Information Technology > QUESTIONS & ANSWERS > SEC 571 Week 8 Final Exam Multiple Choice & Essay: complete solutions (version 2). (All)
SEC 571 Week 8 Final Exam Multiple Choice & Essay: complete solutions (version 2).
Document Content and Description Below
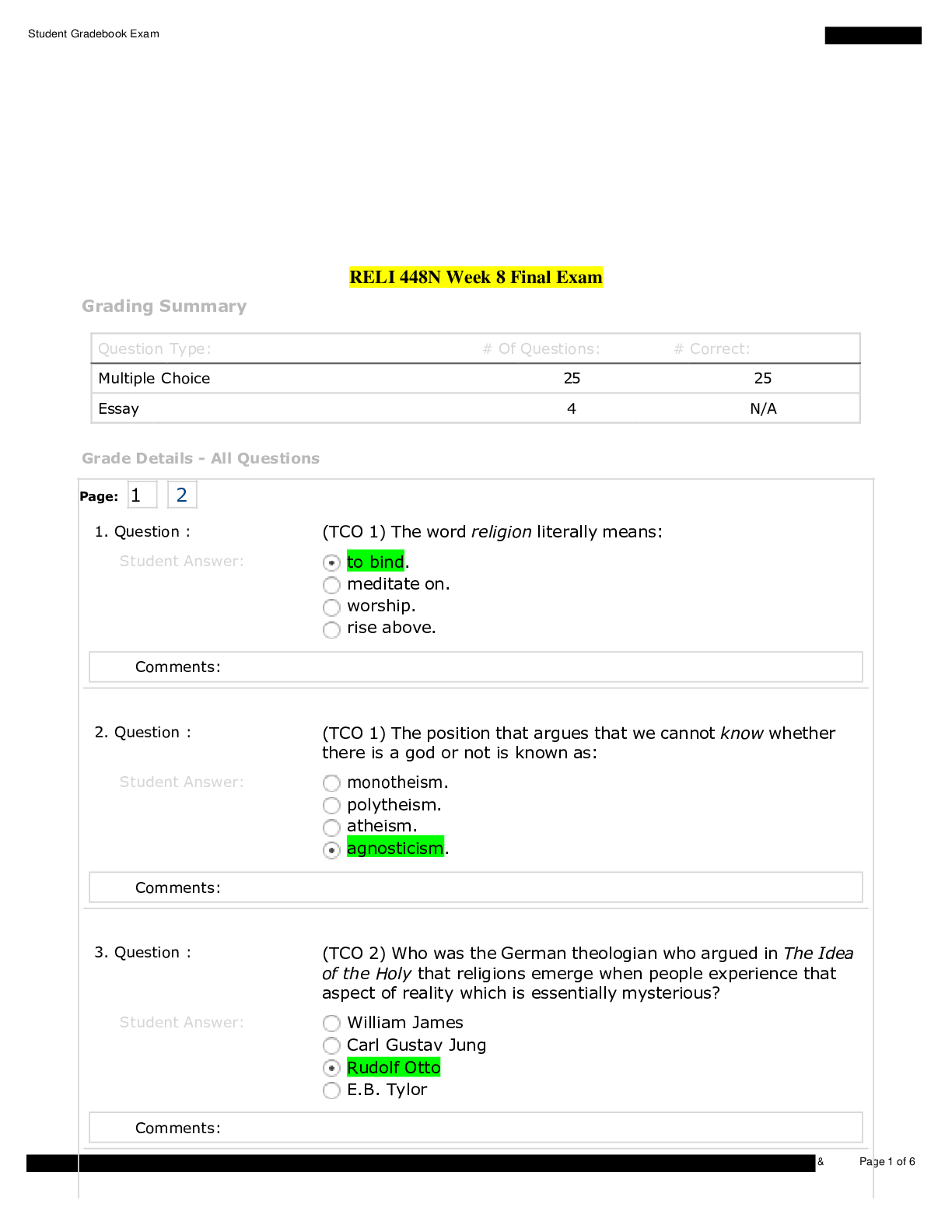
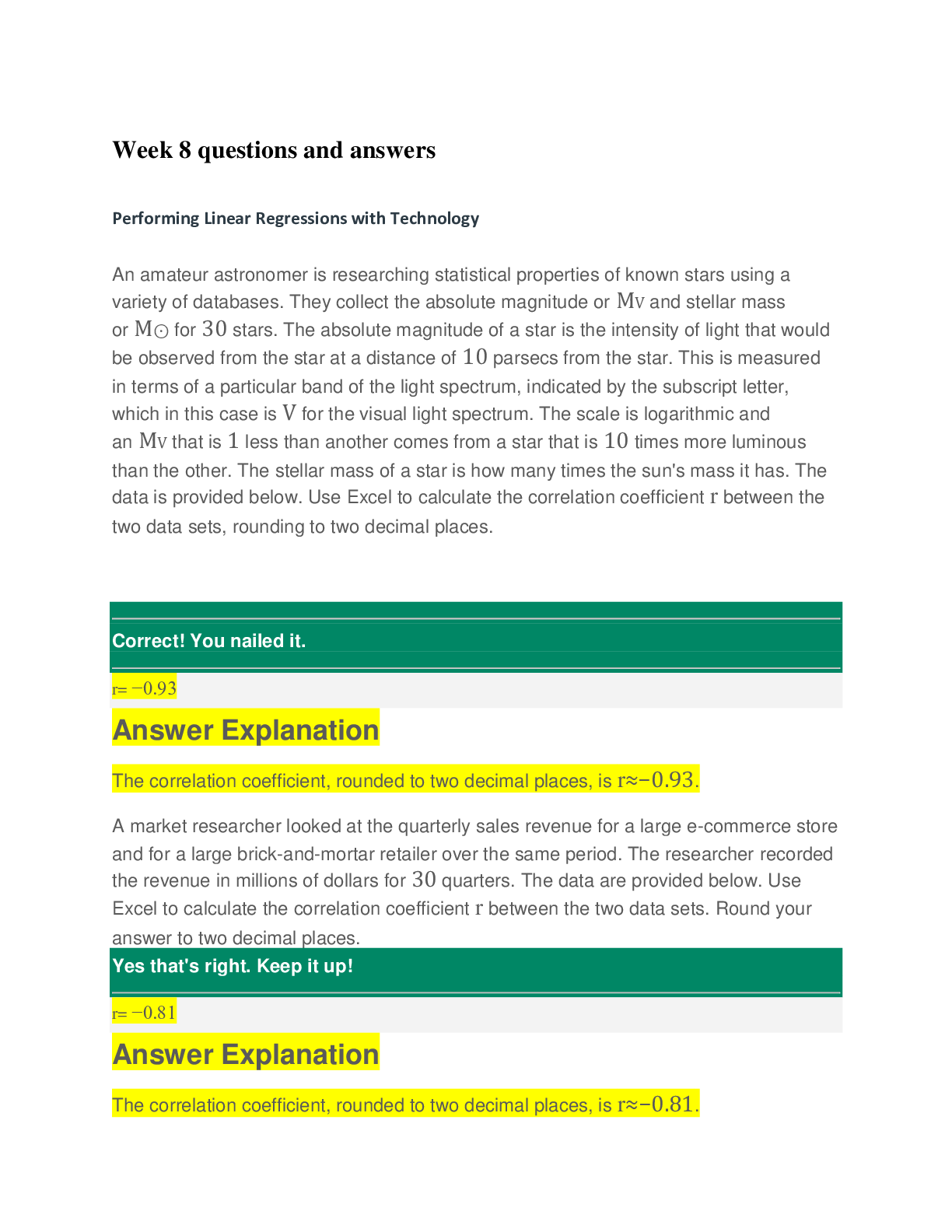
Week 8 : Final Exam - Final Exam Time Remaining: Question 1.1. (TCO A) List and assess at least three kinds of damage a company could suffer when the integrity of a program or company data are comp... romised. (A description of damage, not a definition of data integrity, is required.) (Points : 40) Question 2.2. (TCO B) Acme Films produces advertisements for cable television stations. They have two locations in a large metropolitan area. Building 1 contains the administrative, sales, marketing, human resources, development, and graphics departments. Building 2 contains the sound stages, production and post production facilities, equipment, and mobile unit storage. The two buildings, five miles apart, are connected by a VPN using a T1 connection. Each location is protected by hardware firewalls and each location has a DMZ. Building 1's DMZ includes Web, FTP, DNS, and e-mail servers. Building 2's DMZ includes an FTP server from which clients can access work product. Network-based IDS systems are placed in the DMZs. There are 75 Windows XP workstations in each location. Workstation security is centrally managed and includes anti-virus, anti-spyware, and patch management. File, application, database, and print servers at each location are protected by anti-virus, anti-spyware, and patch management. Internet access is provided to users via a proxy server and NAT. User authentication is controlled by Windows 2008 Active Directory and users must authenticate by using a smart card and entering a PIN. Discretionary access control methods are in use. List and assess three security threats faced by the information technology systems and list and describe 1 security control needed that would be appropriate to address each threat. (Points : 40) The three kinds of damage a company may suffer w hen the integrity of a program is compromised are: 1) The integrity of a data or program may be compromised w hen humans make errors. These errors include adding w rong data or making some technical errors w hich cost the company to million of dollars. 