Telecommunication and Information Technology > EXAM REVIEW > University of the Cumberlands EMISS ISOL532 Telecommunications and Network Security. Midterm Exam. 6 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and Network Security. Midterm Exam. 60 Q&A
Document Content and Description Below
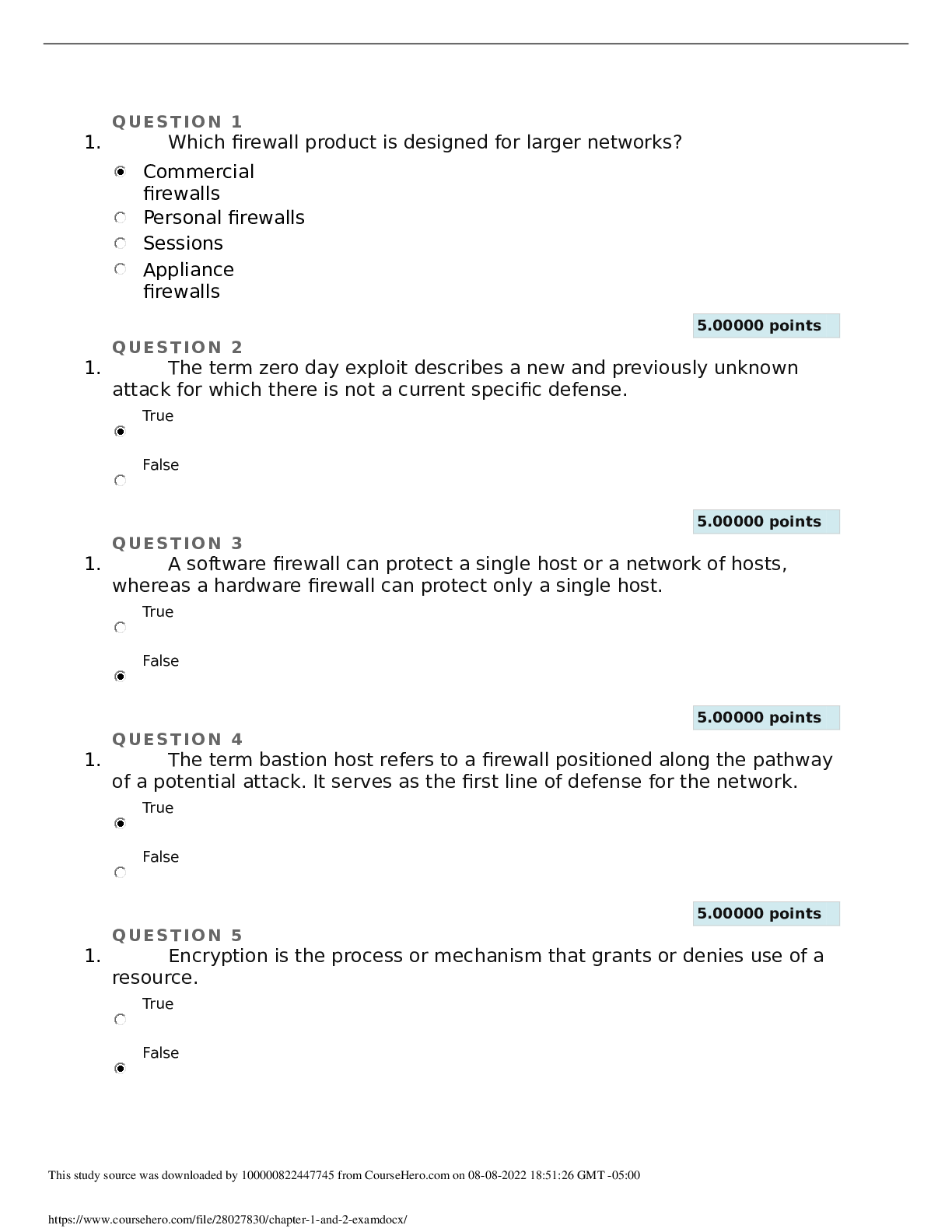
Question 1 1. Intrusion Detection System (IDS) is a security mechanism that detects unauthorized user activities, attacks, and network compromises. True False 10 points Question 2 1. Which of t... he following is not a characteristic of a private address? They are leased. They require translation. They can be mixed with public addresses. They are isolated from the Internet. 10 points Question 3 1. Which of the following terms describes hiding information from unauthorized third parties? Virtual Private Network (VPN) Split tunnel Cryptography Authentication, Authorization, and Accounting (AAA) Services 10 points Question 4 1. Which name is given to a rogue program that automatically dials a modem to a pre-defined number to auto-download additional malware to the victim or to upload stolen data from the victim? Adwar e Sector Spywa re Dialer Save and Submit10 points Question 5 1. Which type of architecture recognizes that the VPN is vulnerable to attack if placed directly in the Internet, and therefore places the Internetfacing VPN connection behind a firewall? Two-factor architecture Internally connected architecture Bypass architecture DMZ architecture 10 points Question 6 1. A personal firewall is an appliance firewall placed on the border or edge of an organization’s network. True False 10 points Question 7 1. What attack cracks a password or encryption key by trying all possible valid combinations from a defined set of possibilities (a set of characters or hex values)? Brute-force attack Hybrid attack Dictionary password attack Modeling 10 points Question 8 1. A private key is kept secret and used only by the intended entity. True False 10 pointsQuestion 9 1. Denial of service (DoS) attacks cannot be detected by a firewall. True False 10 points Question 10 1. Social engineering is the craft of manipulating people into performing tasks or releasing information that violates security. True False 10 points Question 11 1. A hacker uses a valid IP address of an internal host, and then from an external system, the hacker attempts to establish a communication session with the internal host over a multitude of different ports. This is called internal code planting. True False 10 points Question 12 1. Which of the following refers to the malicious insertion of scripting code onto a vulnerable Web site? Insertion attack Upstream filtering Keystroke logger Cross-site scripting (XSS) 10 points Question 13 1. Which of the following characteristics relates to access control? The feature of network design that ensures the existence of multiple pathways of communication.An attack that occurs when a hacker uses a network sniffer to watch a communications session to learn its parameters The process or mechanism of granting or denying use of resources; typically applied to users or generic network traffic The process of confirming the identity of a user 10 points Question 14 1. Which of the following characteristics relates to enumeration? The process of discovering sufficient details about a potential target to learn about network or system vulnerabilities An application attack in which a hacker submits SQL expressions to cause authentication bypass, extraction of data, planting of information, or access to a command shell A criminal whose objective is to compromise IT infrastructures A logical division of data composed of one or more sectors on a hard drive 10 points Question 15 1. Which of the following is commonly used with