Information Technology > QUESTIONS & ANSWERS > Delaware Technical Community College - SEC 355/SEC355 quiz 2 (2022) (All)
Delaware Technical Community College - SEC 355/SEC355 quiz 2 (2022)
Document Content and Description Below
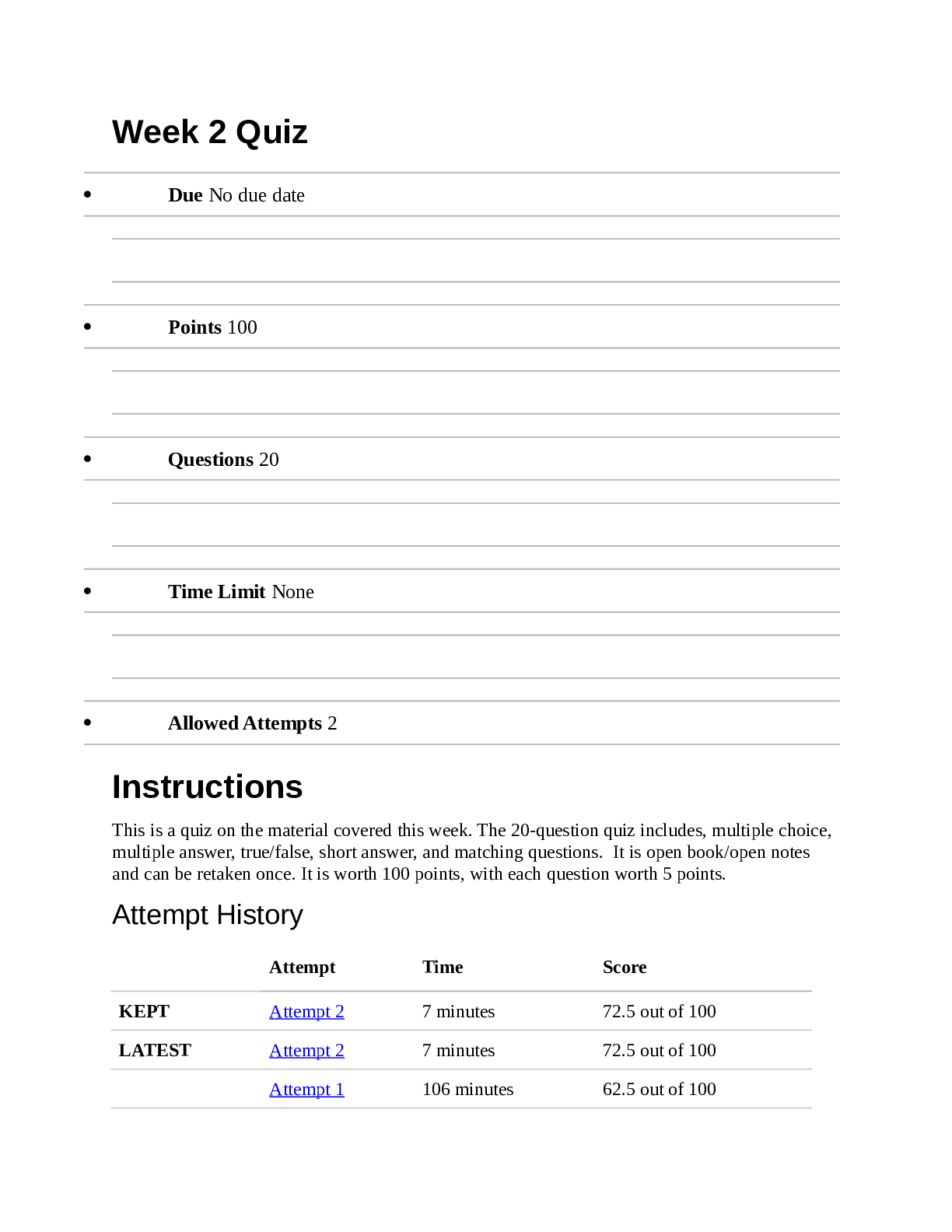
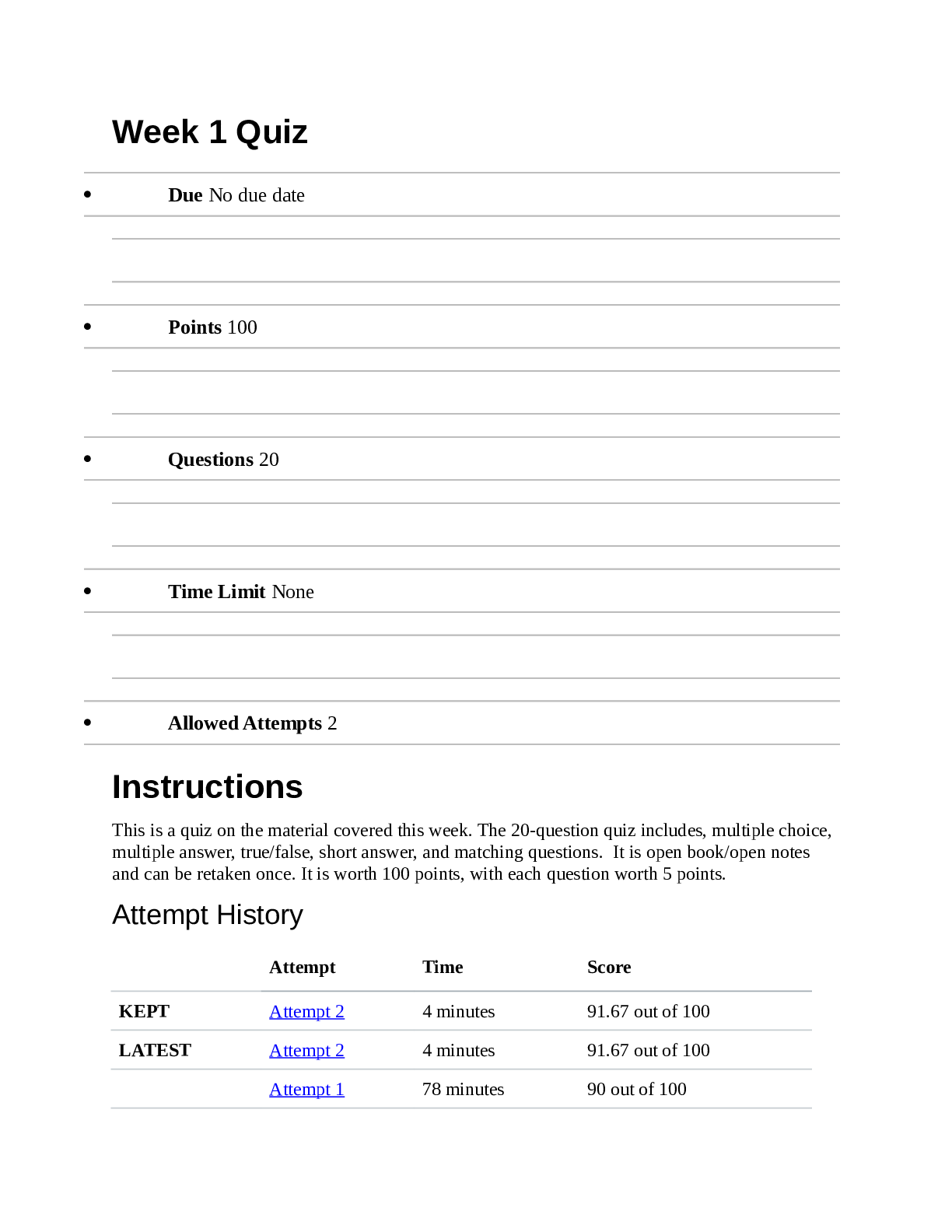
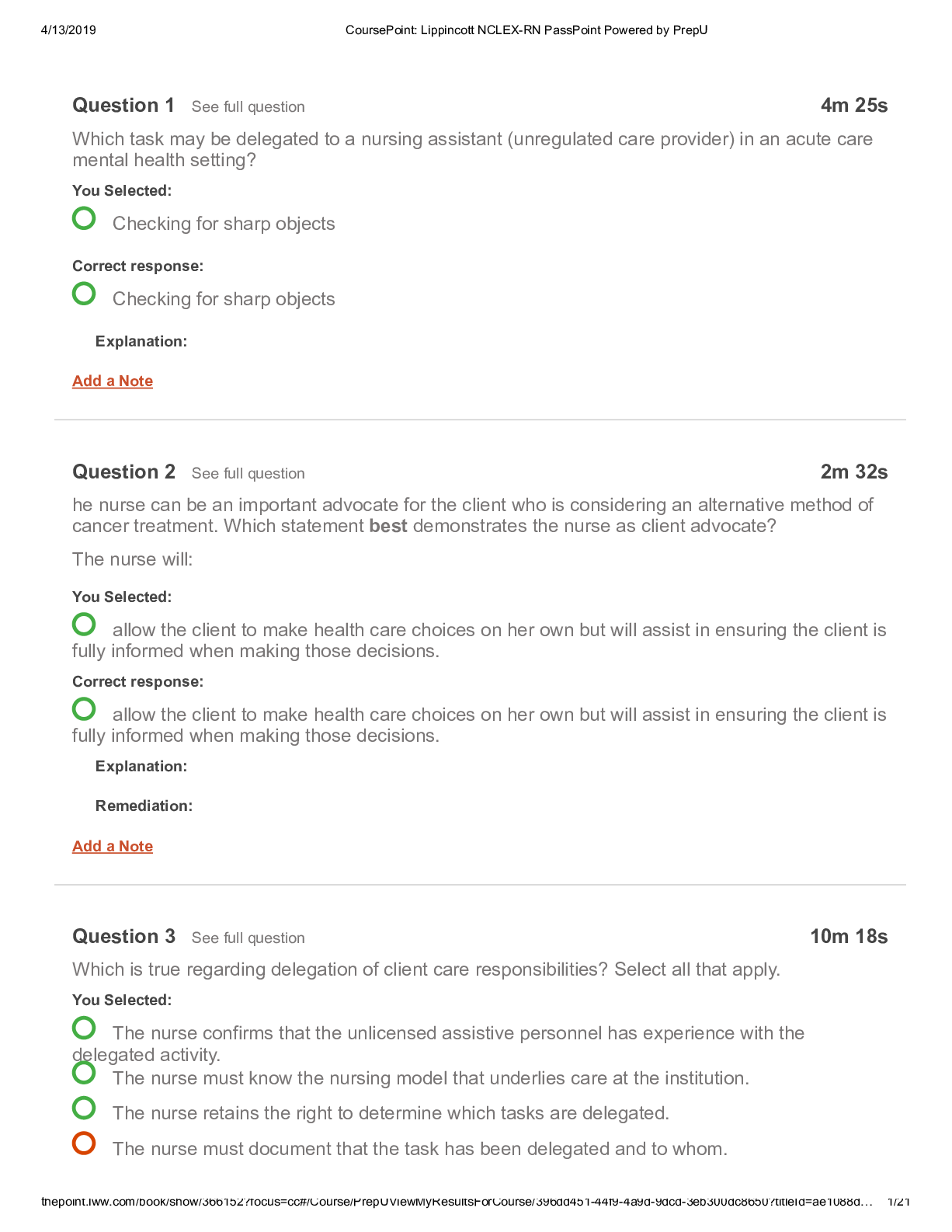
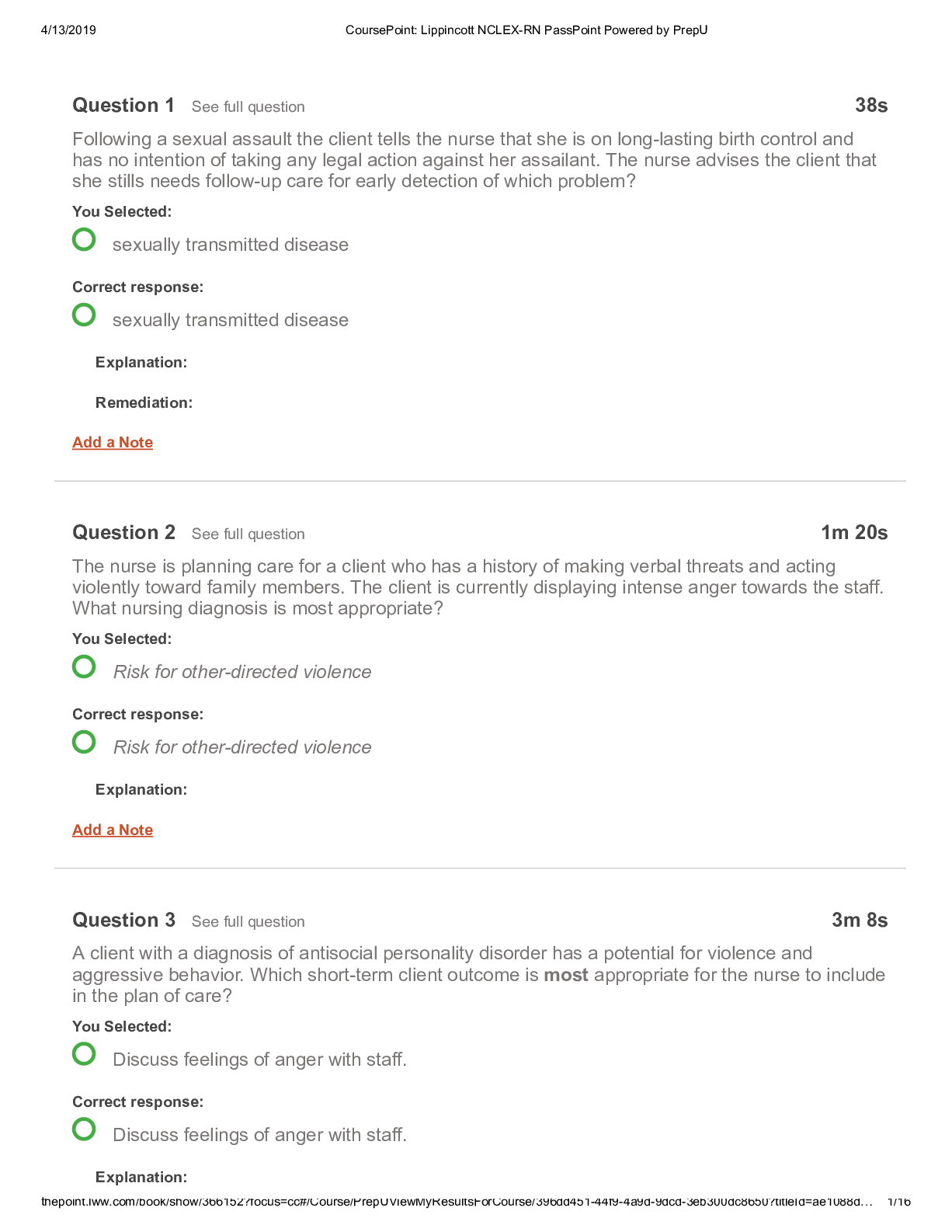
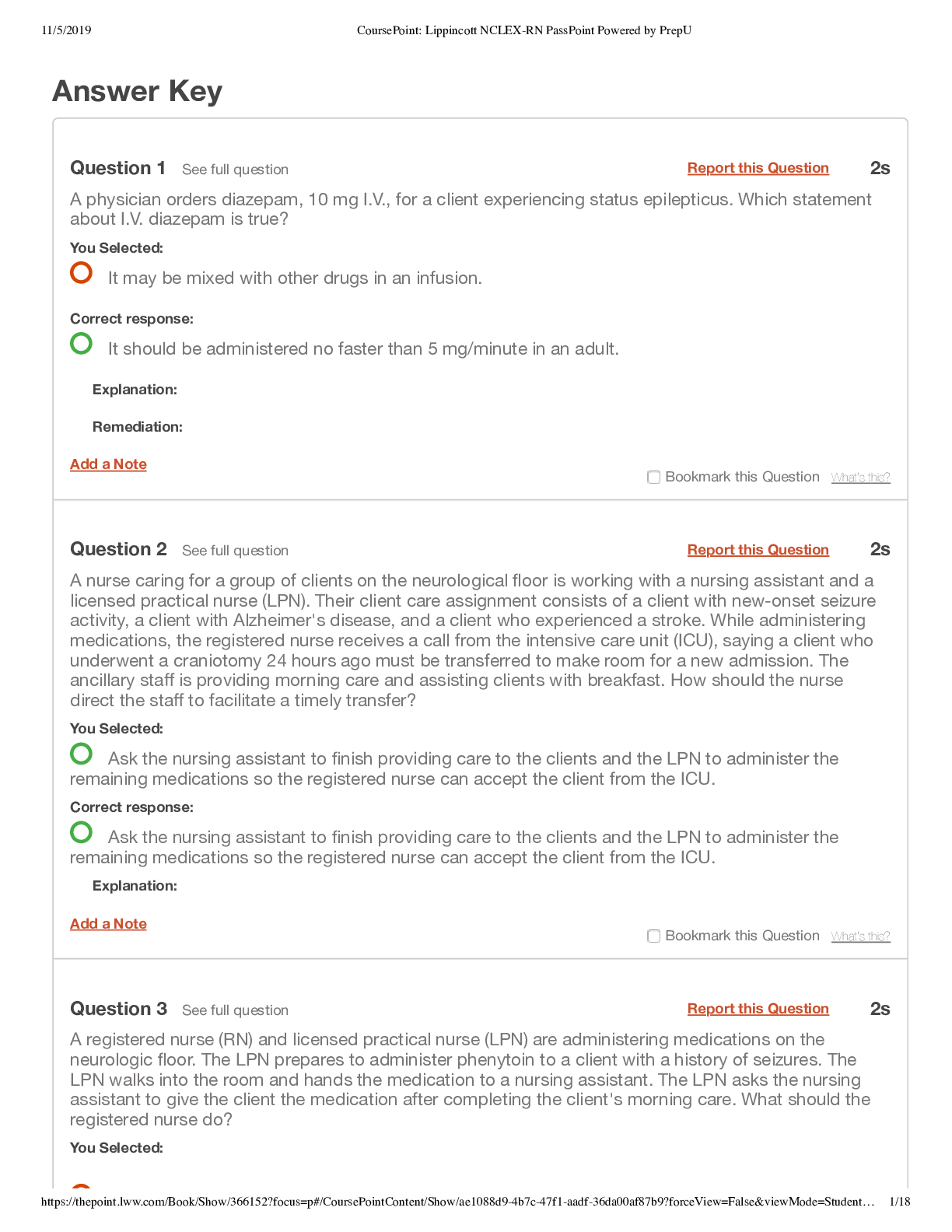
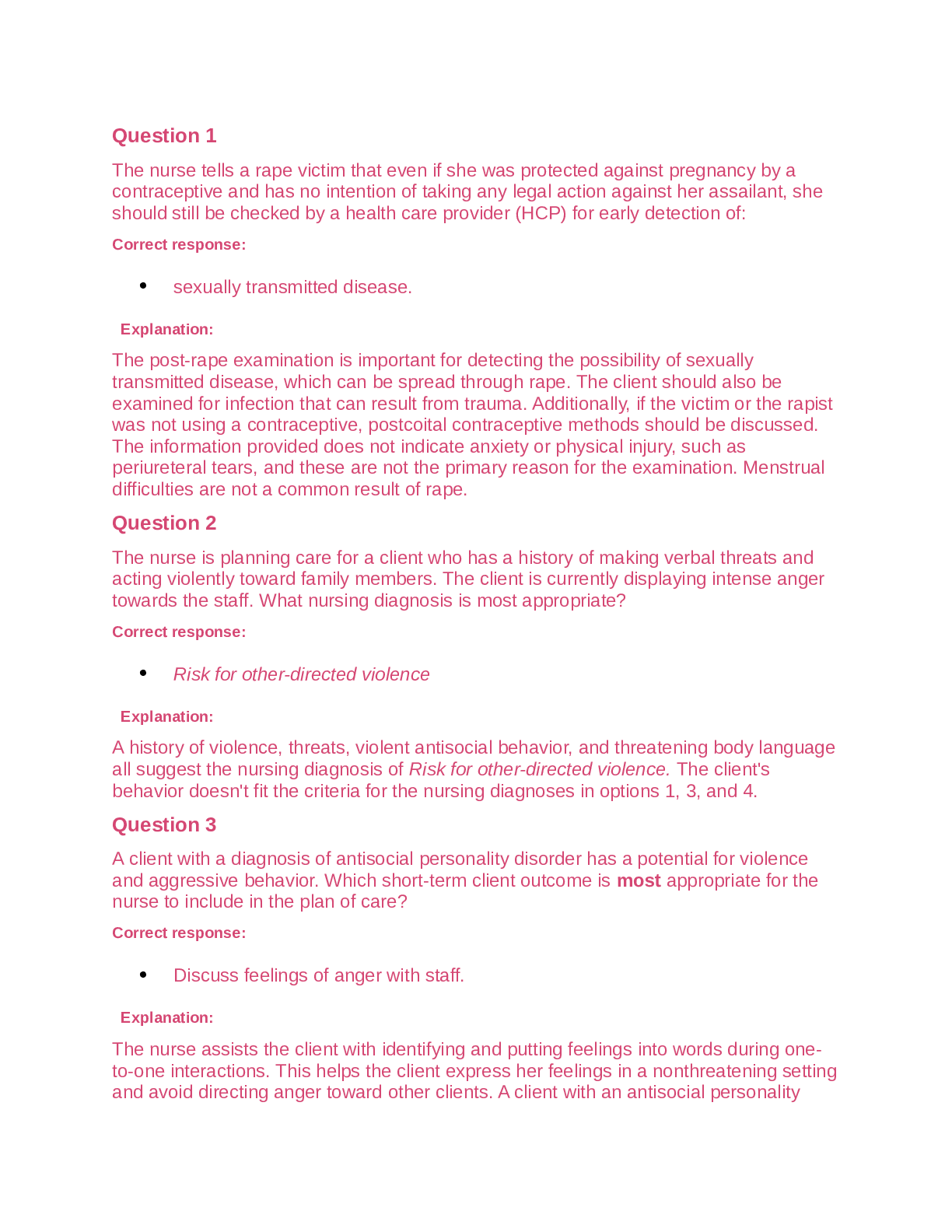
Week 2 Quiz Due No due date Points 100 Questions 20 Time Limit None Allowed Attempts 2 Instructions This is a quiz on the material covered this week. The 20-question quiz in... cludes, multiple choice, multiple