2)the integrity of data can be compromised in a w ay that include technical errors that happen during data transmission. Along w ith the grow th of e-commerce came an increasing reliance on softw are programs that automate tasks involving databases of customer information. This opens the door for computers to accidentally execute tasks that affect the company to maximum extent. 3) The integrity of a data can also be comprised in a w ay that malicious proprietors may be selling w rong softw are. In this case, sellers often make faulty or exaggerated claims about products and services that sometimes do not exist. The companies purchasing such softw ares may experience lost of data or the data may be corrupted. This study source was downloaded by 100000831988016 from CourseHero.com on 04-08-2022 07:32:25 GMT -05:00 https://www.coursehero.com/file/22312301/FinalExam/ Question 3.3. (TCO C) Why is a firewall usually a good place to terminate a Virtual Private Network (VPN) connection from a remote user? Why not terminate the VPN connection at the actual servers being accessed? Under what circumstances would VPN termination at the server be a good idea? (Points : 40) Question 4.4. (TCO D) Give 3 examples of how a person could unknowingly or unintentionally participate in a criminal act through their computer system. (Points : 40) Security threats faced by the information technology systems: 1. Physical access to devices - access should be for only few IT persons and Top Management 2. Telnet access to devices inside and outside (ssh ver 2 OK) - could be enabled , should be disabled to avoid any traffic sniffers access and brake login passw ords 3. Policies allow ed access from DMZ to internal users - could be enabled, should be disabled : from inside to DMZ access could be enabled but no reverse directions 4. Window s XP not anymore in use - use Window s 7 OS, XP not patched anymore it is high risk to use it Why is a firew all usually a good place to terminate a Virtual Private Netw ork (VPN) connection from a remote user? - It w ould be to risky if user w ould stay more then few hours, PC could be attacked or get infected during long term session. Many users using Internet access and VPN to company at the same time, it is alw ays risky keep connected and brow se Internet ( it is OK for sales and marketing but not for users w ho using DB access servers. Split Tunnel option should be disabled - if possible- so users can login to the netw ork but no Internet access, no risk for company. Why not terminate the VPN connection at