an authentication header to provide both confidentiality and integrity protection for communications? Internet Key Exchange (IKE) Layer 2 Forwarding (L2F) Encapsulating Security Payload (ESP) Point-to-Point Protocol (PPP) 10 points Question 16 1. Which of the following is given to an Application Layer protocol used by e-mail clients to receive messages from an e-mail server? Simple Mail Transfer Protocol (SMTP) Post Office Protocol (POP) Transmission Control Protocol/Internet Protocol (TCP/IP) File Transfer Protocol (FTP) 10 points Question 171. Which of the following documents an organization's rules for using a VPN? Hairpinning Remote access policy Service level agreement Vaporware 10 points Question 18 1. Which of the following refers to a form of IDS/IPS detection based on a collection of samples, patterns, signatures, and so on stored in a database of known malicious traffic and events? All traffic or events that match an item in the database are considered abnormal and potentially malicious. Database-based detection Firewalking Anomaly-based detection False Positive 10 points Question 19 1. Which of the following describes identity and access management (IAM)? The security discipline that enables the right individuals to access the right resources at the right times and consistent with organizational policy Portions of a software system that unauthenticated users can run A form of security based on hiding details of a system or creating convolutions that are difficult to understand to overcome the obscure methodology A policy of allowing or even encouraging employees, contractors, and others to connect their own computers, smartphones, and other devices to their organization’s networks 10 points Question 20 1. Which command-line or graphical interface is used to control and configure a device?Port-based network access (Admission) control (PNAC) Fair queuing Management interface Signature 10 points Question 21 1. Which of the following refers to encoding and decoding information using related but different keys for each process? Digital certificate Asymmetric cryptography Ciphertext Algorithm 10 points Question 22 1. Which of the following refers to the end user’s desktop devices such as a desktop computer, laptop, VoIP telephone, or other endpoint device? LAN Domain Workstation Domain WAN Domain Remote Access Domain 10 points Question 23 1. Nonrepudiation ensures that a sender cannot deny sending a message. True False 10 points Question 24 1. Which of the following refers to a network access control or admission control (NAC) used on individual network access devices such as firewalls, VPN gateways, and wireless routers to offload authentication to a dedicated authentication server/service?Port-based network access (admission) control (PNAC) Database-based detection Management interface Access control list (ACL) 10 points Question 25 1. Which of the following characteristics relates to a demilitarized zone (DMZ)? Confidence in the expectation that others will act in your best interest or that a resource is authentic A type of perimeter network used to host resources designated as accessible by the public from the Internet A form of networking where each computer is a peer A host on a network 10 points Question 26 1. Which name is given to an entrance or exit point to a controlled space? Physical layer (Layer 1) Cost/Benefit Analysis Network layer (Layer 3) Gateway 10 points Question 27 1. Which of the following refers to a type of software product that is precompiled and whose source code is undisclosed? Circuit Closed source Bots Physical address 10 points Question 281. Adding caching to a firewall transforms it into a proxy server for whatever service you configure the caching to supplement. True False 10 points Question 29 1. Which of