Information Technology > QUESTIONS & ANSWERS > SEC 571 Week 8 Final Exam Multiple Choice & Essay: complete solution guide (2021/2022) - DeVry Unive (All)
SEC 571 Week 8 Final Exam Multiple Choice & Essay: complete solution guide (2021/2022) - DeVry University, Columbus North.
Document Content and Description Below
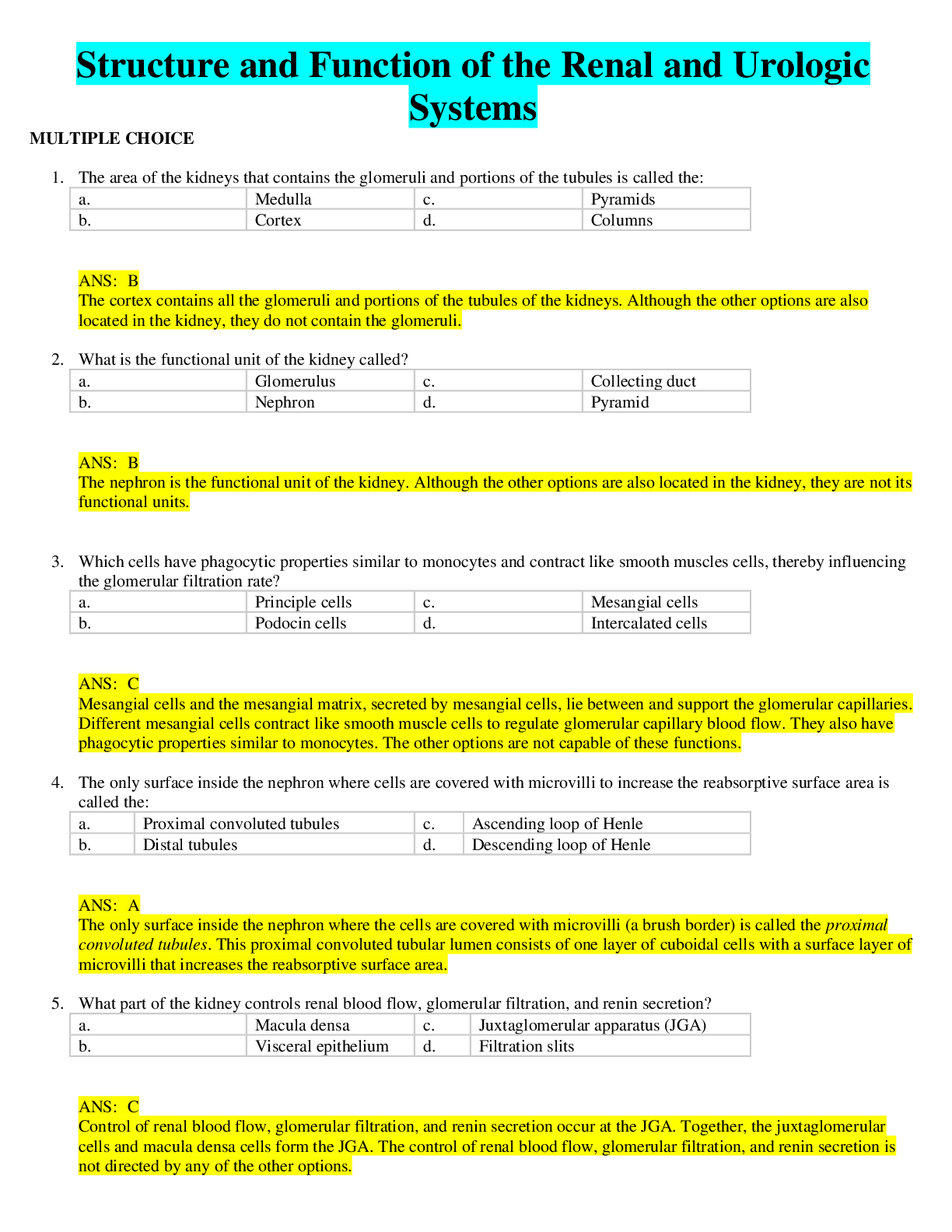
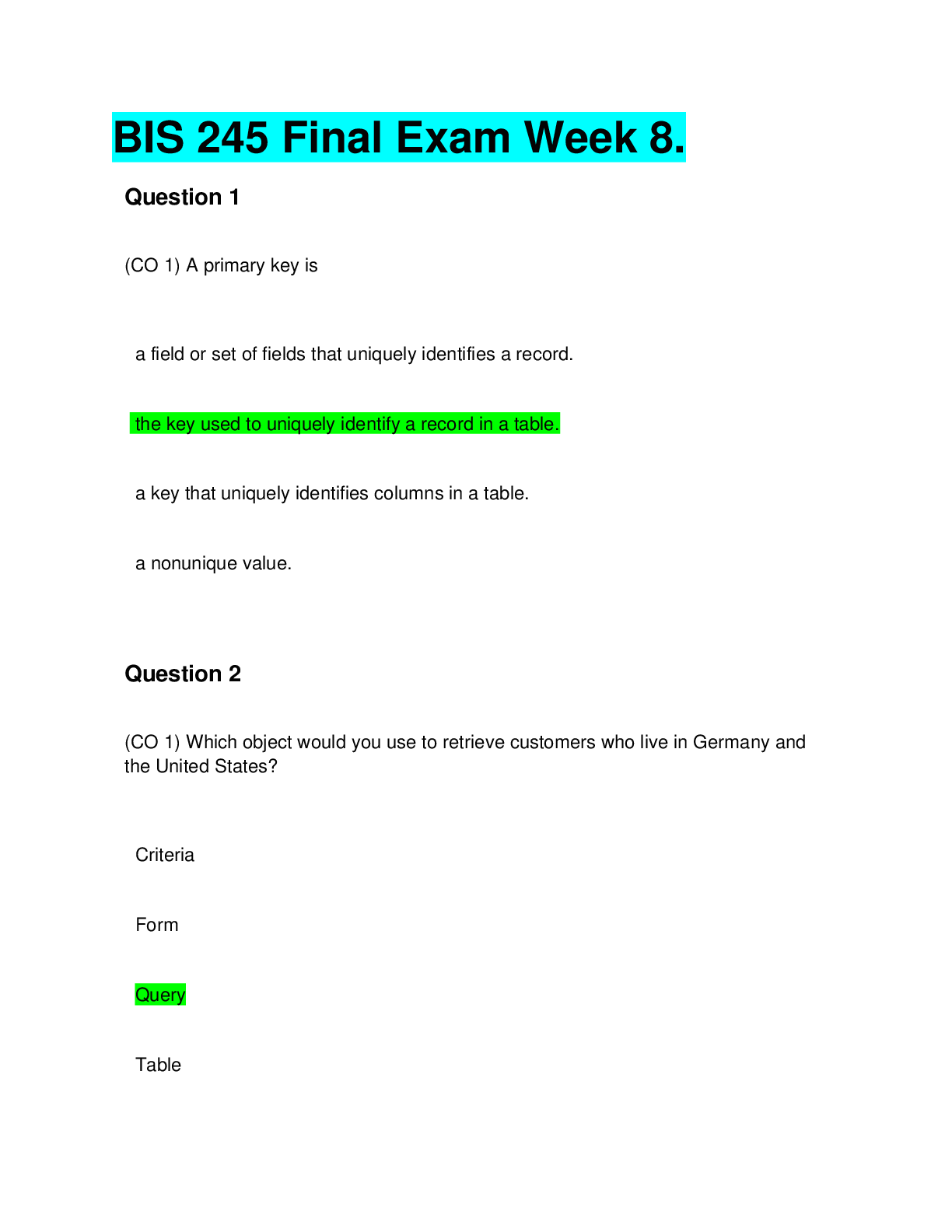
1. (TCO A) You are responsible for developing a security evaluation process that can be used to assess various operating systems both during and after development. List the five most desirable quali... ties your evaluation process should have and explain why they are important. (Be sure to address qualities of the evaluation process, not specific metrics for assessment of operating systems.) (Points : 40) The evaluation process can be approached and attempted with our own set of parameters. The desirable qualities that would be important for the evaluation process have been described below - Speed – This is to ensure that in the product is ready for the competitive market soonest possible, given that time is money and companies need to get their products out in the market as soon as possible Thoroughness – This is required to guarantee that all the various features and aspects of the product have been evaluated Portability – This quality ensures that the product is platform independent and that the evaluation is applicable without any platform related constraints or dependencies, thus allowing the evaluation process to be used for a range of systems and products Consistency – This criterion is to ensure that all similar products are judged and evaluated based on the same set of parameters, and that the same product when judged by different panels receive the same results Granularity – This is to ensure that the evaluation of the product is based on adequate level of detailing, which ensures that all parts of the system are evaluated effectively 2. (TCO B) The Open Systems Interconnection model is inherently inefficient. On the source host, each layer must take the work of higher layers, add some result, and pass the work to lower layers. On the destination host, each layer must process these results from lower layers and pass the appropriate information to upper layers. Surely this wrapping and unwrapping process is inefficient. Assess the security advantage of this layered approach. (Points : 40) As per the Open Systems Interconnection, or the OSI model, there are seven layers through which a message needs to pass from a source to a destination machine. Each of the layers perform different functionalities, and are together responsible for the complete and secure transmission of the message. Each layer performs some sort of function on the message before passing