Information Technology > SOPHIA Milestone > Sophia Intro to IT Milestone Final. Sophia University - IT 100 | Already passed. (All)
Sophia Intro to IT Milestone Final. Sophia University - IT 100 | Already passed.
Document Content and Description Below
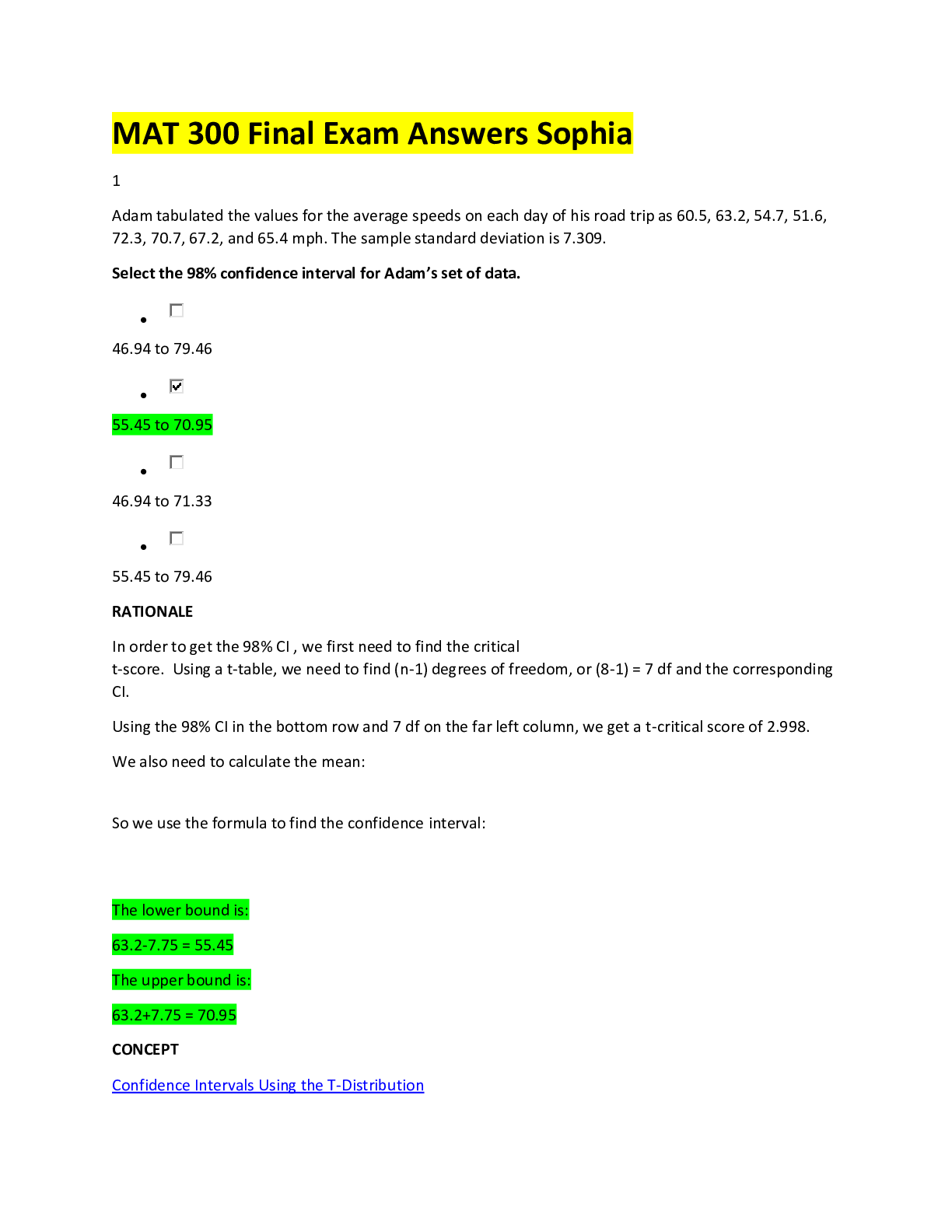
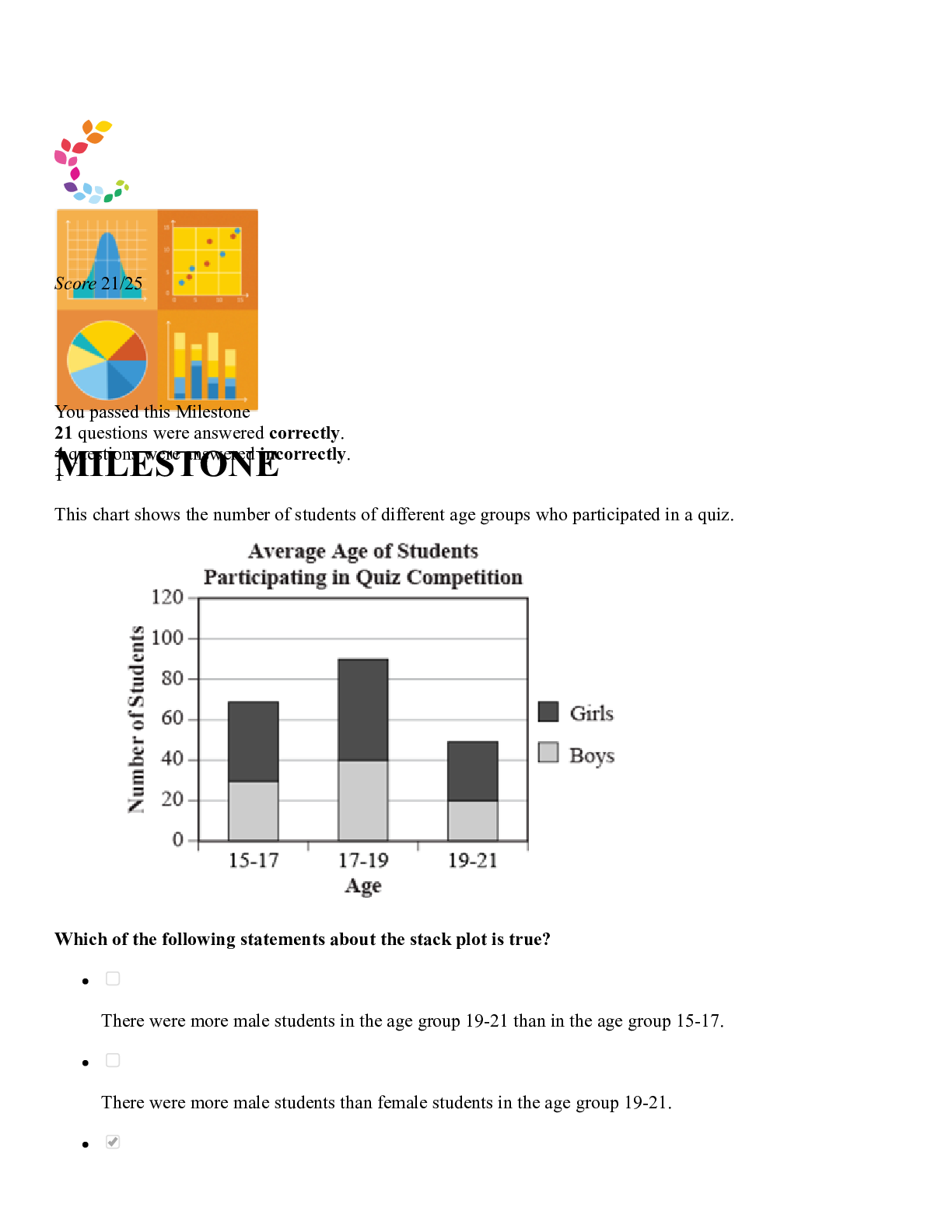
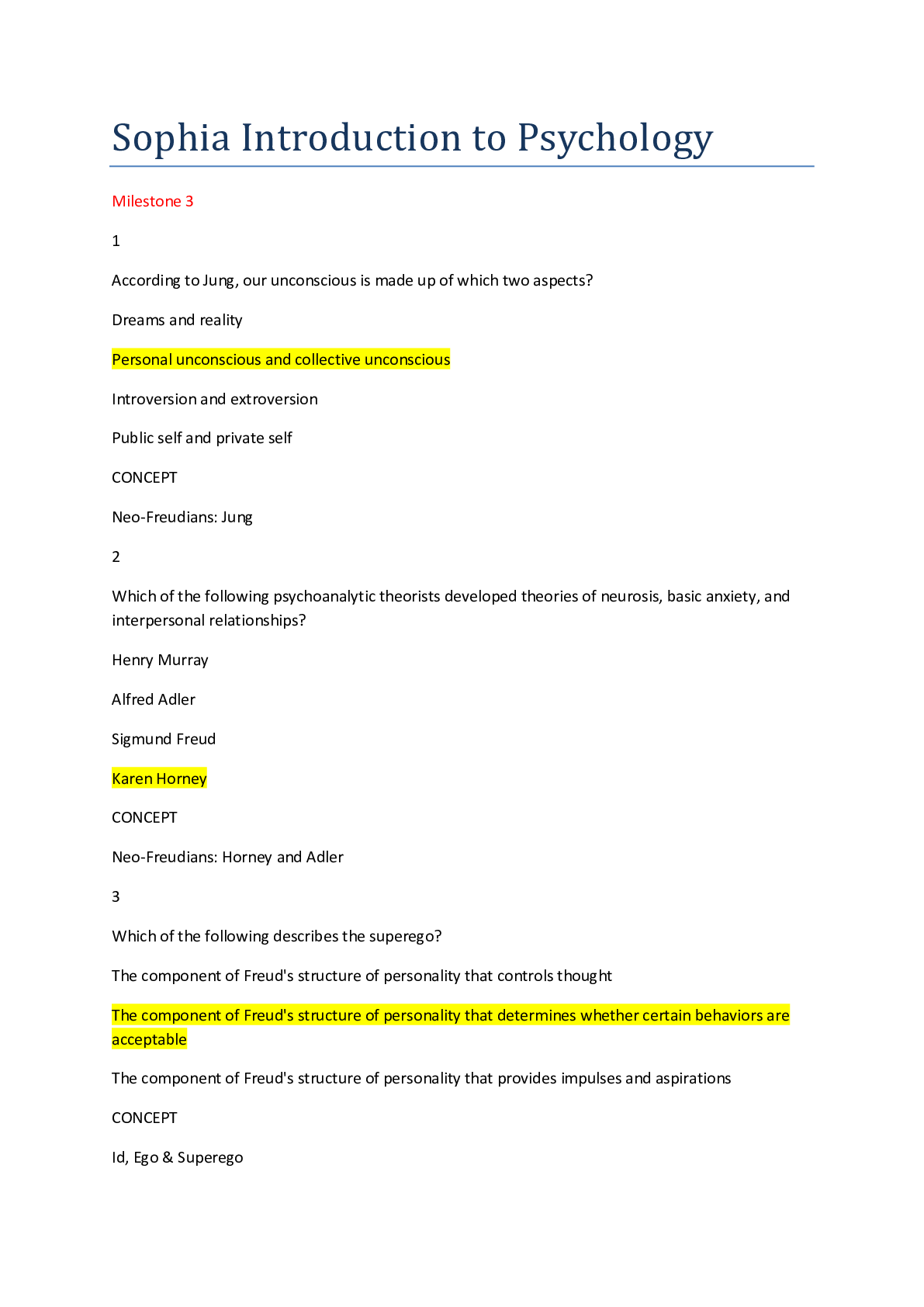
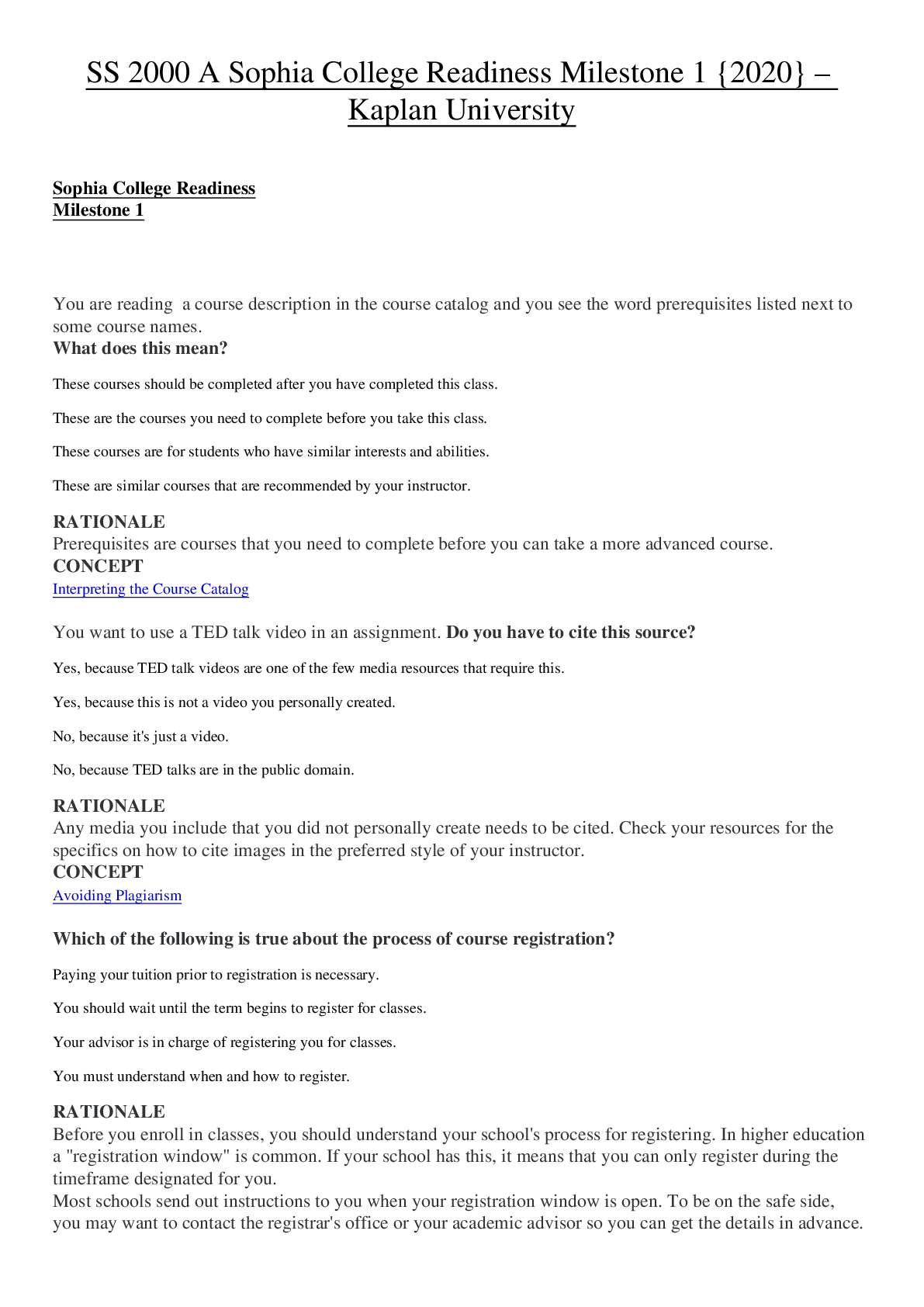
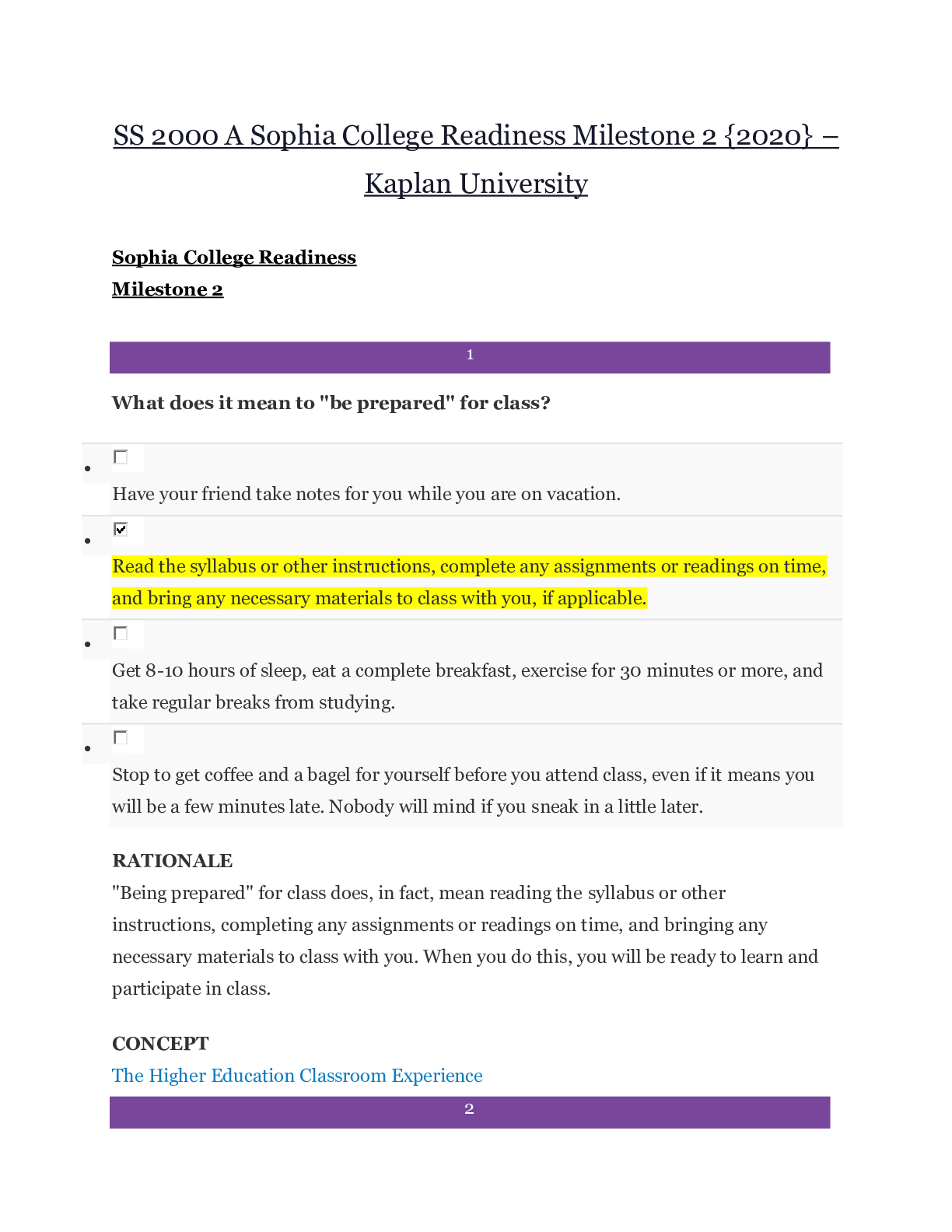
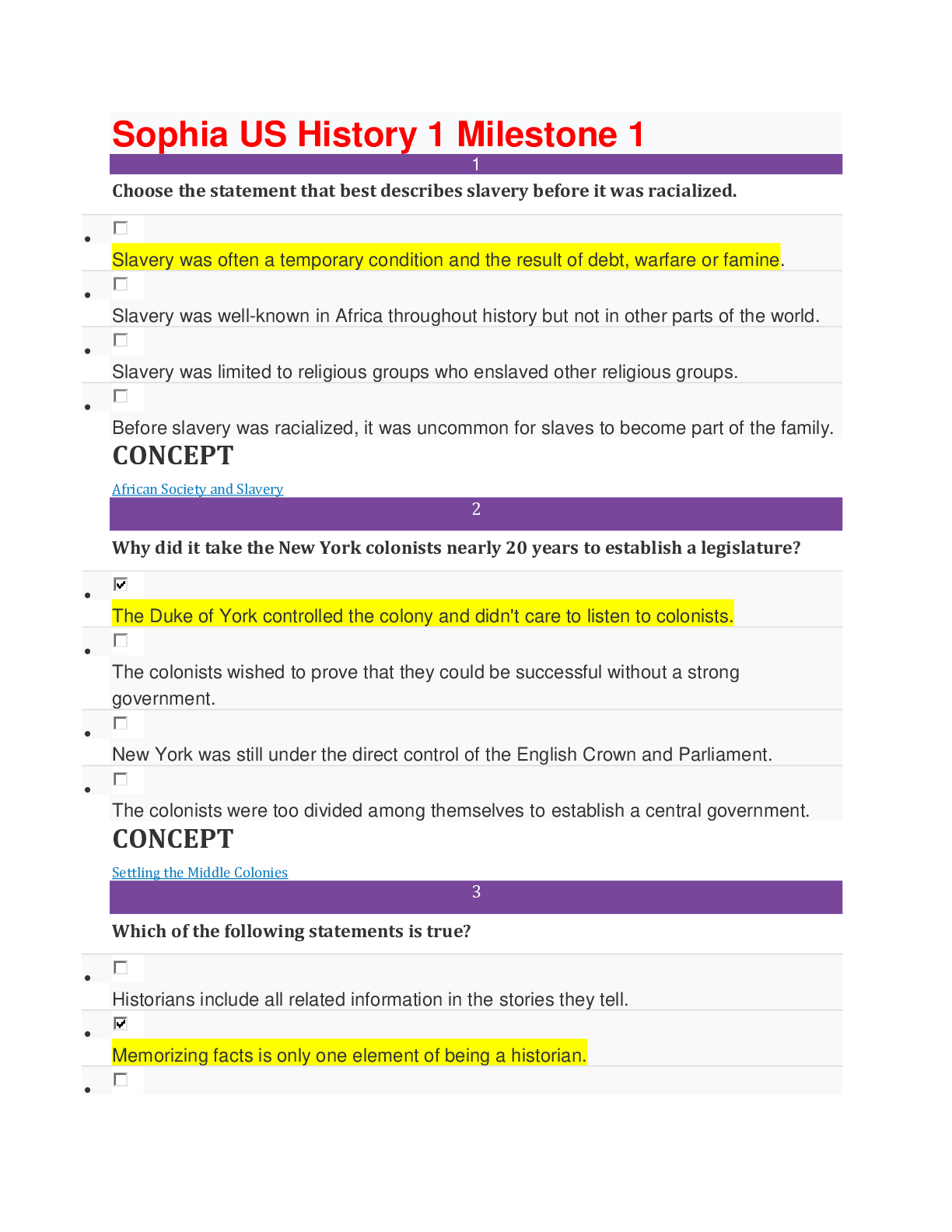
Sophia Intro to IT Milestone Final Score 24/25 1 Game Changer Technologies has four software teams. Each of them is developing four different examples of its new game app. Which software develop... ment methodology is used by the Game Changer teams? Lean Prototyping Cascading/V-model RAD 2 Mark, Sean, and Jackie are members of a software development team. Mark creates the documentation that outlines requirements for the development of new software. Sean creates the system architecture, and builds software applications based on system requirements. Jackie evaluates the new software by running tests to identify bugs and other problems. What is Mark's role on the software development team? Project Manager Software Quality Assurance Software Designer Software Analyst 3 Select the sign of computer addiction that indicates a lack of