the following describes a BYOD? An application-programming interface (API) developed by IBM in 1985 to emulate NetBIOS on a token ring network A policy allowing or encouraging employees, contractors, and others to connect their own computers, smartphones, and other devices to their organization’s networks A legacy protocol developed by Novell for its NetWare networking product A security feature that blocks DDoS attacks 10 points Question 30 1. Although it provides a mechanism for creating tunnels through an IP network, which of the following does not provide a mechanism for encrypting the data being tunneled? Point-to-Point Protocol (PPP) Authentication Header (AH) Layer 2 Tunneling Protocol (L2TP) Encapsulating Security Payload (ESP) 10 points Question 31 1. Which of the following refers to an early communications protocol that competed with Point-to-Point Tunneling Protocol? Point-to-Point Tunneling Protocol (PPTP) Layer 2 Tunneling Protocol (L2TP) Layer 2 Forwarding (L2F) Protocol Internet Engineering Task Force (IETF)10 points Question 32 1. Script Kiddie is an experienced hacker who uses his or her own tools or scripts. True False 10 points Question 33 1. A worm is used to create Trojan horses by embedding malware inside of a host file or program. True False 10 points Question 34 1. In typical end user/browser usage, SSL/TLS authentication is two-way. True False 10 points Question 35 1. Which of the following refers to the entity responsible for global coordination of IP addressing, DNS root, and other Internet protocol resources? AppleTalk Bring Your Own Device (BYOD) Internet Assigned Numbers Authority (IANA) NetBIOS Extended User Interface (NetBEUI) 10 points Question 36 1. Which term describes an object, computer, program, piece of data, or other logical or physical component you use in a business process to accomplish a business task?Asset Client Applian ce Trust 10 points Question 37 1. The higher the encryption levels of VPN, the greater the impact on the memory and processor of the endpoint devices. True False 10 points Question 38 1. Which term describes the cumulative value of an asset based on both tangible and intangible values? Asset value (AV) Exposure factor (EF) Single loss expectancy (SLE) Packet 10 points Question 39 1. Which of the following refers to a network protocol that is a method for secure remote logon and other secure network services over a public network? Point-to-Point Protocol (PPP) Secure Shell (SSH) Authentication Header (AH) Encapsulating Security Payload (ESP) 10 points Question 40 1. A false negative is an event that triggers an alarm when the traffic or event is abnormal and/or malicious.True False 10 points Question 41 1. Which section of the VPN policy describes the systems, networks, or people covered by the policy? Introducti on Policy Scope Purpose 10 points Question 42 1. A firewall can perform only the operations for which it is programmed, and the specifics of and the order of the rules that result in less access rather than greater access are: List specific Deny rules first, then the Allow exceptions, and always keep the default-deny rule last. True False 10 points Question 43 1. Content filtering is a form of filtering that focuses on traffic content. True False 10 points Question 44 1. Which of the following hands out tasks in a repeating non-priority sequence? Port-based network access (admission) control (PNAC) Firewalking Round robinAlert 10 points Question 45 1. Which of the following describes optical carrier (OC)? A network carrier line—often leased or dedicated—which uses fiber optic cables for high-speed connections The process of converting ciphertext back into plain text A program used to control access to computer resources, enforce policies, audit usage, and provide billing