it to the next layer. This mechanism ensures high level of security. For example, at the source system, the seventh layer, or the Application layer interacts with the user and passes the message to the sixth or Presentation layer. The Presentation layer on the host system processes the message and This study source was downloaded by 100000831988016 from CourseHero.com on 04-08-2022 07:35:48 GMT -05:00 https://www.coursehero.com/file/10735851/SE571-Final-Exam-Completed/ encrypts and compresses the message before passing it to the lower Session layer, while at the destination system, the Presentation layer will decompress and decrypt the message that is passed from the Session layer. Similarly, after further processing when the message reaches the second layer or the Data Link layer the message is broken down into smaller packets or frames and each frame is appended with an error control mechanism such as checksum etc, to ensure that when the frames are received at the destination machine, the integrity of the frames can be verified. At the destination host, the data link layer will verify if each of the frames were received correctly and if not it will alert the source to resend the required frames. Although the wrapping and unwrapping process might seem inefficient, the security of delivering message and ensuring that there is no data loss is achieved through this layered approach in OSI model. 3. (TCO C) Why is a firewall usually a good place to terminate a Virtual Private Network (VPN) connection from a remote user? Why not terminate the VPN connection at the actual servers being accessed? Under what circumstances would VPN termination at the server be a good idea? (Points : 40) Answer - The main feature of a firewall is to be provide access control and filter all the incoming traffic from the less trusted ‘external ‘ network to ensure the protection and safety of the ‘internal’ network. Certain scenarios demand that firewalls be used to implement a VPN. This is achieved when the user tries to establish a connection by requesting for a VPN session with the firewall. After an exchange of session encryption key between the user’s client and the VPN, the firewall can filter and encrypt traffic between the two systems. This helps to achieve segmented user access in large networks, where only the users who have the required access are able to connect to the network. In such cases, where the user is accessing the VPN connection from an external location and network, it is better to terminate the connection at the firewall rather than the server as it will be more time consuming and will require additional authentications. In scenarios where the user is accessing VPN from within the internal network, it would be unnecessary to terminate the connection from the firewall. It would be more efficient to terminate the VPN connection at the actual servers as it would require lesser time to connect or authenticate than terminating at the firewall. 