Computer Science > QUESTIONS & ANSWERS > DOD Cyber Awareness 2022 Knowledge Check (Answered, scored A) (All)
DOD Cyber Awareness 2022 Knowledge Check (Answered, scored A)
Document Content and Description Below
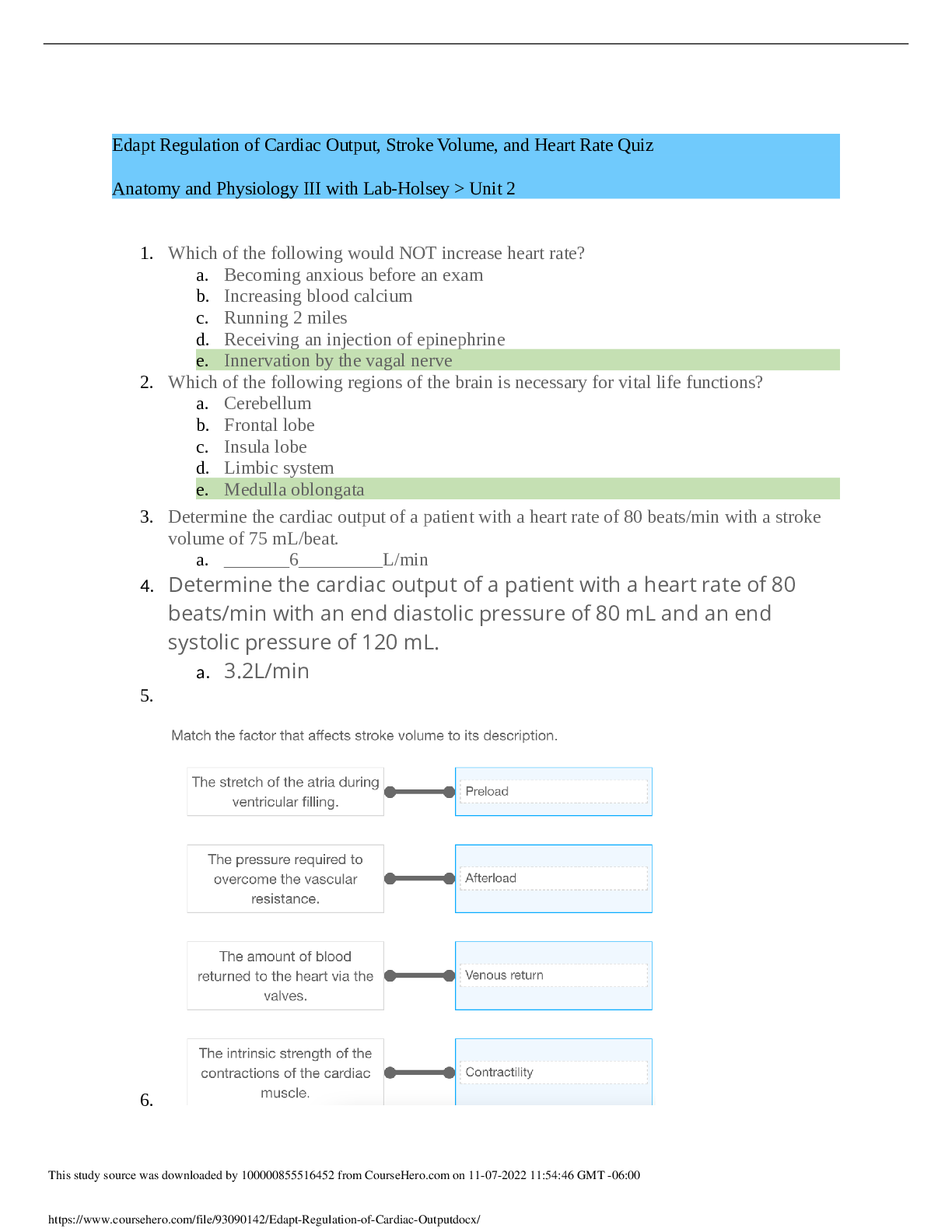
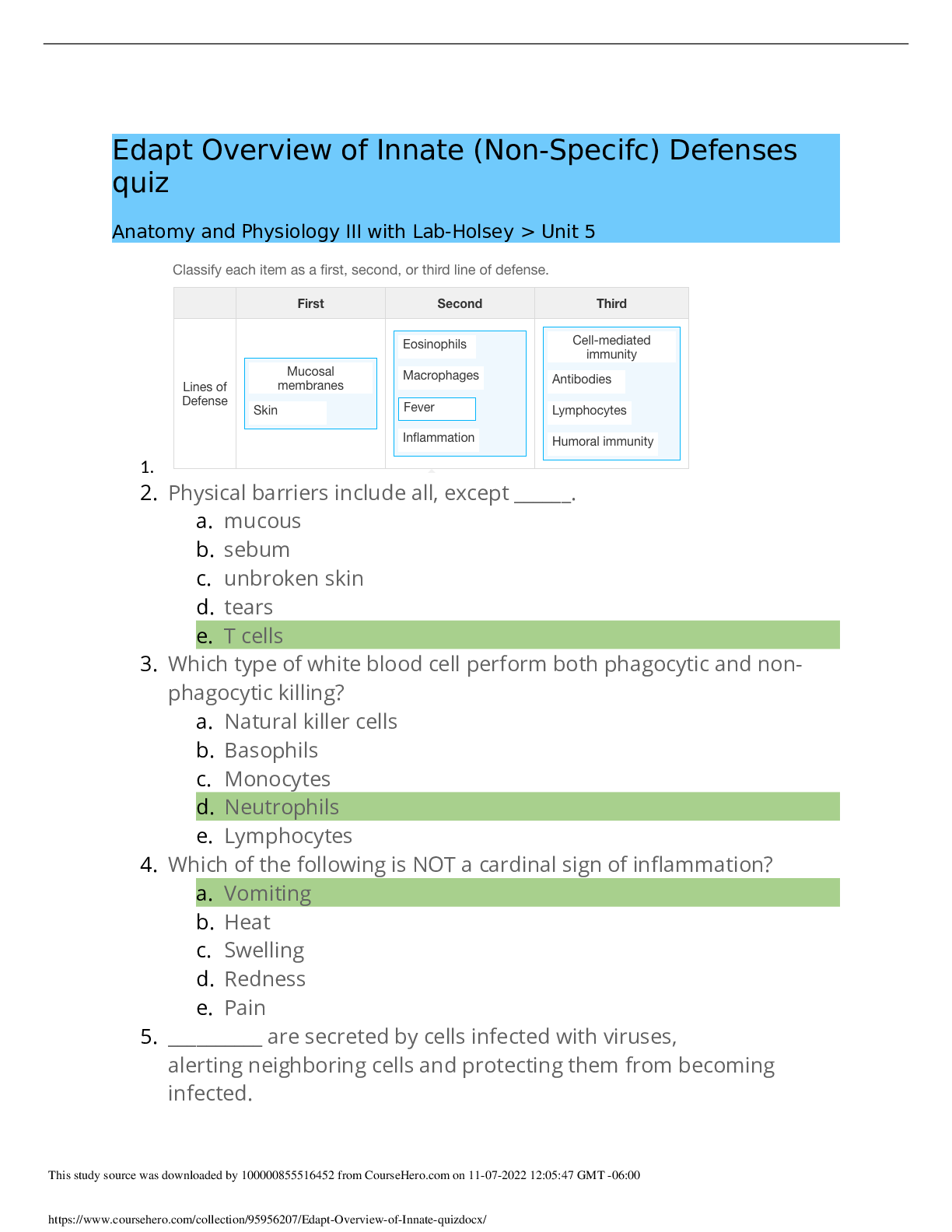
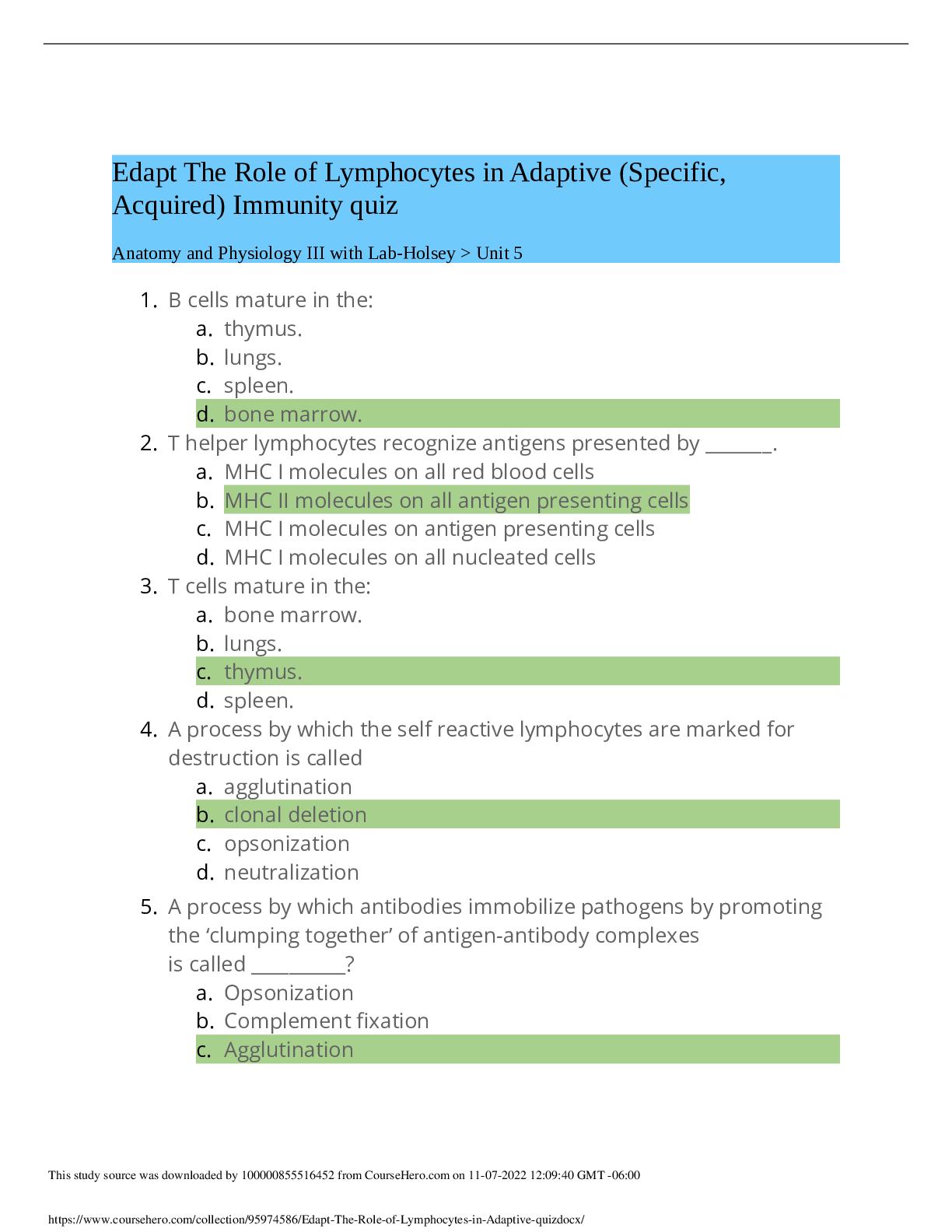
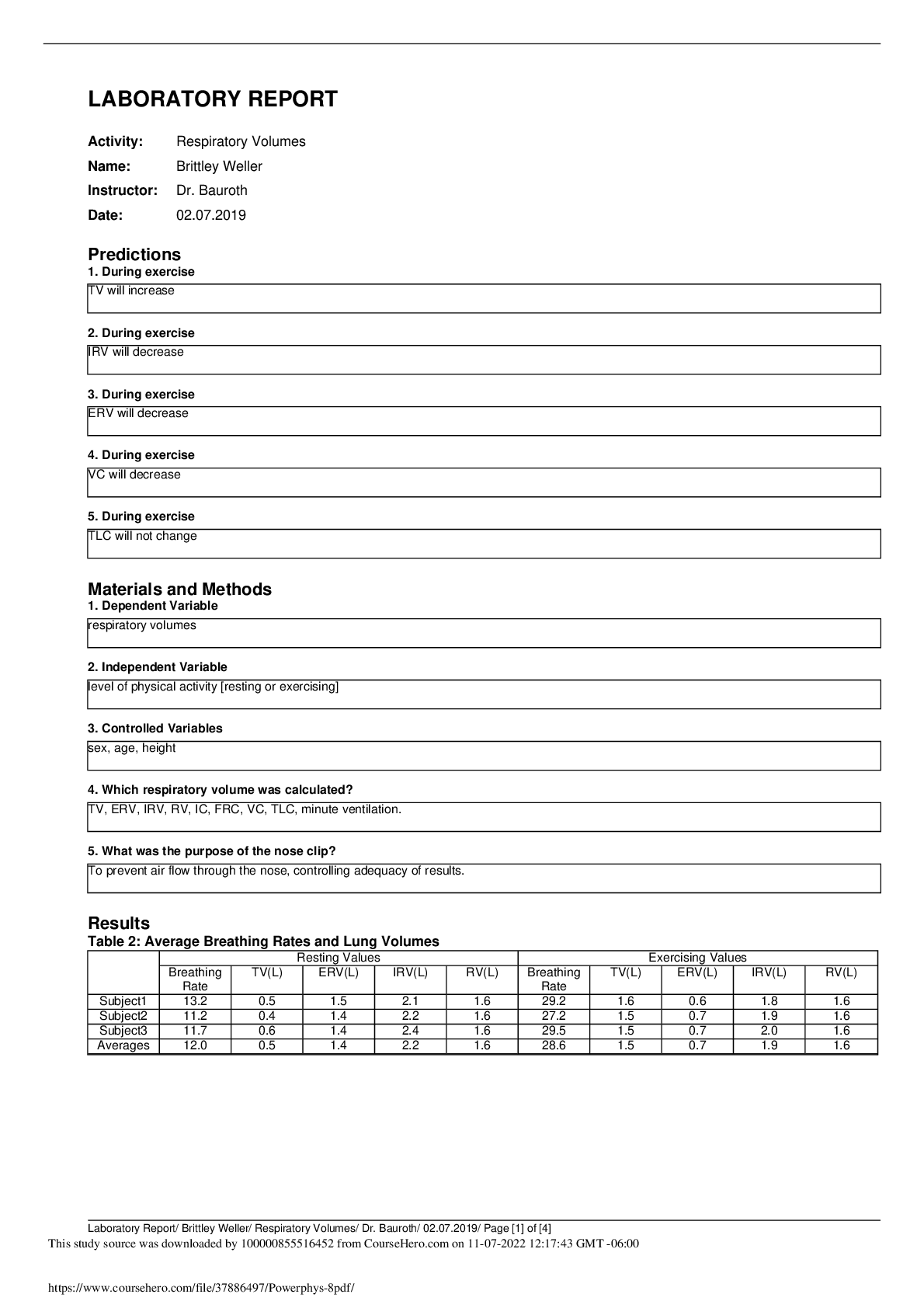
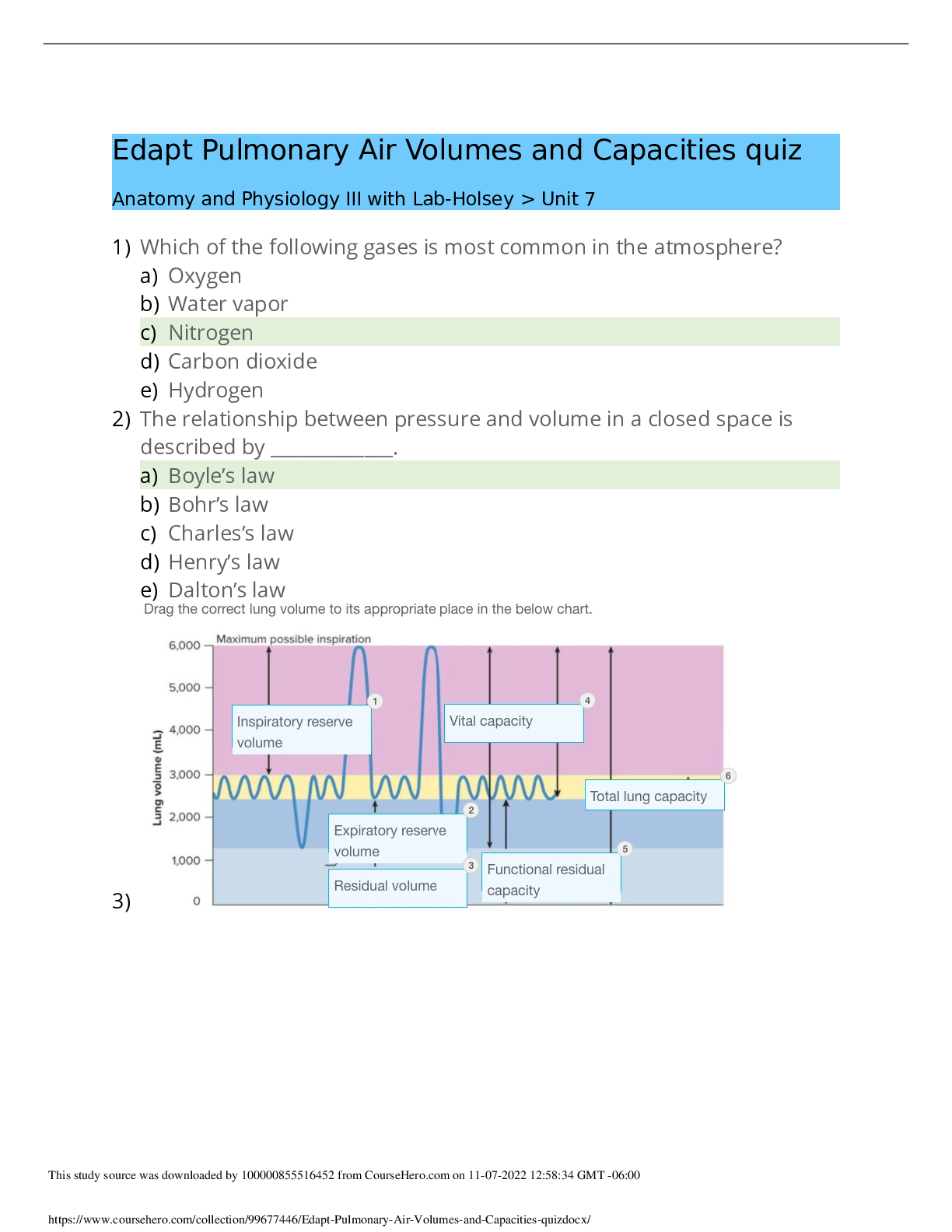
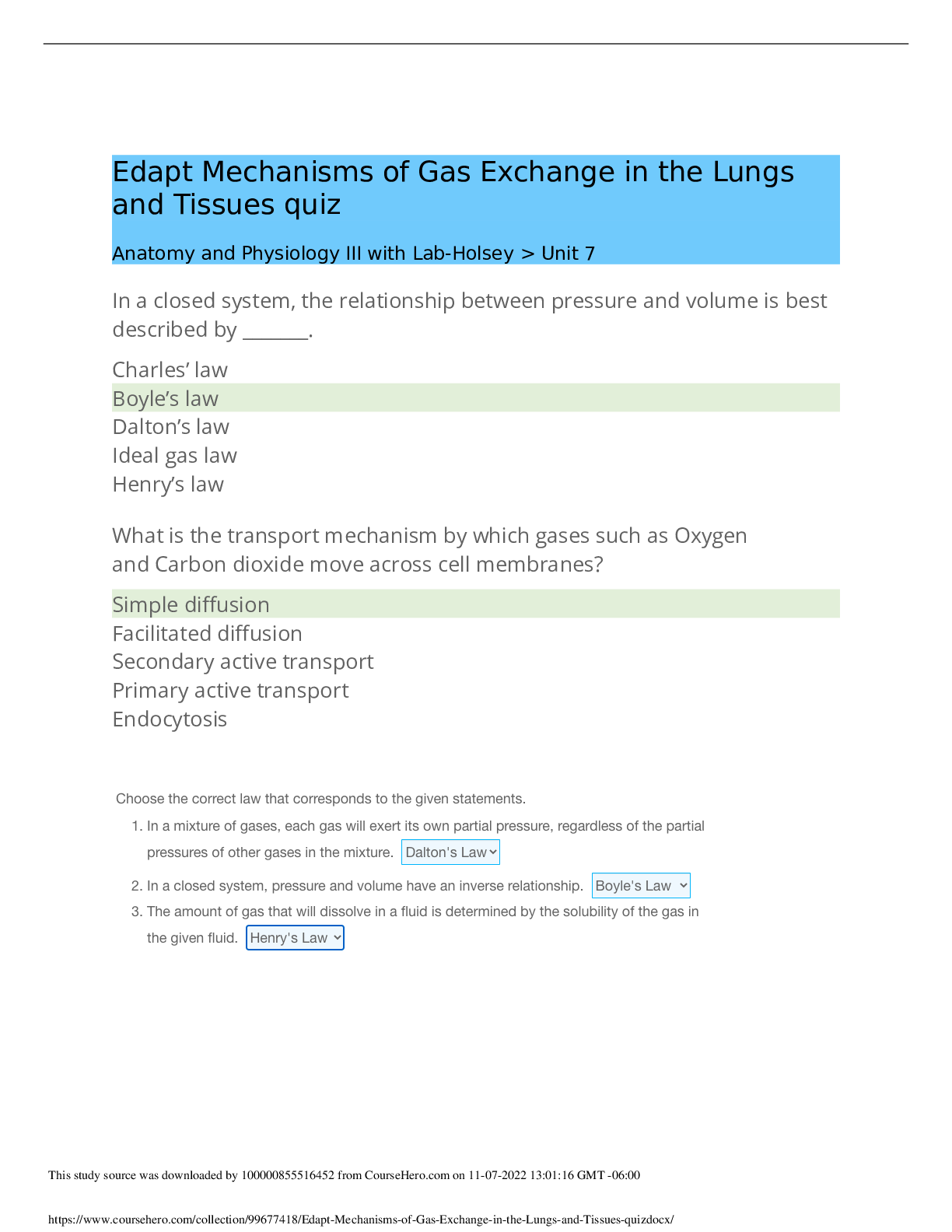
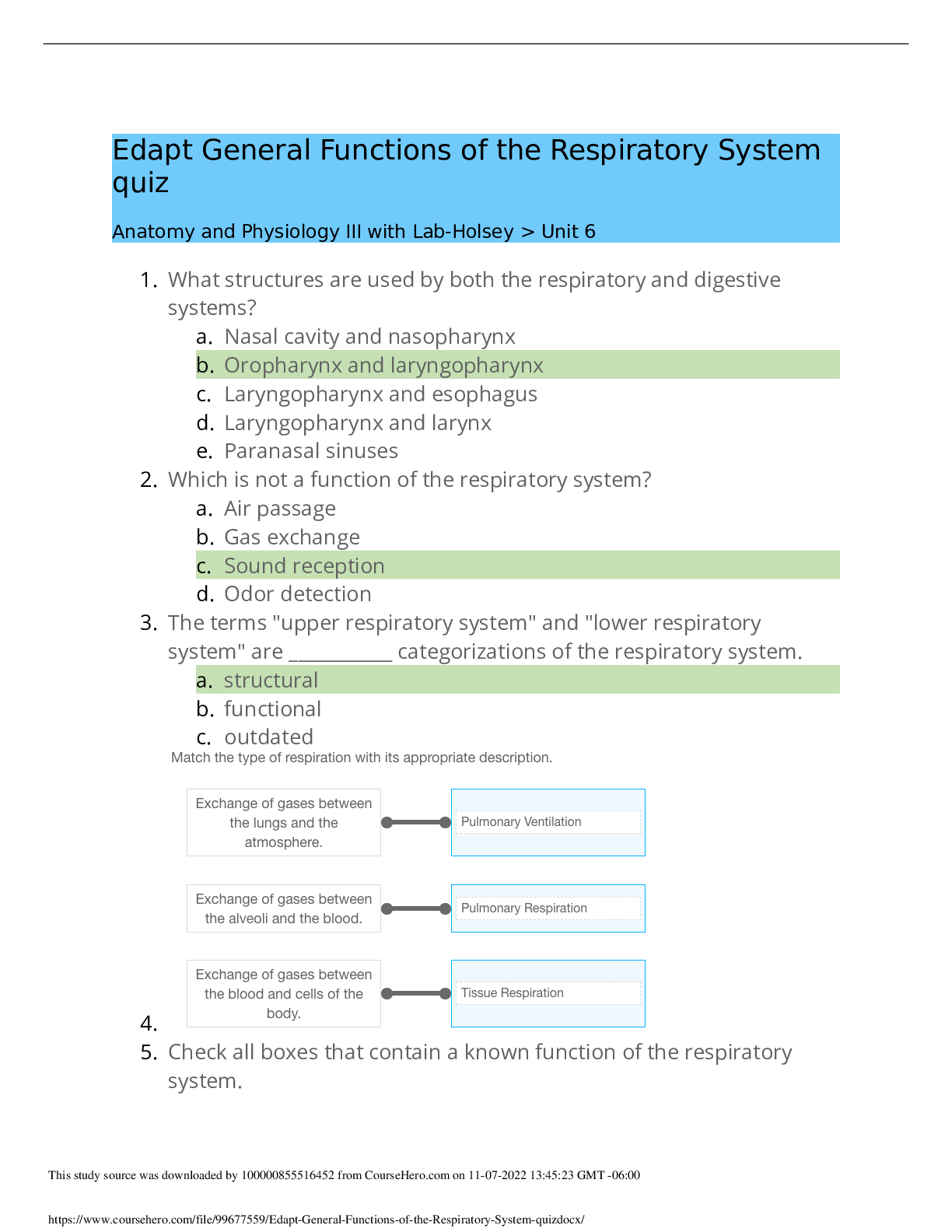
DOD Cyber Awareness 2022 Knowledge Check (Answered,scored A) Spillage: What should you do if a reporter asks you about potentially classified information on the web? - ✔✔Refer the reporter to ... your organization's public affair office What must users ensure when using removable media