information A set of rules and procedures, usually mathematical in nature 10 points Question 46 1. Which term is used to describe a public-key cryptography-based mechanism for proving the source (and possibly integrity) of a dataset or message? Trusted third party Symmetric cryptography Algorithm Digital signature 10 points Question 47 1. Which firewall product is designed for larger networks? Commercial firewalls Personal firewalls Sessions Appliance firewalls 10 points Question 48 1. Anonymity is the capability of a network or system user to remain known on the system. TrueFalse 10 points Question 49 1. Which name is given to a probability prediction based on statistics and historical occurrences on the likelihood of how many times in the next year a threat is going to cause harm? Tunnel mode encryption Physical address Annualized rate of occurrence (ARO) Rule 10 points Question 50 1. Which of the following describes a dedicated leased line? A set of rules and procedures, usually mathematical in nature. A hardware VPN device. An electronic proof of identity issued by a certificate authority (CA). Allows communication between one site and another 10 points Question 51 1. A security policy is important for all of the following reasons except which one? It establishes goals. It helps with planning. With it, you cannot trust the network's security. It helps respond, contain, and repair. 10 points Question 52 1. Which of the following refers to a communication pathway, circuit, or frequency dedicated or reserved for a specific transmission? Hardware VPN Host-to-site VPNAsymmetric cryptography Channel 10 points Question 53 1. Which layer of the OSI model is the Data Link Layer? Layer 1 Layer 2 Layer 3 Layer 4 10 points Question 54 1. Which of the following describes write-once read-many (WORM)? A mechanism defining traffic or an event to apply an authorization control of allow or deny against A storage device that can be written to once, but once written cannot be electronically altered A form of network access control or admission control (NAC) used on individual network access devices, such as firewalls, VPN gateways, and wireless routers A form of IDS/IPS detection based on a recording of real-world traffic as a baseline for normal 10 points Question 55 1. Which of the following refers to a protocol that provides integrity protection for packet headers and data, as well as user authentication? Point-to-Point Tunneling Protocol (PPTP) Request for Comments (RFC) Authentication Header (AH) Layer 2 Tunneling Protocol (L2TP) 10 points Question 561. Which of the following represents a standards-based protocol suite designed specifically for securing Internet Protocol communications? Authentication Header (AH) Tunnel mode Transport mode Internet Protocol Security (IPSec) 10 points Question 57 1. Which of the following should specifically be included in the organizations VPN solution? The prohibiting of split tunneling Encouraging shared VPN credentials Types of VPN connections supported How scalable the VPN is 10 points Question 58 1. Which term describes the seemingly random and unusable output from a cryptographic function applied to original data? Dedicated leased line Ciphertext Identity proofing Host VPN 10 points Question 59 1. A VPN appliance can be placed inside and outside the corporate firewall. True False 10 pointsQuestion 60 1. Which term describes the act of working from a home, remote, or mobile location while connecting into the employer’s private network, often using a VPN? Public key cryptography Host-to-site VPN Telecommuting Scalability [Show More]
Last updated: 1 year ago
Preview 1 out of 16 pages
Reviews( 0 )
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
16
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
64


ddtete3.png)