4. (TCO D) A computer programmer has been arraigned for a computer crime. She is suspected of having accessed system files on a public Web server. The programmer's attorney argues that his client was only trying to determine if the website was secure and that no harm was done to the Web server or its system files. The programmer's attorney also argues that it is possible that the log files that show that his client accessed system files were tampered with. The attorney claims that the Web server was made accessible to the public anyway so that there was no violation of the law and that the arraignment This study source was downloaded by 100000831988016 from CourseHero.com on 04-08-2022 07:35:48 GMT -05:00 https://www.coursehero.com/file/10735851/SE571-Final-Exam-Completed/ against her client should be thrown out. You're the judge. What is your analysis of these arguments? (Points : 40) Answer – Given that the programmer was an employee of the company, she is expected to know what are the information security policies of the company and should be compliant with it. Also, should there be any vulnerability in the company’s computer’s network that she found out; it would have been her duty to proactively inform the company so that it could take appropriate measures. However, in this case, we can see that the employee probably would have stumbled upon or purposely tried to access the company network from outside, and did not inform the right authorities. In addition to it, she had exposed the company’s internal systems to grave danger that could have caused a lot of damage to the company and its information. Therefore, even if the server was made accessible to the public due to a flaw, she is still responsible to trying to take advantage of this flaw and did not do her duty as a responsible employee. In my opinion, the claims that are being made by the attorney are not valid, and the company has proof that there has been an attempt to get illegal access to the systems. Hence the programmer would be guilty of breach and there should be effort to establish what she was trying to do, and if she had any mal intention for coming to a judgment in this case. 5. (TCO E) After reading about [Show More]
Last updated: 1 year ago
Preview 1 out of 5 pages
Instant download

Buy this document to get the full access instantly
Instant Download Access after purchase
Add to cartInstant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Apr 08, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Apr 08, 2022
Downloads
0
Views
80

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)