control. While driving his car, Mitch rear-ended another car when he was checking his social media account. Ever since his mother died, Charlie stays up late every night playing an online game. Even though she knows that she should, Jacqueline cannot stop playing her favorite online game. After moving to a new town, Sal spends most of his time online to keep his mind off the friends he misses. 4 Harriet implements policies and prevents unauthorized access to the network, and to the data stored on the network. Harriet holds the position of __________ in the organization. Database Administrator Network Administrator Computer Operator Security Administrator 5 Brad launches a program in order to see all of his files, folders, and programs in one place. Which element of the Microsoft Windows operating system is Brad using? File Explorer (formerly Windows Explorer) Windows Shell Security and Maintenance Taskbar 6 Information systems consist of five components: hardware, software, data, process, and __________. data management people monitors peripherals 7 Which of the following statements about the relationship between hardware and software is FALSE? Both hardware and software are needed for the computer to function effectively. Computer hardware cannot be used without an operating system. Computer hardware controls the computer's software by telling it what to do. Computer hardware can be physically touched, while computer software is intangible. 8 Select the scenario that demonstrates plagiarism. Allison makes a video of herself using sound effects that she clipped from the soundtrack of a popular action movie to market her business. Summer finds a recent magazine article about an issue that she wants to discuss with her class, so she makes copies of it for the students. Joseph finds a written passage about a new idea to stop cyberbullying and pastes it into his blog entry without giving credit to its author. Dylan contributes some of his own research to an entry on Wikipedia, and includes a citation for his recent book. 9 Which of the following is a best practice for maintaining a safe and healthy workstation? Reaching to the left to access the keyboard Adjusting the chair so that the user can stretch his or her legs straight out Placing the monitor screen seven inches from the face Adjusting the back of the chair so that a person's lower back is supported and perpendicular to the floor 10 Which task is suitable for an automated process? Astor plans to test her software only twice. Kanta’s company requires human review to identify and correct errors. Tanya plans to modify her software, and will retest it many times. Mai's company has a limited testing budget. 