____________ bits. • Question 73 Why were variable-length subnet masks created? • Question 74 You are given an IPv4 network address of 192.168.10.0/24 by your ISP. You need to subnet this network. You know that the subnet mask will be 255.255.255.252. Therefore, how many bits have you borrowed from the host portion of the network address to achieve this subnet mask? • Question 75 Which of the following is false with respect to Server Message Block (SMB)? • Question 76 In a __________________ network, two or more computers are connected through a network and can share resources without having a dedicated server. • Question 77 The type of addressing used when the network administrator manually enters IP address information on network hosts is called _________ addressing. • Question 78 Which protocol is used to assign an IP address, subnet mask, default gateway and DNS address to a host? • Question 79 Which protocol is a reliable, connection-oriented protocol used for interactive file transfer between systems? • Question 80 Which port(s) is(are) assigned to Telnet? • Question 81 Which of the following are functions of the Presentation Layer in the OSI model? • Question 82 Which DHCP message identifies the explicit server and lease offer that a client is accepting? • Question 83 Intruders who gain access by modifying software or exploiting software vulnerabilities are often called _______. • Question 84 A key network switch has failed because of excessive humidity. What type of physical threat caused the problem? • Question 85 A firewall is one of the most effective security tools available for protecting internal network users from external threats. • Question 86 What is true of an application layer service? • Question 87 According to the textbook, real-time applications require more planning and dedicated services (relative to other types of data) to ensure priority delivery of voice and video traffic. • Question 88 What type of network vulnerability is involved with the mere use of HTTP, FTP, and ICMP? • Question 89 ___________________ attacks are the disabling or corruption of networks, systems, or services. • Question 90 Which network protocol should a network administrator use to remotely configure a network device? • Question 91 What is a network vulnerability? • Question 92 ____________________ helps to eliminate single points of failure in a network. • Question 93 What type of network vulnerability is involved when JavaScript is turned on in web browsers? • Question 94 Which of the following is not a type of access attack? • Question 95 A(n) __________ firewall is a firewall that is built into a dedicated hardware device known as a security appliance. • Question 96 Which of the following is an example of a strong password? • Question 97 An attacker runs a ping sweep against a network. What type of attack is this? • Question 98 Which feature of network security records what the user does, including what is accessed, the amount of time the resource is accessed, and any changes that were made? • Question 99 Which of the following firewall techniques prevents or allows access based on IP or MAC addresses? • Question 100 VoIP uses voice-enabled routers that convert analog voice from traditional telephone signals into IP packets. [Show More]
Last updated: 1 year ago
Preview 1 out of 13 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
We Accept:

Reviews( 0 )
$12.00
Document information
Connected school, study & course
About the document
Uploaded On
Feb 08, 2020
Number of pages
13
Written in
Additional information
This document has been written for:
Uploaded
Feb 08, 2020
Downloads
0
Views
77