answer, true/false, short answer, and matching questions. It is open book/open notes and can be retaken once. It is worth 100 points, with each question worth 5 points. Attempt History Attempt Time Score KEPT Attempt 2 7 minutes 72.5 out of 100 LATEST Attempt 2 7 minutes 72.5 out of 100 Attempt 1 106 minutes 62.5 out of 100 Correct answers are hidden. Score for this attempt: 72.5 out of 100 Submitted Sep 13 at 1:58am This attempt took 7 minutes. Question 1 5 / 5 pts IT Security staff implemented a new mobile application on every company-owned Android smart phone the same day the software was uploaded to the Google Play store. The issue with this act is that the IT staff did not throughly test this application in an isolated setting prior to distributing it to the masses. True False IncorrectQuestion 2 0 / 5 pts Which of the following is not a good example of user & device authentication? Automatically lock idle devices Remotely lock devices suspected of being unsecured in an unauthorized location Restricting screen time during business hours Requiring user name and password when accessing organization resources IncorrectQuestion 3 0 / 5 pts IT security personnel can do one of the following to start securing a company smart phone: Install anti-virus on the smart phone Allow employees to have administrative rights to the smart phone Have the employee register the company mobile phone solely in the employee's name Install TOR Browser Question 4 5 / 5 pts _____________ is defined as the ability to detect any intentional or unintentional change to transmitted data. IncorrectQuestion 5 0 / 5 pts The main deterrent for company owned mobile devices is: Invasion of Privacy Cost Phone personalization None of the above Question 6 5 / 5 pts Integrity Bring Your Own Devices (BYOD) policies ensure that organizations do not have to spend any money to implement the policy. True False Question 7 5 / 5 pts BYOD policy limitations involve the following: Compensation Privacy Data Integrity Equipment cost Question 8 5 / 5 pts A supervisor from the human resources walks into your office and puts a Samsung Galaxy S4 on your desk. It looks similar to the company issued phones but you are not certain. The Human Resources supervisor informs you that this phone belonged to an employee that was taking pictures of other employees in the restroom without their consent. The human resource supervisor tells you to examine the phone and leave a report on her desk. Seeing that you are a member of the IT security department, you should start analyzing that phone immediately. True False IncorrectQuestion 9 0 / 5 pts Most UICC/Sim Card tools will acquire the following information except: Last Numbers Dialed SMS messages International Mobile Subscriber Identity Email address book PartialQuestion 10 2.5 / 5 pts Europe & Asia GSM cell phones work on the following bands: 850 MHz 900 MHz 1800 MHz 1900 MHz Question 11 5 / 5 pts Some of the tasks that MDM policies can implement include: Clear passcode locks Wipe device remotely Update the operating system [Show More]
Last updated: 1 year ago
Preview 1 out of 10 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Mar 31, 2022
Number of pages
10
Written in
Additional information
This document has been written for:
Uploaded
Mar 31, 2022
Downloads
0
Views
97

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)







 Correct Study Guide, Download to Score A.png)
 Correct Study Guide, Download to Score A.png)