11 Malouka participates in a research project for a large consumer behavior research firm. Each time she purchases items in a grocery store, she scans the barcodes of her products into an app, which sends her purchase data to the firm for analysis. Malouka is working with an example of automation known as __________. importing/exporting data billing advertising and marketing textfill/autocorrect 12 Victor and Ellen are software engineers working on a popular mobile app. Victor has been in his position for 10 years longer than Ellen, who is a recent graduate. During the development of a new feature, Ellen expressed her concern that VIctor's proposed code would create instability in the app. Victor told Ellen he would address her concern with their supervisor. When Victor met privately with his supervisor, he claimed that he had discovered the problem, and that Ellen had dismissed it. Which principle of the Software Engineering Code of Ethics has Victor violated? Principle 6: Profession Principle 7: Colleagues Principle 8: Self Principle 3: Product 13 Identify the statement about Windows tasks that is FALSE. The boot process is the process for powering off a computer. A common way to shut down the computer’s operating system is by using the Start menu. To launch an application, click the Windows icon, select "All Programs," and then click an application. Users log into their accounts on the Welcome screen, before Windows is ready to use. 14 Which of the following correctly describes a record? A record contains all the qualitative data in a database. A record represents a single type of information found in a database. A record is an organized collection of data associated with other data in a database. A record contains all the data about one instance of an item in a database. 15 Select the scenario that describes a bottom-up approach to data warehouse design. Charley’s Wholesalers combines data from its produce, meat, and dry goods vendors into a single data warehouse, and distributes it among several data marts. Dave’s Appliances, which has five locations in the city, combines data from each store to a single database, and distributes it to three new data marts. Hollywood Advertising combines data marts from its San Diego, Los Angeles, and San Francisco offices into a single data warehouse. Jaime’s Research Consulting Firm combines data from its clients into a central database, then shares the data with several individual contractors. 