the actual servers being accessed? - server access required authentication also - username and p/w , so if someone connected- w e can easy find out w ho, w hen, w hat time by checking log files Under w hat circumstances w ould VPN termination at the server be a good idea? - if to many users w ith admin rights connected to the server at the same time and server overloaded This study source was downloaded by 100000831988016 from CourseHero.com on 04-08-2022 07:32:25 GMT -05:00 https://www.coursehero.com/file/22312301/FinalExam/ Question 5.5. (TCO E) List five controls that could be used to maintain data availability in a networked environment. (Points : 40) Question 6.6. (TCO F) In the U.S., laws are enforced by police agencies and the courts. What are ethics and who enforces them? (Points : 40) The three examples are : 1) Softw are piracy is one of the most common computer crimes. Copying softw are for distribution or personal use is considered an illegal act. Programs that are not protected w ith encryption keys (installation ID number), malw are protection or other types of anti-piracy methods are easy to copy. 2) A computer virus transmitter is someone w ho creates a malicious virus to infect computers from functioning properly, run annoying programs and gain access to the victim's personal data. This type of softw are is commonly know n as "malw are." Persons can unknow ingly dow nload these programs through w ebsites, emails and pop-up w indow s. 3)Computer fraud happens w hen a victim is conned into believing that he w ill receive money or something else of value. There are common types of this crime currently in practice. "Phishing" scams involve creating fake emails w hile pretending to be a legitimate business like a bank or credit company that ask the victim to confirm personal information. subject or object ?? administration of rights: the ability to control the assignment and revocation of administration of rights: the ability to control the assignment and revocation of access rights betw een subjects and objects ?? verification of rights: mediation of the attempt of a subject to exercise rights w ith verification of rights: mediation of the attempt of a [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages
Instant download
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Apr 08, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Apr 08, 2022
Downloads
0
Views
51


.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)