such as a compact disk (CD)? - ✔✔It displays a label showing maximum classification, date of creation, point of contact, and Change Management (CM Control Number. What should you do when you are working on an unclassified system and receive an email with a classified attachment? - ✔✔Call your security point of contact immediately. Which classified level is given to information that could reasonably be expected to cause serious damage to national security? - ✔✔Secret Under what circumstances is it acceptable to use your Government-furnished computer to check personal e-mail and do other non-work-related activities? - ✔✔If allowed by organizational policy. What actions should you take when printing classified material within a Sensitive Compartmented Information Facility (SCIF)? - ✔✔Retrieve classified documents promptly from printers. What actions should you take upon hearing a discussion involving Sensitive Compartmented Information (SCI) while seated in a cafeteria with an SCI Facility (SCIF)? - ✔✔XXXX NOT CORRECT: Remind those involved that such a discussion should not take place in common areas within a SCIF. training states: Physically assess that everyone within listening distance is cleared and has a need-toknow for the information being discussed. (you cannot assume everyone in the SCIF is cleared for that sci information) Which of the following is true of protecting classified data? - ✔✔Classified material must be appropriately marked When classified data is not in use, how can you protect it? - ✔✔Store classified data appropriately in a GSA-approved vault/container. What type of activity or behavior should be reported as a potential insider threat? - ✔✔Coworker making consistent statements indicative of hostility or anger toward the United States and its policies. In setting up your personal social networking service account, what email address should you use? - ✔✔Your personal email address/addresses When is the safest time to post details of your vacation activities on your social networking website? - ✔✔When your vacation is over, after you have returned home What are some potential insider threat indicators? - ✔✔Difficult life circumstances such as substance abuse, divided loyalty or allegiance to the U.S., and extreme, persistent interpersonal difficulties. Which of the following terms refers to