16 Which of the following components is used for data processing? Scanner USB flash drive Network interface card (NIC) Solid-state drive (SSD) 17 All of the following would appear as records in a database table, EXCEPT: Last Name Armstrong Information Technology Specialist Little Rock, AR 18 Suzi is a writer who is using her keyboard to type a story. When she saves her work, her computer issues a command and returns the results, which she checks to ensure that her work has been saved properly. The __________ in Suzi's computer is responsible for the operation sent to it by the software. keyboard CPU ROM RAM 19 Select the true statement about network protocols. Communication cannot take place unless the protocol is executed in the same way on all devices. One function of a protocol is to decompress data when it is delivered to the receiving computer. Using a protocol other than TCP/IP can result in data loss. Computers that are distributed across a large geographic area need a special protocol to resolve errors. 20 Marco travels often and does not have consistent wireless Internet service. He frequently uses his mobile phone service to provide Internet access to his tablet. Which network type is Marco using? PAN MAN WAN LAN Computer Network Types 21 Select the true statement about a scanner. It is a device that enables users to input photographs as digital images. It is an input device that enables users to convert hard copies to digital images or text. It is a device that outputs digital images and text onto a screen. It is a device that enables users to output digital images or text as hard copies. 22 In which of the following scenarios can a trademark be applied? Alanna draws a shape to use as a background image on a company's website. Finn describes the results of his research in a journal article. Glenda writes a computer program for a business. Scott designs a new open-source application that can be used by any web designer. 23 Which technology enhances or augments the real world by using information that is designed to heighten sensory (i.e., auditory and visual) perception? Autonomous technology Artificial intelligence Virtual reality Visualization Advancements in Computer Science 24 Carrie's computer does not recognize her zip drive when she plugs it into a USB port. Carrie's computer is experiencing a(n) __________. external error system performance problem file compatibility issue application crash 25 Which external hardware component is circled in the given image? Eject button Monitor Vent Port [Show More]
Last updated: 1 month ago
Preview 1 out of 12 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 14, 2020
Number of pages
12
Written in
Additional information
This document has been written for:
Uploaded
Aug 14, 2020
Downloads
1
Views
357









_removed.png)