someone who harms national security through authorized access to information system? - ✔✔Insider Threat Under what circumstances could unclassified information be considered a threat to national security? - ✔✔If aggregated, the information could become classified. Under which circumstances is permitted to share an unclassified draft document with a non-DoD professional discussion group? - ✔✔As long as the document is cleared for public release, you may share it outside of DoD. How many the Cyberspace Protection Conditions (CPCON) are there? - ✔✔5 How many potential insider threat indicators does a person who is playful and charming, consistently wins performance awards, but is occasionally aggressive in trying to access sensitive information display? - ✔✔1 indicator A man you do not know is trying to look at your Government-issued phone and has asked to use it. What should you do? - ✔✔Decline to lend the man your phone. Which of the following is NOT considered a potential insider threat indicator? - ✔✔New interest in learning a foreign language What is the best practice while traveling with mobile computing devices? - ✔✔Maintain possession of your laptop and other government-furnished equipment (GFE) at all times. What is the best way to protect your Common Access Card (CAC)? - ✔✔Maintain possession of it at all times. While you are waiting for your lunch bill, a stranger picks up your Government-issued phone from your table and proceeds to exit the facility with it. What should you do? - ✔✔Try to observe the direction taken and any other useful information and immediately make a report to your security point of contact. What should you do if you receive a game application request that includes permission to access your friends, profile information, cookies, and sites visited? - ✔✔Decline the request. You receive a call from someone from the help desk who needs your assistance with a problem on your computer. How should you respond? - ✔✔Ask [Show More]
Last updated: 1 year ago
Preview 1 out of 9 pages
Instant download

Instant download
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
May 22, 2022
Number of pages
9
Written in
Additional information
This document has been written for:
Uploaded
May 22, 2022
Downloads
0
Views
207

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)

.png)
.png)

.png)
.png)
.png)